10 Essential Cyber Security and Risk Management Articles for Defense Contractors
Explore essential cyber security and risk management articles for defense contractors' compliance and security.

Overview
The article titled "10 Essential Cyber Security and Risk Management Articles for Defense Contractors" identifies crucial resources that defense contractors can utilize to enhance their cybersecurity and risk management practices. It underscores the significance of compliance with the Cybersecurity Maturity Model Certification (CMMC), highlighting the necessity for continuous education, effective frameworks, and proactive strategies. In an ever-evolving threat landscape, these elements are vital to ensuring robust security measures.
By focusing on these resources, defense contractors can not only comply with CMMC requirements but also strengthen their overall security posture. The article serves as a guide, urging professionals to engage with these essential materials and implement the recommended practices. As the cybersecurity landscape continues to advance, staying informed and proactive is paramount.
Introduction
In an era where digital threats loom larger than ever, defense contractors find themselves at a critical juncture, navigating a complex landscape of cybersecurity requirements and compliance standards. This article presents a curated selection of ten essential resources that empower these contractors to bolster their cybersecurity and risk management practices.
With the impending Cybersecurity Maturity Model Certification (CMMC) compliance deadline approaching, the stakes have never been higher. How can organizations ensure they are not only compliant but also resilient against evolving threats? Exploring these pivotal articles will reveal strategies and insights vital for safeguarding sensitive information and maintaining a competitive edge in the defense sector.
CMMC Info Hub: Your Essential Resource for Cybersecurity Maturity Model Certification Compliance
The information hub serves as an essential resource for contractors in the military sector seeking compliance with the Cybersecurity Maturity Model Certification (CMMC). This platform offers comprehensive roadmaps and actionable strategies that clarify the Department of Defense's cybersecurity requirements, empowering organizations to secure defense contracts and protect sensitive information effectively. As of November 10, 2025, compliance will be mandatory, with the phased implementation of CMMC requirements across all relevant contracts over the next three years, as outlined in the Final DFARS Rule.
The platform's structured guidance, paired with insights from peers who have successfully navigated the compliance landscape, enables users to transform confusion into clarity. For instance, CyberSheath recently assisted Barge Design Solutions in achieving Level 2 certification on September 17, 2025. This case underscores the importance of proactive compliance efforts and illustrates a successful implementation.
The Info Hub not only equips users with critical information but also emphasizes the paramount importance of cybersecurity and risk management articles in ensuring compliance within the security sector. With only 1% of security suppliers fully prepared for the impending certification deadline, the urgency for adherence is unmistakable. As primary vendors increasingly mandate compliance with these standards from their suppliers, the platform's tailored insights and strategies become vital for maintaining competitiveness and ensuring secure supply chains. By leveraging the resources available through the Info Hub, military suppliers can pursue compliance with confidence and enhance their overall security posture.

Understanding Cyber Risk Management: Key Processes for Defense Contractors
Cyber risk management is paramount for defense contractors, as highlighted in cyber security and risk management articles, focusing on the identification, assessment, and mitigation of digital security threats. Establishing a robust risk management framework that aligns with compliance requirements is essential for the development of cyber security and risk management articles. The CMMC Info Hub provides practical strategies and peer insights to help you achieve CMMC compliance with confidence, serving as your ultimate guide to DoD security success.
Key processes include:
- Conducting thorough risk assessments
- Implementing effective security controls
- Continuously monitoring the effectiveness of these measures, as detailed in cyber security and risk management articles.
Effective strategies, as discussed in cyber security and risk management articles, necessitate:
- A proactive mindset
- The incorporation of advanced monitoring tools
- Fostering a culture of awareness regarding online security among staff.
As John Minnix, Co-Founder of Bright Defense, emphasizes, "Organizations must prioritize digital security as a fundamental aspect of their operational resilience."
By implementing these best practices and adhering to the roadmap provided by the CMMC Info Hub, defense contractors can enhance asset protection and ensure compliance with stringent regulatory standards, as discussed in cyber security and risk management articles.
