4 Key Insights for Mastering CMMC Enclave Compliance
Master CMMC enclave compliance with key insights and strategies for defense contractors.

Introduction
Navigating the complexities of CMMC enclave compliance can feel like traversing a minefield for many organizations within the defense industrial base. With a staggering 58% of entities still unprepared for the evolving CMMC 2.0 requirements, the stakes are high. Failure to comply could lead to severe repercussions, including the loss of crucial defense contracts.
This article delves into four key insights that clarify the compliance landscape and equip organizations with actionable strategies to enhance their security posture and meet regulatory standards. How can businesses effectively leverage these insights to transform compliance challenges into opportunities for growth and resilience?
By understanding the nuances of CMMC compliance, organizations can not only safeguard their operations but also position themselves for future success. Let's explore these insights and discover how they can pave the way for a more secure and compliant future.
CMMC Info Hub: Your Essential Resource for CMMC Enclave Compliance
This information hub serves as a comprehensive resource center tailored for organizations striving to achieve compliance with the CMMC enclave. It offers detailed roadmaps, practical strategies, and insightful articles that demystify the complexities of the framework. By utilizing peer insights and expert guidance, users can confidently navigate the stringent requirements set forth by the Department of Defense. This platform not only simplifies the regulatory process but also empowers organizations to enhance their security posture effectively.
