10 Cybersecurity Governance Best Practices for Defense Contractors
Discover essential cybersecurity governance best practices for defense contractors to enhance compliance.

Introduction
In an age where cyber threats loom larger than ever, defense contractors face immense pressure to strengthen their cybersecurity frameworks. The Cybersecurity Maturity Model Certification (CMMC) stands out as a vital benchmark, guiding organizations through the complexities of compliance and security governance. This article explores ten essential best practices that not only enhance compliance but also empower defense contractors to develop resilient cybersecurity strategies.
How can organizations effectively navigate the intricate landscape of cybersecurity governance while meeting the stringent demands of CMMC? The answer lies in adopting a proactive approach that addresses both current challenges and future risks. By implementing these best practices, defense contractors can not only comply with CMMC but also fortify their defenses against evolving cyber threats.
CMMC Info Hub: Your Essential Resource for Cybersecurity Governance Compliance
CMMC Info Hub stands as a vital knowledge base specifically designed for defense contractors striving to meet the rigorous standards of the Cybersecurity Maturity Model Certification (CMMC). Are you facing practical challenges in achieving certification readiness? This Hub is your solution, providing insights into what truly works in practice. By offering detailed roadmaps, practical strategies, and peer insights, it empowers organizations to effectively navigate the complexities of DoD security requirements.
This resource is not just beneficial; it is essential for ensuring compliance and enhancing your security posture. With the right tools at your disposal, you can make significant strides toward certification readiness. Consider this Hub a cornerstone of your governance strategy, guiding you through the intricate landscape of cybersecurity governance best practices and compliance. Don't miss out on the opportunity to elevate your organization's security framework.
Formal Cybersecurity Program: Establish a Well-Documented Framework
For any organization aiming to protect sensitive information, establishing a formal cybersecurity program that follows cybersecurity governance best practices is essential. It requires the development of a comprehensive, well-documented framework that clearly outlines policies, procedures, and controls. This framework must align with cybersecurity standards and be regularly updated to address evolving cyber threats.
CMMC Info Hub offers The Ultimate Guide to Achieving CMMC Compliance, providing practical strategies and peer insights to help defense contractors navigate this complex landscape with confidence. A strong digital protection program not only aids in compliance but also greatly enhances the entity's overall safety stance. It ensures that all employees understand their roles and responsibilities in upholding digital security, promoting a culture of security awareness across the organization.
Why is documenting security policies and procedures so crucial? Expert insights highlight that organizations should prioritize creating a structured approach that encompasses cybersecurity governance best practices, including risk assessments, incident response plans, and continuous monitoring strategies. By doing so, defense contractors can effectively manage risks and demonstrate their commitment to safeguarding sensitive information.
Best practices for establishing a cybersecurity framework in the defense industry include:
- Conducting regular training sessions to keep staff informed about the latest cybersecurity threats and protocols.
- Implementing a clear incident response plan that outlines steps to take in the event of a breach.
- Utilizing automated tools for monitoring compliance and identifying vulnerabilities in real-time.
The advantages of a documented security framework extend beyond compliance; they enhance operational resilience and build trust with stakeholders. By proactively tackling digital security challenges, firms can better position themselves to secure defense contracts and safeguard sensitive information. With the approaching compliance standards becoming obligatory on November 10, 2025, the necessity for defense contractors to create a formal security framework is evident.
Annual Risk Assessments: Perform Prudent Evaluations of Cybersecurity Risks
Annual risk assessments are crucial for identifying and evaluating cybersecurity threats and ensuring the implementation of cybersecurity governance best practices within a company. These assessments must encompass a comprehensive analysis of potential threats, vulnerabilities, and the effectiveness of existing controls according to cybersecurity governance best practices.
