10 Key Security Compliance Standards for Defense Contractors
Explore essential security compliance standards for defense contractors to ensure contract eligibility.
Introduction
The landscape of defense contracting is evolving rapidly, with cybersecurity compliance standards now a non-negotiable requirement for organizations seeking contracts. As the Cybersecurity Maturity Model Certification (CMMC) and other key regulations come into play, defense contractors face the significant challenge of navigating complex compliance frameworks that directly impact their operational viability.
This article explores ten essential security compliance standards that not only protect sensitive information but also enhance competitive positioning within the defense sector.
How can contractors ensure they meet these rigorous requirements while maintaining their edge in a highly scrutinized industry?
CMMC Info Hub: Your Essential Resource for CMMC Compliance
The Info Hub serves as a comprehensive knowledge repository tailored for organizations striving to achieve compliance with the Cybersecurity Maturity Model Certification (CMMC). It offers detailed roadmaps, practical strategies, and peer insights that empower suppliers to effectively navigate the complexities of Department of Defense (DoD) cybersecurity obligations. By providing structured support, the Info Hub transforms uncertainty into clarity, enabling companies to bolster their cybersecurity posture and readiness for contracts.
Starting in 2026, adherence to security compliance standards will be mandatory for contract eligibility, impacting over 300,000 military suppliers. Todd R. Overman, Managing Partner of Bass, Berry & Sims, underscores the urgency of this shift, stating, "cybersecurity assurance is no longer a best practice but a legal condition of participating in the defense marketplace." This statement highlights the pressing need for builders to act, especially with the phased implementation of CMMC requirements beginning November 10, 2025.
Successful implementation examples demonstrate how organizations have leveraged the Info Hub to refine their compliance processes, ensuring they meet the stringent security compliance standards established by the DoD. Expert insights further affirm the effectiveness of the CMMC Info Hub in providing tailored guidance that directly addresses the challenges faced by military suppliers. This makes it an indispensable resource on the journey toward compliance.
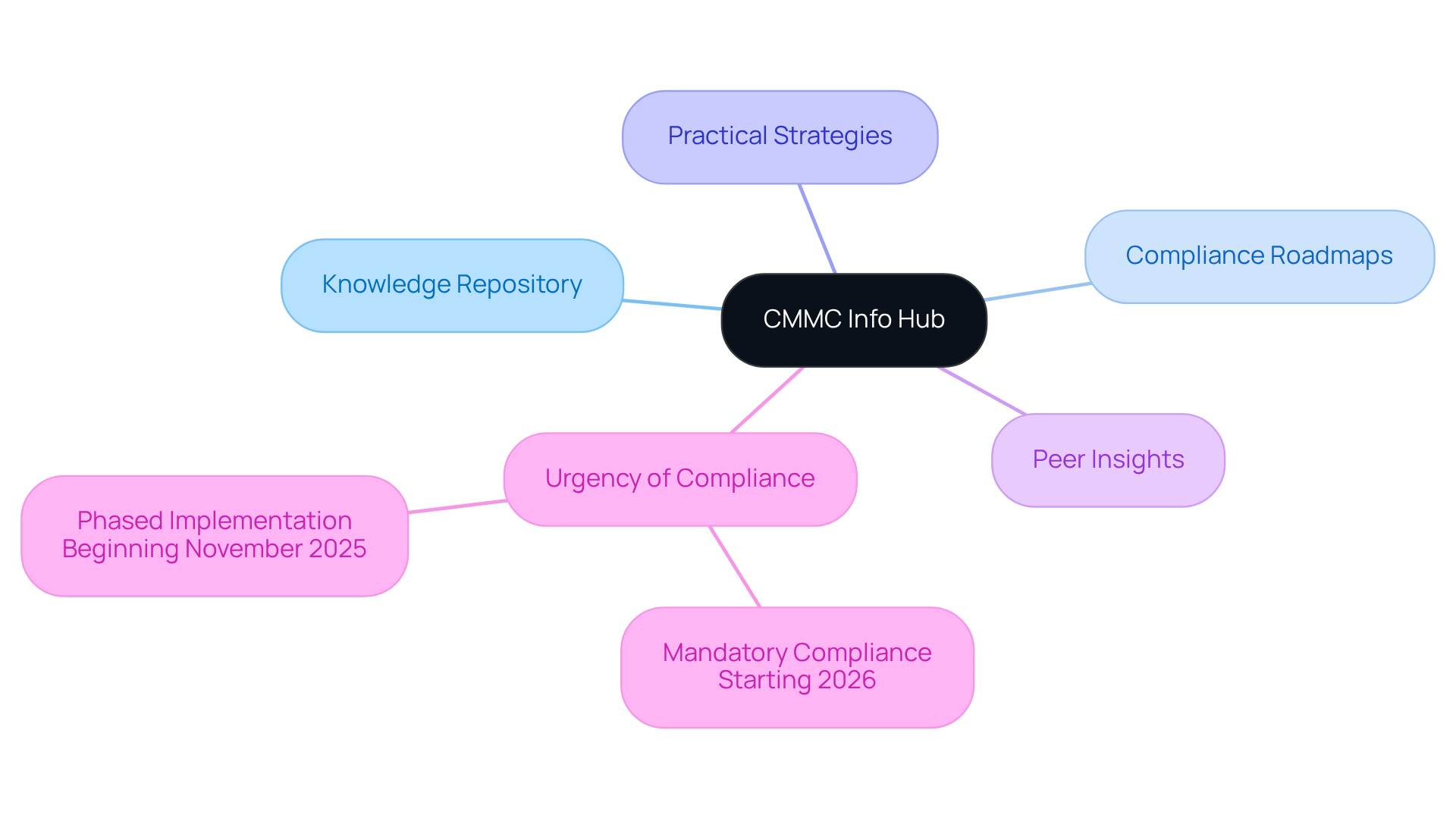
NIST Cybersecurity Framework: Guidelines for Risk Management
The NIST Cybersecurity Framework offers a robust methodology for managing cybersecurity risks, centered around five essential functions: Identify, Protect, Detect, Respond, and Recover. Defense contractors can leverage this framework to evaluate their cybersecurity posture, implement critical controls, and comply with federal regulations. By aligning operations with NIST guidelines, organizations not only bolster their defenses against cyber threats but also enhance their overall security posture.
