4 Best Practices for Effective SSP Documentation Compliance
Master effective SSP documentation with key components for compliance and enhanced cybersecurity.

Introduction
Crafting a comprehensive System Security Plan (SSP) is not merely a regulatory requirement; it stands as a strategic imperative for organizations striving for CMMC compliance. Understanding and implementing best practices in SSP documentation can significantly enhance an entity's cybersecurity posture while ensuring adherence to critical compliance standards.
However, with the complexities surrounding security controls, risk assessments, and continuous monitoring, how can organizations effectively navigate the intricacies of SSP documentation? This article explores four essential practices that empower organizations to streamline their SSP processes, bolster security measures, and foster collaborative efforts across teams.
By delving into these practices, organizations can not only meet compliance requirements but also strengthen their overall security framework. Let's embark on this journey towards effective SSP documentation.
Identify Key Components of an Effective SSP
An effective System Security Plan (SSP) is crucial for achieving CMMC compliance, encompassing several critical components:
-
System Recognition: Clearly define the entity's purpose, scope, and boundaries. Recognizing which networks and data are part of CMMC adherence is essential. Precise identification of the framework establishes the basis for all subsequent protective measures and adherence efforts. Entities that effectively establish their system limits often experience a more seamless regulatory process.
-
Protection Measures: Document all protection measures implemented to safeguard Controlled Unclassified Information (CUI) and Federal Contract Information (FCI). This should include both technical and administrative controls, ensuring a robust defense against potential threats. Efficient monitoring and recording of adherence to standards are crucial, as they enhance a company's overall cybersecurity stance. Peer insights reveal that entities employing a layered protection strategy frequently achieve improved adherence results.
-
Roles and Responsibilities: Clearly specify who is responsible for maintaining and implementing each control. This guarantees accountability within the entity and fosters a culture of safety awareness. Cybersecurity specialists emphasize that defined roles are vital for effective governance management, helping to mitigate risks associated with human error. Organizations that designate specific roles for regulatory tasks often observe enhanced adherence to safety protocols.
-
Risk Assessment: Summarize the risk assessment process that identifies potential threats and vulnerabilities to the system. A comprehensive risk evaluation is not merely a compliance necessity; it’s a proactive step to enhance safety. Organizations that regularly conduct risk assessments are better positioned to adapt to evolving threats. Utilizing peer insights can further refine this process, leading to more effective risk management strategies.
