10 Essential Security Compliance Regulations for Defense Contractors
Discover essential security compliance regulations for defense contractors to enhance cybersecurity.
Introduction
Navigating the complex landscape of security compliance regulations presents a significant challenge for defense contractors, particularly with the Cybersecurity Maturity Model Certification (CMMC) set to be implemented in 2025. This article delves into ten essential regulations that not only protect sensitive information but also bolster competitive positioning within the defense sector. As the stakes continue to rise, organizations face a pressing question: how can they effectively align with these evolving standards to secure contracts and safeguard their operations? By understanding and adhering to these regulations, contractors can not only ensure compliance but also enhance their marketability in a highly competitive environment.
CMMC Info Hub: Your Essential Resource for CMMC Compliance
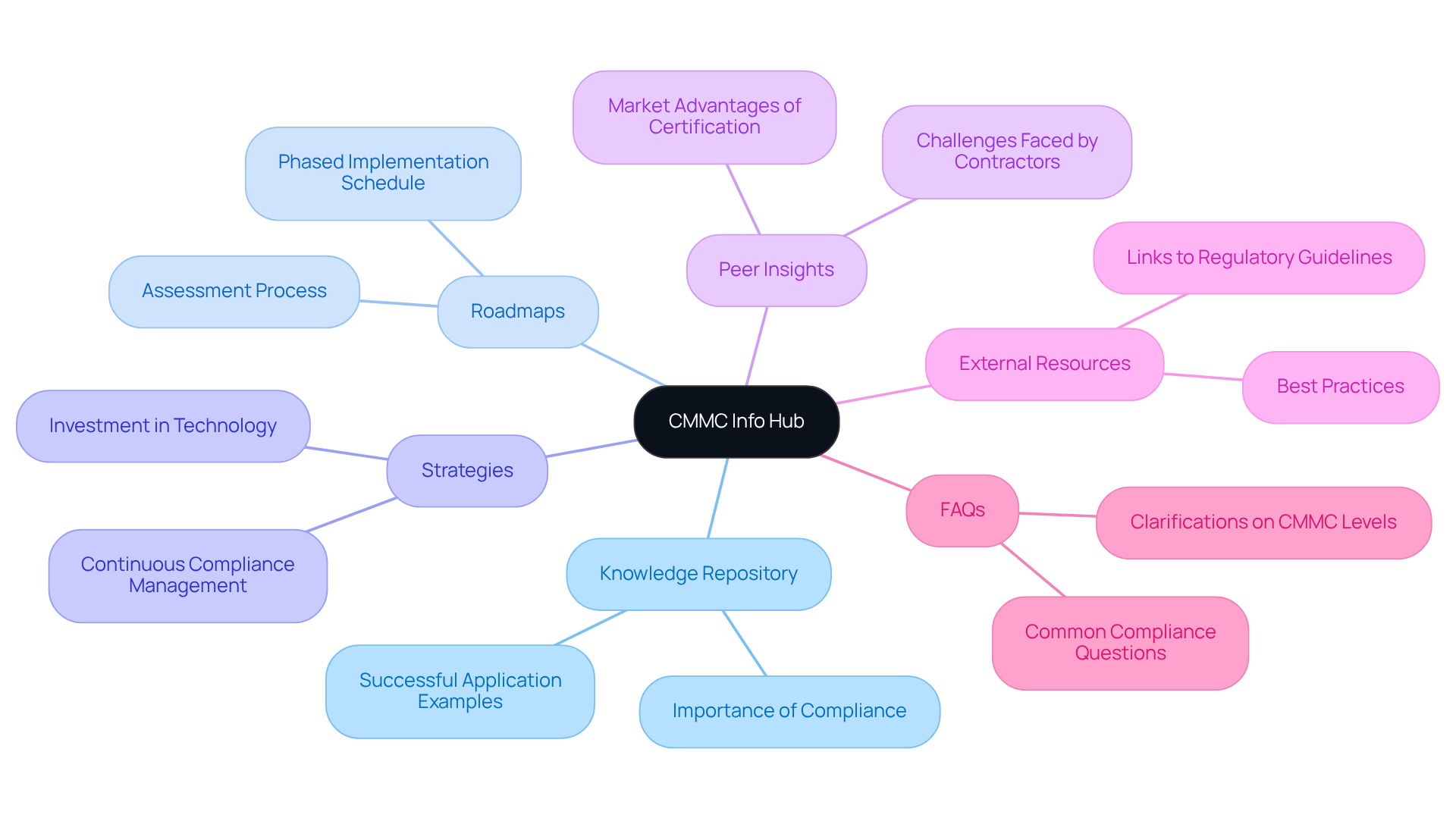
The Info Hub serves as a comprehensive knowledge repository tailored for organizations striving to achieve security compliance regulations, including those outlined in the Cybersecurity Maturity Model Certification (CMMC). It offers detailed roadmaps, practical strategies, and peer insights that empower suppliers to adeptly navigate the complexities of DoD cybersecurity standards. By providing structured support, the Info Hub transforms confusion into clarity, enabling companies to bolster their cybersecurity posture and secure government contracts.
Moreover, the Info Hub features links to external resources and FAQs that further assist professionals in understanding security compliance regulations and the best practices associated with them. Recent updates indicate that adherence to the cybersecurity framework will be crucial for a significant number of contracts, with the program set to impact over 300,000 organizations across various sectors starting November 10, 2025. This underscores the importance of the insights and resources available through the Info Hub for contractors looking to maintain a competitive edge.