Consider this: a significant percentage of organizations that have adopted NIST standards reported improved effectiveness in risk management. This statistic underscores the framework's real-world value. As the security sector faces increasing scrutiny regarding security compliance standards, utilizing the NIST framework is crucial for maintaining a competitive edge and ensuring eligibility for contracts.
Recent updates to the NIST guidelines further emphasize the need for continuous improvement and adaptation in risk management strategies. It’s vital for organizations to stay informed and proactive in their compliance efforts. The CMMC Info Hub offers practical strategies and peer insights to help industry professionals navigate the complexities of CMMC adherence with confidence, transforming confusion into clarity.
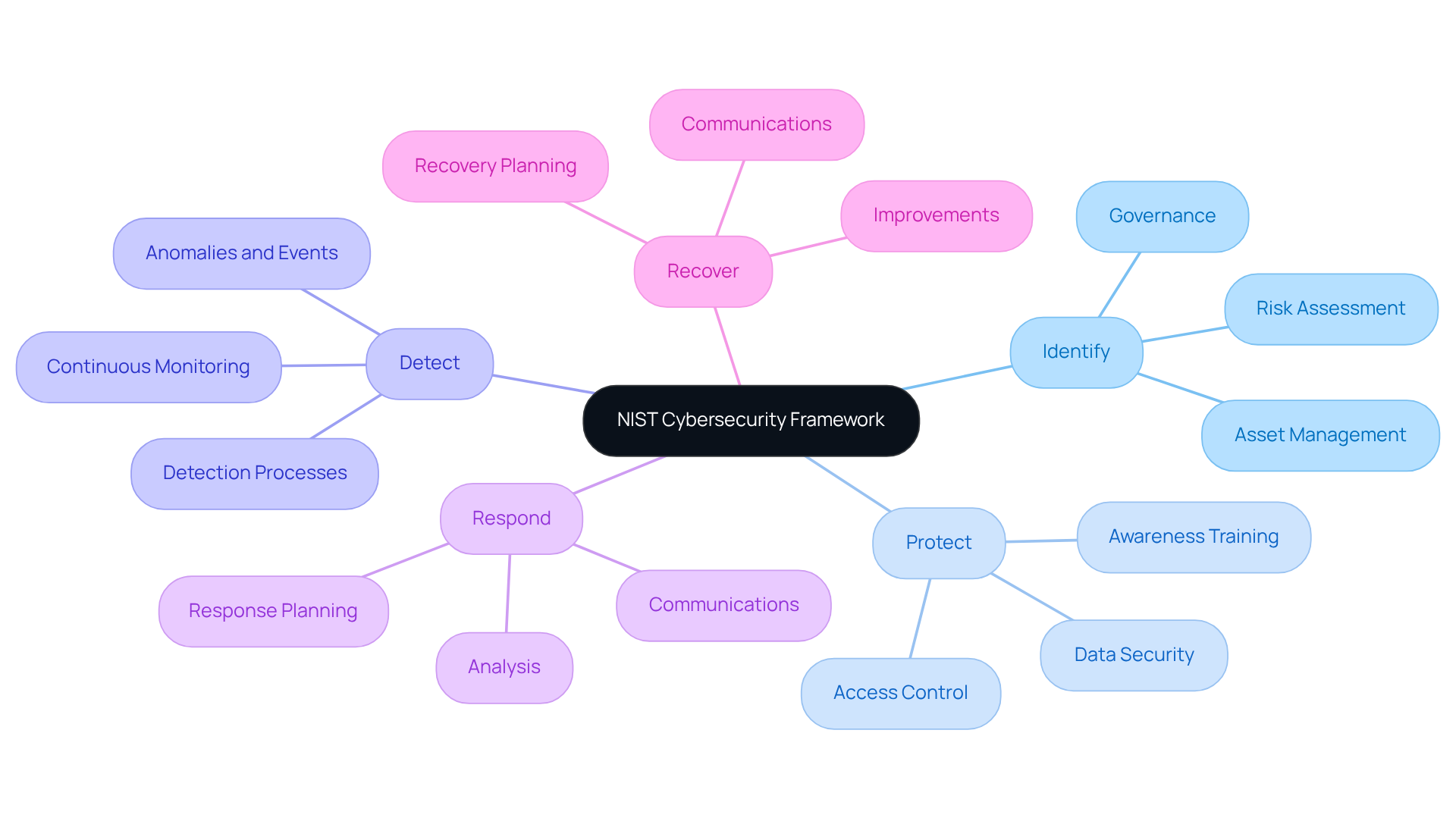
ISO/IEC 27001: Establishing an Information Security Management System
ISO/IEC 27001 provides a robust framework for managing sensitive information, ensuring its confidentiality, integrity, and availability. By adopting an Information Security Management System (ISMS) aligned with this standard, security providers can effectively identify and mitigate risks, meet security compliance standards, and enhance their reputation among clients.
Obtaining ISO/IEC 27001 certification signifies a strong commitment to information security and enhances competitive positioning in the security industry, where adhering to security compliance standards is essential. For example, organizations like Ridge Security, which achieved ISO/IEC 27001 certification, report improved risk management and operational resilience. This demonstrates the tangible benefits of certification.
