10 Essential Steps for Your CMMC Level 1 Checklist
Master the CMMC Level 1 checklist with essential steps for compliance and cybersecurity success.

Introduction
Navigating the complex landscape of Department of Defense (DoD) cybersecurity requirements can be a significant challenge for organizations aiming to achieve CMMC Level 1 compliance. This essential checklist serves not only as a roadmap for meeting stringent standards but also opens doors to lucrative defense contracts. Yet, with only a small percentage of contractors fully prepared for compliance audits, a pressing question arises: how can organizations effectively implement the necessary steps to secure their operations and thrive in a competitive environment?
This article outlines ten crucial steps that will empower organizations to master the CMMC Level 1 checklist, enhance their cybersecurity posture, and ensure they are well-equipped for future challenges. By following these steps, organizations can not only meet compliance requirements but also position themselves for success in the defense sector.
CMMC Info Hub: Your Comprehensive Resource for CMMC Level 1 Compliance
CMMC Info Hub serves as a vital resource for organizations aiming to complete the CMMC Level 1 checklist. Are you navigating the complexities of DoD cybersecurity requirements? This platform provides detailed roadmaps, practical strategies, and informative articles designed to simplify these challenges. By leveraging peer insights and expert advice, users can confidently maneuver through the regulatory landscape, ensuring they meet the stringent standards necessary for securing defense contracts.
Why is compliance crucial? Meeting CMMC standards not only enhances your cybersecurity posture but also opens doors to lucrative defense contracts. With the right tools and knowledge, your organization can thrive in this competitive environment.
Take action today. Explore the resources available on CMMC Info Hub and equip your organization with the insights needed to succeed in achieving compliance with the CMMC Level 1 checklist.
Understand CMMC Level 1 Requirements and Standards
The CMMC Level 1 checklist establishes essential protection measures for Federal Contract Information (FCI), mandating that entities implement 15 specific practices outlined in FAR Clause 52.204-21. These practices are part of the CMMC Level 1 checklist and cover critical areas such as:
- Access control
- Identification and authentication
- Media protection
- Physical protection
Mastering these requirements is not just beneficial; it’s vital for entities looking to build a robust regulatory foundation.
Are you aware of how these practices can safeguard your operations? For those seeking to deepen their understanding, additional resources, including FAQs related to Level 1 adherence, are available through the provided external links. This information can significantly aid entities in navigating the regulatory landscape more effectively.