Successful organizations have redefined compliance with the cybersecurity framework as a strategic investment, enhancing operational efficiency and positioning themselves favorably in the market. The CMMC Info Hub not only simplifies the compliance process but also highlights successful application examples within the military sector, showcasing how organizations have effectively integrated the relevant standards into their operations.
By leveraging the knowledge and tools provided by the CMMC Info Hub, defense contractors can confidently navigate the evolving compliance landscape, ensuring clarity and preparedness in their cybersecurity efforts.
General Data Protection Regulation (GDPR): Key Data Protection Standards
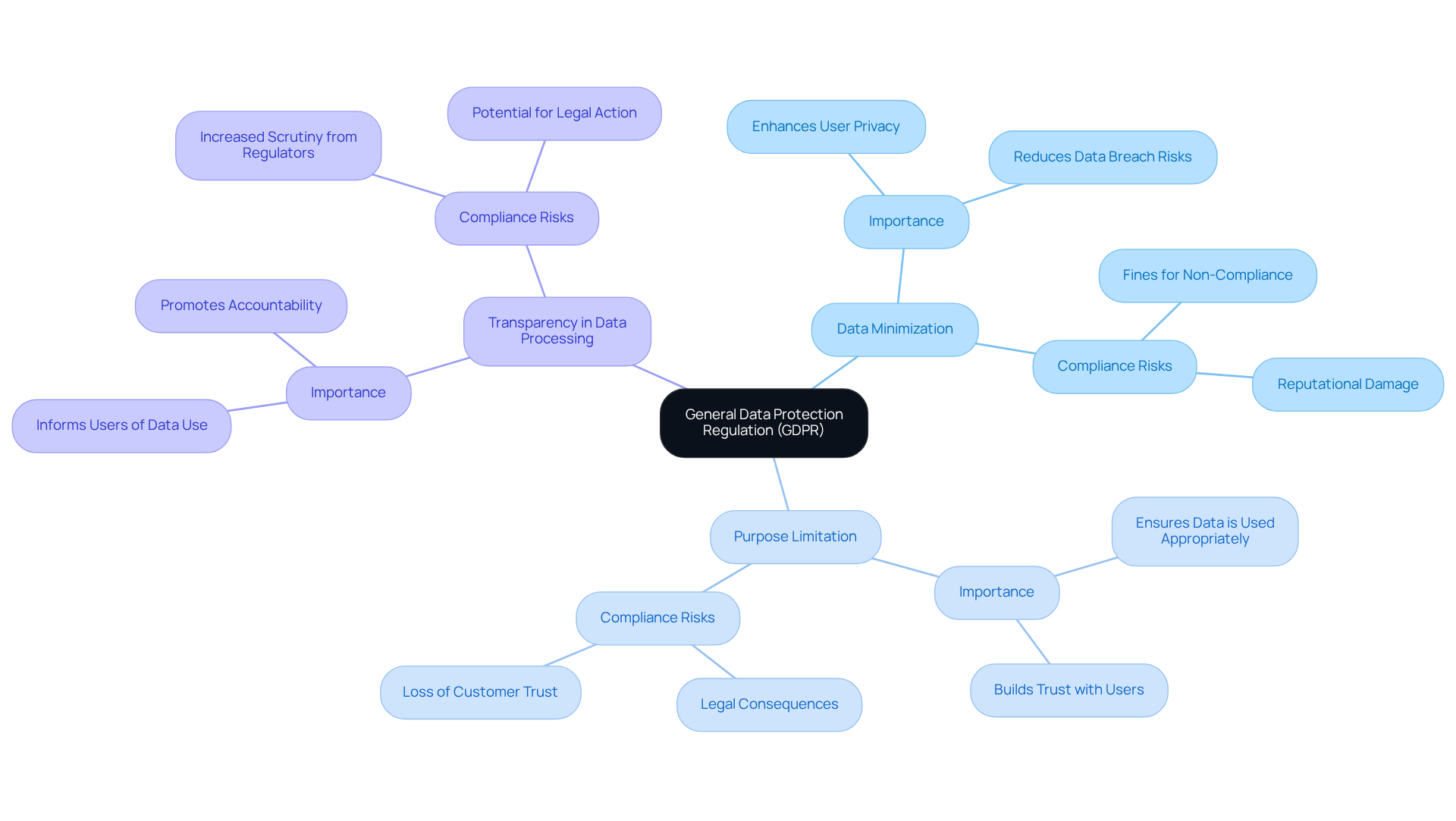
The General Data Protection Regulation (GDPR) sets rigorous data protection standards for organizations handling the personal data of EU citizens. Why is this important? Key principles such as data minimization, purpose limitation, and transparency in data processing are essential for meeting security compliance regulations. Defense providers, in particular, must adopt robust data protection measures to align with security compliance regulations such as GDPR. Non-compliance with security compliance regulations can lead to significant fines and damage to reputation, making it crucial for organizations to take these regulations seriously.
Understanding GDPR is not just a legal obligation; it’s an ethical responsibility for those managing sensitive information in accordance with security compliance regulations. Workers in this field must be well-versed in security compliance regulations to ensure they adhere to both legal and ethical standards. By prioritizing GDPR compliance, organizations can protect themselves and their clients, fostering trust and integrity in their operations. Are you ready to take the necessary steps to ensure compliance?