As cyberattacks and breaches are projected to cost $10.5 trillion globally each year by 2026, the importance of ISO/IEC 27001 in safeguarding sensitive information and adhering to security compliance standards will only grow. This establishes it as a vital standard for security providers moving forward. Are you ready to take the necessary steps to protect your organization?
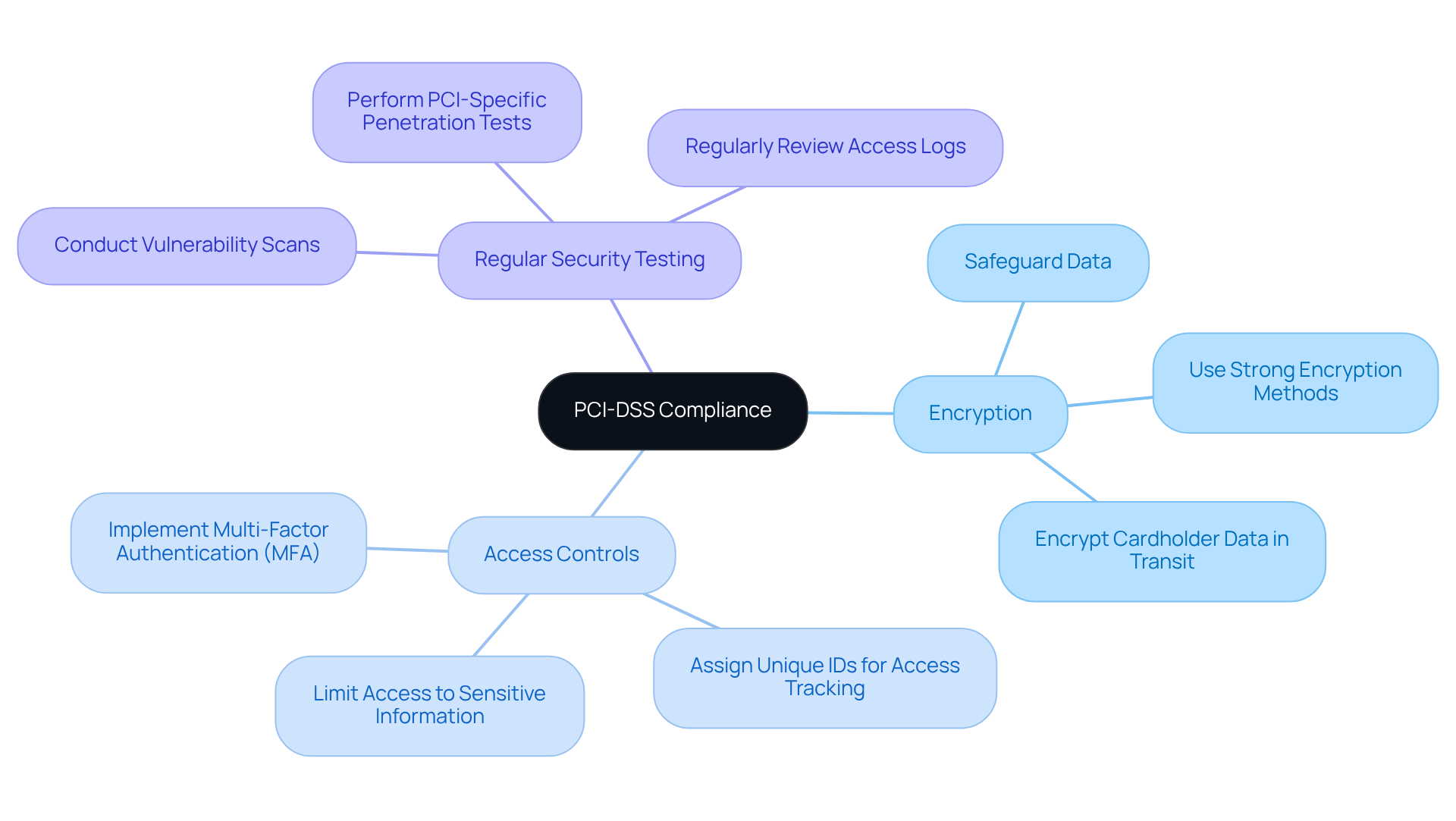
PCI-DSS: Ensuring Payment Card Security Compliance
The Payment Card Industry Data Security Standard (PCI-DSS) is crucial for organizations that handle credit card transactions. Why is this standard so important? Adhering to PCI-DSS helps maintain security compliance standards that protect sensitive cardholder information from breaches and also fosters customer trust in your business.
To meet PCI-DSS requirements, organizations must implement robust security compliance standards. This includes:
- Encryption to safeguard data
- Access controls to limit who can view sensitive information
- Regular security testing to identify vulnerabilities
By taking these steps, companies can significantly reduce the risk of data breaches and enhance their reputation in the marketplace.
In conclusion, adhering to security compliance standards like PCI-DSS is not just a regulatory obligation; it’s a vital component of your business strategy. By prioritizing these security measures, you not only protect your customers but also position your organization as a trustworthy leader in the financial sector.
