10 Essential NIST 800-171 Controls List for Defense Contractors
Discover the essential NIST 800-171 controls list for defense contractors to enhance cybersecurity compliance.

Introduction
Navigating the complex world of cybersecurity compliance can be a significant challenge for defense contractors, particularly with the rigorous demands of the NIST 800-171 controls list. This vital framework not only protects sensitive information but also lays the groundwork for meeting Department of Defense standards. As organizations work to strengthen their cybersecurity posture, a pressing question arises: how can they effectively implement these controls to satisfy regulatory requirements while also enhancing their operational resilience?
This article explores ten essential NIST 800-171 controls that every defense contractor should prioritize. By offering insights and actionable strategies, we aim to transform compliance into a competitive advantage. Are you ready to take the necessary steps towards not just meeting compliance but thriving in a secure environment?
CMMC Info Hub: Your Essential Resource for NIST 800-171 Compliance
CMMC Info Hub stands as a vital resource for organizations aiming to comply with the NIST 800-171 controls list. It offers comprehensive roadmaps, actionable strategies, and insights from peers, empowering defense contractors to effectively navigate the complex cybersecurity landscape. By leveraging this knowledge base, organizations can streamline their regulatory processes and significantly bolster their cybersecurity posture, ensuring compliance with the stringent standards set by the Department of Defense, particularly the NIST 800-171 controls list.
As adherence to CMMC becomes increasingly crucial, the platform is continuously evolving, providing tailored resources that tackle the unique challenges contractors face. Cybersecurity experts emphasize that such knowledge repositories are essential for fostering a culture of compliance. They enable organizations not only to meet regulatory requirements but also to strengthen their overall security framework.
