10 Key Insights on Encryption HIPAA for Defense Contractors
Insights on encryption HIPAA for defense contractors to enhance security and ensure compliance.

Introduction
Encryption stands as a cornerstone of data security, particularly for defense contractors grappling with the complexities of HIPAA compliance. With the deadline of December 31, 2025, fast approaching, it’s crucial for organizations to understand the essential insights surrounding encryption standards to protect electronic Protected Health Information (ePHI). As the stakes escalate, one pressing question arises: are defense contractors truly prepared to implement these vital encryption practices? What strategies can they adopt to sidestep the severe penalties associated with non-compliance? This article explores ten key insights designed to equip organizations with the knowledge necessary to bolster their encryption efforts and effectively safeguard sensitive information.
CMMC Info Hub: Your Resource for HIPAA Encryption Compliance
CMMC Info Hub serves as an essential resource for defense contractors striving to understand and implement data protection standards, including encryption HIPAA. With recent updates mandating the protection of electronic Protected Health Information (ePHI) both at rest and in transit, this platform provides structured guidance and practical strategies for defense contractors on encryption HIPAA. It simplifies the complexities of compliance, enabling organizations to secure sensitive information effectively and meet the stringent standards set by the Department of Defense.
As of December 31, 2025, organizations must comply with these new security protocols, which include the use of AES-256 for information at rest and TLS 1.3 for information in transit. Non-compliance could lead to increased penalties starting January 2026. Cybersecurity experts emphasize the urgency of this matter: "Covered entities and business associates must heed the Security Rule and harden their infrastructure immediately." This statement underscores the critical need for defense contractors to enhance their cybersecurity posture without delay.
Are you prepared to meet these requirements? By leveraging the resources available through CMMC Info Hub, you can ensure compliance and protect your organization from potential penalties. Act now to safeguard your sensitive information and maintain your standing in the defense sector.
Understand HIPAA Data at Rest Encryption Requirements