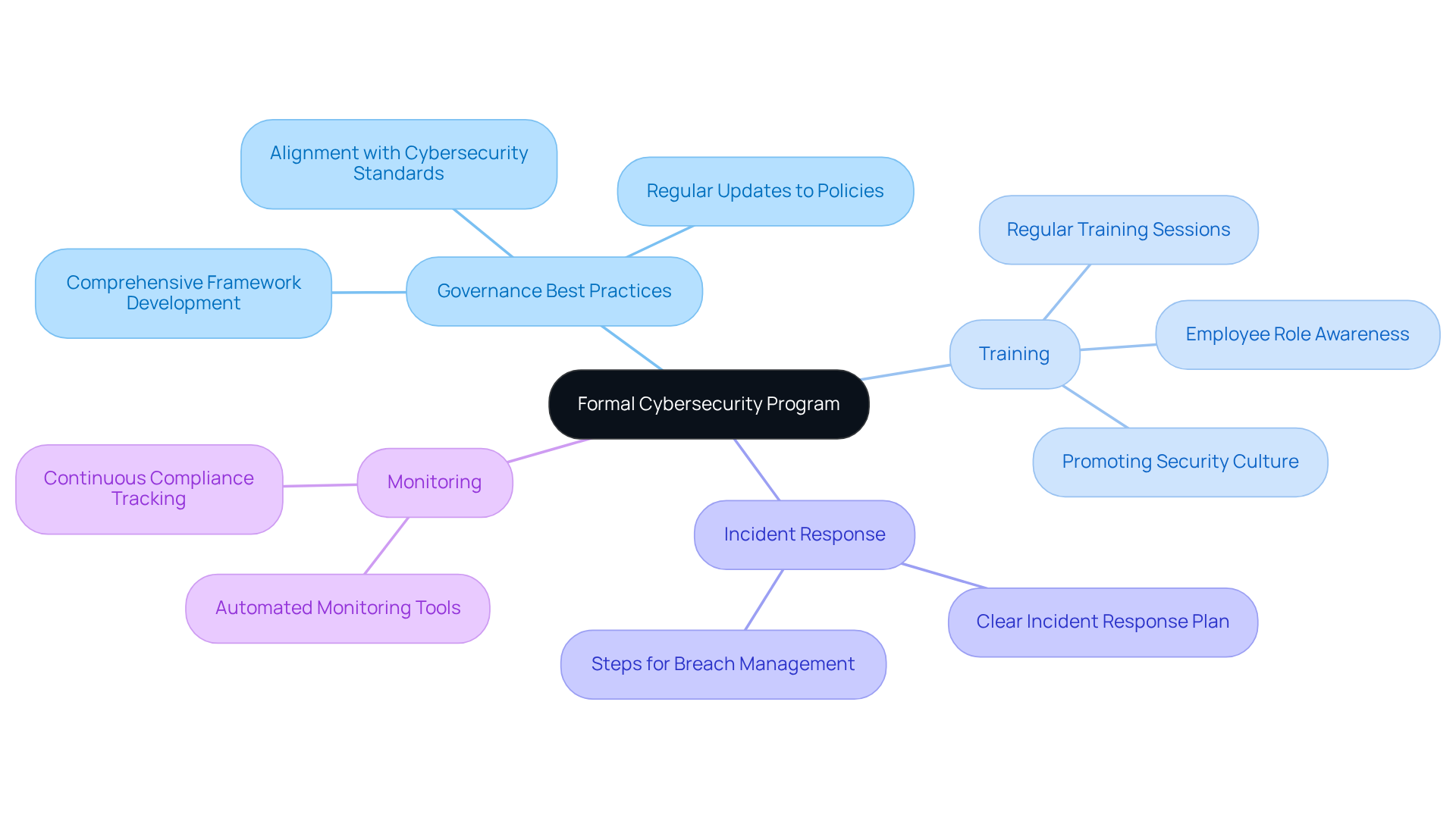
How can organizations ensure they meet security standards? By engaging in continuous monitoring and maintenance activities. This includes:
- Conducting regular vulnerability scans
- Executing prompt patch management
- Examining audit logs for incidents
- Overseeing configurations to prevent deviations from established baselines
Incorporating these continuous activities into risk evaluation procedures allows organizations to effectively adapt their cybersecurity governance best practices. This proactive approach not only reduces identified risks but also helps achieve compliance with assurance.
Are you ready to take your cybersecurity measures to the next level?
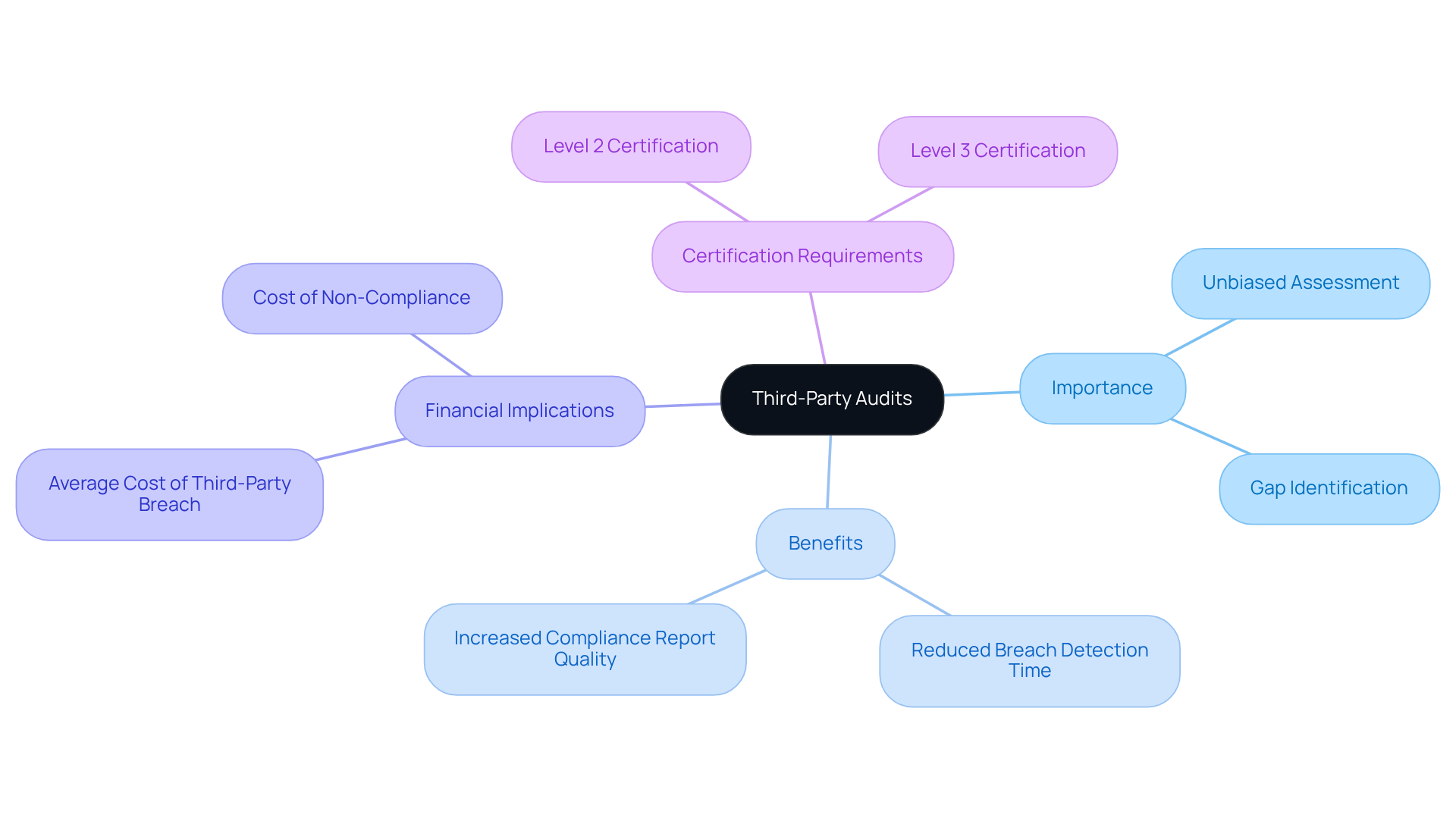
Third-Party Audits: Ensure Reliable Evaluation of Security Controls
Engaging third-party auditors to evaluate security controls is crucial for defense contractors looking to strengthen their cybersecurity posture. Why is this important? These audits offer an unbiased assessment of a company's compliance with CMMC requirements, pinpointing gaps and weaknesses that might otherwise remain hidden. For instance, organizations that implement continuous monitoring and external assessments can significantly reduce their typical breach detection time to just one to two days, compared to the industry average of 207 