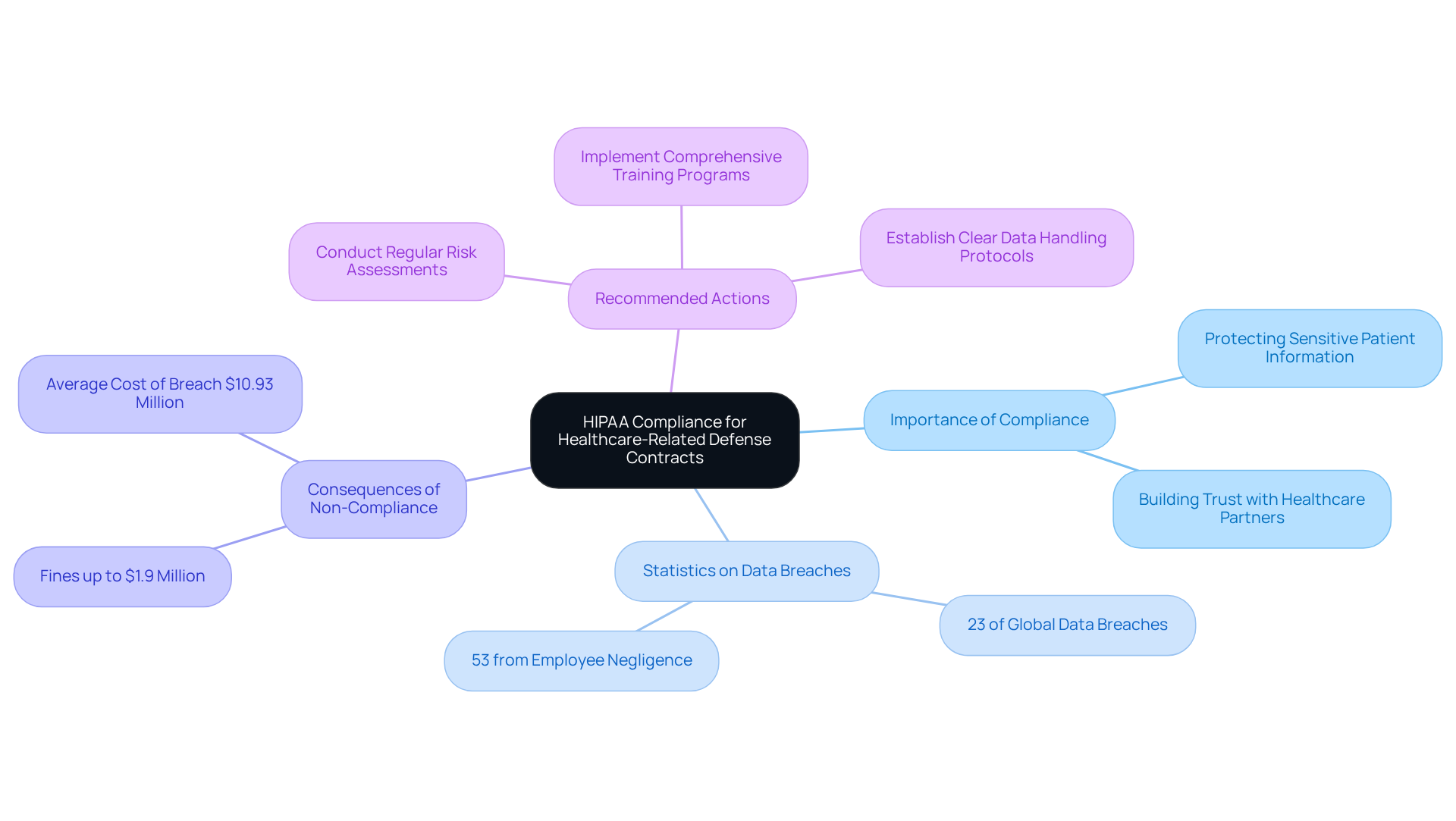
HIPAA: Compliance for Healthcare-Related Defense Contracts
The Health Insurance Portability and Accountability Act (HIPAA) sets vital standards for protecting sensitive patient information, especially for defense companies engaged in healthcare projects. Compliance with HIPAA regulations is not just a requirement; it’s essential for these service providers to ensure the security of electronic protected health information (ePHI). This compliance necessitates implementing robust administrative, physical, and technical safeguards to prevent unauthorized access and data breaches.
Consider this: in 2023, healthcare organizations were responsible for 23% of all global data breaches, with a significant number linked to human error, such as lost devices and phishing attacks. Alarmingly, 53% of healthcare data breaches arise from employee negligence. This statistic underscores the critical need for comprehensive training and awareness programs. As Charlotte Barenz, Vice President of Implementation, points out, "A once a year organization-wide HIPAA training session is not enough. This type of training is not only ineffective, it violates HIPAA. Each employee must be trained upon hire and retrained annually."
Defense companies must remain particularly vigilant, as violations can result in severe penalties. For example, the Office for Civil Rights (OCR) has imposed fines of up to $1.9 million per violation, while the average cost of a healthcare breach in 2023 was around $10.93 million. Recent incidents, such as the $2.4 million settlement faced by Memorial Hermann Health System for the impermissible disclosure of PHI, highlight the financial and reputational risks of non-compliance.
To effectively safeguard ePHI, contractors should prioritize:
- Risk assessments
- Conduct regular training sessions
- Establish clear protocols for data handling
Upholding these regulations is not merely a legal obligation; it’s a crucial aspect of adhering to security compliance standards, building trust with healthcare partners, and protecting the integrity of sensitive information in defense projects.
SOC 2: Data Security and Privacy for Service Organizations
SOC 2 adherence hinges on five Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. For defense firms, implementing robust security measures is not just a best practice; it’s a commitment to protecting customer data and ensuring data privacy. Achieving SOC 2 compliance not only strengthens an organization’s security posture but also aligns with security compliance standards, thereby building trust with clients and stakeholders. This makes it an essential requirement for service organizations in the security industry to meet security compliance standards.
So, how can military suppliers navigate this complex landscape? With the Info Hub, they can transform confusion into clarity. By accessing practical strategies and peer insights, they empower themselves to achieve compliance with confidence. Don’t let uncertainty hold you back - leverage these resources to secure your organization’s future.