Under HIPAA, information at rest encompasses any electronic protected health information (ePHI) stored on devices or servers. The revised regulations mandate that this information be secured using strong cryptographic standards, particularly AES-256. Why is this important? AES-256 is recognized for its strength and effectiveness in safeguarding sensitive information, rendering it unreadable to unauthorized users.
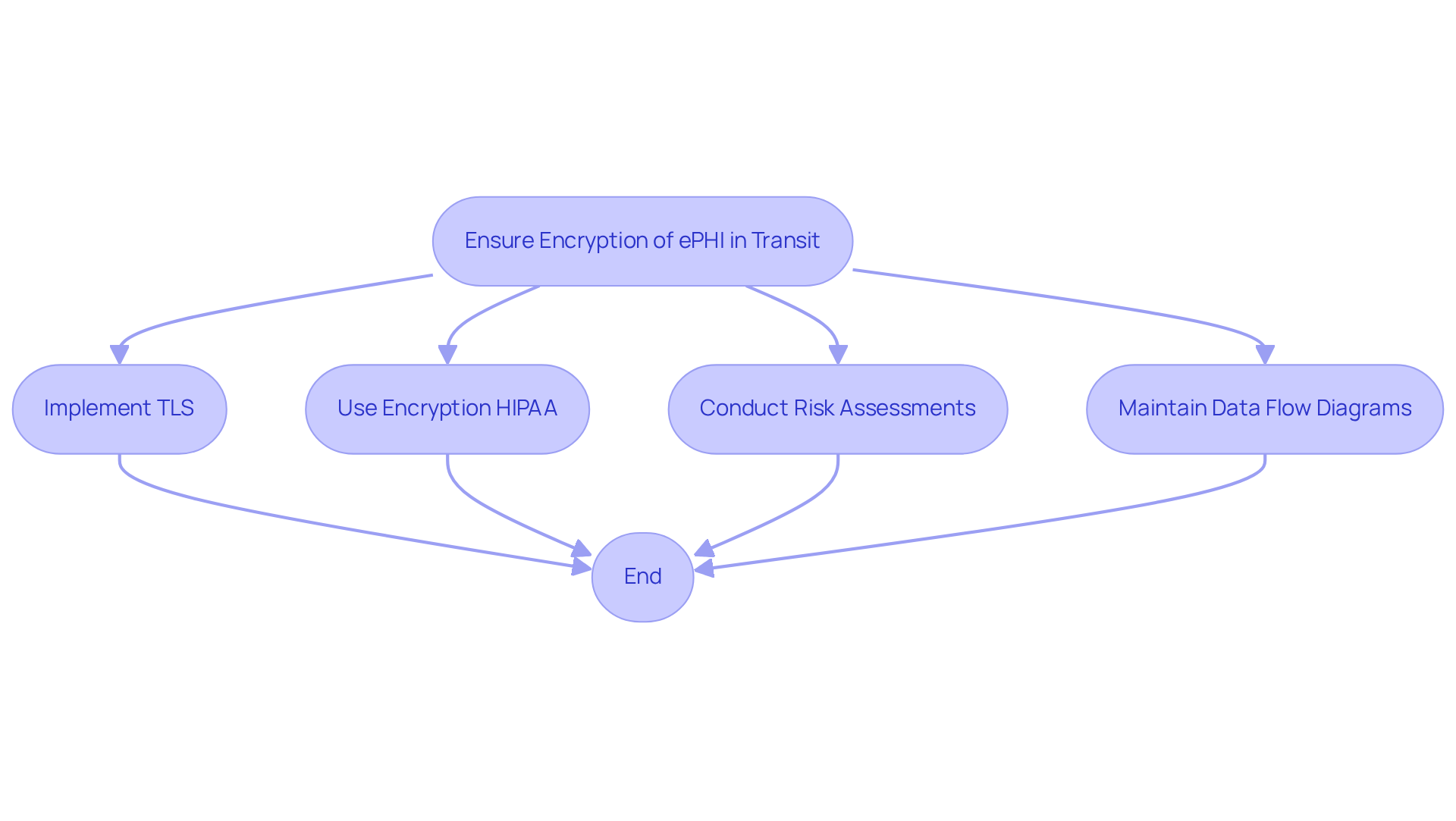
Organizations have until December 31, 2025, to adopt these new data protection standards, reflecting a significant commitment to data security. According to recent reports, around 50% of entities have fully adopted AES-256 coding for HIPAA compliance. This showcases industry leadership in adherence and security. The mandate for robust data protection is not merely a regulatory formality; it is essential for preventing breaches and ensuring that organizations meet HIPAA's stringent requirements.
Consider this: the average cost of a healthcare breach is estimated at $7.13 million. This figure underscores the financial implications of non-compliance. Organizations are encouraged to conduct a gap analysis regarding their current encryption HIPAA practices to ensure they meet these critical standards. Taking action now can safeguard not only sensitive data but also the financial health of your organization.
Ensure Encryption of ePHI in Transit
Using encryption HIPAA to protect electronic Protected Health Information (ePHI) in transit is essential for safeguarding sensitive information as it moves across networks. HIPAA mandates the use of secure transmission protocols, including encryption HIPAA and Transport Layer Security (TLS), to ensure that ePHI remains confidential and protected from unauthorized access. By implementing TLS, organizations can effectively use encryption HIPAA to encrypt information during transfer, significantly reducing the risk of interception and potential breaches.
This proactive strategy aligns with regulatory requirements and strengthens the overall security posture of healthcare organizations. Cybersecurity specialists emphasize that such protective measures are crucial for preserving the integrity of patient information and mitigating risks associated with information transmission. As the landscape of HIPAA compliance evolves, entities must prioritize encryption HIPAA practices to meet regulatory standards and protect sensitive health information.