days. This proactive approach not only enhances protective measures but also ensures compliance with regulatory standards, ultimately safeguarding sensitive information and maintaining eligibility for defense contracts.
Moreover, expert insights reveal that companies utilizing third-party audits see a remarkable 79% increase in the quality of compliance reports. This statistic underscores the importance of reliable assessments in achieving robust security controls. Additionally, consider the financial implications: the average cost of a third-party breach exceeds $5.08 million. This figure highlights the risks associated with neglecting these audits. By prioritizing these evaluations, defense contractors can effectively mitigate risks tied to third-party relationships and bolster their overall protection framework.
Furthermore, for Level 2 and Level 3 certifications, third-party audits are not just beneficial; they are a requirement. This further emphasizes their vital role in ensuring compliance and enhancing security measures.
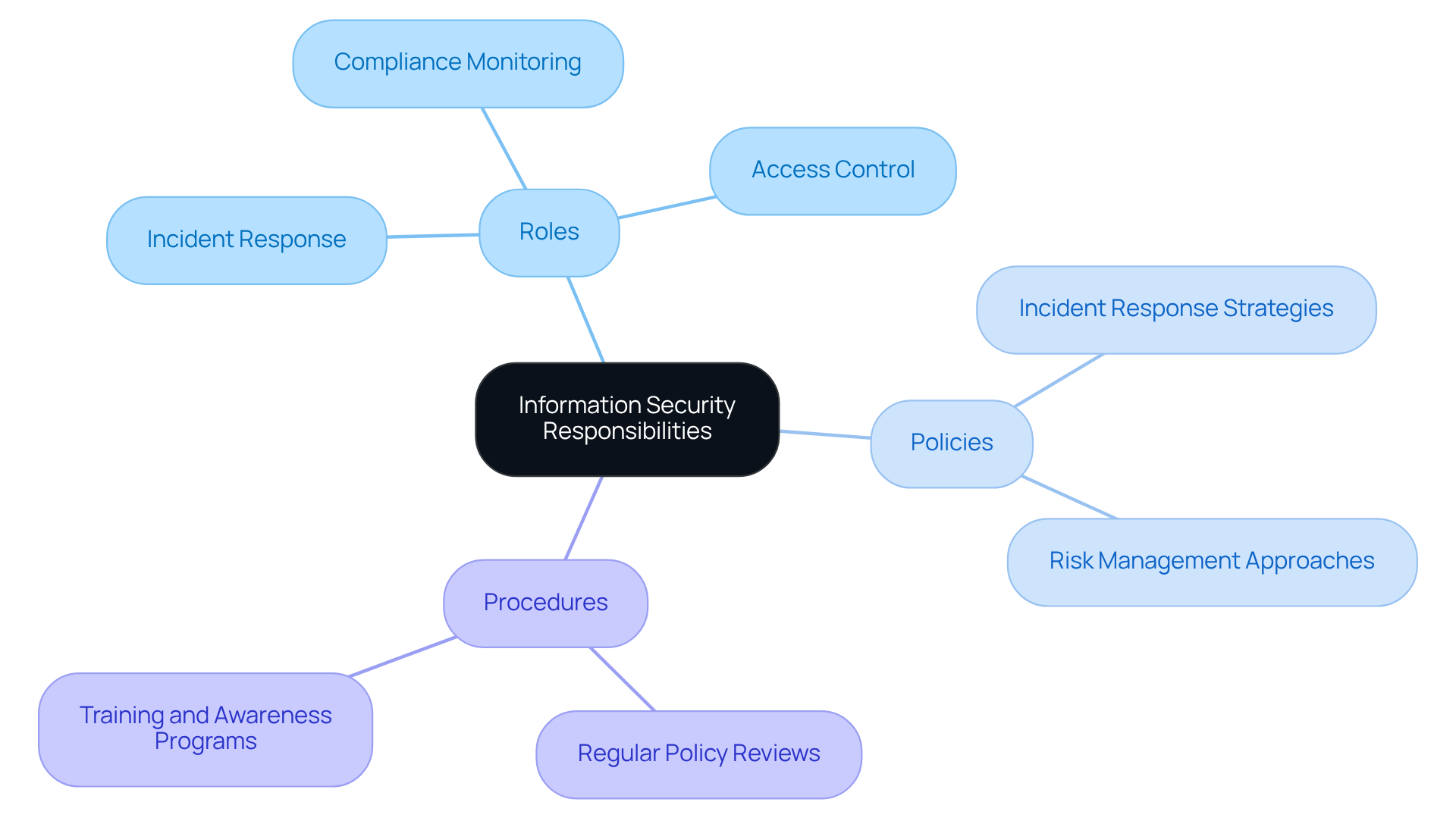
Defined Roles: Assign Clear Information Security Responsibilities
Establishing clear roles and responsibilities within the security framework is essential for implementing cybersecurity governance best practices. Do your team members fully understand their specific duties related to