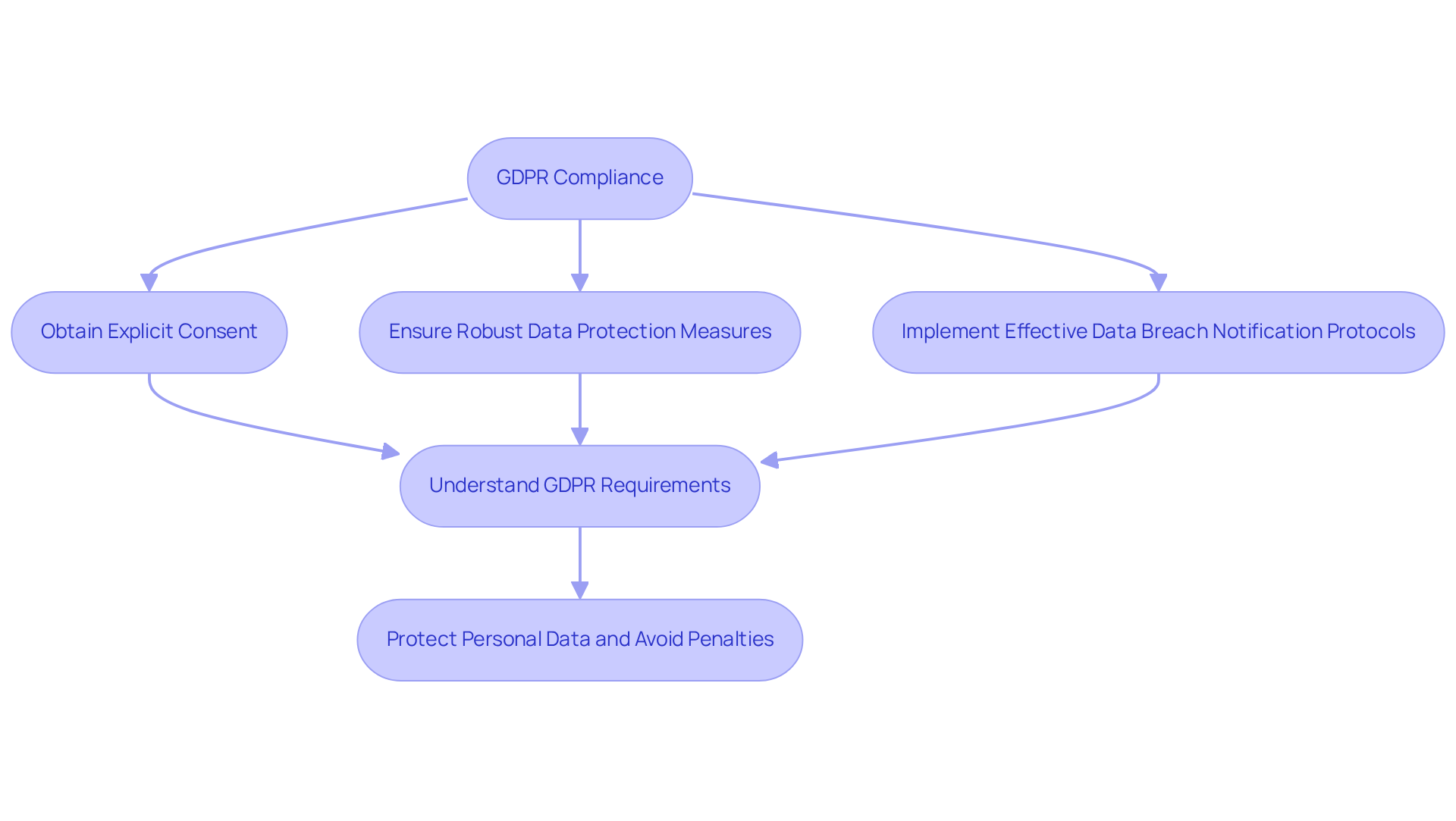
GDPR: Compliance for Handling Personal Data in the EU
The General Data Protection Regulation (GDPR) establishes stringent guidelines for collecting and processing personal data within the European Union. For defense companies handling the personal information of EU citizens, compliance with GDPR is not just a legal obligation; it’s a critical aspect of operational integrity. Are you aware of the specific requirements? Organizations must:
- Obtain explicit consent
- Ensure robust data protection measures
- Implement effective data breach notification protocols
Non-compliance can lead to severe consequences, including hefty fines and lasting reputational damage. This reality underscores the necessity for organizations to fully grasp and adhere to security compliance standards such as GDPR. By prioritizing compliance, companies not only protect themselves from penalties but also build trust with their clients and stakeholders.
In summary, understanding and implementing GDPR requirements is essential for defense companies. Take action now to ensure your organization is compliant and safeguard your reputation in the marketplace.
