3 Best Practices for DOD ATO Compliance Success
Learn essential strategies for achieving successful DOD ATO compliance in this concise guide.

Introduction
Achieving compliance with the Department of Defense's Authorization to Operate (ATO) is no small feat. It’s a complex journey that requires a deep understanding of stringent regulations and best practices. Organizations aiming for ATO success can gain significant advantages by implementing effective strategies and adapting to the ever-evolving industry standards. Yet, many organizations struggle; only a fraction complete essential gap analyses, and numerous entities face hurdles in developing robust cybersecurity programs.
So, what are the most effective ways to navigate this intricate compliance landscape and ensure a seamless ATO process?
Understand DOD ATO Compliance Requirements
To achieve a successful dod ato from the Department of Defense (DoD), it is crucial for entities to understand the specific regulatory requirements governing this process. The dod ato serves as a formal declaration that a system meets the necessary security standards to operate within the DoD environment. Key requirements include:
- Adherence to the Risk Management Framework (RMF)
- Implementation of security controls as outlined in NIST SP 800-53
- Continuous monitoring of security posture
Organizations utilizing cloud services should familiarize themselves with the DoD Cloud Computing Security Requirements Guide (SRG). Additionally, understanding the necessary documentation, such as the System Security Plan (SSP) and Security Assessment Report (SAR), is essential for a smooth ATO application process.
Recent data reveals that only 41% of entities have completed a comprehensive CMMC gap analysis, underscoring the challenges in meeting dod ato standards. Case studies indicate that companies have lost business due to lacking necessary certifications, highlighting the financial repercussions of regulatory failures. By thoroughly understanding these requirements, including the obstacles faced by 31% of entities struggling to develop effective cybersecurity programs with limited budgets, organizations can better prepare for the subsequent phases of the regulatory process.
For further insights, entities are encouraged to consult external resources and FAQs that address common issues related to ATO compliance.
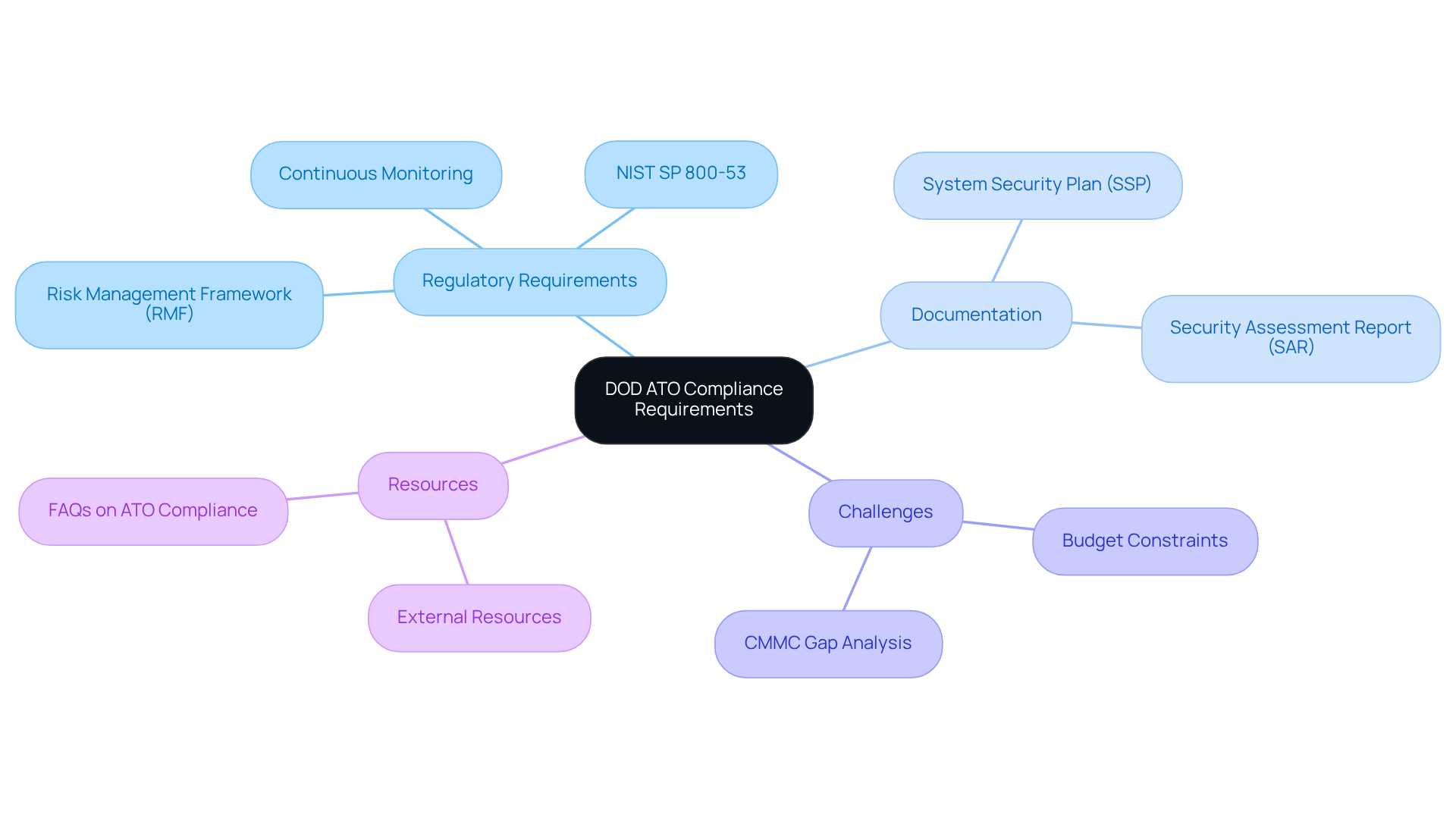
Implement Effective Strategies for ATO Compliance
To effectively navigate the ATO regulatory environment, entities must adopt a proactive approach that encompasses several key strategies.