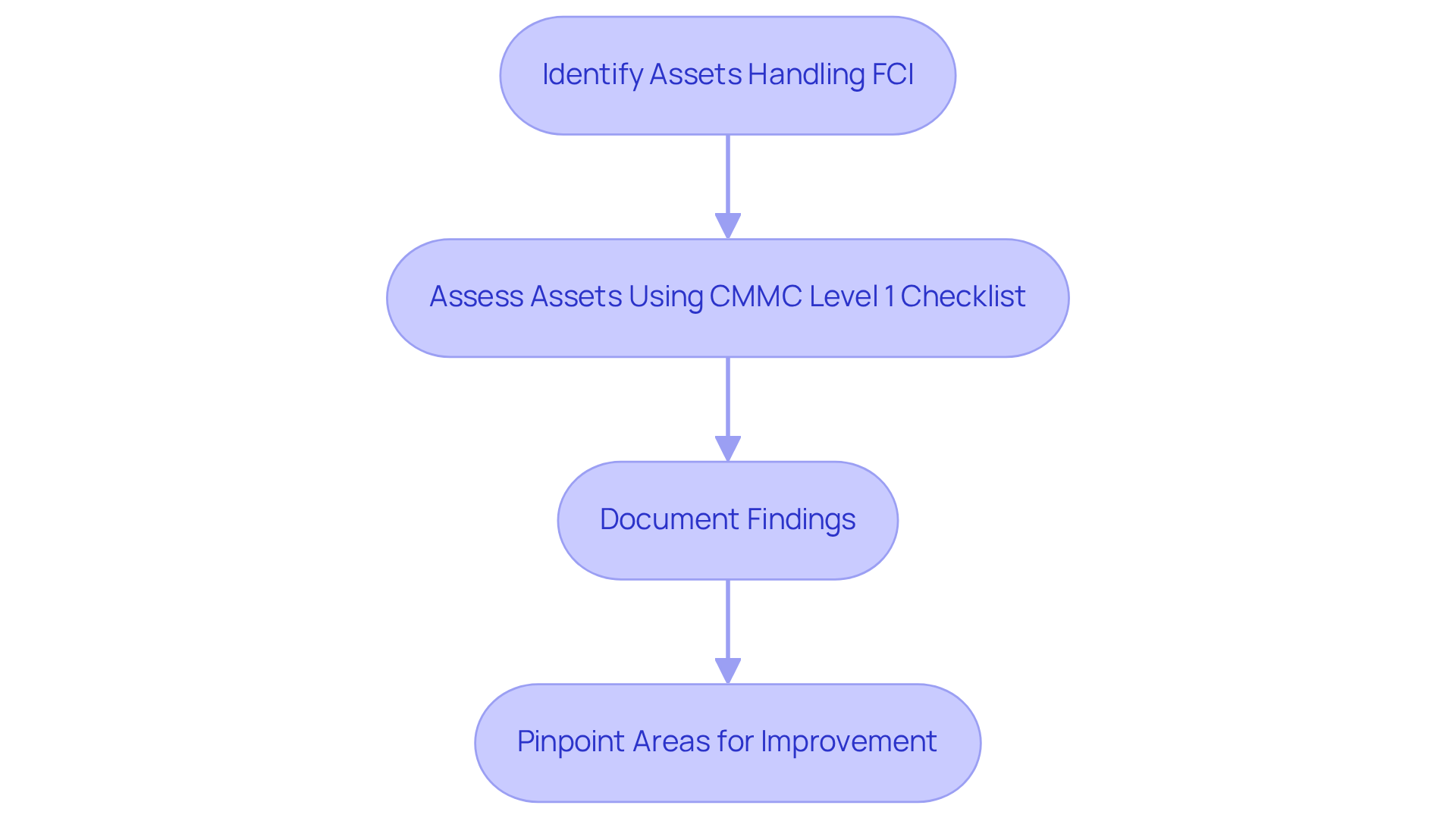
Conduct a Comprehensive Self-Assessment of Current Practices
To achieve compliance with the CMMC Level 1 checklist, organizations must conduct a comprehensive self-evaluation of their current cybersecurity practices. Have you identified all assets that handle, store, or transmit Federal Contract Information (FCI)? This crucial first step involves assessing these assets using the CMMC Level 1 checklist against the 15 required practices. By leveraging specialized tools and templates, you can streamline this assessment process, effectively documenting your findings and pinpointing areas that need improvement.
Cybersecurity experts emphasize that a thorough review not only helps meet regulatory requirements but also strengthens your overall security posture. This proactive approach ensures that your organization is well-prepared for future evaluations and contract opportunities. Remember, the time to act is now-don’t wait until it’s too late to enhance your cybersecurity measures.
Implement Required Security Controls for Compliance
To achieve CMMC Level 1 certification, one must follow the CMMC Level 1 checklist that includes 15 essential security controls. These key measures include:
- Restricting access to authorized users
- Ensuring robust authentication processes
- Safeguarding sensitive media
But how can organizations navigate this complex landscape? By devising a structured plan that incorporates practical strategies and peer insights, entities can systematically integrate these controls into their daily operations while continuously monitoring their effectiveness.
This proactive approach not only meets regulatory demands but also fortifies the entity's overall security posture. Security experts emphasize that effective access control measures are crucial for managing risks and protecting sensitive information. This highlights the importance of embedding these practices into the organizational culture.
As a practical suggestion, organizations should regularly assess and revise their access control policies. This ensures they adapt to evolving threats and maintain compliance. By taking these steps, entities can comply with the CMMC Level 1 checklist and enhance their security framework, ultimately safeguarding their critical assets.
Train Employees on CMMC Compliance and Cybersecurity Best Practices
Organizations must prioritize training their employees on cybersecurity standards and best practices. Why? Because safeguarding Federal Contract Information (FCI) is crucial in today’s digital landscape. Educating staff on the importance of this protection, recognizing potential threats, and adhering to established security protocols is not just beneficial; it’s essential.