Health Insurance Portability and Accountability Act (HIPAA): Compliance for Healthcare Projects
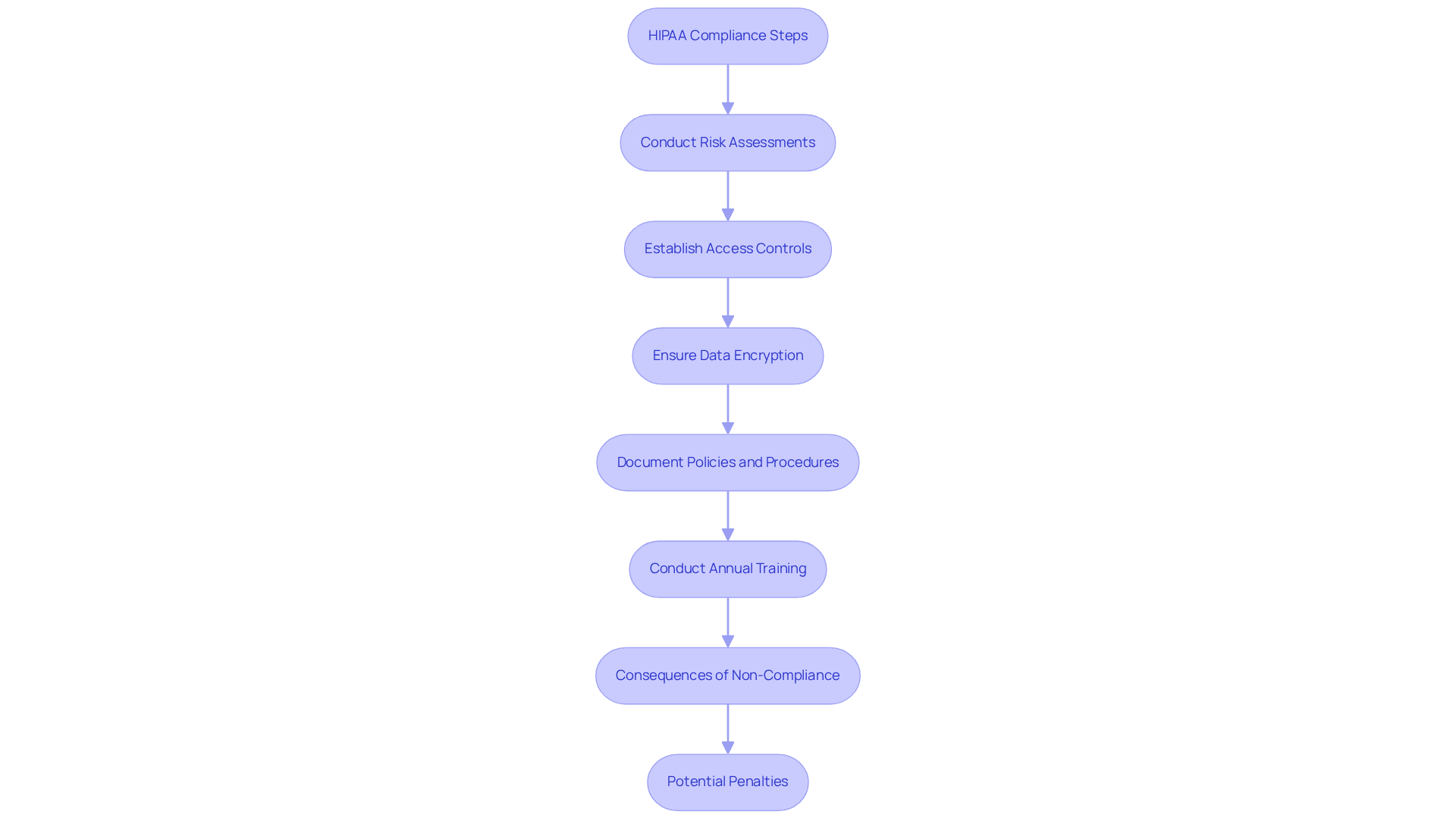
The Health Insurance Portability and Accountability Act (HIPAA) sets forth essential regulations aimed at protecting sensitive patient health information. For defense contractors engaged in healthcare projects, adhering to security compliance regulations, including HIPAA's Privacy and Security Rules, is imperative. These rules require comprehensive safeguards for electronic protected health information (ePHI).
What does this mean for your organization? It means implementing thorough risk assessments, establishing robust access controls, ensuring effective data encryption, and maintaining well-documented policies and procedures. Additionally, organizations must conduct annual HIPAA training for employees to ensure that all staff understand regulatory requirements and best practices.
Consider the consequences of non-compliance: severe penalties can ensue, including fines that may reach millions of dollars. A notable example is Premera Blue Cross, which faced a staggering $6.85 million penalty due to inadequate risk analysis. With civil monetary penalties projected to increase in 2026, prioritizing HIPAA compliance is not just about avoiding financial repercussions; it’s about safeguarding the integrity and security of patient data in your healthcare initiatives.
In summary, the stakes are high. By adhering to security compliance regulations, including HIPAA, you not only protect your organization from potential fines but also contribute to a secure healthcare environment. Are you ready to take the necessary steps to ensure compliance?