-
Conducting a thorough gap analysis is essential. This process helps identify areas where current practices fall short of DoD requirements. Following this analysis, it’s crucial to create a comprehensive regulatory roadmap that outlines specific actions, timelines, and responsible parties.
-
Utilizing automation tools can significantly streamline documentation and monitoring processes. This not only reduces the administrative burden but also minimizes human error. Have you considered how automation could enhance your compliance efforts?
-
Regular training and awareness initiatives for personnel are vital. Ensuring that everyone understands their role in upholding regulations is key to maintaining compliance.
By leveraging practical strategies and insights from peers, as highlighted by CMMC Info Hub, defense contractors can transform confusion into clarity and effectively expedite the dod ato process.
- Real-world examples, such as the successful execution of automated regulatory checks by multiple defense contractors, illustrate the effectiveness of these strategies in achieving CMMC adherence with confidence.
In summary, adopting these strategies not only fosters compliance but also positions entities to navigate the regulatory landscape with assurance.
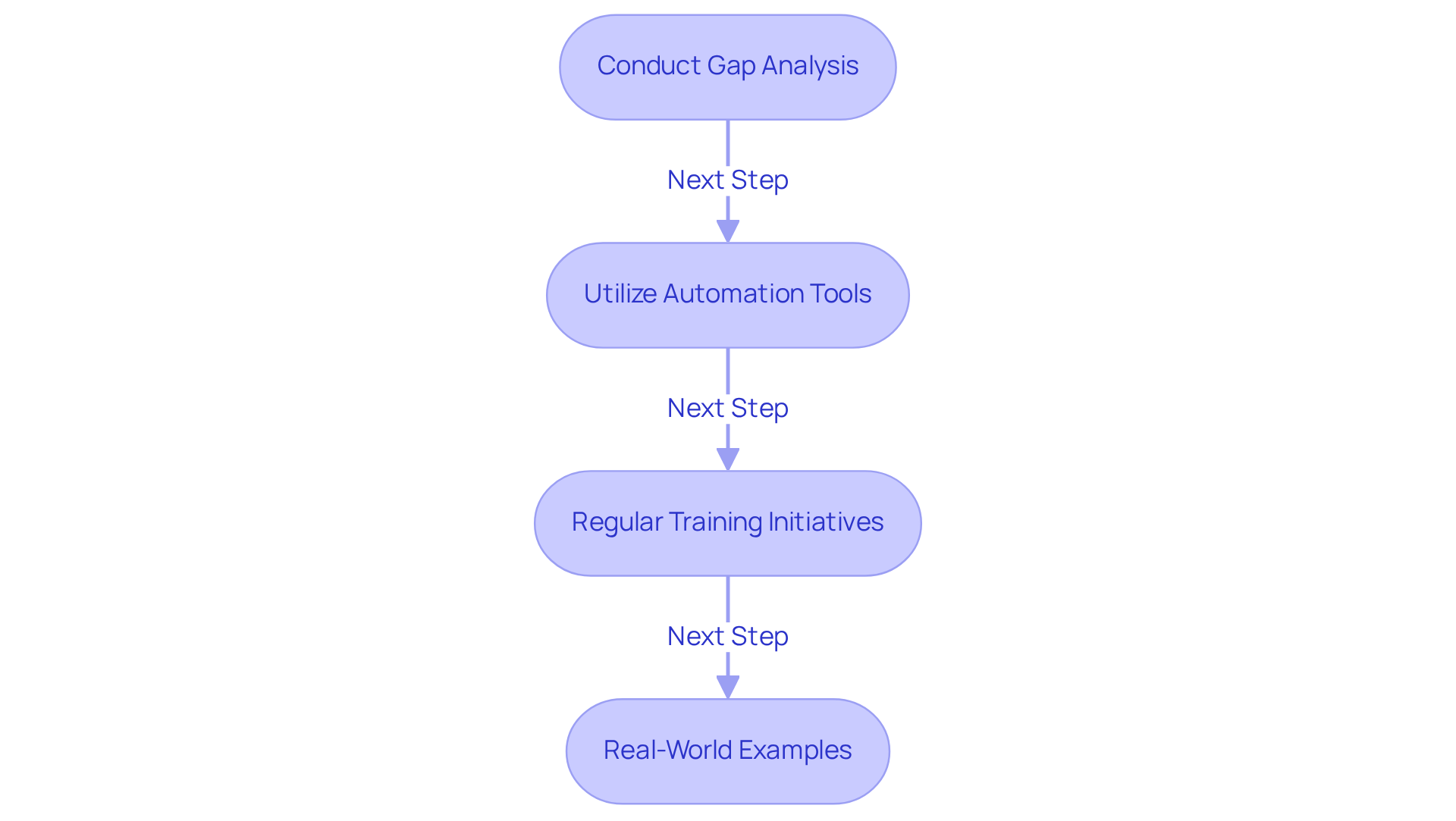
Adapt and Evolve Compliance Practices Based on Industry Insights
In the ever-evolving realm of cybersecurity, organizations must enhance their adherence practices to meet the rigorous standards set by the Department of Defense (DoD) and align with industry best practices. Are you keeping up with the latest trends? The increasing emphasis on automation and DevSecOps methodologies can offer a significant edge in this competitive landscape. Regularly revisiting and updating your regulatory frameworks in response to new DoD guidance or technological advancements is essential for achieving dod ato.
Consider leveraging industry case studies that showcase successful adaptations in regulatory processes. For example, the implementation of continuous monitoring systems enables real-time assessments of compliance, providing organizations with a proactive approach to cybersecurity.
It's also crucial to recognize that this platform may contain links to external websites. We do not control the content of these external sites and accept no responsibility for their content or availability. By fostering a culture of continuous improvement and learning, your organization can strengthen its defenses against cyber threats while ensuring ongoing compliance with dod ato requirements. Take action now - invest in your cybersecurity practices and stay ahead of the curve.
Conclusion