With CMMC Info Hub, defense contractors can transform their approach to regulations, turning potential hurdles into opportunities for growth and enhanced operational efficiency. Are you ready to take the next step in your compliance journey? Explore the resources available and empower your organization today.
Access Control: Safeguarding Sensitive Information
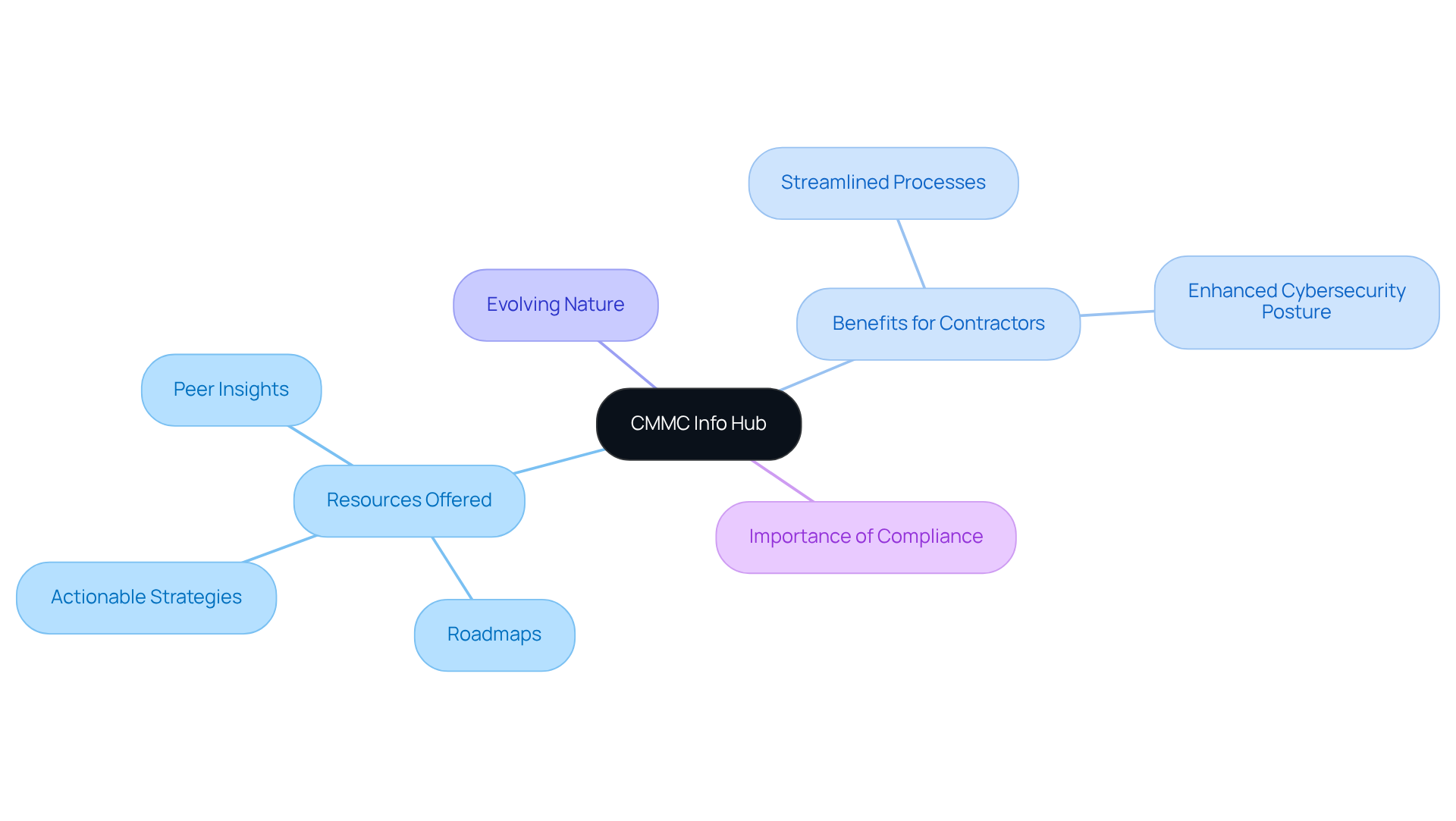
Access control is crucial for protecting sensitive information within an organization and serves as a vital step toward achieving CMMC compliance. According to the NIST 800-171 controls list, access to Controlled Unclassified Information (CUI) must be restricted to authorized users, processes, and devices. One effective strategy is implementing multi-factor authentication (MFA), which significantly boosts security by requiring multiple forms of verification before granting access. Additionally, role-based access controls ensure that individuals can only access information pertinent to their responsibilities, thereby reducing the risk of unauthorized retrieval.
Regular audits of access permissions are essential as well. They help identify and rectify any discrepancies, ensuring that only authorized personnel can access sensitive data. These measures not only safeguard critical information but also align with the NIST 800-171 controls list, which strengthens the organization's cybersecurity posture. As Bruce Schneier aptly noted, "individuals are often the weakest link in the protection chain," highlighting the importance of human factors in control strategies.
Moreover, consider this: Business Email Compromise (BEC) losses have exceeded $26 billion since 2016, underscoring the financial repercussions of inadequate permission controls. A compelling case study of an accounting firm illustrates this point well. By implementing regular role-specific protective training, they effectively mitigated internal incidents, showcasing how robust access control measures can lead to improved safety outcomes. This aligns perfectly with the essential self-assessment guide for CMMC adherence. Are you ready to take action and enhance your organization's security posture?
