10 Key Strategies to Enhance Your Security Risk Posture
Enhance your security risk posture with key strategies for effective cybersecurity management.

Overview
The primary focus of the article titled "10 Key Strategies to Enhance Your Security Risk Posture" is to delineate effective strategies for improving an organization's security risk management. This title immediately captures attention, signaling a wealth of insights that organizations can leverage. While the specific content of the article is not provided, it is evident that it will detail actionable steps and approaches aimed at strengthening defenses against cybersecurity threats.
By likely drawing on best practices and industry insights, the article promises to engage readers with relevant data and case studies that underscore the importance of proactive risk management. Ultimately, it aims to equip organizations with the knowledge necessary to bolster their security posture effectively.
Introduction
In an era where cyber threats are becoming increasingly sophisticated, organizations face the daunting task of enhancing their security risk posture to protect sensitive information and maintain compliance. This article explores ten key strategies that not only streamline compliance efforts with standards like the Cybersecurity Maturity Model Certification (CMMC) but also foster a culture of resilience against evolving threats. As organizations navigate this complex landscape, a pressing question arises: how can they effectively implement these strategies to not only meet regulatory requirements but also safeguard their operations against potential breaches?
CMMC Info Hub: Your Guide to Cybersecurity Maturity Model Certification Compliance
CMMC Info Hub serves as a vital resource for organizations aiming to achieve compliance with the Cybersecurity Maturity Model Certification (CMMC). It offers detailed roadmaps, actionable strategies, and insightful articles that cover every facet of CMMC compliance. By leveraging the Hub, organizations can streamline their compliance efforts and enhance their cybersecurity posture, ensuring alignment with the rigorous standards set forth by the Department of Defense (DoD).
Recent updates underscore the phased rollout of CMMC, with the initial phase set to begin on November 10, 2025, mandating Level 1 or Level 2 self-assessments for contract awards. This structured approach not only facilitates compliance but also highlights the critical importance of safeguarding Controlled Unclassified Information (CUI) throughout the defense supply chain.
CMMC Info Hub empowers organizations by delivering tailored insights and strategies pertinent to their compliance journey. For example, a defense subcontractor responsible for managing CAD files for aircraft components must prove its capability to control access, monitor usage, and respond effectively to incidents involving sensitive data. Successful case studies illustrate how defense contractors have adeptly navigated the complexities of CMMC, showcasing the efficacy of proactive compliance strategies, such as regular assessments and the formulation of Plans of Action & Milestones (POA&Ms).
As the CMMC compliance landscape continues to evolve, it is imperative to remain informed about emerging trends and expert perspectives. The Hub enables organizations not only to meet regulatory requirements but also to foster a culture of cybersecurity resilience through robust training initiatives for stakeholders, ensuring they are well-prepared to secure defense contracts and protect sensitive information. Non-compliance could result in disqualification from bidding on future DoD projects, emphasizing the necessity of adhering to CMMC standards.
Additionally, the Hub features a section dedicated to frequently asked questions (FAQs) concerning CMMC compliance, providing clarity on common inquiries and challenges organizations may face. External links to relevant resources are also included, augmenting the overall support for users navigating the compliance process.
IBM Security Posture Framework: Comprehensive Risk Management Solutions
IBM's Security Posture Framework provides entities with a comprehensive methodology for effectively managing their security risk posture in cybersecurity. This framework underscores the necessity of continuous monitoring, regular evaluations, and ongoing improvements of protective measures. By adopting this structured approach, entities can systematically identify vulnerabilities, implement essential controls, and uphold compliance with regulatory standards. Such a proactive stance not only fortifies their defenses against emerging threats but also aligns with the latest trends in risk management solutions.
Recent data reveals a growing adoption rate of the IBM Security Posture Framework among entities, reflecting its effectiveness in enhancing their security risk posture management practices. Industry reports indicate that over 70% of IT leaders are integrating AI-driven cybersecurity solutions into their strategies, underscoring the increasing reliance on advanced frameworks like IBM's. To effectively adopt this framework, entities should focus on embedding it within their current protective protocols, ensuring that all team members are educated and informed about the framework's principles and practices. This alignment fosters a culture of awareness and resilience, which is crucial for navigating today's complex cybersecurity landscape.