information protection? From incident response to compliance monitoring, this clarity not only promotes accountability but also ensures that all facets of cybersecurity are sufficiently managed. This contributes to a more robust defense stance.
Moreover, strong policies and procedures are crucial to ensuring cybersecurity governance best practices. Access control measures, incident response strategies, and risk management approaches must be uniformly and effectively applied in accordance with the framework. By leveraging practical strategies and peer insights, defense contractors can achieve CMMC compliance with confidence.
As a practical tip, regularly review and update these policies to adapt to evolving threats and compliance requirements. This proactive approach not only safeguards your organization but also reinforces your commitment to security excellence.
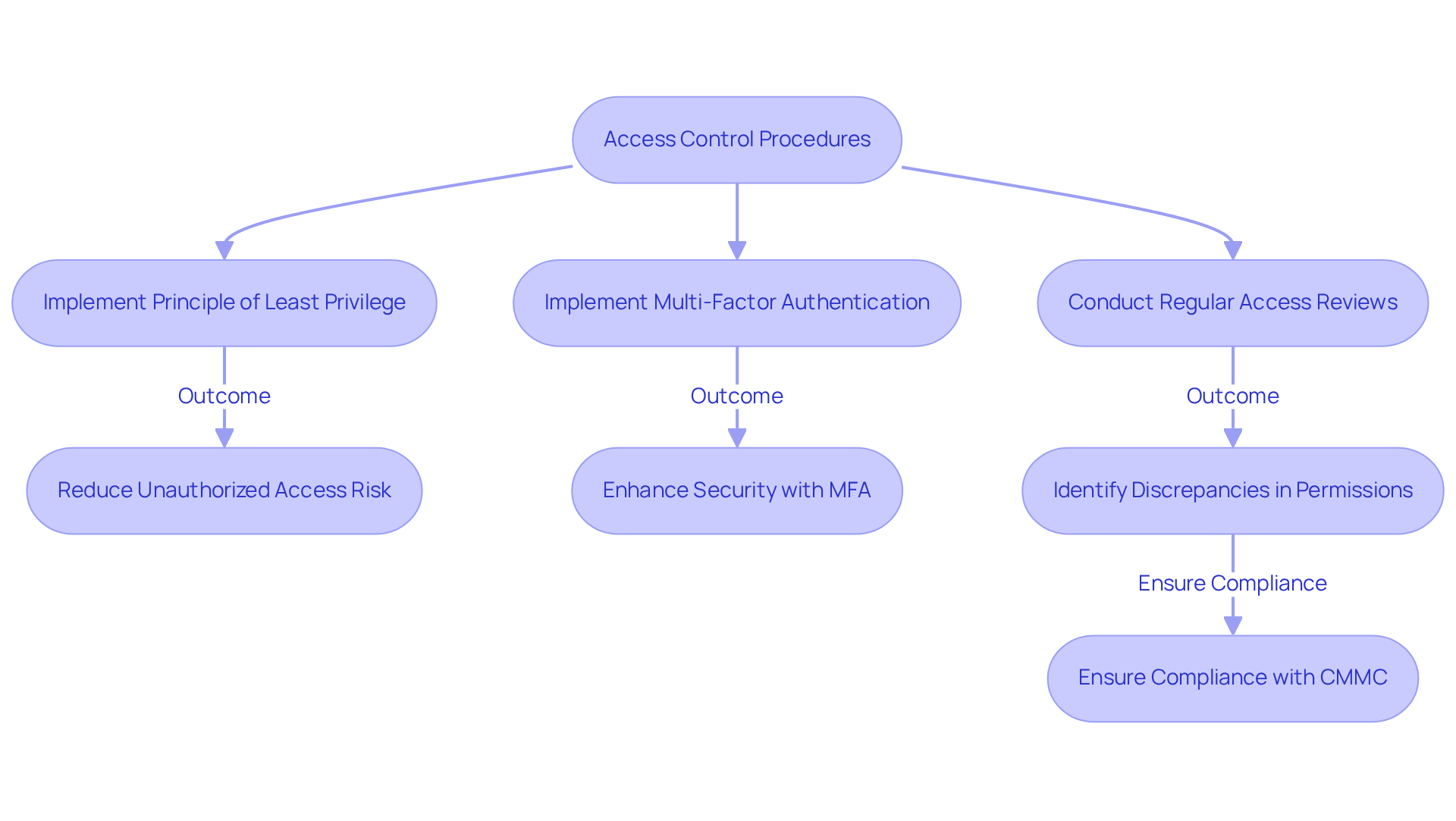
Access Control Procedures: Enforce Strong Security Measures
Implementing robust access control procedures is crucial for protecting sensitive information within entities. Have you considered how the principle of least privilege can transform your security measures? By ensuring that employees have access solely to the information necessary for their specific roles, you significantly reduce the risk of unauthorized access and potential data breaches.