Looking ahead, the forthcoming 2026 HIPAA modifications will make the protection of ePHI during transmission and storage mandatory. This underscores the necessity for organizations to enhance their compliance efforts. To achieve this, maintaining detailed data flow diagrams and conducting ongoing risk assessments will be essential components of a robust compliance strategy. Are you prepared to take the necessary steps to safeguard your patients' information?
Comprehend HIPAA Encryption Standards
The encryption HIPAA security standards are crucial for safeguarding electronic Protected Health Information (ePHI) from unauthorized access. Organizations must adopt secure coding techniques that align with NIST guidelines, specifically AES-128, AES-192, and AES-256. These standards not only ensure that ePHI is adequately protected through encryption HIPAA but also significantly reduce the risk of data breaches, thereby promoting compliance with HIPAA regulations.
As we approach 2026, a growing number of companies are implementing NIST cryptography standards, recognizing their importance in developing robust cryptographic strategies. Why is this understanding vital for organizations? Enhancing cybersecurity posture and maintaining compliance are paramount in today’s digital landscape. Non-compliance with HIPAA regulations regarding encryption HIPAA can lead to severe penalties, making it imperative for defense contractors to prioritize these security measures.
Compliance specialists emphasize that adopting AES coding not only meets regulatory requirements but also builds trust with clients and stakeholders. By taking proactive steps towards compliance, organizations can foster a secure environment that benefits everyone involved. Are you ready to prioritize these essential security techniques?
Recognize the Benefits of HIPAA Compliant Encryption
Adopting HIPAA-compliant coding brings significant advantages, particularly in enhancing security and reducing the risk of breaches. By using encryption HIPAA to encrypt electronic protected health information (ePHI), organizations can effectively protect sensitive data from unauthorized access, thereby minimizing the potential for costly data breaches. In fact, entities that implement robust data protection measures have reported a notable decrease in breach incidents, underscoring the critical importance of data security in meeting HIPAA standards.
Moreover, following these security protocols not only lowers the risk of hefty fines but also boosts an organization’s reputation. A recent survey revealed that 71% of healthcare entities practice encryption HIPAA to secure patient information, showcasing a growing commitment to information security. This proactive stance fosters greater trust among patients, who are more inclined to engage with healthcare providers that prioritize the safeguarding of their sensitive information.
As of 2026, protecting data at rest has become mandatory, alongside safeguarding data in transit, highlighting the evolving requirements for HIPAA compliance. Organizations must adopt strong, government-approved methods to effectively secure information. Industry leaders stress the essential role of data protection in cultivating patient trust. As Monte Coulter, a leading CISO, points out, "Healthcare is the No. 1 attacked sector right now, and if we continue to put off security, that’s not good." This sentiment emphasizes the urgent need for healthcare institutions to implement stringent data protection strategies, not only to comply with regulations but also to reassure patients that their information is secure. By prioritizing data protection, organizations can strengthen their overall security posture while fostering a culture of trust and accountability in the healthcare sector.
Determine If HIPAA Requires Encryption
While HIPAA may not explicitly mandate encryption HIPAA in every scenario, it strongly advocates for its implementation as a best practice. Organizations are urged to conduct comprehensive risk evaluations to determine the necessity of encryption HIPAA for protecting electronic Protected Health Information (ePHI). This process involves assessing the specific circumstances surrounding their data handling practices and pinpointing potential vulnerabilities.
What happens if an organization opts not to implement encryption HIPAA? It becomes crucial to document the alternative safeguards employed to protect ePHI. This documentation not only bolsters compliance efforts but also plays a vital role in effective risk management. Compliance professionals stress that a formal risk assessment should encompass a thorough analysis of data flow, potential threats, and the effectiveness of existing security measures.
Consider the cases of MarinHealth and Kaiser Permanente, which faced substantial settlements due to inadequate safeguarding of ePHI. These instances underscore the critical need for robust security practices. By proactively assessing their data protection requirements and applying necessary safeguards, including encryption HIPAA, organizations can enhance their compliance posture and better secure sensitive patient information.