Cybersecurity Frameworks: NIST CSF and ISO for Effective Risk Management
The NIST Cybersecurity Framework (CSF) and ISO 27001 are essential frameworks that are often highlighted in cyber security and risk management articles for their structured approaches to managing information security risks. NIST CSF centers around five critical functions: Identify, Protect, Detect, Respond, and Recover. These functions empower organizations to craft a robust security strategy that effectively addresses potential threats. Conversely, ISO 27001 delivers a systematic method for protecting sensitive information, ensuring its confidentiality, integrity, and availability.
Integrating NIST CSF with ISO 27001 not only enhances risk management practices but is also a topic covered in numerous cyber security and risk management articles, aligning organizations with the rigorous requirements of the Cybersecurity Maturity Model Certification (CMMC). This integration fosters a comprehensive understanding of security risks while promoting adherence to industry standards, as discussed in cyber security and risk management articles. Notably, recent updates to NIST CSF 2.0 have expanded its applicability beyond critical infrastructure, making it relevant for organizations of all sizes and sectors, including those within the military.
Furthermore, the implementation of these frameworks has been streamlined through practical tools and quick-start guides, enabling organizations to efficiently adopt best practices. As military suppliers navigate the complexities of compliance, leveraging the strengths of both NIST CSF and ISO 27001 can significantly bolster their security posture and readiness for contracts.
This platform may contain links to external websites. We have no control over the content of these external sites and accept no responsibility for their content or availability. The inclusion of any link does not imply endorsement by us.
Continuous Monitoring and Incident Response: Best Practices for Defense Contractors
Ongoing surveillance is essential for security providers, as highlighted in cyber security and risk management articles, including the routine evaluation of a company's security posture to identify weaknesses and threats. Implementing best practices such as:
- Automated monitoring tools
- Conducting thorough security audits
- Establishing a robust incident response plan
is vital, as discussed in various cyber security and risk management articles. Notably, statistics reveal that organizations with well-defined incident response strategies can reduce the average cost of a data breach—reaching $4.88 million in 2024—by up to 30%. In the event of a cyber incident, having a well-structured response strategy is crucial for minimizing damage and is often discussed in cyber security and risk management articles to ensure compliance with reporting requirements.
Moreover, it’s alarming that 88% of security breaches are attributed to human error. This highlights the importance of training teams on incident response protocols, a topic covered in cyber security and risk management articles, to enhance their preparedness. Case studies further illustrate that security providers emphasizing incident response training can achieve a 50% quicker recovery time from incidents. This clearly demonstrates the tangible advantages of being ready against cyber threats. By prioritizing ongoing surveillance and effective incident response training, organizations can significantly bolster their security measures, as discussed in cyber security and risk management articles.

Financial and Legal Implications: The Cost of Poor Cybersecurity for Defense Contractors
Inadequate online security poses significant risks, including substantial financial losses, legal responsibilities, and damage to reputation for defense contractors. Non-compliance with CMMC and other regulations can lead to hefty fines, loss of contracts, and increased scrutiny from regulatory bodies. Furthermore, data breaches necessitate costly remediation efforts and can erode customer trust. Organizations must recognize the importance of investing in robust security measures to mitigate these risks and protect their profits.
By prioritizing security compliance, defense contractors can safeguard their operations and maintain a competitive edge in the industry. The implementation of strong security protocols not only reduces the likelihood of breaches but also enhances the overall resilience of the organization. Therefore, it is imperative for stakeholders to take proactive steps towards ensuring compliance with CMMC and other relevant regulations.
Challenges in Cybersecurity: Addressing Skills Shortages and Operational Balance
Defense contractors frequently encounter significant challenges, including skills shortages in security personnel and the pressing need to balance operational demands with protection requirements. The rapid evolution of cyber threats underscores the necessity for a skilled workforce capable of implementing and managing effective strategies outlined in cyber security and risk management articles. To address these issues, organizations must invest in robust training and development programs designed to upskill existing employees while attracting new talent.