Achieving successful DOD ATO compliance is a complex journey that demands a thorough understanding of regulatory requirements, effective strategies, and a commitment to continuous improvement. Organizations must prioritize grasping the specific standards set forth by the Department of Defense, including adherence to the Risk Management Framework and the implementation of security controls. By doing so, entities can navigate the complexities of compliance while safeguarding their operations against potential risks.
Key insights from this discussion underscore the importance of:
- Conducting thorough gap analyses
- Leveraging automation tools
- Fostering a culture of training and awareness
These strategies are essential for identifying deficiencies, streamlining processes, and ensuring that all personnel are equipped to uphold compliance standards. Real-world examples illustrate that these practices can lead to successful outcomes, reinforcing the notion that proactive engagement is crucial in the regulatory landscape.
As the cybersecurity environment evolves, organizations must remain adaptable and responsive to new challenges and technological advancements. Investing in cybersecurity practices and embracing industry insights will not only enhance compliance but also fortify defenses against emerging threats. By taking decisive action now, entities can position themselves for long-term success in DOD ATO compliance, ensuring they meet the rigorous standards necessary to thrive in a competitive landscape.
Frequently Asked Questions
What is the purpose of a DoD ATO?
The DoD ATO (Authorization to Operate) serves as a formal declaration that a system meets the necessary security standards to operate within the Department of Defense environment.
What are the key requirements for achieving a DoD ATO?
Key requirements include adherence to the Risk Management Framework (RMF), implementation of security controls as outlined in NIST SP 800-53, and continuous monitoring of security posture.
What should organizations using cloud services do regarding DoD ATO compliance?
Organizations utilizing cloud services should familiarize themselves with the DoD Cloud Computing Security Requirements Guide (SRG).
What documentation is necessary for a smooth ATO application process?
Essential documentation includes the System Security Plan (SSP) and the Security Assessment Report (SAR).
What challenges do organizations face in meeting DoD ATO standards?
Recent data shows that only 41% of entities have completed a comprehensive CMMC gap analysis, and 31% struggle to develop effective cybersecurity programs due to limited budgets.
What are the potential consequences of failing to meet DoD ATO requirements?
Companies have lost business due to lacking necessary certifications, highlighting the financial repercussions of regulatory failures.
Where can entities find more information about ATO compliance?
Entities are encouraged to consult external resources and FAQs that address common issues related to ATO compliance.