Explore Recommended HIPAA Compliant Email Encryption Software
To ensure the secure communication of electronic Protected Health Information (ePHI), organizations must utilize encryption HIPAA to comply with regulations. Leading solutions like Paubox, Virtru, and LuxSci offer advanced encryption features designed to protect emails containing confidential information. These tools not only comply with HIPAA regulations but also significantly enhance overall information security with encryption HIPAA, ensuring that ePHI remains confidential during transmission.
Consider Paubox, for instance. It provides seamless integration with existing email systems, allowing users to send encrypted emails without requiring recipients to log in or create accounts. Virtru enhances email protection with features such as loss prevention and access controls, enabling entities to regulate who can see or forward confidential information. Meanwhile, LuxSci offers adjustable security options and robust key management, ensuring that organizations can customize their protective measures to meet specific compliance requirements.
Statistics reveal that entities using email security solutions experience a significant decline in breaches of information. Research shows that encrypted messages are 70% less likely to be intercepted by unauthorized individuals. Cybersecurity specialists emphasize that these tools are essential for any organization managing ePHI, particularly regarding encryption HIPAA. The right encryption solution not only safeguards sensitive information but also fosters trust with clients and partners, showcasing a commitment to information security.
In conclusion, adopting HIPAA-compliant email coding software is not just a regulatory requirement; it’s a strategic move to protect your organization and build trust. Are you ready to take action and secure your communications?
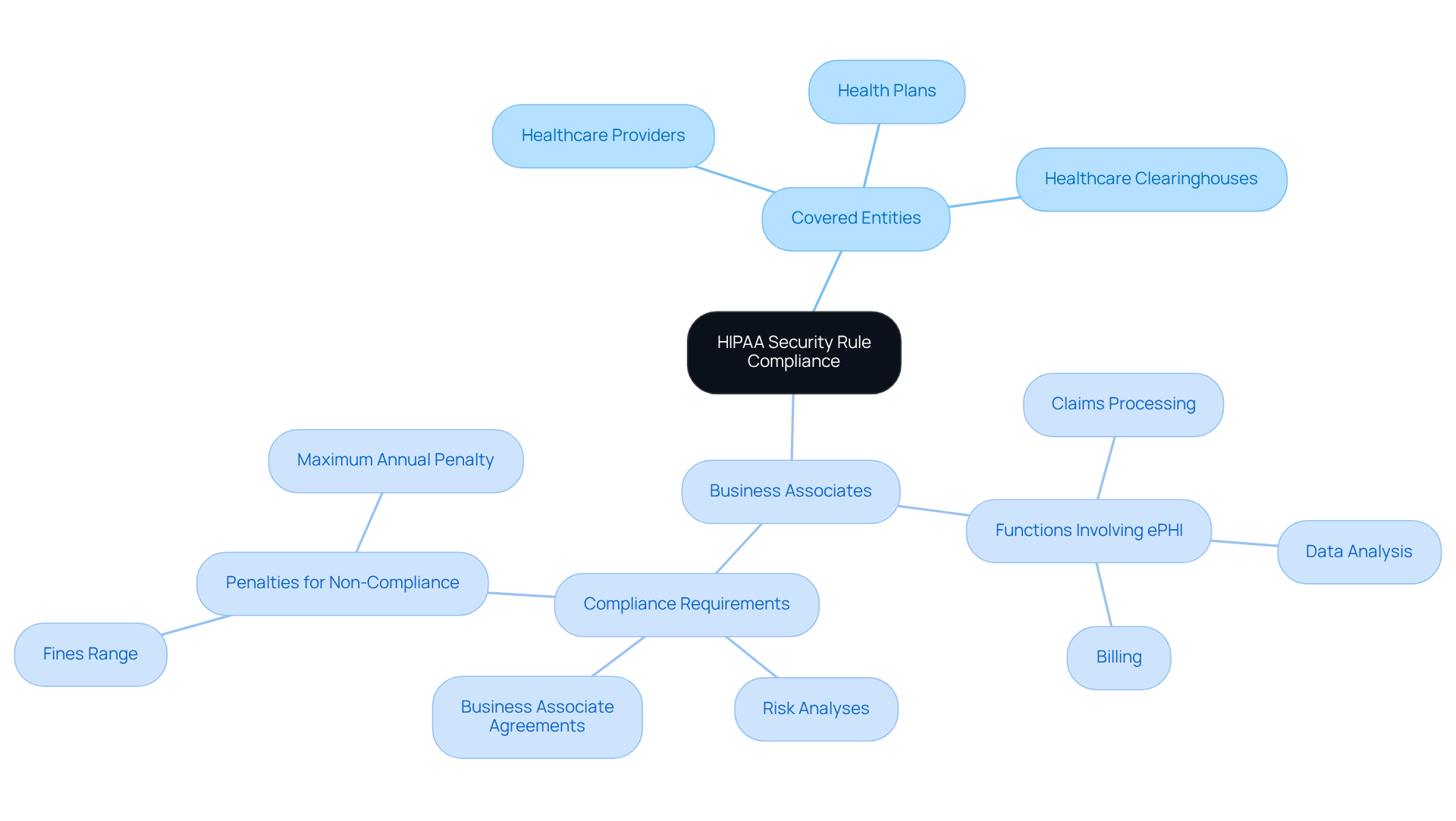
Identify Who Must Comply with HIPAA Security Rule
The HIPAA Security Rule mandates strict adherence for covered entities, which encompass healthcare providers, health plans, and healthcare clearinghouses managing electronic Protected Health Information (ePHI). But it doesn’t stop there-business associates, those entities performing functions involving ePHI on behalf of covered entities, must also comply with HIPAA regulations. This includes a variety of services such as claims processing, data analysis, and billing.