Consider this: while 81% of defense industrial base (DIB) entities have embarked on their CMMC adherence journey, only 13% currently meet Level 1 standards, and a staggering 58% remain unprepared for CMMC 2.0 requirements. Furthermore, organizations that conduct thorough gap evaluations are significantly better positioned for compliance, with 73% of these companies having fully documented cybersecurity policies.
The potential consequences of non-compliance - such as losing defense contracts or facing prosecution under the US Department of Justice Civil Cyber-Fraud Initiative - underscore the urgency and importance of adhering to regulations within the defense sector.
Additionally, this platform may include links to external websites. While we do not control their content, the presence of these links does not imply our endorsement.
Understand CMMC Enclave Compliance Requirements
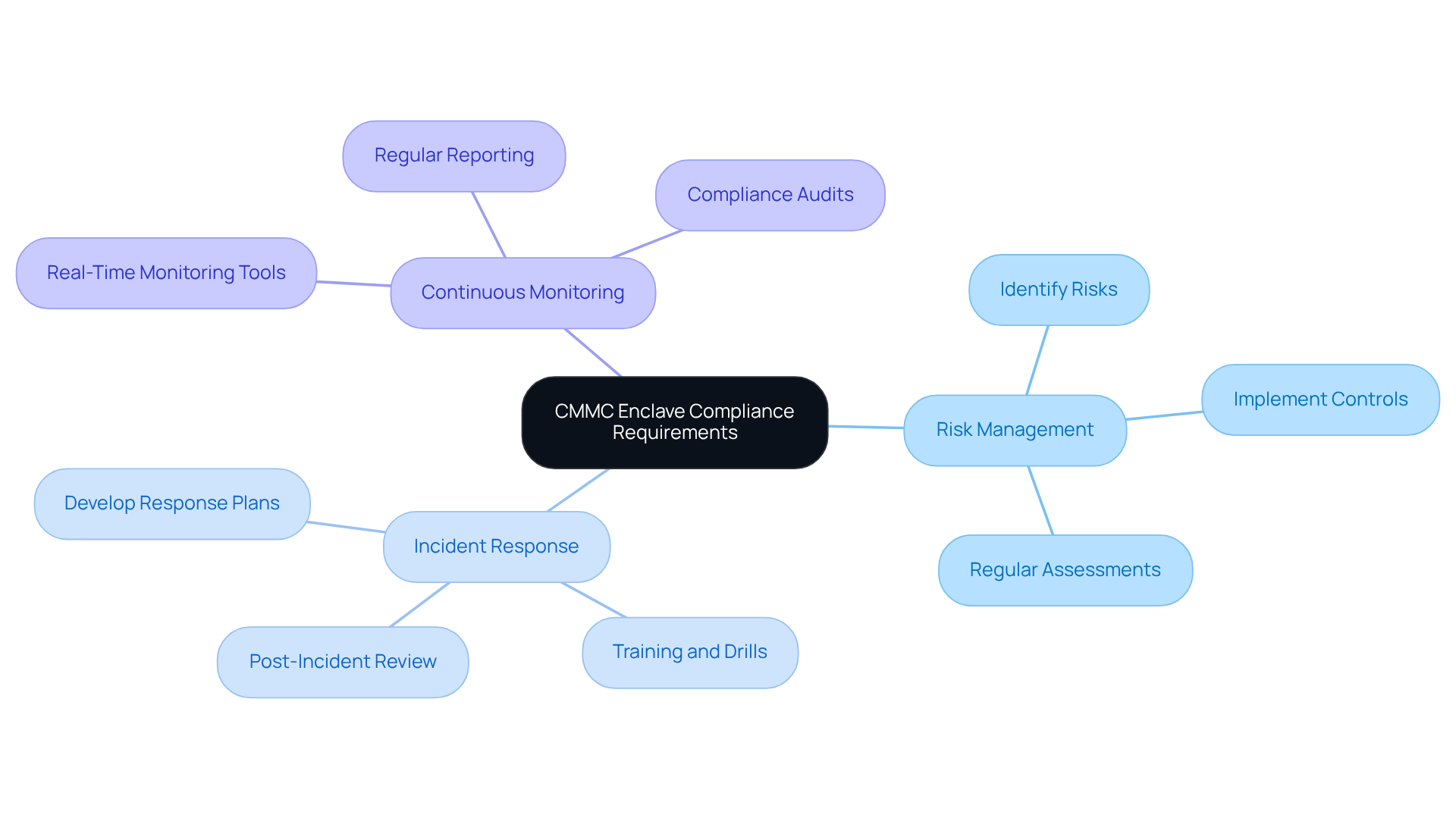
To master compliance with the CMMC enclave effectively, organizations must grasp the specific requirements outlined in the framework. This includes understanding various certification levels, essential security controls, and the assessment process. Key areas of focus are:
- Risk management
- Incident response
- Continuous monitoring
Why is this knowledge crucial? Familiarity with these elements not only prepares organizations for assessments in the CMMC enclave but also ensures they meet the stringent standards necessary for securing defense contracts. Surprisingly, many organizations remain unaware of the full range of requirements. This highlights the critical need for thorough education and strategic planning in this field.
By prioritizing compliance and leveraging available resources, organizations can position themselves for success in the competitive landscape of defense contracting.