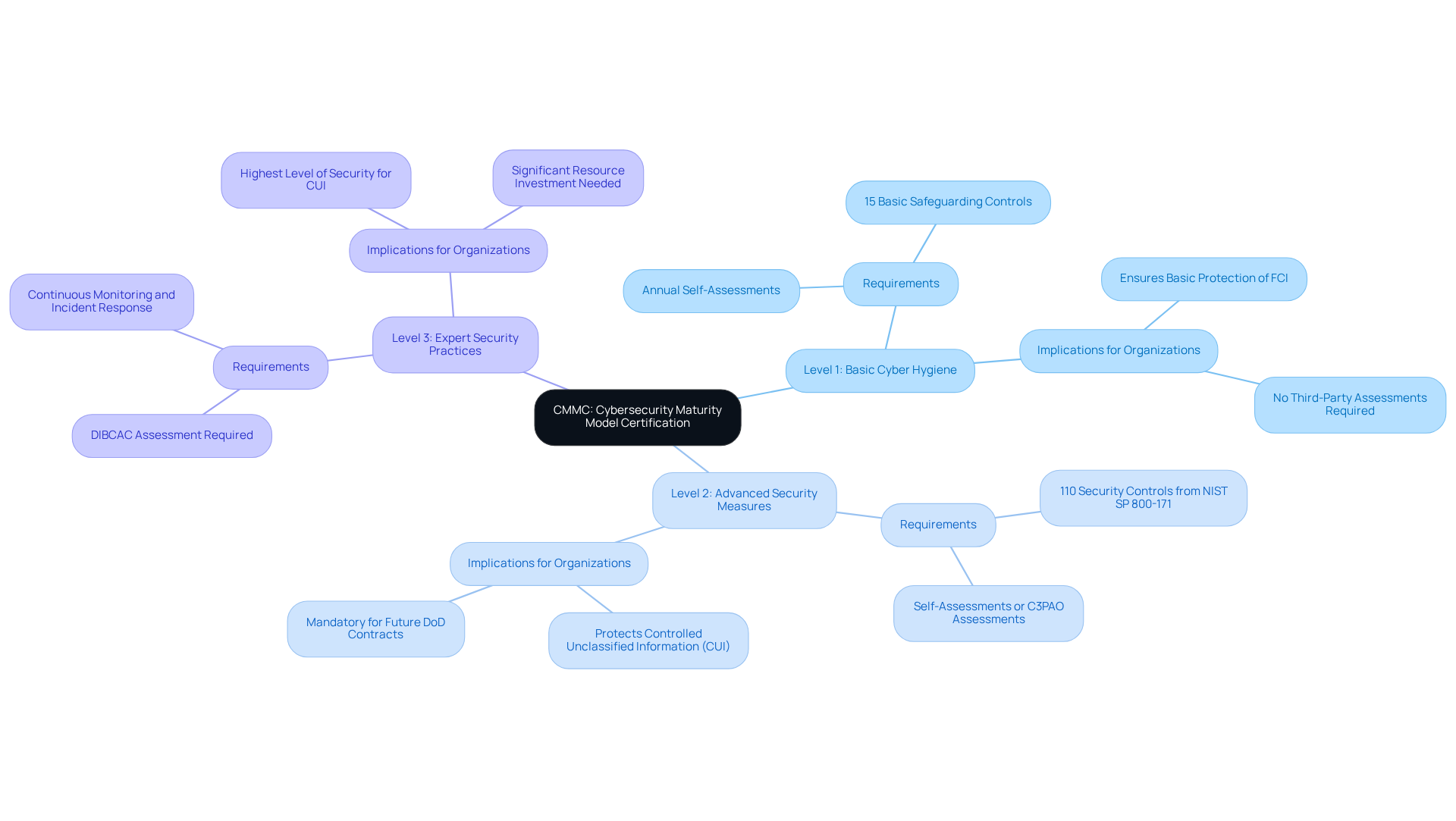
CMMC: Cybersecurity Maturity Model Certification for Defense Contractors
The Cybersecurity Maturity Model Certification (CMMC) serves as a crucial framework aimed at bolstering the cybersecurity posture of military suppliers. This model is divided into three distinct levels of certification, each outlining specific security requirements that organizations must meet to qualify for Department of Defense (DoD) contracts. Starting January 2026, compliance with this certification will be mandatory, making it vital for contractors in the military sector to fully understand its standards to remain competitive.
Why is this important? The framework underscores the necessity of implementing robust cybersecurity measures and conducting regular evaluations to ensure adherence to security compliance standards. It is specifically designed to safeguard Controlled Unclassified Information (CUI) and enhance the overall security of the defense industrial base. Alarmingly, only 1% of service providers are fully prepared for audits, highlighting the urgent need for compliance. Organizations that postpone meeting these requirements risk losing their competitive edge and future contract opportunities with the DoD.
Recent updates to the security framework have further emphasized the importance of continuous compliance with security compliance standards, as the DoD plans to introduce more stringent criteria in the coming years. This evolving landscape demands that security providers not only understand the CMMC requirements but also actively engage in security compliance standards to protect sensitive information and secure their positions within the supply chain.
In summary, the CMMC is not just a guideline; it is a necessity for survival in the military contracting arena. Organizations must prioritize understanding and adhering to these standards to thrive in an increasingly competitive environment.