-
Continuous Monitoring Strategy: Describe how the entity will assess the efficiency of protective measures over time. This includes regular assessments and updates to ensure that security measures remain effective against emerging threats. Ongoing observation is increasingly recognized as a best practice in cybersecurity, aiding entities in upholding regulations and responding promptly to incidents. Implementing practical strategies for continuous monitoring can significantly enhance compliance outcomes.
By meticulously documenting these components and incorporating practical strategies, entities can develop SSP documentation that not only meets CMMC requirements but also significantly strengthens their cybersecurity posture, ultimately enhancing their readiness for defense contracts.
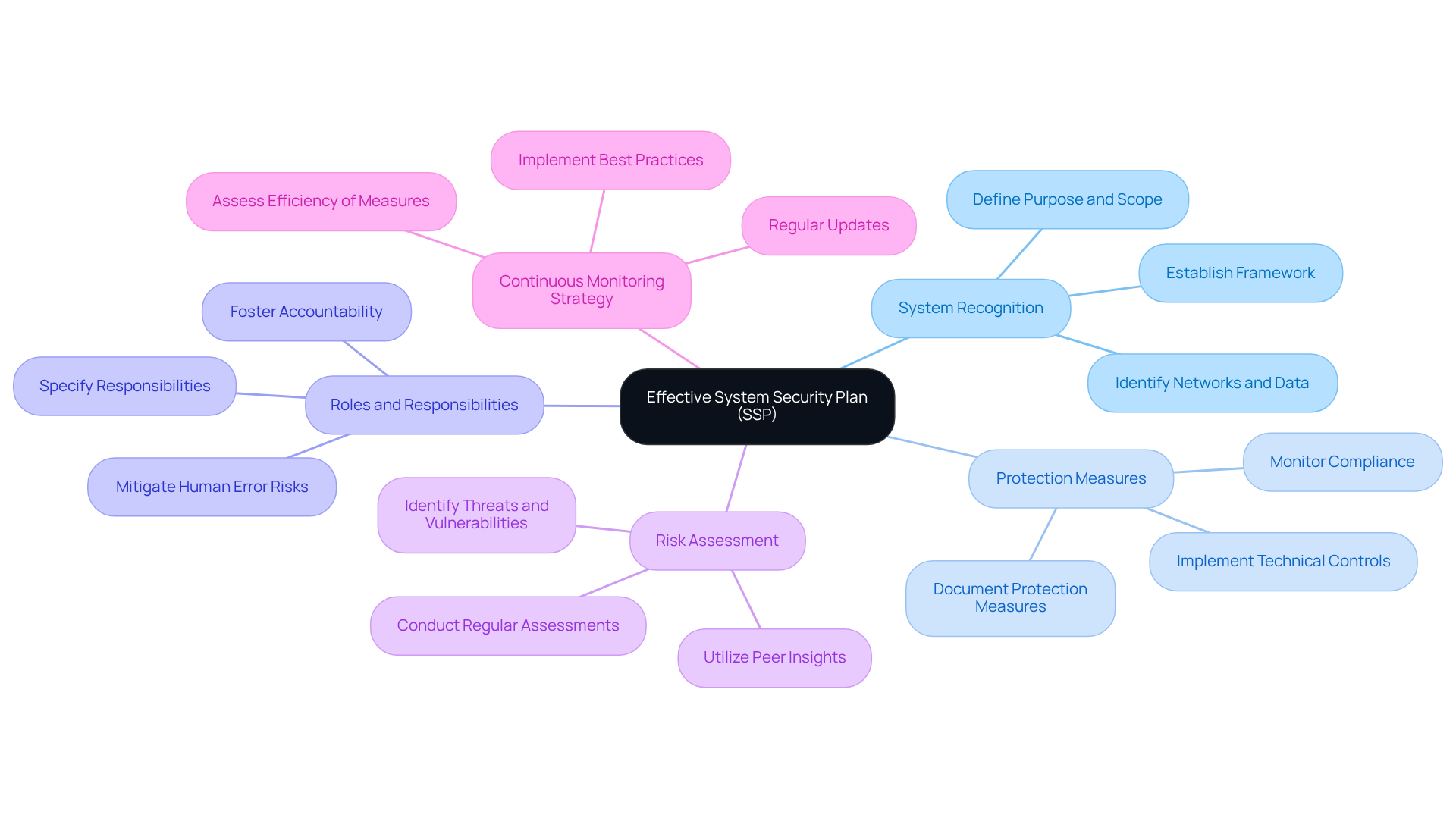
Document Security Controls Thoroughly
To document security controls effectively, organizations must embrace the following best practices:
-
Detail Each Control: Start by providing a comprehensive description for every protective control. Outline its purpose, implementation, and the specific risks it mitigates. This clarity is essential for understanding the role of each control in your security framework.
-
Use Standardized Templates: Implement standardized documentation templates to ensure consistency and completeness across all security controls. This method simplifies the documentation process, enhances clarity, and promotes adherence throughout the organization. Are your teams using the same templates?
-
Include Evidence of Implementation: Attach supporting evidence such as screenshots, logs, or policy documents that demonstrate the active functionality of each control. This evidence is vital for validating adherence during assessments. How can you ensure that your controls are functioning as intended?
-
Version Control: Maintain strict version control for all documentation. This practice ensures that updates are meticulously tracked, previous versions are archived appropriately, and a formal process for proposing and approving changes is established. This guarantees that all modifications are documented and communicated effectively. Are your version control practices robust enough?
-
Regular Evaluations: Arrange regular assessments of documentation, at least once a year, to guarantee it stays up-to-date and accurately reflects any alterations in the risk environment or regulatory needs. Inform all impacted staff of any policy changes to maintain awareness and adherence. When was your last evaluation?
By adhering to these practices, organizations can establish a strong ssp documentation framework that not only aids in compliance but also significantly enhances their overall safety stance.