Leverage Microsoft's Secure Enclaves for Compliance Support
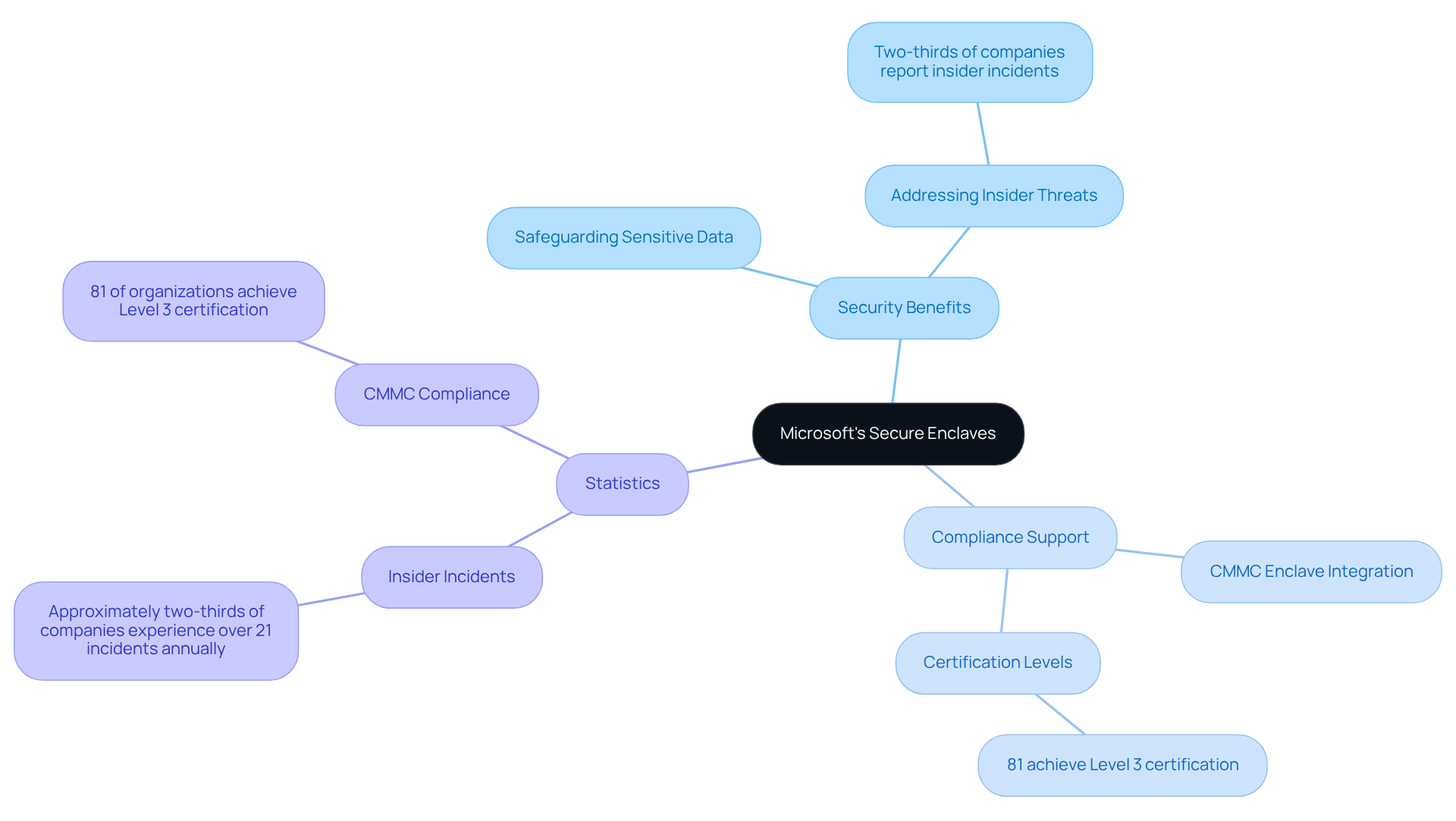
Microsoft's Secure Enclaves present a powerful solution for businesses aiming to elevate their security standards. These secure environments are meticulously crafted to safeguard sensitive data and Controlled Unclassified Information (CUI), facilitating secure collaboration while meeting stringent information security requirements. By incorporating the CMMC enclave into their cybersecurity frameworks, organizations can effectively meet the necessary security measures for certification compliance.
This technology not only supports adherence to regulations but also significantly bolsters overall data security, addressing the pressing concerns surrounding insider threats and cyber-espionage. Did you know that approximately two-thirds of companies report experiencing over 21 insider incidents annually? This statistic highlights the critical need for implementing Secure Enclaves as a protective strategy. Furthermore, 81% of organizations achieve Level 3 certification upon project completion by leveraging these solutions.
As businesses increasingly recognize the value of these solutions, many are turning to the CMMC enclave offered by Microsoft to ensure robust protection of sensitive information while keeping pace with evolving regulatory demands. As Corrin Jones, Director of Digital Demand Generation, aptly puts it, 'Secure enclaves provide the cybersecurity necessary to meet strict compliance standards 2.0 regulations.' This approach transforms uncertainty into clarity, offering practical tactics and insights that empower defense contractors to confidently attain cybersecurity maturity model certification.