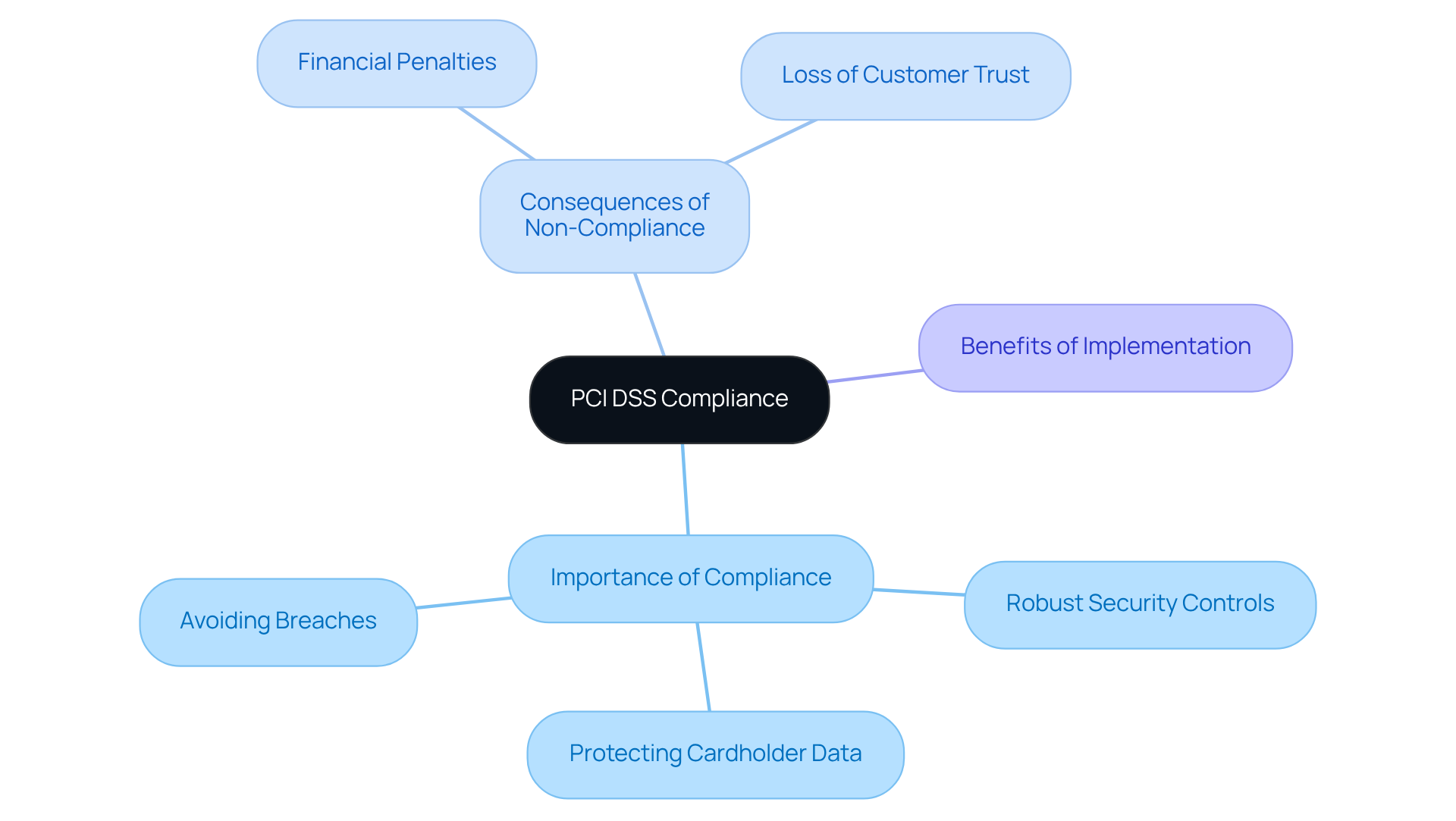
Payment Card Industry Data Security Standard (PCI DSS): Protecting Payment Information
The Payment Card Industry Data Security Standard (PCI DSS) is crucial for organizations handling credit card transactions. Why is compliance so vital? It mandates robust security controls like encryption, access control, and regular security testing. For defense providers processing payment information, adhering to PCI DSS is not just a recommendation; it’s essential for protecting cardholder data and avoiding costly breaches.
Consider this: failure to comply can lead to severe financial penalties and a significant loss of customer trust. According to a study by the Ponemon Institute, over half of customers reportedly lose faith in an organization following a data breach. This statistic underscores the importance of maintaining PCI DSS standards, especially in light of past breaches that have exposed vulnerabilities in payment systems.
To safeguard your organization and your customers, it’s imperative to prioritize security compliance regulations, including PCI DSS compliance. Implementing these standards not only protects sensitive information but also aligns with security compliance regulations, reinforcing your reputation in the marketplace. Are you ready to take action and ensure your organization meets these critical security measures?