However, entities may face challenges such as resistance to change and the necessity for ongoing training. To address these issues, it is essential to engage stakeholders early in the process and provide continuous education on the framework's benefits and applications.
Balbix Insights: Key Components of a Strong Security Posture
Balbix identifies several essential components that bolster a robust security risk posture, notably automated asset inventory management and continuous risk assessment. Automated asset inventory management simplifies the tracking of assets, ensuring entities maintain a precise and current inventory, which is essential for identifying vulnerabilities and managing risks effectively. This approach not only enhances operational efficiency but also supports compliance with cybersecurity standards. According to Myos, 62% of business finances are affected due to failure in inventory tracking, highlighting the critical need for effective asset management.
Ongoing risk evaluation is another crucial approach that helps improve an organization's security risk posture by allowing entities to proactively recognize and tackle potential threats. By consistently assessing their protective environment, companies can adjust to new threats and apply prompt counteractions. This dynamic process promotes a culture of awareness regarding safety among employees, incorporating protective measures into the entity's overall strategy. As Marijn Overvest, founder of Procurement Tactics, states, 'Ongoing risk evaluation is crucial for entities to stay ahead of possible dangers and ensure a robust security risk posture in cybersecurity.'
Recent trends indicate a growing emphasis on these practices, with entities increasingly adopting automated solutions to enhance their security frameworks. For instance, a case study revealed that the use of barcode technology in inventory management reduced human error by 43.5%, demonstrating the effectiveness of automated asset tracking. As cybersecurity risks develop, the necessity for ongoing monitoring and evaluation becomes crucial, guaranteeing that entities stay robust against possible breaches. Authorities in the area promote these strategies, emphasizing their significance in creating a robust cybersecurity framework that can improve the security risk posture to endure the challenges of today's risk landscape.

Picus Security: Risk Posture Assessment and Threat Landscape Insights
Picus Security equips organizations with vital tools for conducting thorough evaluations of their security risk posture and gaining insights into the evolving threat landscape. By simulating real-world attacks, Picus empowers organizations to pinpoint vulnerabilities and gauge their preparedness against potential threats. This proactive strategy is essential for fortifying defenses and adapting to the dynamic cybersecurity environment, ensuring resilience against emerging challenges.
In 2025, organizations face a notable escalation in cyber risks, evidenced by a reported 150% increase in China-nexus activity and an alarming 442% surge in vishing incidents during the latter half of 2024. Cybersecurity experts emphasize the necessity of continuous adaptation to these risks, with authorities like Mikey Anderson asserting, "Discover how an integrated, AI-driven strategy enhances security throughout the complete attack lifecycle."
By utilizing tools like Picus, organizations can adeptly navigate the complexities of the current threat landscape and enhance their security risk posture. To effectively implement these strategies, organizations should regularly conduct simulations and assessments to uncover vulnerabilities and adjust their defenses accordingly.
Uptycs: Asset Inventory and Automated Security Tools for Risk Management
CMMC Info Hub specializes in offering automated protection tools that facilitate comprehensive asset inventory management. By continuously monitoring and assessing assets across hybrid cloud environments, CMMC Info Hub empowers organizations to identify potential vulnerabilities and misconfigurations.