Moreover, fostering a culture of security awareness across all tiers of the organization is crucial. This approach not only assists in mitigating risks but also enhances the overall security posture. By prioritizing training and promoting a security-centric culture, defense contractors can better navigate the complexities of today’s threat landscape, as discussed in cyber security and risk management articles, and ensure compliance with industry standards.

Best Practices for Cyber Risk Management: Training and Awareness for Defense Contractors
Creating a robust training program is essential for cultivating a culture of security awareness among employees, as emphasized in cyber security and risk management articles. Regular training sessions, phishing simulations, and access to resources that keep staff informed about emerging threats are best practices discussed in cyber security and risk management articles. Have you considered how encouraging open communication about security concerns and incidents can empower employees? This approach fosters a proactive stance towards the topics covered in cyber security and risk management articles.
For instance, successful phishing simulation initiatives within security contracting have demonstrated significant reductions in susceptibility to cyber threats, showcasing the effectiveness of hands-on training. Moreover, engaging in activities such as the Cyber Storm series can enhance preparedness for major cyber incidents. Additionally, CISA's security evaluations can assist organizations in assessing their operational resilience and procedures.
By equipping staff with essential knowledge and skills, security firms can substantially diminish the likelihood of cyber incidents stemming from human errors, a topic explored in numerous cyber security and risk management articles, thereby bolstering their overall cybersecurity posture. To implement an effective training program, consider leveraging resources from CISA and incorporating regular assessments to measure progress and adapt strategies accordingly.
Integrating Cyber Risk Management with Anti-Fraud Technology: A Strategic Approach
Integrating cyber security and risk management articles with anti-fraud technology is essential for defense contractors aiming to safeguard sensitive information and assets. This strategic approach leverages advanced technologies such as machine learning and artificial intelligence to detect anomalies and potential fraud in real-time.
How can organizations attain compliance in this complex landscape? By adopting practical strategies, including:
- Regular training for staff to recognize fraud patterns
- Implementing robust monitoring systems utilizing AI for continuous threat assessment