Understanding the distinction between covered entities and business associates is crucial for organizations aiming to fulfill their regulatory responsibilities effectively. As the landscape of HIPAA compliance evolves, especially with the anticipated 2026 changes that will emphasize operational regulations and enhance patient access processes, it’s vital for organizations to accurately identify their roles and responsibilities.
Moreover, business associates are required to conduct risk analyses to evaluate vulnerabilities to ePHI. Non-compliance can lead to severe penalties, with fines ranging from $100 to $50,000 per violation, and a staggering maximum annual penalty of $1.5 million.
Additionally, covered entities must have a written business associate agreement with any business associate involved in healthcare activities to ensure compliance. As Ross Filipek, CISO at Corsica Technologies, aptly states, "HIPAA compliance is only getting more complex in 2026, which increases the burden on covered entities to achieve and maintain compliance."
Are you prepared to navigate these complexities? Ensuring compliance is not just a regulatory requirement; it’s a commitment to safeguarding patient information.
Highlight the Importance of Encryption for Sensitive Data
Encryption HIPAA serves as a vital defense mechanism for protecting sensitive information, especially electronic Protected Health Information (ePHI). By ensuring that intercepted data remains unreadable to unauthorized individuals, robust encoding techniques significantly mitigate the risk of information breaches and enhance patient privacy. This proactive approach not only meets regulatory requirements but also builds trust among patients and stakeholders.
As cybersecurity specialist Beth Osborne states, "Safeguarding information through encoding, masking, or redaction secures it at rest and in motion and ensures that exfiltrated information is worthless to malicious individuals." Organizations that prioritize data protection can improve their compliance rates and reduce the likelihood of costly breaches, ultimately preserving their reputation and operational integrity.