To further enhance security measures, consider implementing multi-factor authentication (MFA) across all access points. This adds an extra layer of verification beyond just passwords, making it harder for unauthorized users to gain access.
Regular access reviews are essential as well. These audits help identify and rectify any discrepancies in user permissions, ensuring compliance with CMMC standards. By systematically implementing cybersecurity governance best practices, you can improve your security stance and uphold trust with the Department of Defense.
Are you ready to take the necessary steps to safeguard your sensitive information?
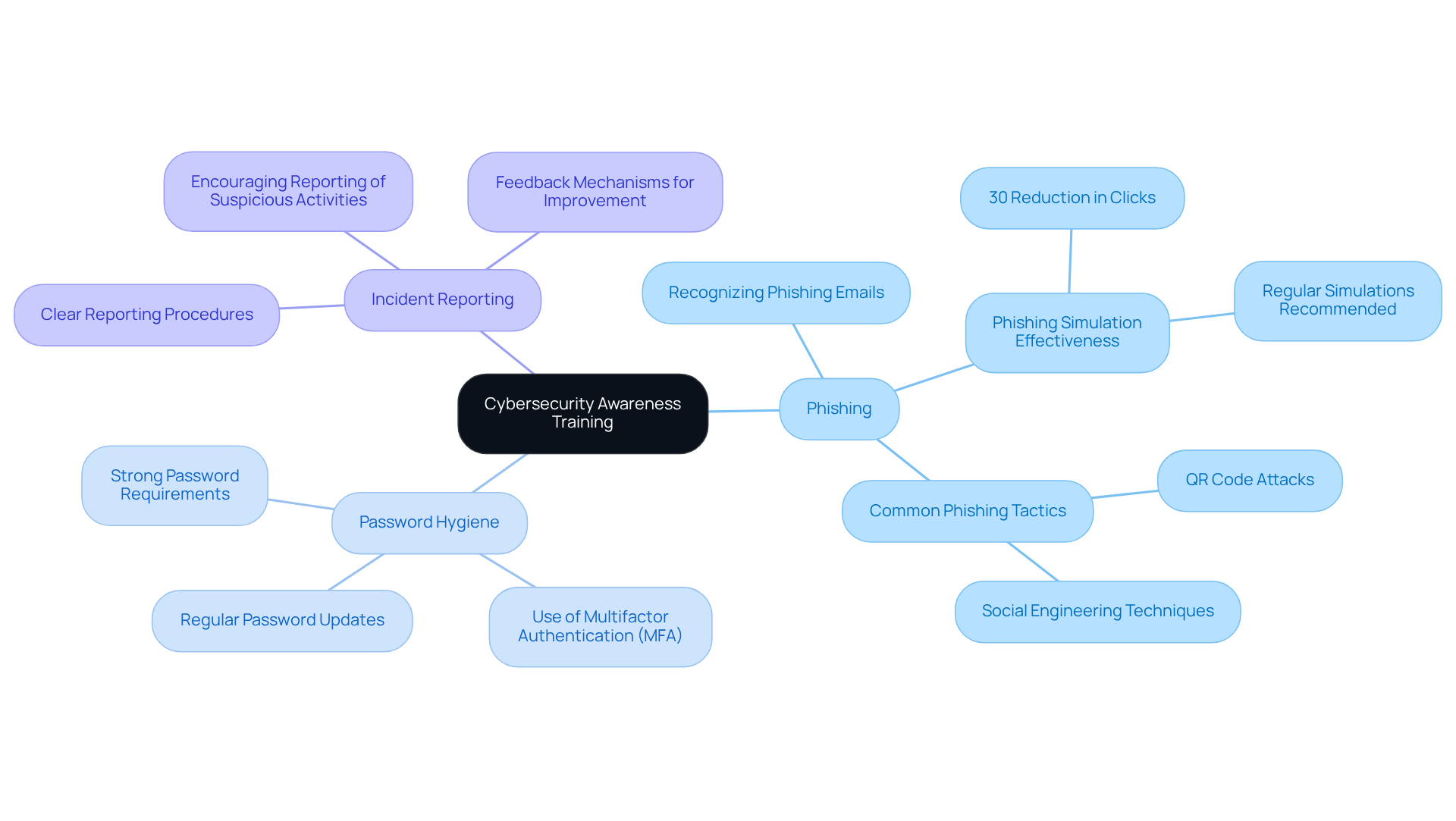
Cybersecurity Awareness Training: Educate Personnel Annually
Annual cybersecurity awareness training is essential for educating personnel about potential threats and the importance of cybersecurity governance best practices for safeguarding sensitive information. What if your organization could significantly reduce the risk of breaches? Training programs should encompass critical topics such as:
- Phishing
- Password hygiene
- Incident reporting
By fostering a culture of safety awareness, organizations can effectively lower the likelihood of human errors that lead to security incidents.