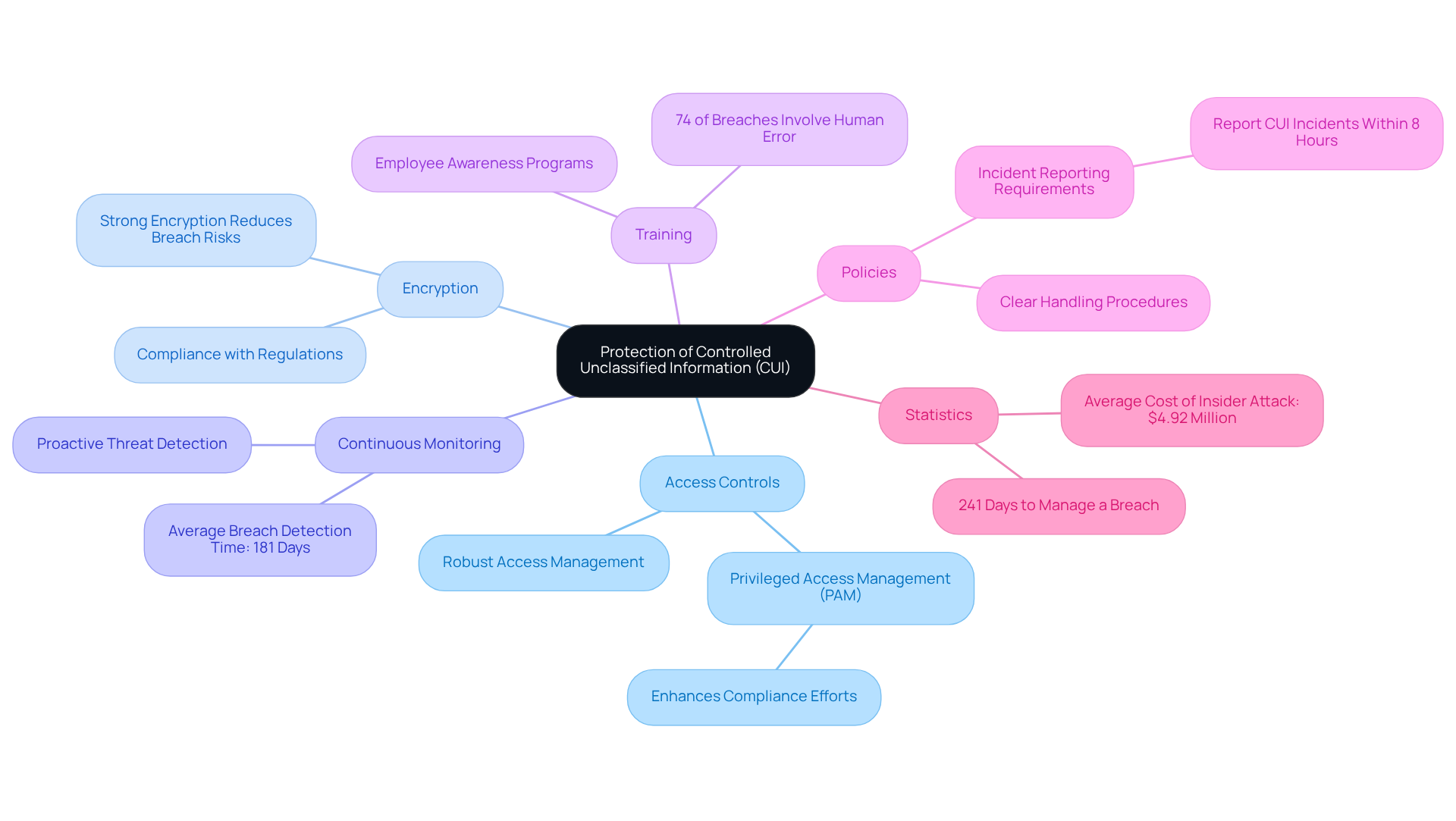
Prioritize Protection of Controlled Unclassified Information (CUI)
Protecting Controlled Unclassified Information (CUI) is essential for organizations striving to achieve compliance within the CMMC enclave. Robust access controls, encryption, and continuous monitoring practices are crucial to prevent unauthorized access and data breaches. Did you know that entities employing strong encryption and Privileged Access Management (PAM) solutions significantly enhance their compliance efforts and reduce breach costs? In fact, malicious insider attacks have led to the highest average breach costs among initial threat vectors, averaging $4.92 million in 2025. Moreover, it takes organizations an average of 181 days to detect a data breach and 60 days to manage it, totaling 241 days. This stark reality underscores the need for proactive measures in safeguarding CUI.