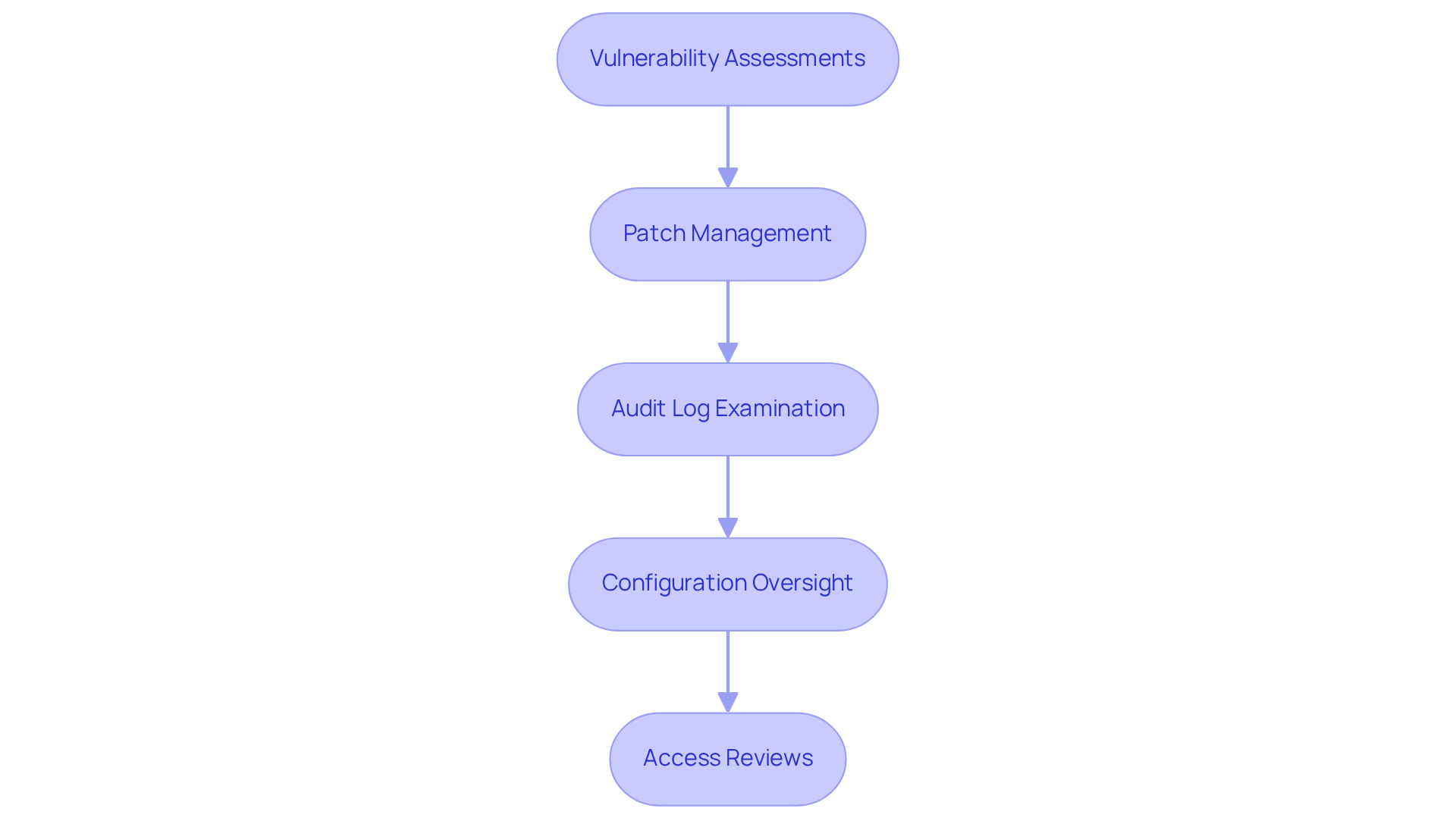
Crucial continuous tasks include:
- Performing regular vulnerability assessments
- Applying prompt patch management
- Examining audit logs for indications of incidents
- Overseeing configurations for deviations from baselines
- Carrying out access reviews to ensure suitability
This proactive strategy not only enhances risk management but also ensures adherence to regulatory standards, ultimately contributing to a stronger security risk posture.
Through effective strategies and peer perspectives, CMMC Info Hub transforms uncertainty into understanding. This enables defense contractors to achieve CMMC adherence with confidence. Are you ready to fortify your security framework? Engage with CMMC Info Hub today to secure your compliance and protect your assets.
UpGuard: Governance and Compliance for Enhanced Security Posture
CMMC Info Hub serves as a vital resource, enhancing governance and compliance for defense contractors striving to meet industry standards and regulatory requirements. By implementing effective strategies and leveraging peer insights, organizations can confidently achieve CMMC adherence. Continuous observation and evaluation of safety measures empower entities to identify regulatory gaps and enact necessary improvements. This proactive approach not only fortifies the security risk posture but also cultivates trust among stakeholders and clients.