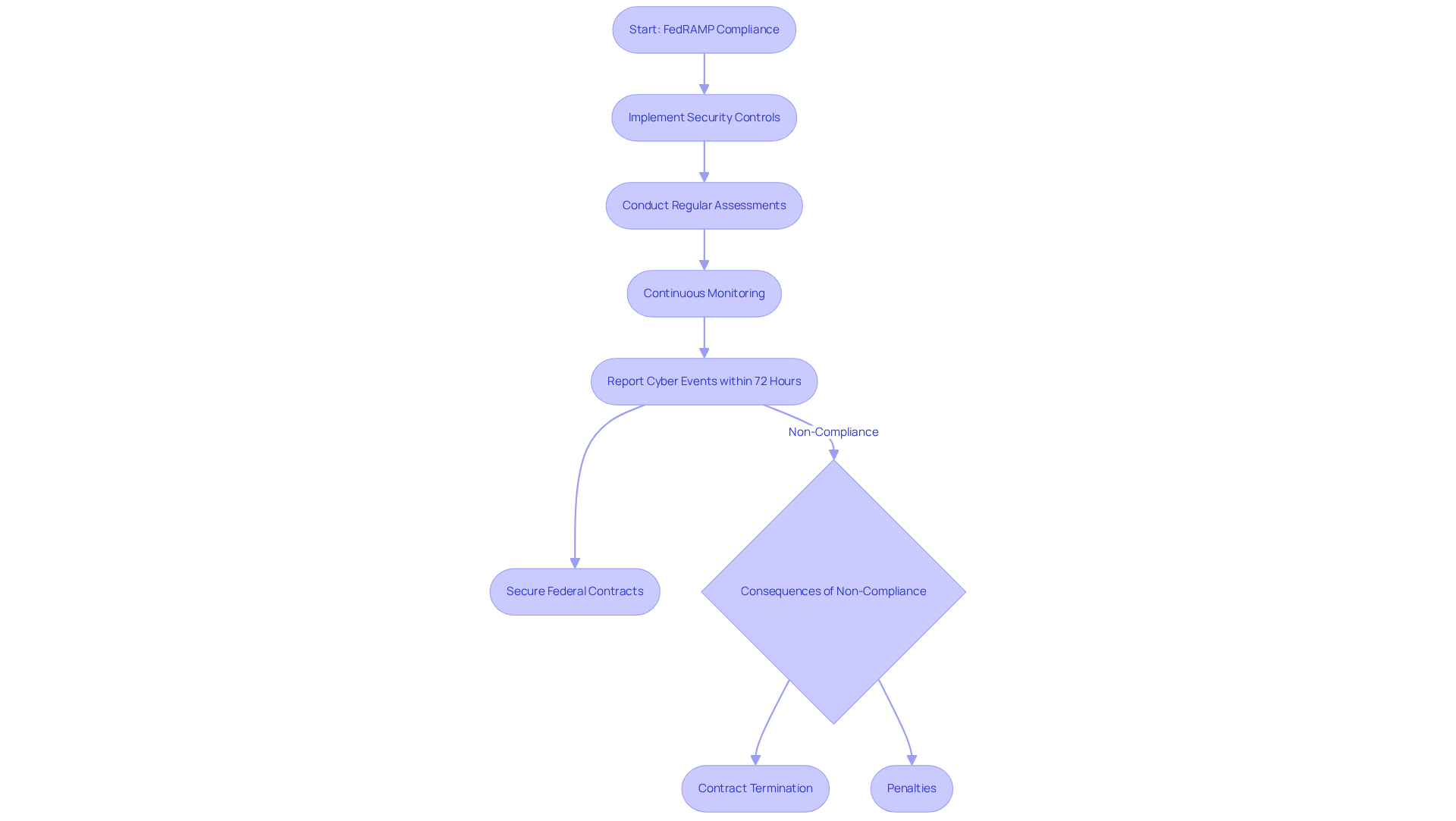
FedRAMP: Cloud Security Compliance for Federal Agencies
The Federal Risk and Authorization Management Program (FedRAMP) establishes a standardized framework for security assessment and authorization specifically designed for cloud service providers working with federal agencies. For defense firms utilizing cloud solutions, obtaining FedRAMP certification is not just beneficial; it’s essential for safeguarding federal data. This compliance mandates the implementation of stringent security controls, regular assessments, and continuous monitoring to adhere to security compliance standards and ensure data integrity and security.
Starting in 2026, builders must report any cyber event that results in unauthorized access, disruption, or destruction of information within 72 hours. This requirement underscores the urgency of compliance. Adhering to FedRAMP not only strengthens security measures but also significantly improves access to federal contracts, making it a critical requirement for defense contractors. Non-compliance can lead to severe repercussions, including contract termination and penalties under the False Claims Act.
As the cybersecurity landscape evolves, the importance of FedRAMP compliance in adhering to security compliance standards continues to escalate, especially in light of rising state-sponsored cyber threats and the pressing need for robust data protection protocols. Employing a 'FedRAMP Moderate' or 'FedRAMP High' authorized environment is often essential for securing contracts in 2026, further highlighting the critical nature of this compliance.
In summary, the path to securing federal contracts is paved with the commitment to FedRAMP adherence. Are you prepared to take the necessary steps to ensure compliance and protect your organization?
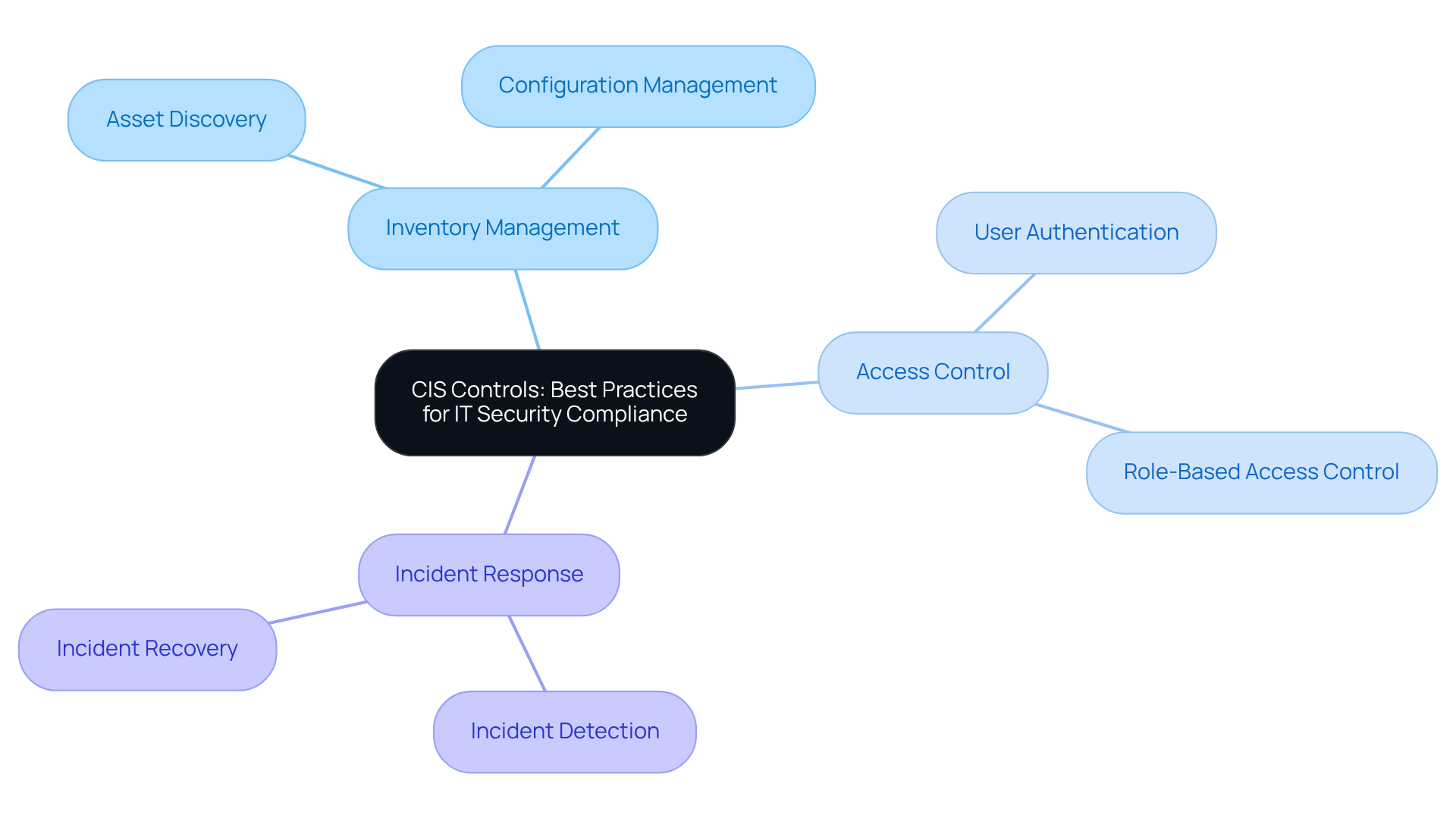
CIS Controls: Best Practices for IT Security Compliance
The Center for Internet Security (CIS) has established a set of Critical Security Controls designed to enhance your cybersecurity posture through a prioritized approach. These controls emphasize essential areas such as:
- Inventory management
- Access control
- Incident response
By adopting CIS Controls, security firms can significantly bolster their defenses against cyber threats while ensuring they meet security compliance standards.
Why should organizations consider these best practices? Simply put, implementing these controls can dramatically reduce risk exposure and strengthen your overall security framework. Furthermore, the CMMC Info Hub provides practical strategies and peer insights, empowering defense contractors to navigate the complexities of CMMC compliance with confidence. This resource transforms confusion into clarity, making compliance not just achievable but straightforward.
Conclusion
The landscape of security compliance standards for defense contractors is evolving at an unprecedented pace. Critical frameworks like CMMC, NIST, and ISO/IEC 27001 are now essential for maintaining eligibility for government contracts. With the Department of Defense implementing stricter regulations, understanding and adhering to these standards has become a necessity for organizations aiming to secure their place in the defense sector.