Frequent training sessions and awareness initiatives play a vital role in fostering a security culture within the organization. These efforts minimize the likelihood of human mistakes and significantly improve adherence to security measures. Consider this: organizations that invest in regular cybersecurity training see a marked decrease in security breaches.
To truly enhance your organization’s security posture, make training a priority. Implementing a structured training program can lead to a more informed workforce, ready to tackle the challenges of cybersecurity head-on. Don’t wait-start building a robust security culture today.
Document Policies and Procedures Aligned with CMMC Level 1
Organizations must develop and document policies and procedures that are in accordance with the CMMC Level 1 checklist requirements. Why is this crucial? Because clear documentation not only facilitates compliance but also serves as a vital reference for employees, promoting consistent adherence to security measures. In fact, organizations with documented security policies are significantly better positioned to mitigate risks. This is due to the fact that clear documentation enhances understanding and execution of protection protocols. Well-organized documentation is essential for fostering a culture of security awareness, ensuring that all team members are aligned with the entity's cybersecurity objectives.
To maintain the effectiveness of these policies, organizations should implement essential practices for policy maintenance:
- Conduct annual reviews to ensure policies remain current.
- Establish a formal process for proposing and approving changes.
- Maintain version control of policies.
- Archive previous versions.
- Communicate any changes to all affected personnel.
With only 1% of Defense Industrial Base contractors fully ready for compliance audits, the necessity for thorough documentation becomes evident. Attaining these standards is intricate and resource-demanding, necessitating continuous dedication to retain eligibility for DoD contracts. Are you ready to take the necessary steps to ensure your organization meets these critical requirements?
Monitor and Audit Compliance Efforts Regularly
Organizations must establish a structured process for tracking and reviewing their adherence efforts to effectively meet the CMMC Level 1 checklist. This involves conducting regular reviews of security controls and assessing the effectiveness of implemented measures. Did you know that 44% of risk and governance experts position their programs in the lowest three maturity tiers? Furthermore, 87% of entities report adverse results stemming from low maturity. This highlights the critical need for consistent oversight.
By identifying gaps in regulations early, entities can address issues proactively, ensuring ongoing adherence to the CMMC Level 1 checklist. Cybersecurity specialists emphasize that frequent evaluations not only boost adherence but also strengthen an organization’s overall security stance. Research indicates that regular adherence audits saved companies an average of $2.86 million. Therefore, it is essential for organizations to prioritize these practices.
For further information and answers to common questions about CMMC compliance, please refer to our FAQs and external resources linked throughout this platform.
Establish an Incident Response Plan for Cybersecurity Events
Organizations must establish a comprehensive incident response plan that clearly defines procedures for detecting, responding to, and recovering from cybersecurity incidents. This plan should delineate specific roles and responsibilities, outline communication protocols, and detail steps for documenting incidents.
Notably, only 55% of companies have a fully documented incident response plan. This statistic highlights a significant gap in preparedness that organizations cannot afford to overlook. Regular testing and updates to the incident response plan are essential; entities that perform such testing at least twice annually can save an average of $1.49 million per breach.
As compliance with the CMMC framework becomes increasingly stringent, aligning incident response plans with NIST SP 800-171 controls is crucial. This alignment not only improves adherence but also bolsters overall digital security resilience. It allows entities to react effectively to incidents and protect sensitive information.
By adhering to the comprehensive manual for attaining necessary standards, organizations can guarantee their incident response strategies are strong and efficient. Ultimately, this approach secures defense contracts and enhances their security stance.
Engage Third-Party Assessors for Compliance Validation
Organizations can significantly enhance their compliance efforts by involving third-party assessors to verify adherence to the CMMC Level 1 checklist requirements. These independent evaluators provide an unbiased assessment of security practices, helping to identify gaps and offering tailored recommendations for improvement. By collaborating with a trusted external evaluator, organizations not only boost their credibility but also ensure that their compliance efforts align with industry standards.