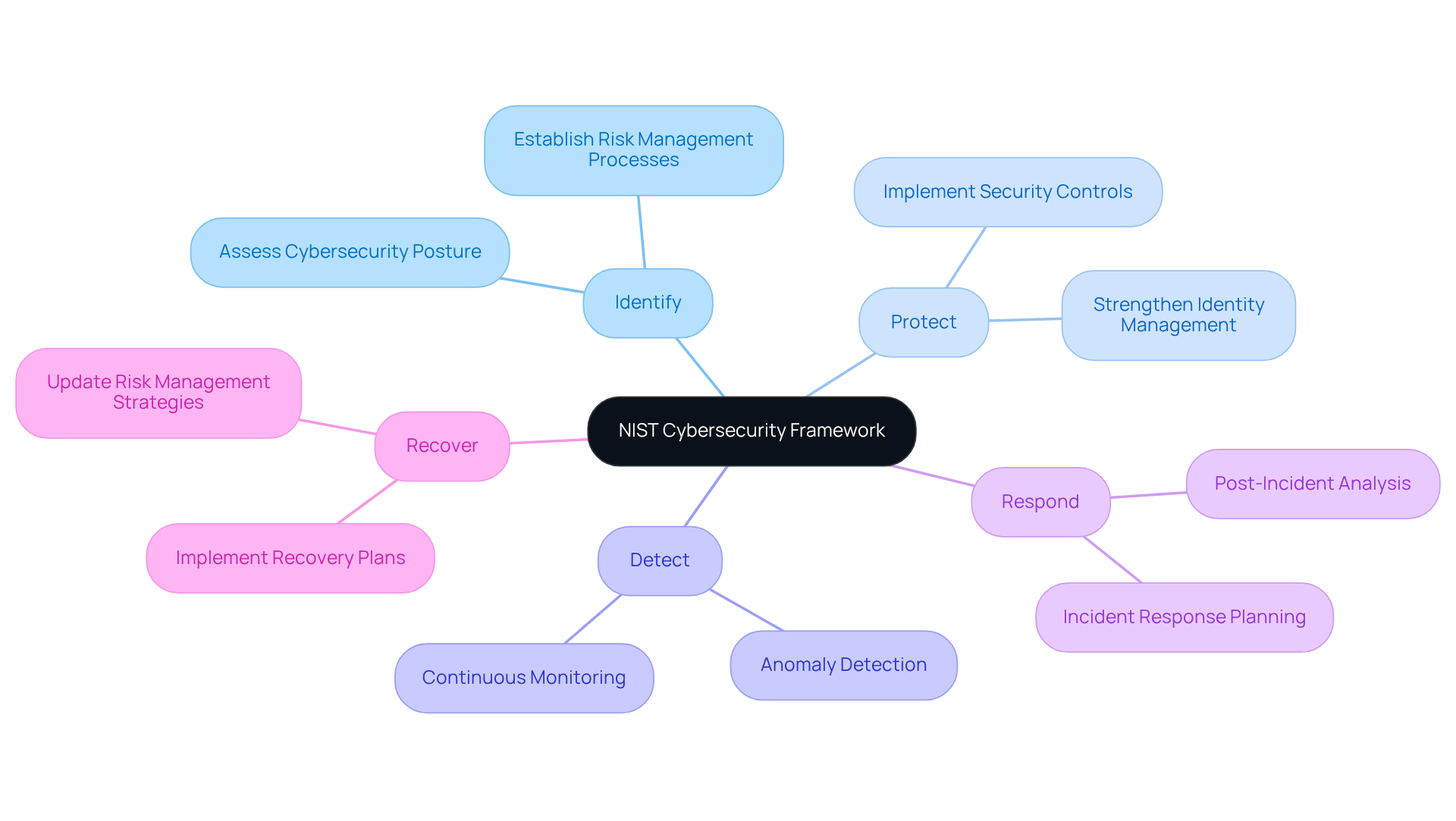
NIST Cybersecurity Framework: Guidelines for Managing Cybersecurity Risks
The NIST Cybersecurity Framework provides a robust methodology for organizations aiming to manage and mitigate cybersecurity risks effectively. It consists of five essential functions:
- Identify
- Protect
- Detect
- Respond
- Recover
How can security providers leverage this framework? By assessing their cybersecurity posture, implementing necessary controls, and fortifying their defenses against evolving cyber threats.
Following NIST guidelines not only ensures adherence to security compliance regulations but also significantly enhances an organization’s overall cybersecurity strategy. For example, organizations that have adopted NIST standards often report improved resilience against attacks. The cybersecurity technology market, projected to reach $185.7 billion in 2024, highlights the increasing significance of these frameworks in protecting sensitive information.
As defense providers navigate the complexities of security compliance regulations, utilizing NIST guidelines can lead to a more secure operational environment and a stronger defense against potential breaches. The CMMC Info Hub offers practical strategies and peer insights to help you achieve CMMC compliance with confidence. Are you ready to transform confusion into clarity as you work towards meeting these vital cybersecurity standards?