Consider this: a well-informed team is your first line of defense against cyber threats. Implementing comprehensive training not only empowers employees but also cultivates a proactive approach to cybersecurity governance best practices. Organizations must prioritize these training initiatives to protect sensitive data and maintain trust with clients and stakeholders.
Secure SDLC: Implement a Robust System Development Life Cycle
For defense contractors, adhering to cybersecurity governance best practices while implementing a secure software development life cycle (SDLC) is not just important; it’s essential. This process demands the integration of protective practices at every stage of development, from initial planning to deployment. Are you aware of the potential risks that could arise if these measures are overlooked? Frequent evaluations are crucial to identify weaknesses early on, while safe coding practices must be woven into the development process to mitigate risks effectively.
By prioritizing these measures, organizations not only enhance their protective stance but also ensure compliance with the stringent standards of cybersecurity governance best practices and the Cybersecurity Maturity Model Certification (CMMC). This proactive approach safeguards sensitive information and fortifies the overall integrity of defense contracts. Remember, the stakes are high, and the cost of non-compliance can be significant. Take action now to secure your development processes and protect your assets.
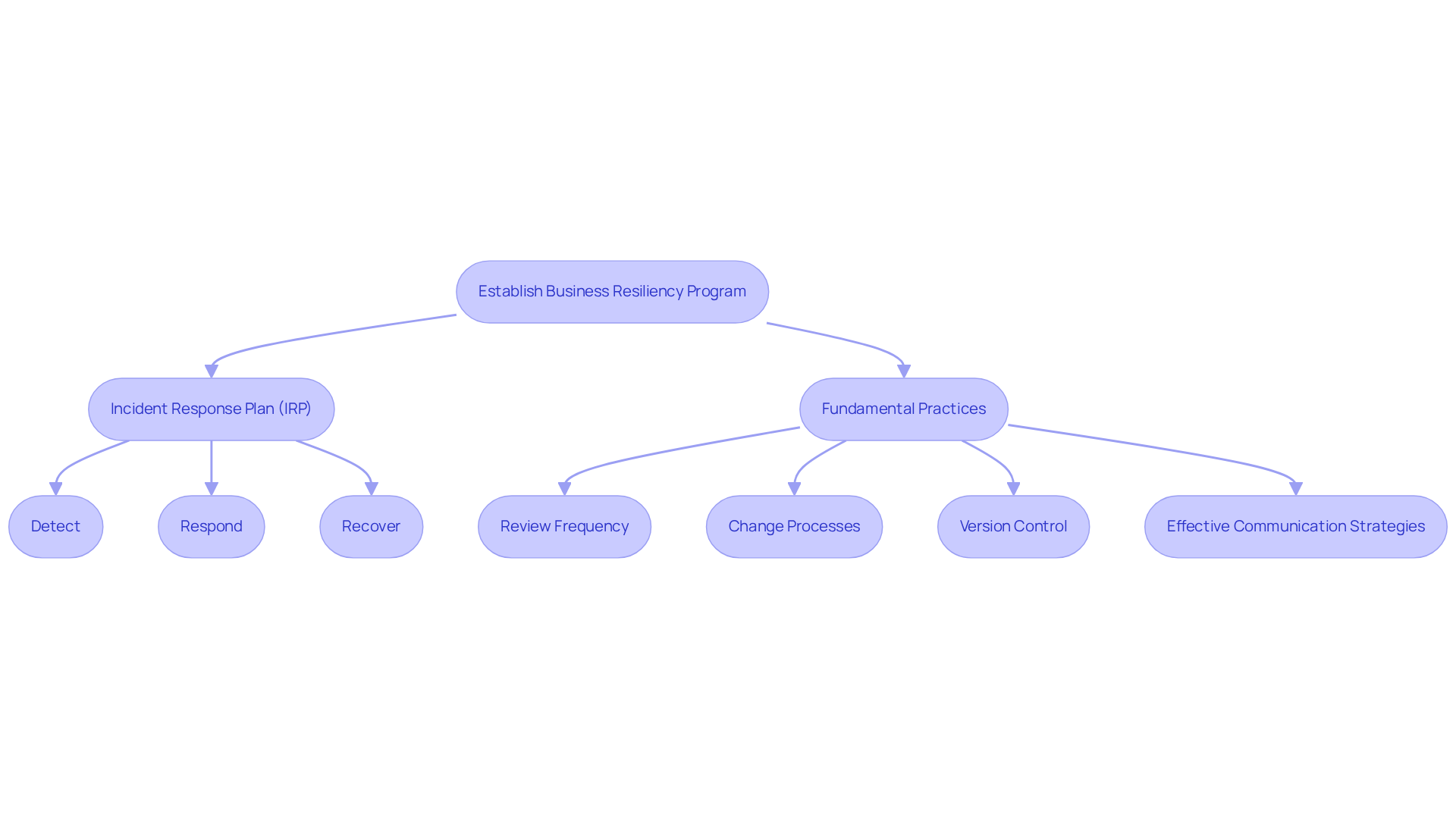
Business Resiliency Program: Address Continuity and Incident Response
Establishing a robust business resiliency program is essential for entities aiming to sustain operations during and after a cybersecurity incident, in accordance with cybersecurity governance best practices. At the heart of this program lies an incident response plan (IRP), which clearly outlines procedures for detecting, responding to, and recovering from security breaches. Why is this important? A well-defined IRP not only prepares entities for potential disruptions but also mitigates the impact of incidents, thereby enhancing compliance with CMMC standards.