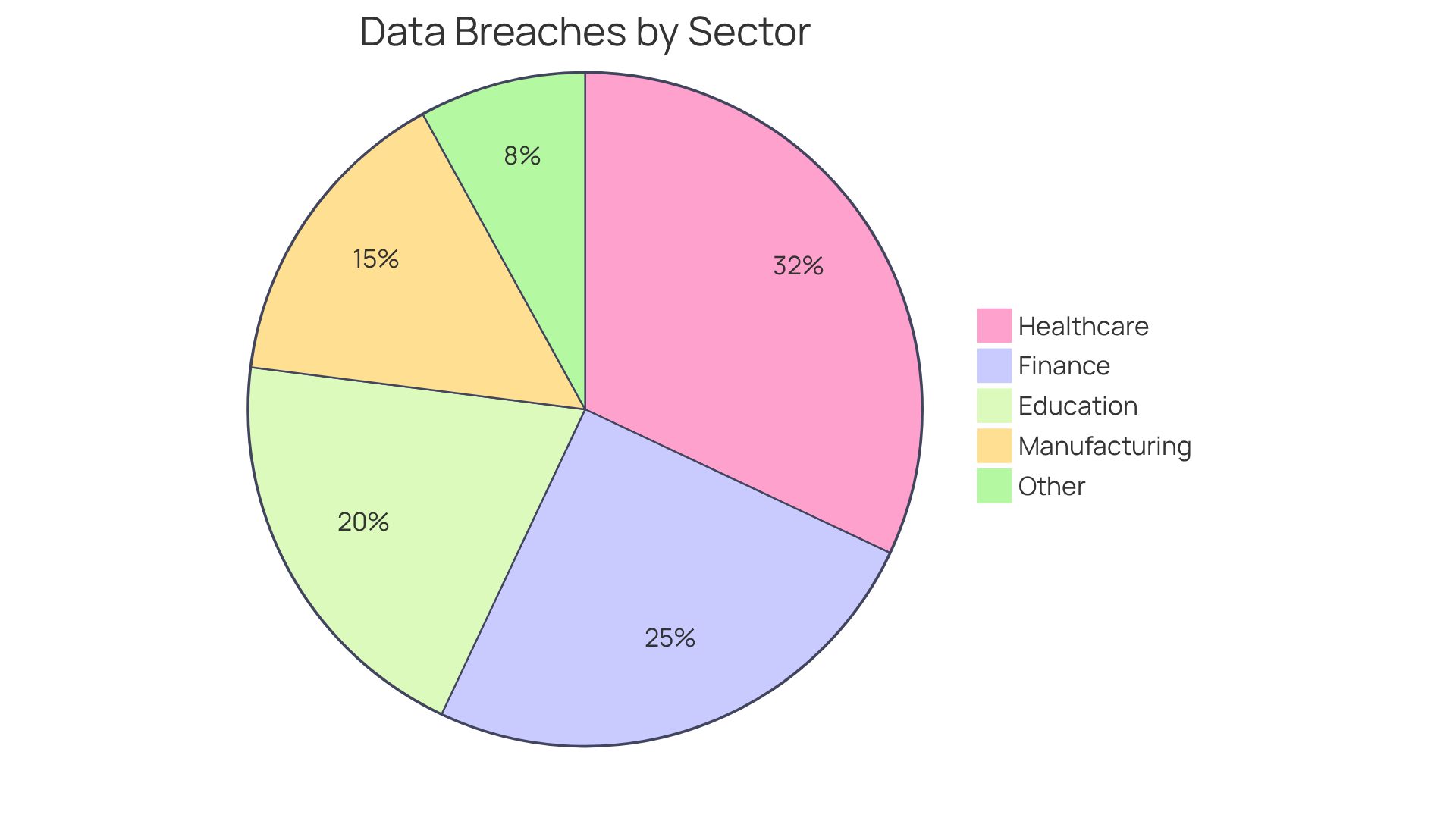
Consider this: data breaches in the healthcare sector accounted for 32% of all documented breaches from 2015 to 2022. This statistic underscores the critical need for robust security measures. By implementing strong encryption HIPAA practices, organizations not only protect sensitive information but also position themselves as leaders in compliance and trustworthiness.