As companies increasingly recognize the significance of ongoing monitoring, trends indicate that 76% of organizations employ technology for risk assessments. This statistic underscores the critical role of vigilance in maintaining compliance and enhancing overall safety. Insights from industry professionals confirm that continuous monitoring facilitates quicker identification and resolution of compliance issues, which ultimately improves an entity's security risk posture against potential threats.
It is important to note that this platform may contain links to external websites, over which we have no control regarding their content or availability.

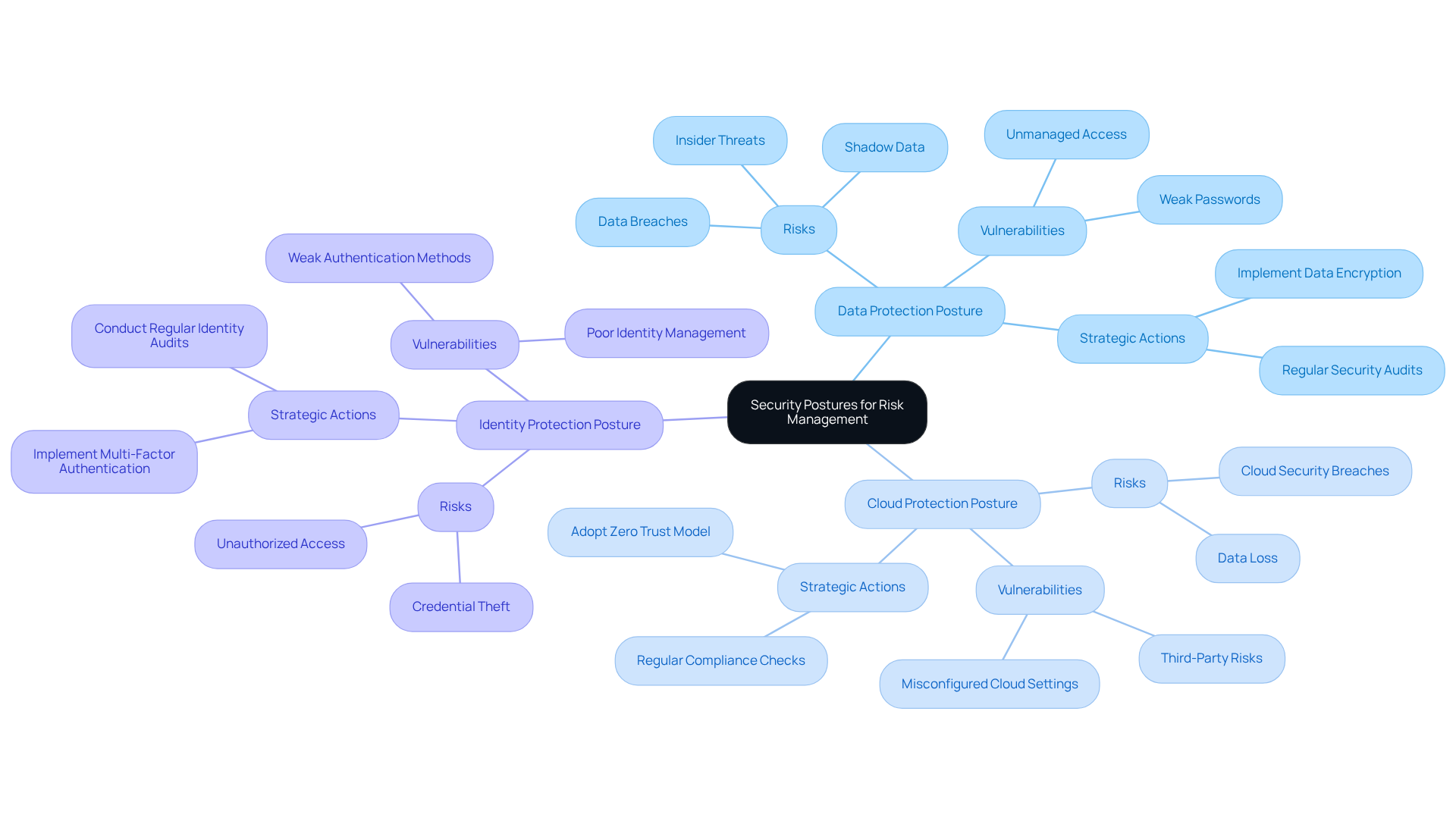
IBM: Types of Security Postures for Tailored Risk Management
Organizations must acknowledge the various protection postures, including data protection posture, cloud protection posture, and identity protection posture, as identified by industry leaders. Each category addresses distinct risks and vulnerabilities inherent to different operational facets. By classifying their security risk posture, organizations can develop tailored risk management strategies that effectively mitigate their specific security challenges. This strategic alignment enhances overall cybersecurity resilience and ensures compliance with evolving regulatory requirements.