Research shows that companies with documented IRPs incur significantly lower costs per breach - 58% less than those lacking structured protocols. Furthermore, organizations that regularly conduct incident response drills can respond 35% faster to incidents. This demonstrates the tangible benefits of preparedness. By prioritizing the development and maintenance of an IRP, defense contractors can effectively manage digital security threats in accordance with cybersecurity governance best practices, safeguarding their operations and sensitive information.
The Ultimate Guide to Achieving CMMC Compliance offers a comprehensive roadmap, providing practical strategies and peer insights that empower defense contractors to navigate the complexities of CMMC requirements with confidence. Fundamental practices for policy upkeep, such as:
- Review frequency
- Change processes
- Version control
- Effective communication strategies
are vital for strengthening the policies and procedures that reflect cybersecurity governance best practices in a robust security program.
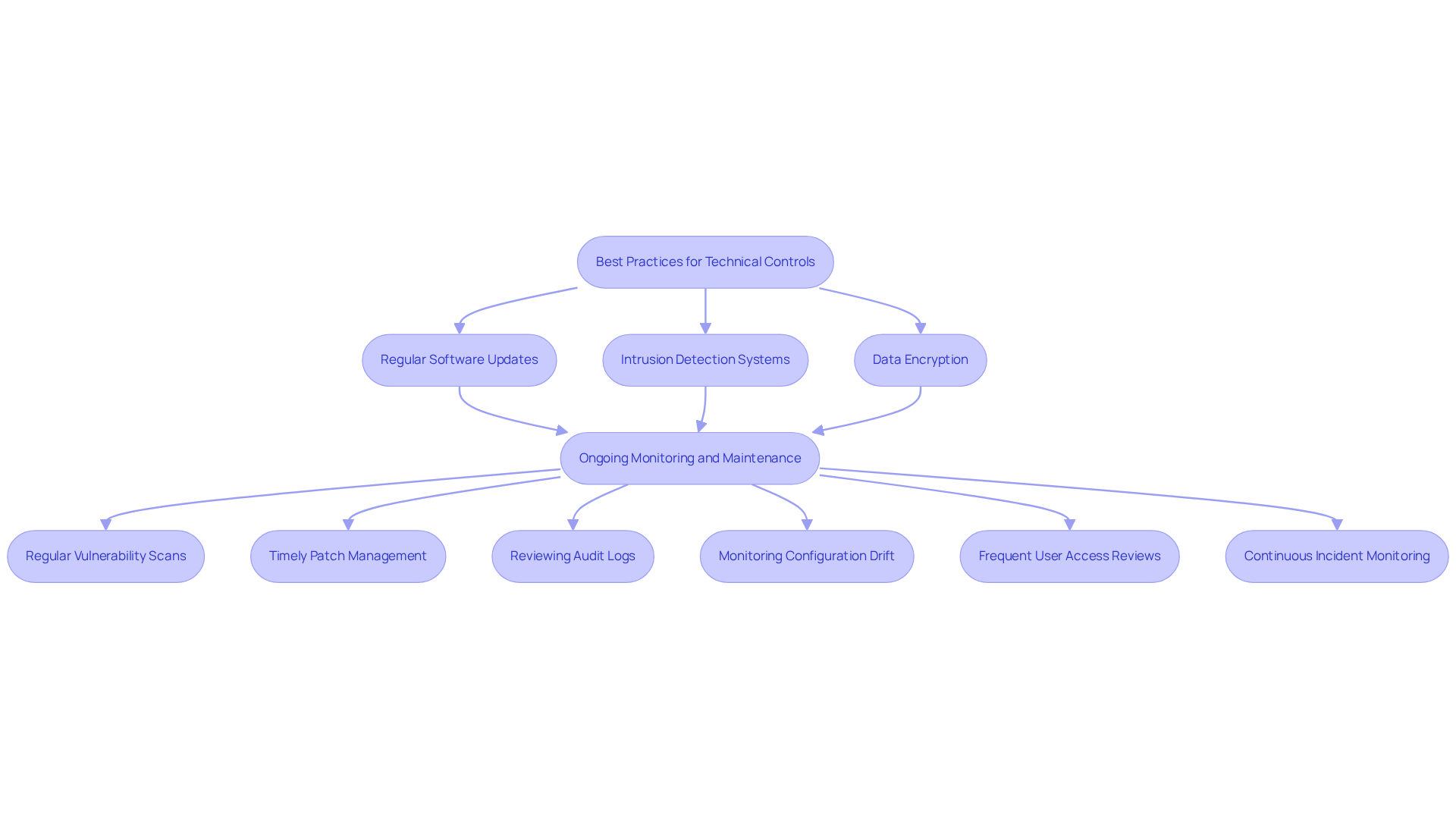
Technical Controls: Implement Best Security Practices
Implementing technical controls is essential for a robust cybersecurity strategy. To safeguard sensitive information, organizations must adopt cybersecurity governance best practices, such as:
- Regular software updates
- Intrusion detection systems
- Data encryption
But how can these measures ensure compliance with the cybersecurity maturity model?