Peer insights reveal that collaboration with security specialists can significantly enhance these efforts, providing valuable perspectives on emerging threats and compliance challenges. Regular assessments and updates to these integrated systems are crucial for maintaining effectiveness.
Are you confident in your current compliance measures? Ensuring that your organization is equipped with the latest tools and knowledge is vital for achieving compliance with confidence. Take action now to fortify your defenses and protect your assets.
Regular Risk Assessments: Keeping Cybersecurity Measures Up-to-Date for Defense Contractors
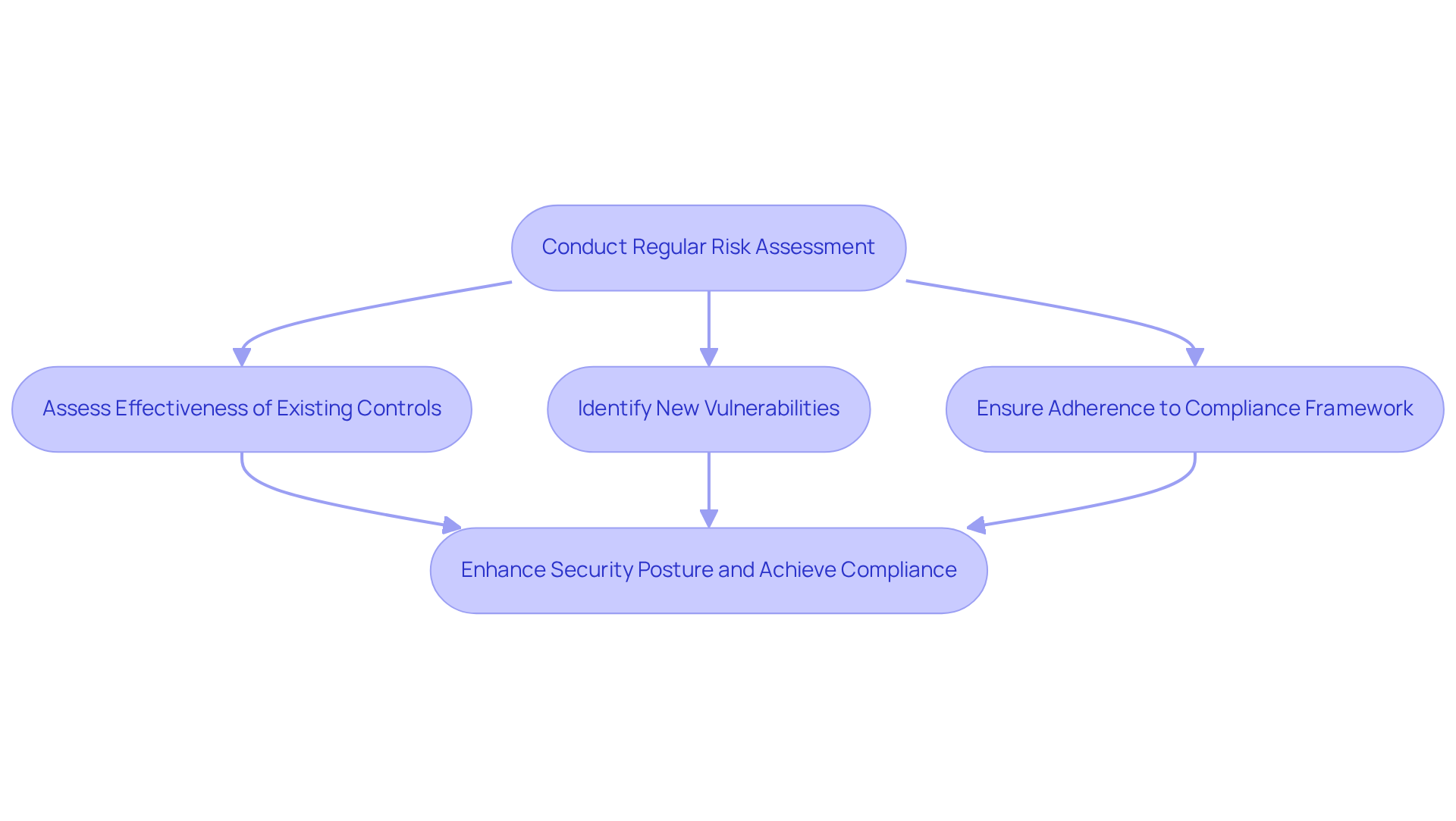
Routine risk evaluations, as emphasized in cyber security and risk management articles, are essential for defense contractors aiming to keep their cybersecurity strategies up-to-date and compliant with regulatory requirements. These evaluations must:
- Assess the effectiveness of existing controls
- Identify new vulnerabilities
- Ensure adherence to the compliance framework
By adopting a risk-oriented approach, organizations can prioritize areas with the highest potential impact, thereby achieving compliance more effectively.
Conducting evaluations at least annually or in response to significant changes allows security providers to proactively address emerging threats, enhance their security posture, and navigate the complexities of CMMC requirements with confidence. This proactive stance not only safeguards sensitive information but also fortifies the organization's overall cybersecurity framework. Are you ready to take the necessary steps to ensure your compliance and security?
In conclusion, regular risk evaluations are not just a regulatory requirement; they are a strategic imperative that empowers organizations to stay ahead in the ever-evolving cybersecurity landscape, as discussed in numerous cyber security and risk management articles.
Navigating the Evolving Threat Landscape: Strategies for Defense Contractors
In the face of an increasingly complex threat landscape, defense contractors must prioritize staying informed about emerging cyber threats and trends through cyber security and risk management articles. Active participation in threat intelligence sharing initiatives, as discussed in cyber security and risk management articles, is a key strategy that fosters collaboration among industry peers and enhances collective security. Recent statistics indicate that organizations typically face around 15,000 exposures across their environments, and more than 80 percent of data breaches involve data stored in the cloud. This underscores the necessity for robust threat intelligence frameworks. Engaging with resources from organizations like CISA and NIST can provide valuable insights and tools found in cyber security and risk management articles for effective risk management.