Why rely solely on internal assessments when an objective perspective can reveal hidden vulnerabilities? Engaging with external experts can illuminate areas for enhancement that may otherwise go unnoticed. This proactive approach not only strengthens security measures but also fosters a culture of continuous improvement.
In conclusion, leveraging third-party assessors is a strategic move that can lead to more robust compliance with the CMMC Level 1 checklist. Organizations should consider this valuable resource to ensure they are not just meeting requirements but exceeding them.
Commit to Continuous Improvement in Cybersecurity Practices
Organizations must embrace a culture of ongoing enhancement in their security practices to effectively navigate the challenges posed by regulatory standards. This commitment involves regularly reviewing and updating security measures, integrating feedback from audits and assessments, and staying alert to emerging threats and best practices, particularly those associated with generative AI. By fostering this proactive mindset, organizations can significantly bolster their resilience against cyber threats.
Why is this important? The stakes are high. The average cost of a data breach in healthcare reached a staggering $10.93 million in 2023. This underscores the necessity for organizations to adopt proactive measures. Ongoing enhancement not only strengthens adherence to the CMMC Level 1 checklist but also equips entities to swiftly adapt to the ever-evolving digital security landscape.
Moreover, organizations that prioritize continuous feedback mechanisms are better positioned to identify vulnerabilities and refine their strategies. This ultimately leads to a more robust cybersecurity posture. Implementing strong identity controls and auditing cloud persistence are crucial steps in enhancing security.
Additionally, public-private collaboration plays a vital role in fortifying digital infrastructure against cyber threats. By working together, stakeholders can create a more secure environment for all.
In conclusion, the path to effective cybersecurity is clear: adopt a culture of ongoing enhancement, prioritize feedback, and collaborate across sectors. The time to act is now.
Conclusion
Achieving compliance with the CMMC Level 1 checklist is not just a regulatory requirement; it’s a crucial step for organizations looking to secure defense contracts and bolster their cybersecurity posture. Are you ready to navigate the complexities of DoD cybersecurity requirements with confidence? By understanding the requirements, implementing necessary security controls, and fostering a culture of continuous improvement, your organization can enhance its defenses effectively.
In this article, we’ve outlined essential steps for CMMC Level 1 compliance. These include:
- Conducting comprehensive self-assessments
- Documenting policies
- Training employees
- Engaging third-party assessors for validation
Each of these actions is vital in establishing a robust security framework that not only meets regulatory standards but also fortifies your organization against potential cyber threats.
The significance of these practices cannot be overstated. Organizations must prioritize their cybersecurity efforts, invest in employee training, and commit to the ongoing enhancement of their security measures. By doing so, you not only ensure compliance with the CMMC Level 1 checklist but also build a resilient defense against the ever-evolving landscape of cyber threats. Taking decisive action today will pave the way for a more secure and compliant future. Don’t wait-start implementing these strategies now to protect your organization.
Frequently Asked Questions
What is the CMMC Info Hub?
The CMMC Info Hub is a resource platform designed to help organizations complete the CMMC Level 1 checklist, providing detailed roadmaps, practical strategies, and informative articles to navigate DoD cybersecurity requirements.
Why is compliance with CMMC standards important?
Compliance with CMMC standards enhances an organization's cybersecurity posture and opens doors to lucrative defense contracts, making it essential for success in the competitive environment of defense contracting.
What are the main requirements of the CMMC Level 1 checklist?
The CMMC Level 1 checklist includes 15 specific practices outlined in FAR Clause 52.204-21, covering critical areas such as access control, identification and authentication, media protection, and physical protection.
How can organizations prepare for CMMC Level 1 compliance?
Organizations can prepare by conducting a comprehensive self-assessment of their current cybersecurity practices, identifying assets that handle, store, or transmit Federal Contract Information (FCI), and using specialized tools and templates for evaluation.
What benefits does a thorough self-assessment provide?
A thorough self-assessment helps meet regulatory requirements, strengthens the overall security posture of the organization, and prepares it for future evaluations and contract opportunities.
Where can additional resources for CMMC Level 1 compliance be found?
Additional resources, including FAQs related to Level 1 adherence, can be accessed through external links provided on the CMMC Info Hub, aiding in the navigation of the regulatory landscape.