As cybersecurity experts emphasize, a comprehensive understanding of the security risk posture is essential for establishing effective risk management frameworks that adapt to the current danger environment. Present trends indicate that entities are increasingly prioritizing updates to their data security posture in 2025, demonstrating a proactive approach to safeguarding sensitive information from emerging risks.
In light of these developments, organizations are encouraged to assess their current security risk posture and consider adjustments that align with these identified measures. This proactive stance not only fortifies defenses but also positions organizations favorably within the regulatory landscape.
Picus Security: Proactive vs. Reactive Approaches to Risk Posture
Embracing a proactive strategy for security risk posture management is vital for entities seeking to strengthen their cybersecurity defenses. Unlike reactive measures that address dangers after they arise, proactive strategies concentrate on recognizing and reducing risks before they intensify. Ongoing oversight plays a crucial role in this method, enabling entities to identify vulnerabilities in real-time and react quickly to possible risks. Moreover, incorporating risk intelligence into protective frameworks enables entities to foresee and ready themselves for emerging cyber dangers, greatly diminishing the chances of successful assaults.
Current trends suggest that entities are increasingly acknowledging the importance of proactive cybersecurity strategies. By conducting regular assessments and leveraging advanced monitoring tools, they can maintain a robust security risk posture that adapts to the evolving threat landscape. Insights from cybersecurity experts highlight the significance of instilling a culture of ongoing enhancement and alertness within entities. As Jim Langevin aptly stated, "Effective cybersecurity is not a product, but a process." As we move into 2025, prioritizing proactive measures will be crucial for safeguarding sensitive information and maintaining trust in digital operations.