Understand the Consequences of Non-Compliance with HIPAA Encryption
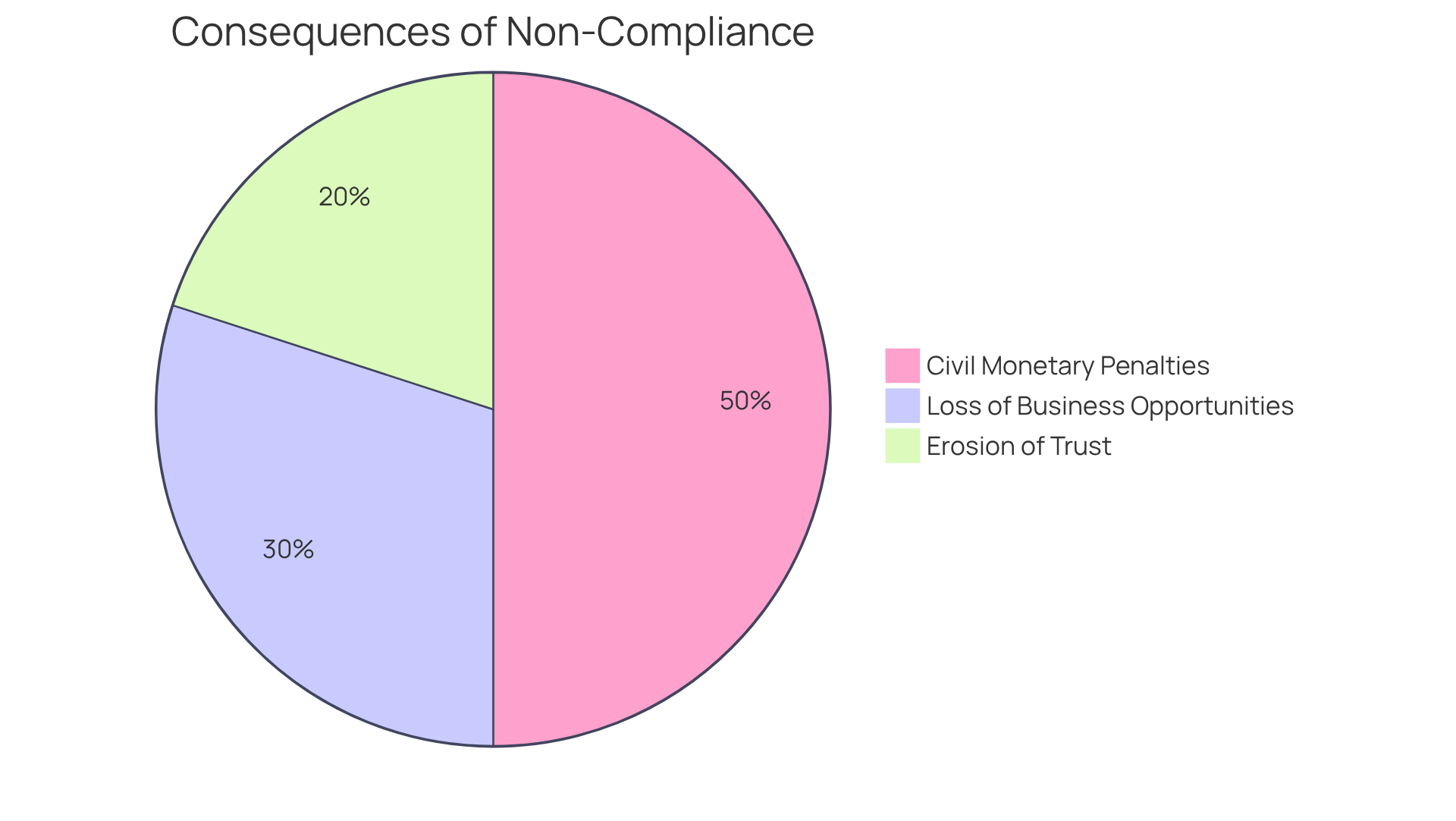
Non-compliance with encryption HIPAA standards can lead to severe consequences. Are you aware of the potential fallout? Organizations face civil monetary penalties ranging from $145 to over $2 million per violation, depending on the severity of the breach. This isn’t just about fines; it’s about the loss of business opportunities and the erosion of trust from patients.