Ongoing monitoring and maintenance practices are crucial. This involves:
- Conducting regular vulnerability scans to pinpoint weaknesses
- Implementing timely patch management
- Reviewing audit logs for signs of incidents
- Monitoring systems for configuration drift
- Frequent reviews of user access to ensure appropriateness
- Continuous incident monitoring
By establishing these technical controls and ensuring they function effectively, organizations can significantly enhance their security posture and adhere to cybersecurity governance best practices to meet CMMC requirements. This approach transforms confusion into clarity, providing practical strategies and peer insights that drive compliance. Are you ready to take action and fortify your cybersecurity measures?
Conclusion
Establishing robust cybersecurity governance is not just important; it's essential for defense contractors, especially as compliance with the Cybersecurity Maturity Model Certification (CMMC) becomes mandatory. This article outlines critical best practices, emphasizing a structured approach that not only meets regulatory requirements but also strengthens an organization's overall security posture. By prioritizing these practices, defense contractors can effectively navigate the complexities of cybersecurity governance and protect sensitive information.
Key insights include:
- The necessity of a formal cybersecurity program
- Regular risk assessments
- Third-party audits
- Clearly defined roles within the organization
Each of these components plays a vital role in creating a comprehensive security framework that enhances compliance and operational resilience. Moreover, implementing strong access control measures and conducting annual cybersecurity awareness training are crucial for cultivating a culture of security and reducing human error.
In summary, the urgency for defense contractors to adopt these cybersecurity governance best practices cannot be overstated. As the landscape of cyber threats continues to evolve, organizations must remain vigilant and proactive in their security measures. Taking action now to implement these strategies not only ensures compliance with forthcoming standards but also lays a solid foundation for a secure and resilient future in defense contracting.
Frequently Asked Questions
What is the CMMC Info Hub and its purpose?
The CMMC Info Hub is a resource designed for defense contractors to help them meet the standards of the Cybersecurity Maturity Model Certification (CMMC). It provides insights, roadmaps, practical strategies, and peer insights to aid organizations in navigating DoD security requirements.
Why is it important to establish a formal cybersecurity program?
Establishing a formal cybersecurity program is essential for protecting sensitive information. It involves creating a comprehensive framework that outlines policies, procedures, and controls, ensuring alignment with cybersecurity standards and addressing evolving cyber threats.
What resources does the CMMC Info Hub offer for achieving compliance?
The CMMC Info Hub offers 'The Ultimate Guide to Achieving CMMC Compliance,' which includes practical strategies and peer insights to help defense contractors navigate the complexities of achieving compliance with CMMC standards.
What are the key components of a well-documented cybersecurity framework?
A well-documented cybersecurity framework should include clear policies, procedures, and controls, regular updates to address evolving threats, risk assessments, incident response plans, and continuous monitoring strategies.
How can organizations promote a culture of security awareness?
Organizations can promote a culture of security awareness by conducting regular training sessions for staff to inform them about the latest cybersecurity threats and protocols, ensuring that all employees understand their roles in maintaining digital security.
What are the best practices for establishing a cybersecurity framework in the defense industry?
Best practices include conducting regular training sessions, implementing a clear incident response plan, utilizing automated tools for monitoring compliance, and identifying vulnerabilities in real-time.
Why are annual risk assessments important for organizations?
Annual risk assessments are crucial for identifying and evaluating cybersecurity threats, ensuring that cybersecurity governance best practices are implemented, and assessing the effectiveness of existing controls.
What activities should organizations engage in for continuous monitoring and maintenance?
Organizations should conduct regular vulnerability scans, execute prompt patch management, examine audit logs for incidents, and oversee configurations to prevent deviations from established baselines.
What are the benefits of having a documented security framework?
A documented security framework enhances operational resilience, builds trust with stakeholders, aids in compliance, and positions firms to secure defense contracts while safeguarding sensitive information.
What is the deadline for defense contractors to create a formal security framework?
The compliance standards for defense contractors will become obligatory on November 10, 2025, highlighting the necessity for them to establish a formal security framework.