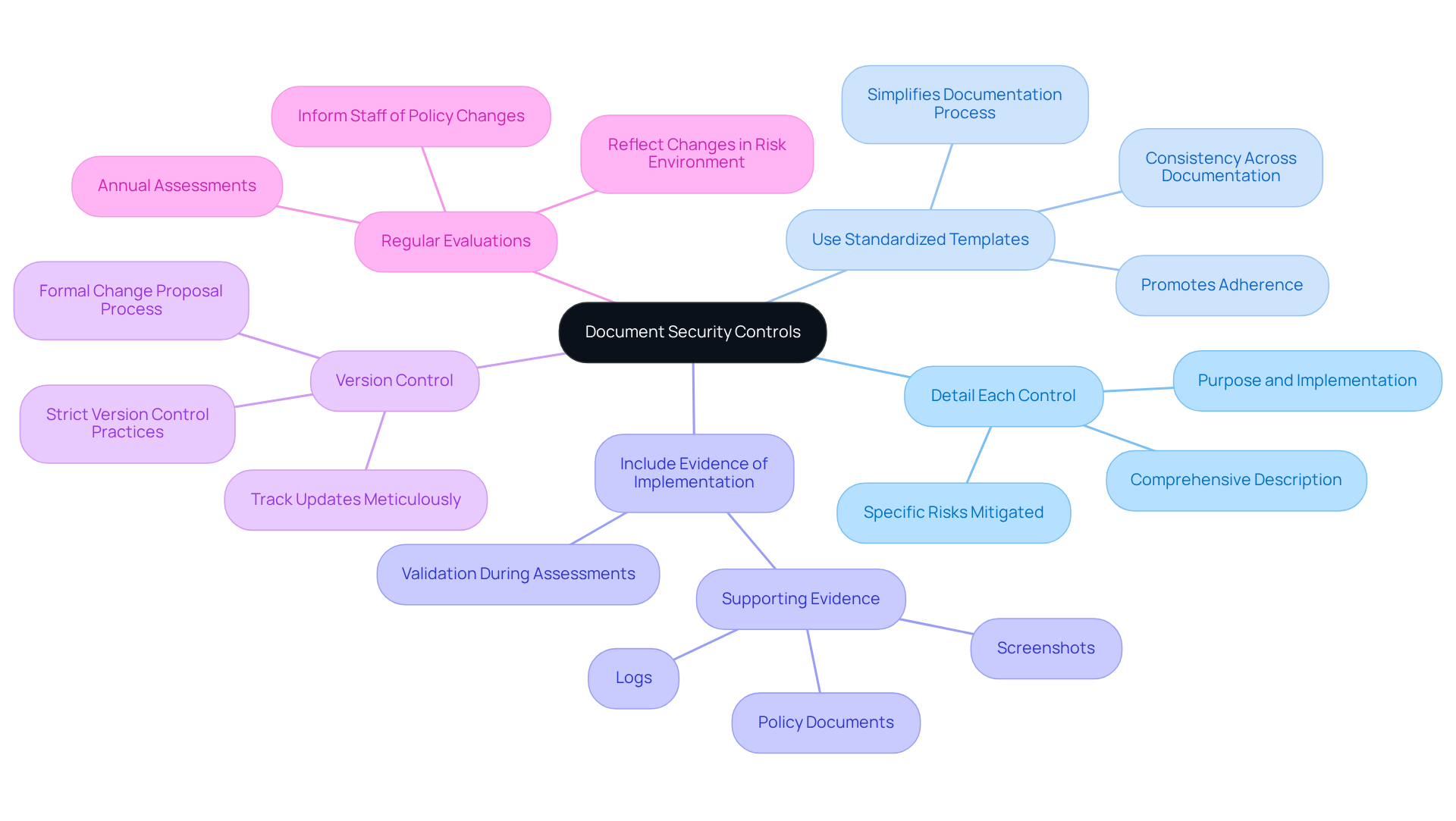
Establish Continuous Monitoring and Updates
To establish an effective continuous monitoring strategy, organizations must follow these essential steps:
-
Define Monitoring Objectives: Start by clearly outlining the specific aspects of your setup that need observation. This includes protective measures, user access, and performance metrics. What are you aiming to achieve with your monitoring efforts?
-
Implement Automated Tools: Leverage automated monitoring tools like Security Information and Event Management (SIEM) systems, Intrusion Detection Systems (IDS), and Vulnerability Scanners. These tools continuously assess the effectiveness of security controls and detect anomalies in real-time. This significantly enhances your organization’s ability to respond to threats promptly. Notably, 66% of companies report that compliance mandates are driving their cybersecurity spending, underscoring the financial implications of effective monitoring tools.
-
Conduct Regular Vulnerability Scans: Schedule regular vulnerability scans and penetration testing to identify and remediate potential weaknesses in your system. This proactive strategy is essential; entities that systematically search for vulnerabilities are less exposed to cyber risks. Ongoing observation helps maintain a strong defense stance, lowering the likelihood of breaches. Consider this: the average expense of a data breach in the United States was $10.22 million in 2025.