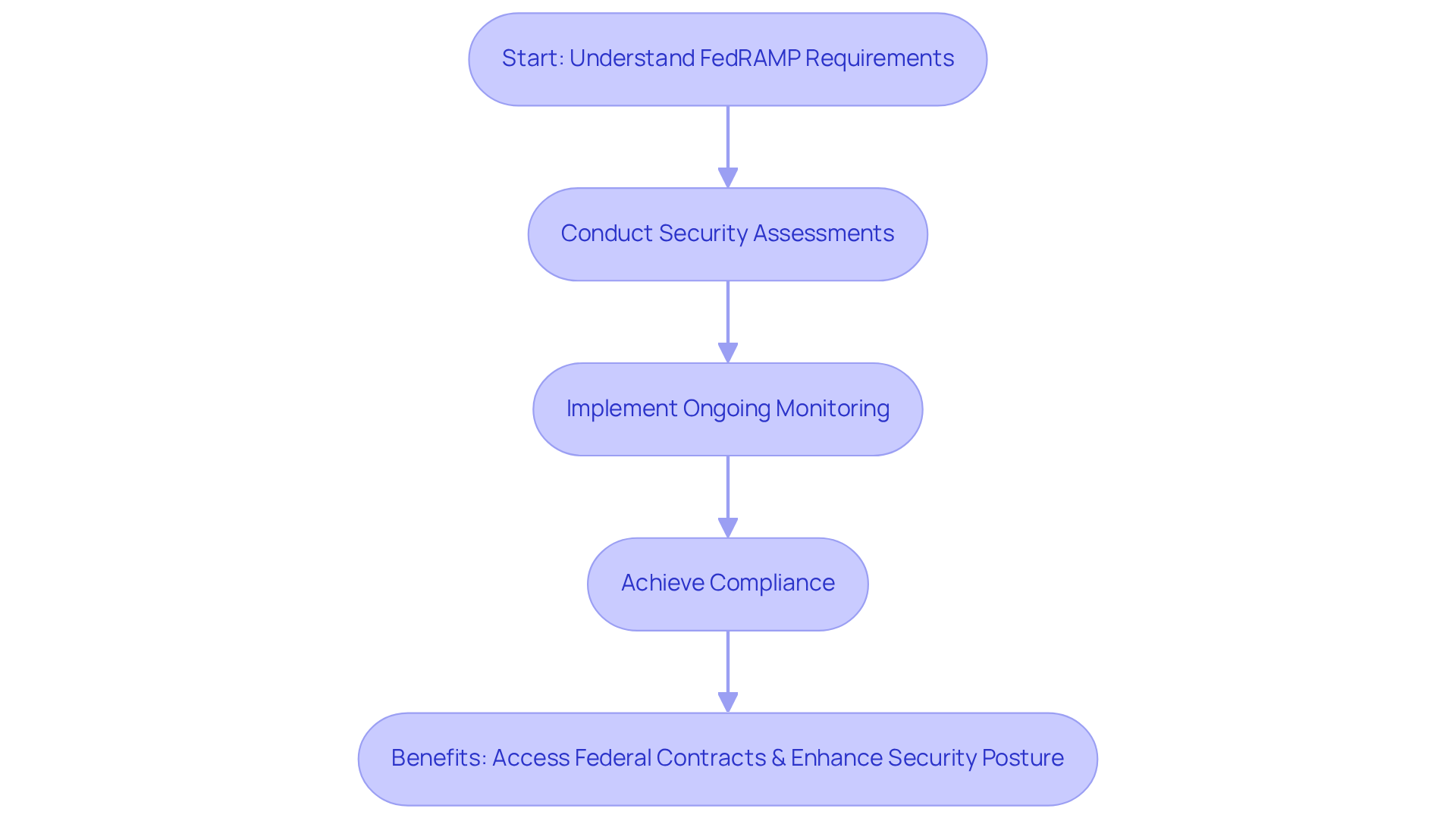
Federal Risk and Authorization Management Program (FedRAMP): Cloud Security Compliance
The Federal Risk and Authorization Management Program (FedRAMP) sets a crucial standard for security assessment and authorization of cloud services utilized by federal agencies. Why is this important? Defense providers must adhere to FedRAMP requirements to ensure that their cloud solutions comply with federal security compliance regulations. This process involves rigorous security assessments and ongoing monitoring of cloud services, ensuring that security remains a top priority.
By adhering to security compliance regulations like FedRAMP, organizations not only gain access to federal contracts but also significantly enhance their overall security posture when leveraging cloud technologies. This dual benefit underscores the necessity of understanding and implementing security compliance regulations, including FedRAMP guidelines. Are you ready to elevate your security measures and seize federal opportunities? Embracing FedRAMP compliance is a strategic move that can lead to greater trust and reliability in your cloud services.