Furthermore, regular updates to security policies and incident response plans are essential to incorporate the latest threat intelligence. As Kay Pang emphasizes, boards must acknowledge digital security as a business risk, which is frequently discussed in cyber security and risk management articles, highlighting the significance of a proactive approach. This proactive strategy not only enhances protections but also guarantees adherence to evolving regulatory standards. Industry leaders stress that a well-coordinated effort in threat intelligence sharing, as highlighted in cyber security and risk management articles, can significantly reduce risks and improve overall security resilience for firms in the defense sector. To effectively implement these strategies, defense contractors should establish regular review cycles for their cybersecurity policies and incident response plans, ensuring alignment with the latest threat intelligence.

Conclusion
In summary, the landscape of cybersecurity for defense contractors is increasingly complex, necessitating a proactive approach to compliance and risk management. By leveraging resources such as the CMMC Info Hub and integrating established frameworks like NIST CSF and ISO 27001, organizations can enhance their security posture while ensuring adherence to regulatory standards. The importance of continuous monitoring, incident response preparedness, and regular risk assessments cannot be overstated; these practices are fundamental to safeguarding sensitive information and maintaining a competitive edge in the industry.
The article highlights several key insights, including:
- The urgent need for compliance with the Cybersecurity Maturity Model Certification (CMMC)
- The critical role of training and awareness programs
- The financial and legal implications of insufficient cybersecurity measures
Furthermore, addressing skills shortages and fostering a culture of security awareness are essential steps that defense contractors must undertake to navigate the evolving threat landscape effectively.
Ultimately, the call to action for defense contractors is clear: prioritize cybersecurity as an integral part of operational resilience. By investing in robust security measures, staying informed about emerging threats, and fostering collaboration within the industry, organizations can not only protect their assets but also contribute to a more secure defense ecosystem. Embracing these strategies will empower defense contractors to face the challenges ahead with confidence and agility.
Frequently Asked Questions
What is the CMMC Info Hub?
The CMMC Info Hub is a resource for military contractors seeking compliance with the Cybersecurity Maturity Model Certification (CMMC), offering roadmaps and strategies to clarify Department of Defense cybersecurity requirements.
When will CMMC compliance become mandatory?
Compliance with CMMC will be mandatory as of November 10, 2025, with a phased implementation of requirements across relevant contracts over the next three years.
Why is cybersecurity important for defense contractors?
Cybersecurity is crucial for defense contractors to protect sensitive information and secure defense contracts, especially as primary vendors increasingly require compliance from their suppliers.
What key processes are involved in cyber risk management for defense contractors?
Key processes include conducting thorough risk assessments, implementing effective security controls, and continuously monitoring the effectiveness of these measures.
What mindset and tools are necessary for effective cyber risk management?
A proactive mindset and the incorporation of advanced monitoring tools, along with fostering a culture of online security awareness among staff, are essential for effective cyber risk management.
What are the NIST Cybersecurity Framework (CSF) and ISO 27001?
The NIST CSF is a framework that focuses on five critical functions: Identify, Protect, Detect, Respond, and Recover, while ISO 27001 provides a systematic method for protecting sensitive information's confidentiality, integrity, and availability.
How can integrating NIST CSF and ISO 27001 benefit organizations?
Integrating NIST CSF with ISO 27001 enhances risk management practices and aligns organizations with CMMC requirements, promoting a comprehensive understanding of security risks and adherence to industry standards.
What resources does the CMMC Info Hub provide for compliance?
The CMMC Info Hub provides practical strategies, peer insights, and a roadmap to help defense contractors achieve CMMC compliance and enhance their overall security posture.