-
Maintain Comprehensive Audit Logs: Keep detailed audit logs that monitor access and alterations to your platform. This practice allows organizations to examine activities and recognize suspicious behavior, which is crucial for upholding integrity. Are you tracking the right data?
-
Update the SSP Regularly: Ensure that your System Security Plan (SSP) is updated at least annually or whenever significant changes occur in the system or its environment. This guarantees that the SSP accurately reflects your current protective stance and adherence status. The average lifecycle of a breach in 2025 fell to 241 days, highlighting the urgency of timely monitoring and response.
By implementing these strategies, organizations can adopt a proactive approach to security and compliance, effectively mitigating risks and enhancing readiness for CMMC compliance. However, it’s important to be aware of challenges such as data overload and resource requirements that can complicate continuous monitoring efforts.
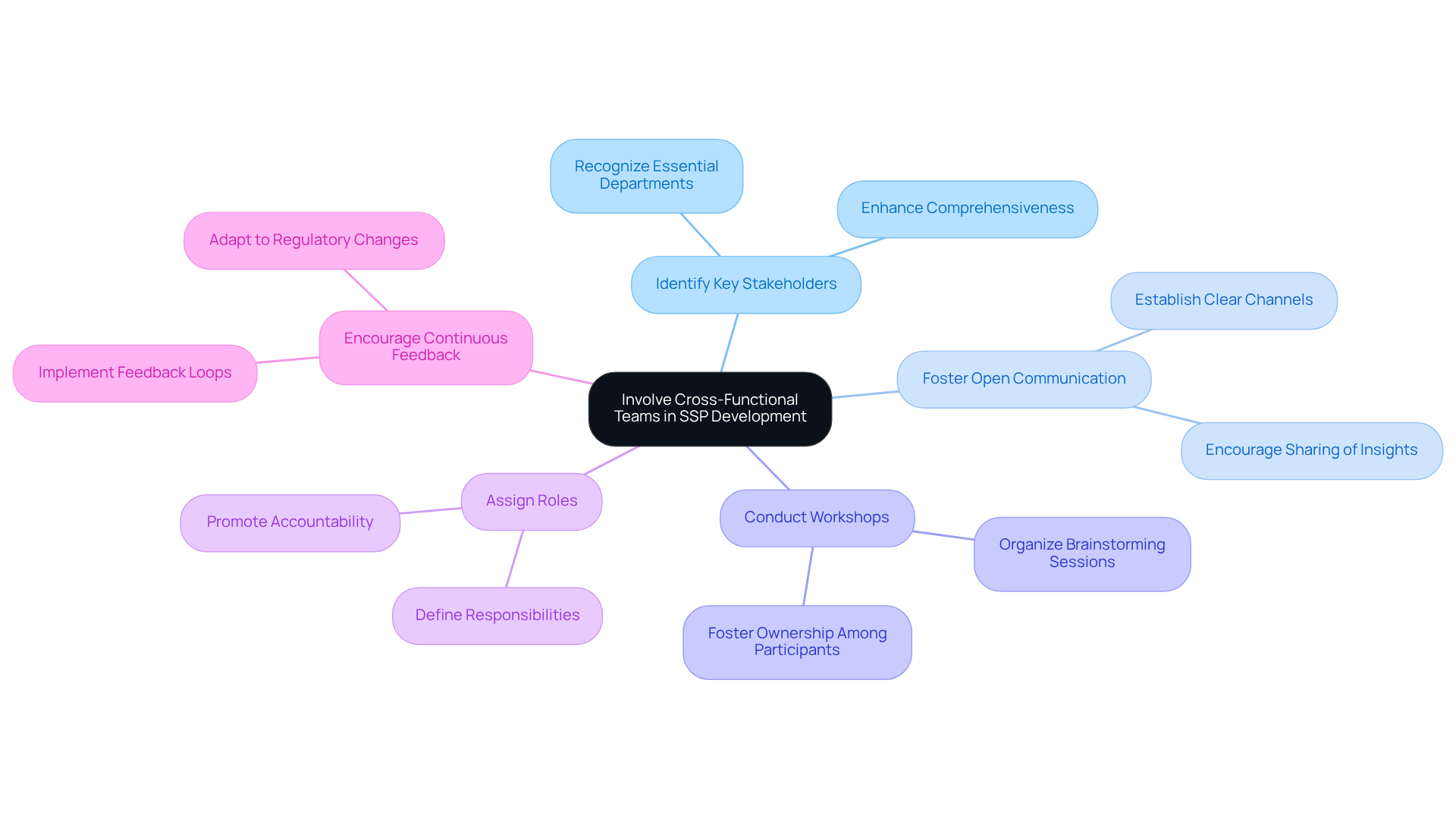
Involve Cross-Functional Teams in SSP Development
To effectively engage cross-functional teams in the development of System Security Plans (SSPs), organizations must adopt the following best practices:
-
Identify Key Stakeholders: Recognizing essential departments such as IT, legal, regulatory, and operations is crucial. Their participation in the SSP documentation development process ensures that all relevant perspectives are included, enhancing the comprehensiveness of the plan.