Awareness and Training: Educating Your Workforce
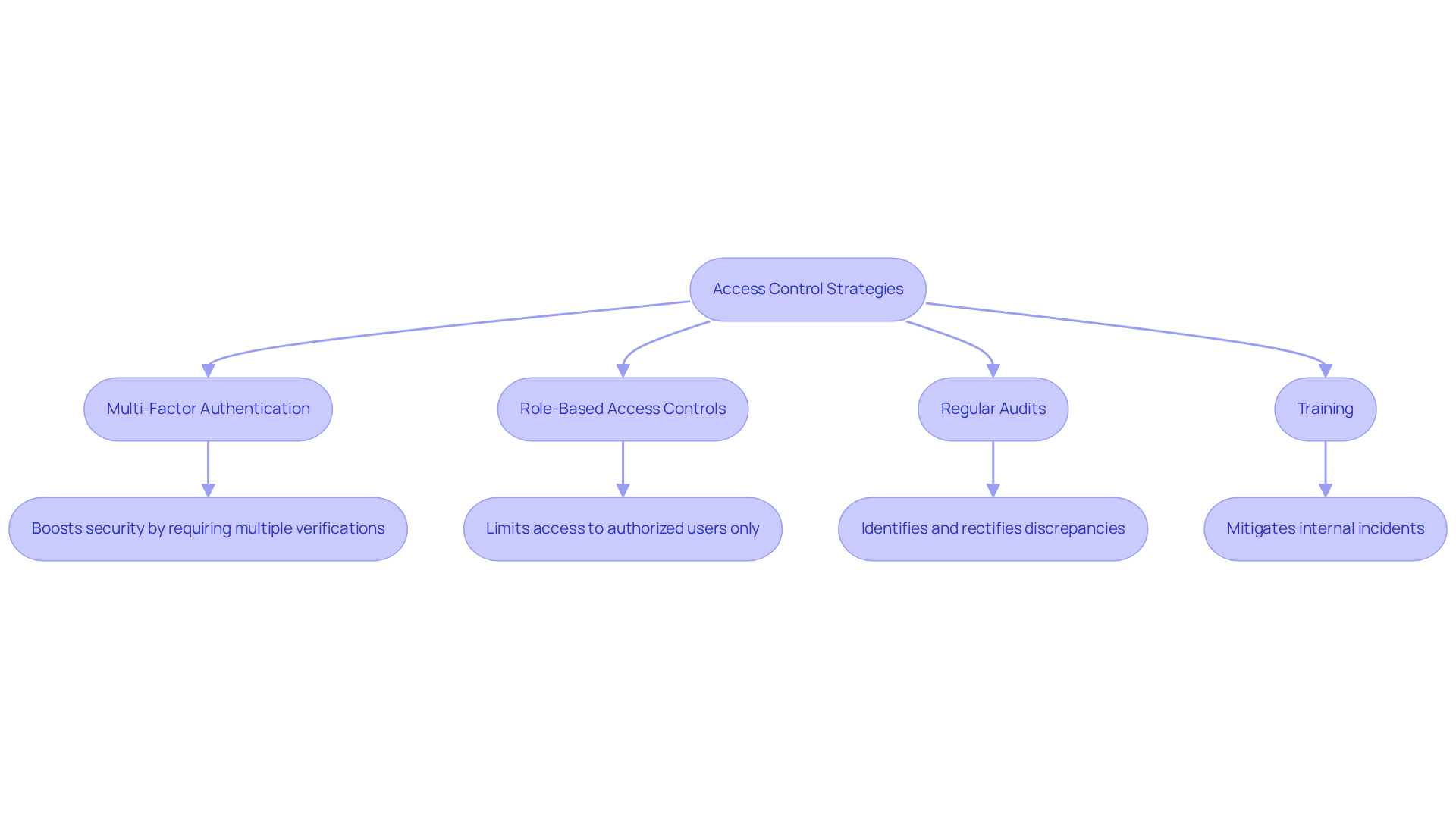
Awareness and training are essential for achieving compliance with the NIST 800-171 controls list. Organizations must establish ongoing cybersecurity training programs that empower employees to protect Controlled Unclassified Information (CUI). These programs should focus on critical areas such as:
- Identifying phishing attempts
- Understanding data handling protocols
- Adhering to established safety policies
By cultivating a strong culture of awareness, organizations can significantly reduce the risk of human errors, a leading cause of data breaches.