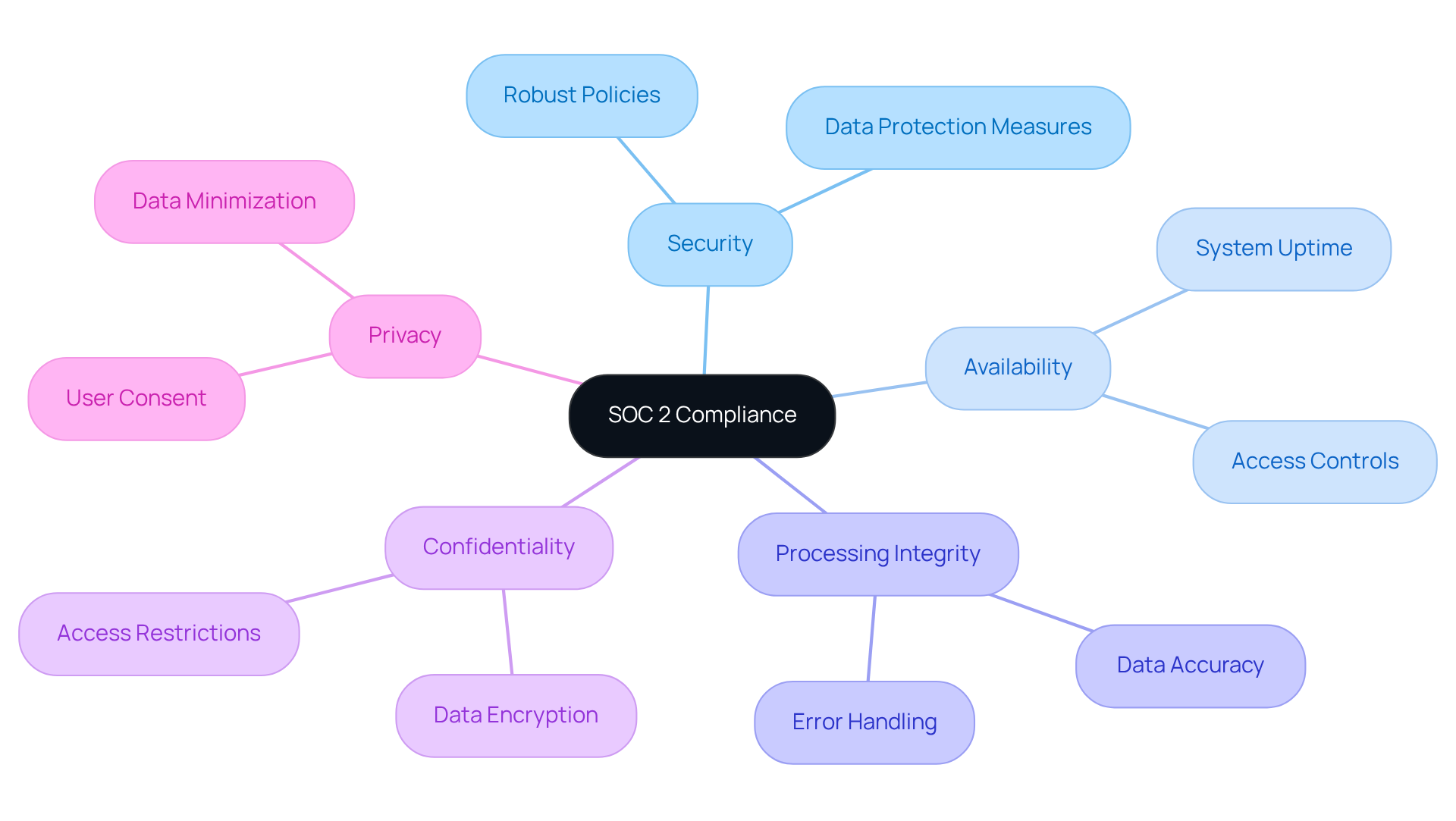
Service Organization Control 2 (SOC 2): Ensuring Data Management Compliance
Service Organization Control 2 (SOC 2) adherence is crucial for organizations that handle customer data, particularly in the defense sector. Why is this framework so important? It emphasizes five Trust Services Criteria:
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
Defense suppliers must establish robust policies and controls that align with these criteria to effectively safeguard sensitive information.
Achieving SOC 2 adherence signifies a strong commitment to data security. It also enhances trust with clients and stakeholders significantly. For instance, numerous security firms have successfully obtained SOC 2 certification, showcasing their dedication to upholding high security standards and building trust with their clients. As cybersecurity threats continue to rise, the importance of SOC 2 compliance in establishing and maintaining client trust cannot be overstated. This makes it a vital consideration for all professionals in the security sector.
In summary, organizations must prioritize SOC 2 compliance not just as a regulatory requirement but as a strategic advantage in fostering trust and credibility while ensuring adherence to security compliance regulations in an increasingly complex cybersecurity landscape.
Cybersecurity Maturity Model Certification (CMMC): Securing Defense Contracts
The Cybersecurity Maturity Model Certification (CMMC) is essential for enhancing the cybersecurity posture of defense suppliers. It sets forth a series of cybersecurity standards that organizations must meet to secure Department of Defense (DoD) contracts. This framework comprises multiple tiers, each with increasingly stringent security requirements. For vendors aiming to bid on DoD contracts, adherence to these standards is not optional; understanding and implementing the necessary measures for certification is crucial.
To assist defense contractors in navigating the complexities of compliance, we encourage you to explore our Frequently Asked Questions (FAQs) section. This resource addresses common concerns and provides valuable insights. Additionally, our platform may feature links to external sites that offer further resources related to CMMC. While we do not control the content of these external sites, they can be instrumental in your compliance journey.
Recent data reveals that organizations that proactively prepare for certification gain a competitive edge, while those that delay face significant challenges. For example, in 2025, only 4% of builders were ready for certification, underscoring a considerable gap between awareness and action. Successful contractors began their preparations early, viewing adherence to the CMMC as an ongoing program rather than a last-minute task. This strategic approach not only positions them favorably in the market but also helps mitigate risks associated with regulatory failures by ensuring compliance with security compliance regulations.
Moreover, the impact of the CMMC on contract bidding success cannot be overstated. As the final regulation mandates this framework as a contractual obligation, vendors must demonstrate adherence to security compliance regulations before contract awards and maintain it throughout the contract's duration. This shift transforms cybersecurity from a technical issue into a fundamental legal requirement, making it imperative for contractors to integrate CMMC standards into their operational frameworks.
In conclusion, CMMC is not merely a regulatory hurdle; it is a critical component of security compliance regulations for securing military contracts and safeguarding sensitive information. Organizations that embrace this framework will not only enhance their compliance posture but also strengthen their competitive position within the defense industrial base.