-
Foster Open Communication: Establishing clear channels for communication among team members encourages the sharing of insights, challenges, and best practices. This is vital for cultivating a collaborative environment.
-
Conduct Workshops: Organizing workshops or brainstorming sessions allows for diverse input from various teams. This collaborative approach not only enriches the SSP documentation but also fosters a sense of ownership among participants.
-
Assign Roles: Clearly defining roles and responsibilities for each team member involved in the SSP development promotes accountability. It ensures that everyone understands their contributions to the process.
-
Encourage Continuous Feedback: Implementing a feedback loop enables team members to provide ongoing input and suggestions for improving the SSP as it evolves. Continuous involvement is essential for adapting to changing regulatory demands and enhancing protective measures.
Integrating these practices helps organizations avoid common pitfalls, such as neglecting high-value stakeholders, and underscores the importance of collaboration in SSP documentation adherence. By leveraging the strengths of cross-functional teams in this manner, organizations can develop a more robust and effective SSP that not only meets compliance requirements but also bolsters overall security.
Conclusion
An effective System Security Plan (SSP) is crucial for organizations aiming for compliance, especially with standards like CMMC. Have you considered how understanding and implementing the key components of an SSP - such as system recognition, protection measures, defined roles, risk assessments, and continuous monitoring - can not only help meet compliance requirements but also strengthen your cybersecurity defenses?
This article underscores essential best practices for ensuring effective SSP documentation compliance. Key strategies include:
- Thoroughly documenting security controls
- Utilizing standardized templates
- Maintaining version control
- Involving cross-functional teams in the development process
Each of these strategies plays a vital role in creating a comprehensive and robust SSP, ensuring that all security aspects are addressed while keeping the organization agile in the face of evolving threats and regulatory demands.
Ultimately, the importance of a well-documented and continuously updated SSP cannot be overstated. Organizations are urged to adopt these best practices, fostering collaboration and communication across departments to enhance their security posture. By doing so, they not only protect their sensitive information but also position themselves favorably for future compliance and operational excellence. Are you ready to take the next step in fortifying your organization’s security framework?
Frequently Asked Questions
What is the purpose of a System Security Plan (SSP)?
The purpose of a System Security Plan (SSP) is to achieve CMMC compliance by outlining critical components necessary for safeguarding Controlled Unclassified Information (CUI) and Federal Contract Information (FCI).
What are the key components of an effective SSP?
The key components of an effective SSP include system recognition, protection measures, roles and responsibilities, risk assessment, and a continuous monitoring strategy.
What does "system recognition" entail in the context of an SSP?
System recognition involves clearly defining the entity's purpose, scope, and boundaries, including identifying which networks and data are part of CMMC adherence. This establishes the foundation for protective measures.
What types of protection measures should be documented in an SSP?
Protection measures should include both technical and administrative controls implemented to safeguard CUI and FCI, along with efficient monitoring and recording of adherence to standards.
Why are roles and responsibilities important in an SSP?
Clearly specifying roles and responsibilities ensures accountability within the entity and fosters a culture of safety awareness, which is vital for effective governance management and mitigating risks associated with human error.
What is the significance of conducting a risk assessment in an SSP?
A risk assessment identifies potential threats and vulnerabilities to the system and is a proactive step to enhance safety, helping organizations adapt to evolving threats.
How does a continuous monitoring strategy contribute to an SSP?
A continuous monitoring strategy assesses the efficiency of protective measures over time through regular assessments and updates, ensuring that security measures remain effective against emerging threats.
How can documenting these SSP components strengthen cybersecurity posture?
By meticulously documenting these components and incorporating practical strategies, entities can enhance their cybersecurity posture, meet CMMC requirements, and improve readiness for defense contracts.