Consider this: recent trends show that organizations prioritizing tailored training initiatives experience notable improvements in employee engagement and adherence. In fact, 96% of executives believe that comprehensive training can substantially reduce cyberattacks. Yet, only 10% actively promote such initiatives, according to the Boston Consulting Group. This gap underscores the urgent need for leadership to champion training in safety.
Moreover, effective training programs that incorporate real-world scenarios and role-specific content enhance employees' ability to identify and respond to phishing threats. This ultimately fosters a more secure organizational environment. Statistics reveal that phishing click rates drop significantly after recurring, role-based training combined with simulations, demonstrating the effectiveness of targeted training approaches.
In conclusion, organizations must take action now to implement robust training programs. By doing so, they not only protect their sensitive information but also empower their workforce to be vigilant against cyber threats.
Audit and Accountability: Ensuring Compliance Integrity
Audit and Accountability: Ensuring Compliance Integrity
Audit and accountability are not just buzzwords; they are essential pillars for achieving and maintaining compliance with NIST 800-171. Organizations must implement robust procedures for creating, protecting, and retaining audit logs that meticulously document system activities. Regular audits are crucial for detecting unauthorized access and verifying that security controls operate effectively. Have you considered how automated logging solutions could simplify your log management? These tools not only streamline the process but also provide vital insights for identifying regulatory gaps.
Best Practices for Audit Log Management:
- Ensure logs are tamper-proof.
- Retain logs for a specified duration.
- Regularly review logs to detect anomalies.
Cybersecurity auditors emphasize that accountability is paramount; entities must clearly define roles and responsibilities in the regulatory process to mitigate risks and ensure adherence to standards. By adopting these best practices, defense contractors can significantly enhance their compliance posture with the NIST 800-171 controls list and safeguard sensitive information. Furthermore, leveraging practical strategies and insights from 'The Ultimate Guide to Achieving CMMC Adherence' can transform confusion into clarity, guiding entities through the complexities of CMMC adherence and ensuring a comprehensive approach to cybersecurity maturity.
Configuration Management: Maintaining System Security
Configuration management is vital for maintaining the security and compliance of systems with the NIST 800-171 controls list. Have you established baseline configurations for your systems? Implementing effective controls to manage changes is crucial. Regular reviews and updates of configurations can prevent unauthorized changes that might introduce vulnerabilities.
To achieve CMMC adherence confidently, organizations must adopt practical strategies that incorporate the NIST 800-171 controls list. This includes:
- Maintaining a formal process for proposing and approving changes
- Ensuring version control of policies
Utilizing automated configuration management tools can significantly enhance this process. These tools streamline monitoring and maintenance, ensuring that systems are consistently managed.
Moreover, it’s essential to communicate policy alterations clearly to all impacted staff. This promotes understanding and adherence, which are key to successful compliance. By taking these steps, organizations not only protect their systems but also foster a culture of security and compliance.
Identification and Authentication: Verifying User Access
Identification and authentication are crucial for achieving compliance with the NIST 800-171 controls list. Organizations must establish robust mechanisms to verify the identities of users and devices accessing their systems. This includes implementing unique identifiers, enforcing strong password policies, and utilizing multi-factor authentication (MFA). Did you know that 95% of security incidents stem from human error, often linked to weak passwords? Organizations with strict password policies significantly reduce their vulnerability to breaches.
Multi-factor authentication has become a vital defense strategy. Studies show that MFA can prevent over 99.9% of unauthorized entry attempts. Organizations that adopt MFA experience a marked decrease in successful phishing attacks, highlighting its effectiveness in protecting sensitive information. In the defense sector, where the stakes are particularly high, strong authentication mechanisms are not just a compliance requirement; they are essential for operational security, as emphasized in 'The Ultimate Guide to Achieving CMMC Compliance.'
Regularly reviewing and updating authentication methods is essential to ensure access controls remain resilient against evolving threats. As cybercriminals increasingly target organizations with sophisticated tactics like SIM-jacking and MFA Hammering, defense contractors must prioritize advanced authentication strategies. By doing so, they not only enhance their protective measures but also demonstrate a commitment to safeguarding sensitive information, which is vital for maintaining trust with clients and stakeholders.