Significantly, entities with high cyber risk exposure have up to 2.6 times greater likelihood of suffering damage from cyberattacks compared to those with low exposure, emphasizing the essential requirement for proactive strategies.

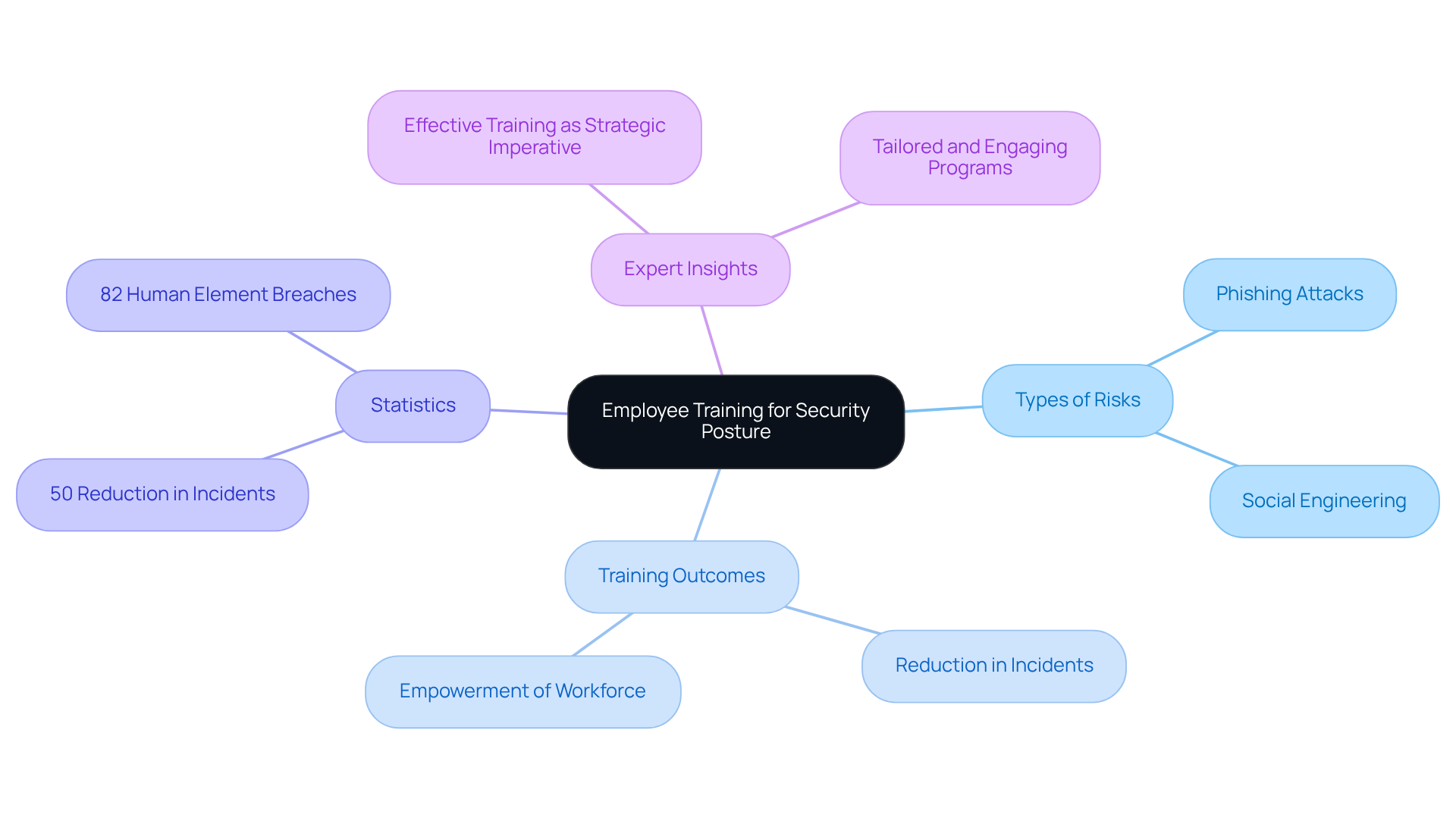
Balbix: Employee Training and Awareness for Security Posture Strength
Staff training and awareness are essential for bolstering a company's protective measures. Regular training sessions equip employees to identify potential risks, such as phishing attacks and social engineering tactics. By cultivating an environment of awareness, organizations empower their workforce to serve as the first line of defense against cyber threats. This proactive approach not only strengthens overall security but also aligns with contemporary trends that highlight the necessity for tailored, engaging training programs. Cybersecurity experts assert that effective training transforms employees from vulnerabilities into invaluable assets, significantly minimizing the risk of incidents related to human error.
Consider this: studies indicate that organizations with comprehensive awareness training programs experienced a 50% reduction in incidents over the course of a year. Additionally, the 2022 Data Breach Investigations Report by Verizon revealed that 82% of data breaches involved a human element, underscoring the critical need for training to mitigate human error. As cyber threats evolve, organizations must prioritize continuous learning and adaptation to maintain a robust defense posture. As Akshay V. notes, 'Effective awareness training is not just a regulatory checkbox; it’s a strategic necessity.