This article explored key compliance standards, emphasizing their significance and the specific requirements for adherence. The CMMC, for instance, is a pivotal certification that will soon dictate contract eligibility. Meanwhile, frameworks like NIST and ISO/IEC 27001 provide vital guidelines for risk management and information security. Each standard serves a unique purpose, yet collectively, they underscore the importance of robust cybersecurity measures in safeguarding sensitive information and maintaining trust with clients.
As the defense contracting environment grows increasingly competitive and regulated, organizations must prioritize their compliance efforts. Embracing these standards not only mitigates risks but also enhances operational resilience, positioning companies as industry leaders. Taking proactive steps toward compliance today will ensure that defense contractors are well-prepared for the challenges of tomorrow. Ultimately, securing success in a landscape where adherence to security compliance standards is paramount is within reach.
Frequently Asked Questions
What is the CMMC Info Hub?
The CMMC Info Hub is a comprehensive knowledge repository designed for organizations seeking compliance with the Cybersecurity Maturity Model Certification (CMMC). It provides roadmaps, strategies, and insights to help suppliers navigate Department of Defense (DoD) cybersecurity requirements.
Why is CMMC compliance important?
CMMC compliance is crucial because starting in 2026, adherence to security compliance standards will be mandatory for contract eligibility, affecting over 300,000 military suppliers. Cybersecurity assurance has become a legal requirement for participating in the defense marketplace.
When will CMMC requirements begin to be implemented?
The phased implementation of CMMC requirements will begin on November 10, 2025.
How does the CMMC Info Hub support organizations?
The Info Hub supports organizations by providing structured guidance, expert insights, and successful implementation examples that help refine compliance processes and meet DoD security standards.
What is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework is a methodology for managing cybersecurity risks, focusing on five essential functions: Identify, Protect, Detect, Respond, and Recover. It helps defense contractors evaluate their cybersecurity posture and comply with federal regulations.
What are the benefits of adopting the NIST Cybersecurity Framework?
Organizations that adopt NIST standards report improved effectiveness in risk management, enhanced defenses against cyber threats, and better compliance with security standards, which are essential for maintaining a competitive edge.
What is ISO/IEC 27001?
ISO/IEC 27001 is a standard that provides a framework for managing sensitive information through an Information Security Management System (ISMS), ensuring the confidentiality, integrity, and availability of data.
What are the advantages of obtaining ISO/IEC 27001 certification?
Achieving ISO/IEC 27001 certification indicates a strong commitment to information security, enhances competitive positioning, and improves risk management and operational resilience among security providers.
Why is ISO/IEC 27001 increasingly important?
With projected global costs of cyberattacks and breaches reaching $10.5 trillion annually by 2026, ISO/IEC 27001 is vital for safeguarding sensitive information and meeting security compliance standards.