To further bolster your compliance efforts, consider conducting regular training sessions for employees on the importance of strong authentication practices and the latest cyber threats. This proactive approach not only strengthens your security posture but also fosters a culture of awareness and responsibility within your organization.
Incident Response: Preparing for Security Breaches
A robust incident response strategy is crucial for organizations aiming to manage breaches effectively. Did you know that the NIST 800-171 controls list requires entities to establish procedures for detecting, reporting, and responding to incidents? This mandate emphasizes the importance of:
- Defining roles and responsibilities
- Conducting regular training exercises
- Maintaining open communication channels for incident reporting
Moreover, ongoing monitoring practices are vital. These include:
- Vulnerability scanning
- Patch management
- Log review
- Continuous incident monitoring
Such measures ensure that security controls remain effective and responsive to emerging threats. By proactively preparing for potential incidents and implementing these ongoing practices, organizations can significantly minimize damage and recover more swiftly.
In conclusion, investing in a comprehensive incident response strategy not only aligns with compliance requirements but also fortifies your organization against future threats as outlined in the NIST 800-171 controls list. Are you ready to take action and enhance your incident response capabilities?
Media Protection: Safeguarding Physical Data
Media protection is a pivotal component of the NIST 800-171 controls list, particularly in light of FAR 52.204-21, which outlines essential safeguarding standards for federal contractors. Organizations are required to implement robust measures to physically control and securely store media that contains Controlled Unclassified Information (CUI), whether digital or paper-based. This involves:
- Employing encryption for digital media
- Restricting access to authorized personnel
- Ensuring thorough sanitization of media prior to disposal
Why is this important? By adhering to the safeguarding measures specified in the NIST 800-171 controls list and FAR 52.204-21, organizations can effectively prevent unauthorized access and protect sensitive information. This not only secures data but also helps achieve compliance with CMMC Level 1 requirements.
In summary, the implementation of these measures is not just a regulatory obligation; it is a critical step towards safeguarding your organization’s integrity and reputation. Take action now to ensure your compliance and protect your sensitive information.
Personnel Security: Ensuring Trustworthy Access
Personnel protection is crucial for safeguarding Controlled Unclassified Information (CUI). Organizations must implement robust screening processes for individuals accessing sensitive information, which includes thorough background checks and continuous monitoring. Did you know that 96% of employers conduct background screenings before hiring? This statistic underscores the importance of vetting candidates to mitigate risks associated with insider threats. Efficient screening procedures should encompass:
- Criminal background checks
- Employment verification
- Social media evaluations
These actions can reveal potential warning signs that may jeopardize safety.
Creating clear guidelines regarding personnel entry and conducting regular training on protective protocols are vital measures to ensure that only reliable individuals are granted access to CUI. Industry leaders emphasize that cultivating a culture of protection within organizations is essential. Cybersecurity is not merely an IT concern; it is a leadership necessity. By prioritizing personnel protection and adhering to the NIST 800-171 controls list, defense contractors can significantly enhance their overall defense posture and safeguard sensitive information from unauthorized access.
Risk Assessment: Identifying and Mitigating Vulnerabilities
Conducting regular risk assessments is crucial for maintaining compliance with the NIST 800-171 controls list, as emphasized in The Ultimate Guide to Achieving CMMC Compliance. Organizations must assess their protection stance to identify vulnerabilities and evaluate the potential impact of incidents. This process involves analyzing existing controls, pinpointing gaps, and developing a comprehensive plan of action to address identified risks. To implement effective risk assessments, organizations should:
- Establish a routine schedule for evaluations.
- Utilize self-assessment checklists to ensure comprehensive coverage of all controls.
- Engage in tabletop exercises to test incident response plans, ensuring key decision-makers are prepared for crises.