Training employees on the importance of CUI protection and establishing clear policies for handling sensitive information are also critical components of a comprehensive security strategy. With 74% of all breaches involving human error, privilege misuse, stolen credentials, or social engineering, fostering a culture of security awareness can significantly mitigate risks. As highlighted in 'The Ultimate Guide to Achieving Compliance,' organizations must prioritize the development and maintenance of effective policies and procedures to ensure adherence. By doing so, they not only meet the requirements of the CMMC enclave but also bolster their overall cybersecurity posture, positioning themselves advantageously in the competitive defense contracting landscape.
Conclusion
Achieving compliance with the CMMC enclave stands as a pivotal goal for organizations involved in defense contracting. Why is this so crucial? Understanding the complexities of the CMMC framework-including the specific certification requirements and the necessity for robust cybersecurity measures-is essential for navigating this intricate landscape. By prioritizing compliance and utilizing available resources, organizations can not only meet the required standards but also bolster their overall security posture.
This article underscores several key insights vital for mastering CMMC enclave compliance. It highlights the significance of:
- Grasping compliance requirements
- Leveraging technologies like Microsoft’s Secure Enclaves for enhanced security
- Prioritizing the protection of Controlled Unclassified Information (CUI)
Moreover, the statistics presented reveal the current state of compliance within the defense industrial base, emphasizing the urgency for organizations to take proactive steps to avoid the severe repercussions of non-compliance.
Ultimately, the journey toward CMMC enclave compliance demands a commitment to continuous improvement and a strategic approach to cybersecurity. Organizations must not only concentrate on fulfilling regulatory requirements but also cultivate a culture of security awareness among their employees. How can they achieve this? By doing so, they can significantly mitigate risks, safeguard sensitive information, and position themselves for success in the competitive arena of defense contracting. Embracing these insights empowers organizations to turn compliance challenges into opportunities for growth and resilience.
Frequently Asked Questions
What is the CMMC Info Hub?
The CMMC Info Hub is a comprehensive resource center designed for organizations seeking to achieve compliance with the CMMC enclave, offering roadmaps, strategies, and articles to help navigate the framework's complexities.
What resources does the CMMC Info Hub provide?
The hub provides detailed roadmaps, practical strategies, insightful articles, peer insights, and expert guidance to assist organizations in meeting the stringent requirements of the CMMC framework.
Why is CMMC compliance important for organizations?
CMMC compliance is crucial as non-compliance can lead to losing defense contracts or facing prosecution under the US Department of Justice Civil Cyber-Fraud Initiative, making adherence to regulations in the defense sector urgent and important.
What statistics highlight the current state of CMMC compliance among defense industrial base entities?
As of now, 81% of defense industrial base entities have started their CMMC compliance journey, but only 13% meet Level 1 standards, and 58% are unprepared for CMMC 2.0 requirements.
How can organizations improve their chances of achieving CMMC compliance?
Organizations that conduct thorough gap evaluations are better positioned for compliance, with 73% of these companies having fully documented cybersecurity policies.
Does the CMMC Info Hub include links to external websites?
Yes, the CMMC Info Hub may include links to external websites; however, the hub does not control the content of these sites, and their presence does not imply endorsement.