Defense Federal Acquisition Regulation Supplement (DFARS): Cybersecurity Requirements
The Defense Federal Acquisition Regulation Supplement (DFARS) imposes specific cybersecurity obligations on military suppliers to protect Controlled Unclassified Information (CUI). Are you aware of the critical DFARS clauses that contractors must adhere to? These include essential requirements for incident reporting and the safeguarding of sensitive information. Non-compliance can lead to severe consequences, including the potential loss of contracts.
Understanding and following security compliance regulations, including DFARS requirements, is not just a regulatory necessity; it’s crucial for military suppliers aiming to maintain eligibility for federal agreements. By ensuring security compliance regulations, you not only protect sensitive information but also secure your position in a competitive landscape.
Take action now: familiarize yourself with DFARS clauses and implement the necessary measures to safeguard your operations. The stakes are high, and the resources available can guide you through this complex landscape.
ISO 27001: Framework for Information Security Management
ISO 27001 stands as a globally recognized standard that outlines the requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). For security providers, obtaining ISO 27001 certification signals a strong commitment to securely managing sensitive information. This compliance process necessitates thorough risk assessments, the implementation of essential security controls, and ongoing monitoring and enhancement of the ISMS to adhere to security compliance regulations.
By adhering to ISO 27001, organizations not only strengthen their security posture but also foster trust among clients and stakeholders. This reinforces the idea that cybersecurity is a business imperative, not just an IT concern. As Katherine Neville aptly stated, "Cybersecurity is much more than a matter of IT-it’s a business imperative."
Moreover, security providers that have successfully adopted ISO 27001 standards report significant improvements in their information security management. This illustrates the standard's effectiveness in mitigating risks and enhancing overall security resilience. To further bolster their security framework, defense contractors should consider integrating a layered defense strategy, as emphasized by James Scott. This approach ensures comprehensive protection against a variety of threats.
In conclusion, embracing ISO 27001 is not merely a compliance measure; it is a strategic move that enhances security and aligns with security compliance regulations while building trust. Are you ready to take the next step in securing your organization?
Conclusion
The landscape of security compliance regulations for defense contractors is both critical and complex, particularly as the industry prepares for the implementation of the Cybersecurity Maturity Model Certification (CMMC) in 2025. Adhering to these regulations isn’t just a legal obligation; it’s a strategic necessity that empowers organizations to secure government contracts and protect sensitive information. By prioritizing compliance, defense contractors can enhance their operational efficiency and solidify their competitive edge in a challenging market.
Key security compliance regulations such as:
- GDPR
- HIPAA
- PCI DSS
- NIST Cybersecurity Framework
are essential for safeguarding data and ensuring organizational resilience. Each regulation presents unique requirements and implications for defense contractors, underscoring the need for a comprehensive understanding and proactive measures. Non-compliance can lead to significant financial penalties and reputational damage, making it imperative for organizations to stay informed and prepared.
In this rapidly evolving regulatory environment, the call to action is clear: defense contractors must take decisive steps to embrace these compliance frameworks. By leveraging resources like the CMMC Info Hub and staying updated on the latest developments in security compliance regulations, organizations can navigate this complex landscape with confidence. Ultimately, a commitment to security compliance will not only protect sensitive information but also foster trust, integrity, and a robust operational framework crucial for future success.
Frequently Asked Questions
What is the CMMC Info Hub?
The CMMC Info Hub is a comprehensive knowledge repository designed for organizations aiming to achieve compliance with the Cybersecurity Maturity Model Certification (CMMC) and other security regulations. It provides roadmaps, strategies, and peer insights to help suppliers navigate DoD cybersecurity standards.
How does the CMMC Info Hub assist organizations?
The Info Hub offers structured support, transforming confusion into clarity, which enables companies to improve their cybersecurity posture and secure government contracts. It also includes external resources and FAQs for better understanding of security compliance regulations.
Why is CMMC compliance important?
CMMC compliance is crucial for securing government contracts, as adherence to the cybersecurity framework will impact over 300,000 organizations starting November 10, 2025. It is seen as a strategic investment that enhances operational efficiency and market positioning.
What role does GDPR play in data protection?
The General Data Protection Regulation (GDPR) establishes strict data protection standards for organizations handling personal data of EU citizens, emphasizing principles like data minimization, purpose limitation, and transparency in data processing.
Why must defense providers comply with GDPR?
Defense providers must adopt robust data protection measures to align with GDPR and other security compliance regulations, as non-compliance can lead to substantial fines and reputational damage.
What does HIPAA regulate?
The Health Insurance Portability and Accountability Act (HIPAA) regulates the protection of sensitive patient health information, requiring defense contractors in healthcare to adhere to its Privacy and Security Rules.
What are the key requirements for HIPAA compliance?
Key requirements include conducting risk assessments, implementing access controls, ensuring data encryption, and maintaining documented policies and procedures. Annual HIPAA training for employees is also essential.
What are the consequences of non-compliance with HIPAA?
Non-compliance can lead to severe penalties, including fines that can reach millions of dollars. For example, Premera Blue Cross faced a $6.85 million penalty due to inadequate risk analysis.
Why is prioritizing compliance with security regulations important?
Prioritizing compliance protects organizations from potential fines and contributes to a secure environment for sensitive data, particularly in healthcare initiatives. It is both a legal obligation and an ethical responsibility.