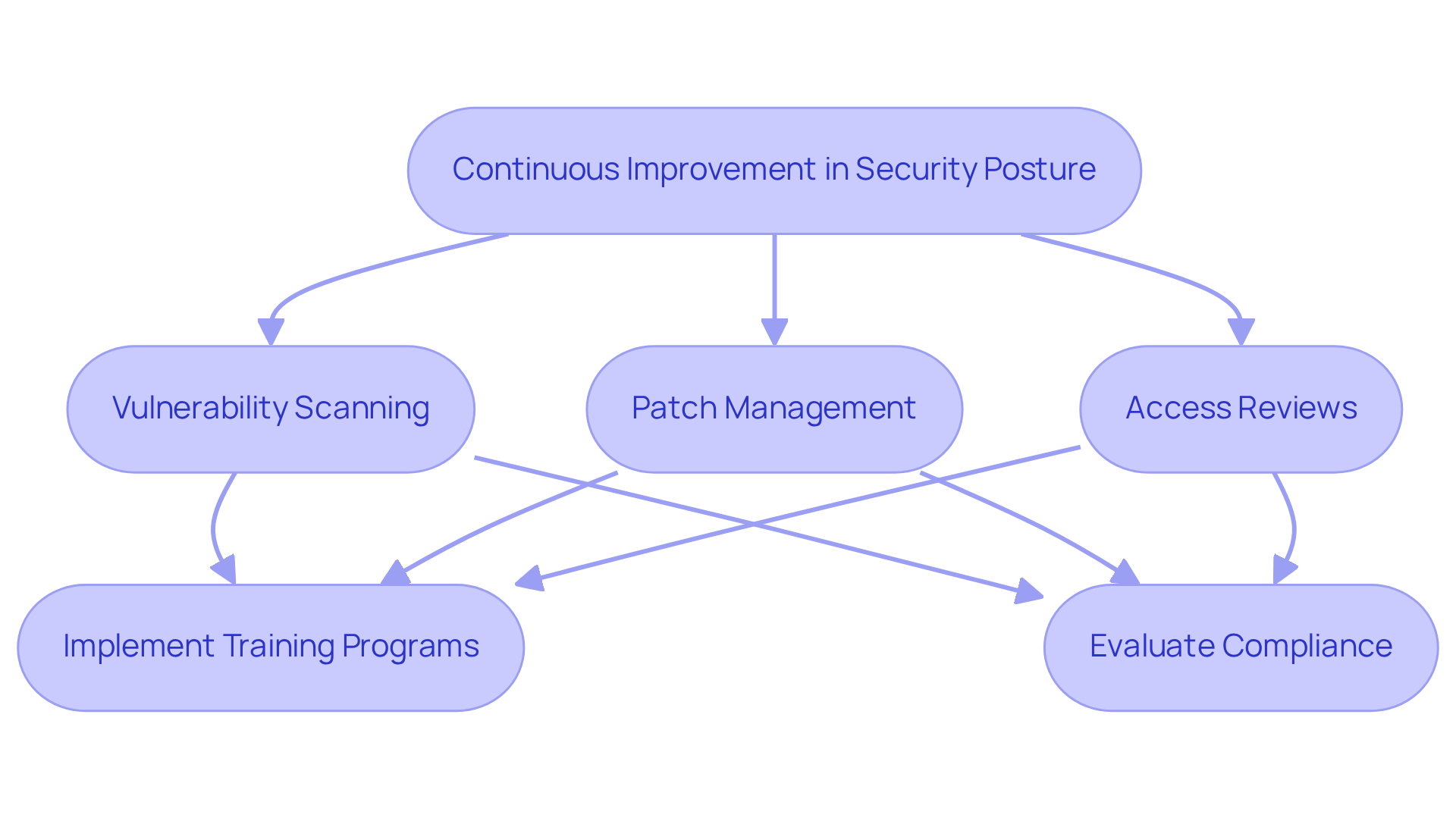
Uptycs and IBM: Continual Improvement for Evolving Security Posture
Uptycs and IBM advocate for a constant enhancement strategy for managing security risk posture, which is essential for defense contractors navigating the complexities of CMMC regulations. By consistently evaluating security measures—including vulnerability scanning, patch management, and access reviews—organizations can improve their security risk posture and adapt to the evolving risk landscape. This proactive approach not only strengthens defenses but also ensures compliance with regulatory requirements, fostering a culture of resilience and adaptability in the face of cyber challenges.
To further mitigate risks associated with human error and emerging threats, organizations should implement regular training and awareness programs. These initiatives ensure that teams remain compliant and prepared for the challenges that lie ahead. Are your security measures up to date? By embracing a continuous improvement mindset, you can safeguard your organization against potential vulnerabilities and enhance your overall security risk posture.