As Sarah Ward, Chief Legal Officer at Chainalysis, emphasizes, "Cybersecurity tabletop exercises expose the gaps. You can have a beautifully written incident response plan, but if you don't test it, you'll realize too late that key decision-makers are missing when a crisis hits." By proactively managing risks, entities can enhance their security measures and ensure ongoing compliance with CMMC requirements.
Current trends indicate a shift towards structured approaches in vulnerability management, underscoring the importance of continuous improvement and adaptation in cybersecurity practices. Furthermore, organizations must recognize that non-compliance with DFARS can lead to severe consequences, including contract loss and penalties. This reality underscores the urgency of conducting regular risk assessments.

Conclusion
Navigating the complexities of NIST 800-171 compliance is not just essential; it’s a strategic imperative for defense contractors committed to securing sensitive information and maintaining operational integrity. This article underscores the critical controls necessary for achieving compliance, emphasizing that a proactive approach to cybersecurity not only meets regulatory requirements but also strengthens an organization's overall security framework.
Key points to consider include:
- Access Control: Safeguarding sensitive data through stringent measures.
- Employee Training: Fostering a culture of awareness among staff.
- Regular Audits: Ensuring ongoing compliance and identifying vulnerabilities.
- Robust Incident Response Strategies: Preparing for potential breaches effectively.
Each control serves a specific purpose, and effective implementation can significantly reduce vulnerabilities while enhancing compliance with the stringent standards set forth by the Department of Defense.
Ultimately, organizations must recognize that adherence to the NIST 800-171 controls list is not merely a checklist; it’s a vital commitment to protecting their assets and ensuring trust with clients and stakeholders. By taking decisive action and leveraging available resources, such as the CMMC Info Hub, defense contractors can transform compliance into a strategic advantage, paving the way for sustained success in an increasingly challenging cybersecurity landscape.
Frequently Asked Questions
What is the CMMC Info Hub and its purpose?
The CMMC Info Hub is a vital resource for organizations seeking to comply with the NIST 800-171 controls list. It provides comprehensive roadmaps, actionable strategies, and peer insights to help defense contractors navigate the cybersecurity landscape and ensure compliance with Department of Defense standards.
How does the CMMC Info Hub assist defense contractors?
The CMMC Info Hub assists defense contractors by offering tailored resources that address unique challenges, streamlining regulatory processes, and enhancing overall cybersecurity posture to meet compliance requirements.
Why is access control important for organizations?
Access control is crucial for protecting sensitive information and achieving CMMC compliance. It restricts access to Controlled Unclassified Information (CUI) to authorized users, processes, and devices, thereby reducing the risk of unauthorized retrieval.
What strategies can organizations implement for effective access control?
Organizations can implement multi-factor authentication (MFA) to enhance security, use role-based access controls to limit access based on responsibilities, and conduct regular audits of access permissions to ensure only authorized personnel can access sensitive data.
What role does employee training play in cybersecurity compliance?
Employee training is essential for compliance with the NIST 800-171 controls list. Ongoing cybersecurity training programs educate employees on identifying phishing attempts, understanding data handling protocols, and adhering to safety policies, thereby reducing the risk of human errors that can lead to data breaches.
What are the benefits of tailored training programs for employees?
Tailored training programs lead to significant improvements in employee engagement and adherence to security protocols. Organizations that prioritize such training can reduce cyberattacks substantially, as evidenced by statistics showing decreased phishing click rates after role-based training and simulations.
How can organizations foster a culture of awareness regarding cybersecurity?
Organizations can foster a culture of awareness by implementing robust training programs that include real-world scenarios and role-specific content, empowering employees to recognize and respond to cyber threats effectively.
What is the financial impact of inadequate permission controls?
Inadequate permission controls have led to significant financial losses, with Business Email Compromise (BEC) losses exceeding $26 billion since 2016, highlighting the importance of effective access control measures.