Understanding these consequences is essential for organizations to prioritize compliance with encryption HIPAA regulations. The stakes are high, and the risks are real. By taking proactive steps to ensure compliance, organizations can protect their interests and maintain their reputation in the industry. Don’t wait until it’s too late - act now to safeguard your organization against these risks.
Conclusion
The significance of encryption in HIPAA compliance for defense contractors is paramount. As organizations gear up for impending deadlines and stringent regulations, grasping and implementing encryption standards is essential for protecting electronic Protected Health Information (ePHI). Robust encryption practices not only fulfill compliance requirements but also strengthen the overall security posture of organizations, ensuring sensitive data is shielded from unauthorized access.
Key insights throughout this article underscore the necessity of adopting AES-256 for data at rest and TLS 1.3 for data in transit. The urgency for compliance is heightened by the potential financial repercussions of breaches, with the average cost of a healthcare data breach soaring into the millions. Moreover, the article highlights the importance of comprehensive risk assessments and the careful selection of encryption tools, such as HIPAA-compliant email encryption software, to bolster security measures and cultivate trust with clients and stakeholders.
In light of these insights, it is crucial for defense contractors to act swiftly. By prioritizing compliance with HIPAA encryption standards, organizations can sidestep severe penalties and foster a culture of data protection that ultimately benefits both the organization and its clients. As the cybersecurity landscape evolves, embracing encryption as a foundational element of data security transcends mere regulatory obligation; it emerges as a strategic imperative that safeguards sensitive information and maintains the trust of those they serve.
Frequently Asked Questions
What is the purpose of the CMMC Info Hub?
The CMMC Info Hub serves as a resource for defense contractors to understand and implement data protection standards, including encryption for HIPAA compliance, particularly for protecting electronic Protected Health Information (ePHI).
What are the new requirements for protecting ePHI as mandated by recent updates?
Organizations must use AES-256 encryption for information at rest and TLS 1.3 for information in transit to protect ePHI, with compliance required by December 31, 2025.
What are the consequences of non-compliance with HIPAA encryption standards?
Non-compliance could lead to increased penalties starting January 2026, emphasizing the urgency for organizations to enhance their cybersecurity measures.
What is the significance of AES-256 encryption for data at rest?
AES-256 is a strong cryptographic standard recognized for its effectiveness in safeguarding sensitive information, making it unreadable to unauthorized users.
How many organizations have adopted AES-256 coding for HIPAA compliance?
Approximately 50% of entities have fully adopted AES-256 coding for HIPAA compliance.
What is the average cost of a healthcare breach?
The average cost of a healthcare breach is estimated at $7.13 million, highlighting the financial implications of non-compliance.
What is required for encrypting ePHI in transit?
Organizations must use secure transmission protocols, including Transport Layer Security (TLS), to encrypt ePHI during transfer and protect it from unauthorized access.
What future changes to HIPAA compliance should organizations prepare for?
The forthcoming 2026 HIPAA modifications will mandate the protection of ePHI during both transmission and storage, requiring organizations to enhance their compliance efforts.
What are essential components of a robust compliance strategy for HIPAA?
Maintaining detailed data flow diagrams and conducting ongoing risk assessments are essential for a robust compliance strategy to safeguard sensitive health information.