Conclusion
Enhancing security risk posture transcends mere compliance; it stands as a vital pillar of an organization’s resilience against the escalating tide of cyber threats. By adopting the strategies delineated in this article, organizations can proactively mitigate vulnerabilities and align with the dynamic standards of cybersecurity, particularly in anticipation of the Cybersecurity Maturity Model Certification (CMMC) requirements slated for 2025.
Key strategies include:
- The adoption of comprehensive frameworks such as the IBM Security Posture Framework
- The utilization of automated tools for asset inventory management
- The promotion of a culture of continuous improvement through regular training and awareness initiatives
Each of these components fortifies a robust defense mechanism that not only satisfies regulatory demands but also equips organizations to confront emerging threats directly.
As the cybersecurity landscape evolves, organizations must remain vigilant and adaptable. Embracing these best practices will not only enhance compliance with CMMC and other regulatory frameworks but also strengthen overall security postures. The journey toward a resilient security strategy is continuous; thus, organizations are encouraged to engage with resources like CMMC Info Hub and other industry insights to remain informed and proactive in their risk management endeavors.
Frequently Asked Questions
What is the purpose of the CMMC Info Hub?
The CMMC Info Hub serves as a vital resource for organizations aiming to achieve compliance with the Cybersecurity Maturity Model Certification (CMMC) by providing detailed roadmaps, actionable strategies, and insightful articles on CMMC compliance.
When does the initial phase of CMMC compliance begin?
The initial phase of CMMC compliance is set to begin on November 10, 2025, requiring Level 1 or Level 2 self-assessments for contract awards.
Why is safeguarding Controlled Unclassified Information (CUI) important in the defense supply chain?
Safeguarding CUI is critical to protect sensitive information throughout the defense supply chain, ensuring compliance with CMMC standards and maintaining national security.
How can organizations demonstrate compliance with CMMC?
Organizations can demonstrate compliance by proving their capability to control access, monitor usage, and respond effectively to incidents involving sensitive data, as illustrated by successful case studies of defense contractors.
What are Plans of Action & Milestones (POA&Ms) in the context of CMMC?
Plans of Action & Milestones (POA&Ms) are proactive compliance strategies that organizations can formulate to address deficiencies and outline steps for achieving CMMC compliance.
What are the consequences of non-compliance with CMMC standards?
Non-compliance with CMMC standards can result in disqualification from bidding on future Department of Defense (DoD) projects.
What resources does the CMMC Info Hub provide for users?
The CMMC Info Hub provides tailored insights, strategies, a FAQ section addressing common inquiries, and external links to relevant resources to support users navigating the compliance process.
What is the IBM Security Posture Framework?
The IBM Security Posture Framework is a comprehensive methodology for managing security risk posture in cybersecurity, emphasizing continuous monitoring, regular evaluations, and ongoing improvements.
Why is continuous monitoring important in cybersecurity?
Continuous monitoring is essential for identifying vulnerabilities, implementing necessary controls, and maintaining compliance with regulatory standards, thereby fortifying defenses against emerging threats.
What challenges might entities face when adopting the IBM Security Posture Framework?
Entities may encounter challenges such as resistance to change and the need for ongoing training, which can be addressed through early stakeholder engagement and continuous education on the framework's benefits.
What are key components of a strong security posture according to Balbix?
Key components include automated asset inventory management and ongoing risk assessment, which help organizations track assets and proactively recognize potential threats.
How does automated asset inventory management benefit organizations?
Automated asset inventory management enhances operational efficiency, ensures accurate tracking of assets, and supports compliance with cybersecurity standards, reducing the risk of financial impacts from inventory tracking failures.
What is the importance of ongoing risk evaluation?
Ongoing risk evaluation allows organizations to proactively identify and address potential threats, fostering a culture of safety awareness and ensuring a robust security risk posture in cybersecurity.
What recent trends are influencing security risk posture management?
There is a growing emphasis on automated solutions and ongoing monitoring within security risk posture management, reflecting the need for organizations to adapt to evolving cybersecurity risks.