4 Key Steps to Meet CMMC Certification Requirements for Contractors
Streamline your path to CMMC certification requirements with essential strategies and resources.

Introduction
Navigating the complex landscape of Cybersecurity Maturity Model Certification (CMMC) can be a daunting task for contractors eager to secure defense contracts. With the Department of Defense tightening its grip on compliance requirements, understanding the CMMC framework is not just beneficial - it's essential for survival in a competitive market. This article reveals four critical steps contractors can take to meet CMMC certification requirements, addressing common challenges and offering practical strategies to bridge compliance gaps.
How can organizations effectively position themselves to thrive amidst the evolving regulatory environment?
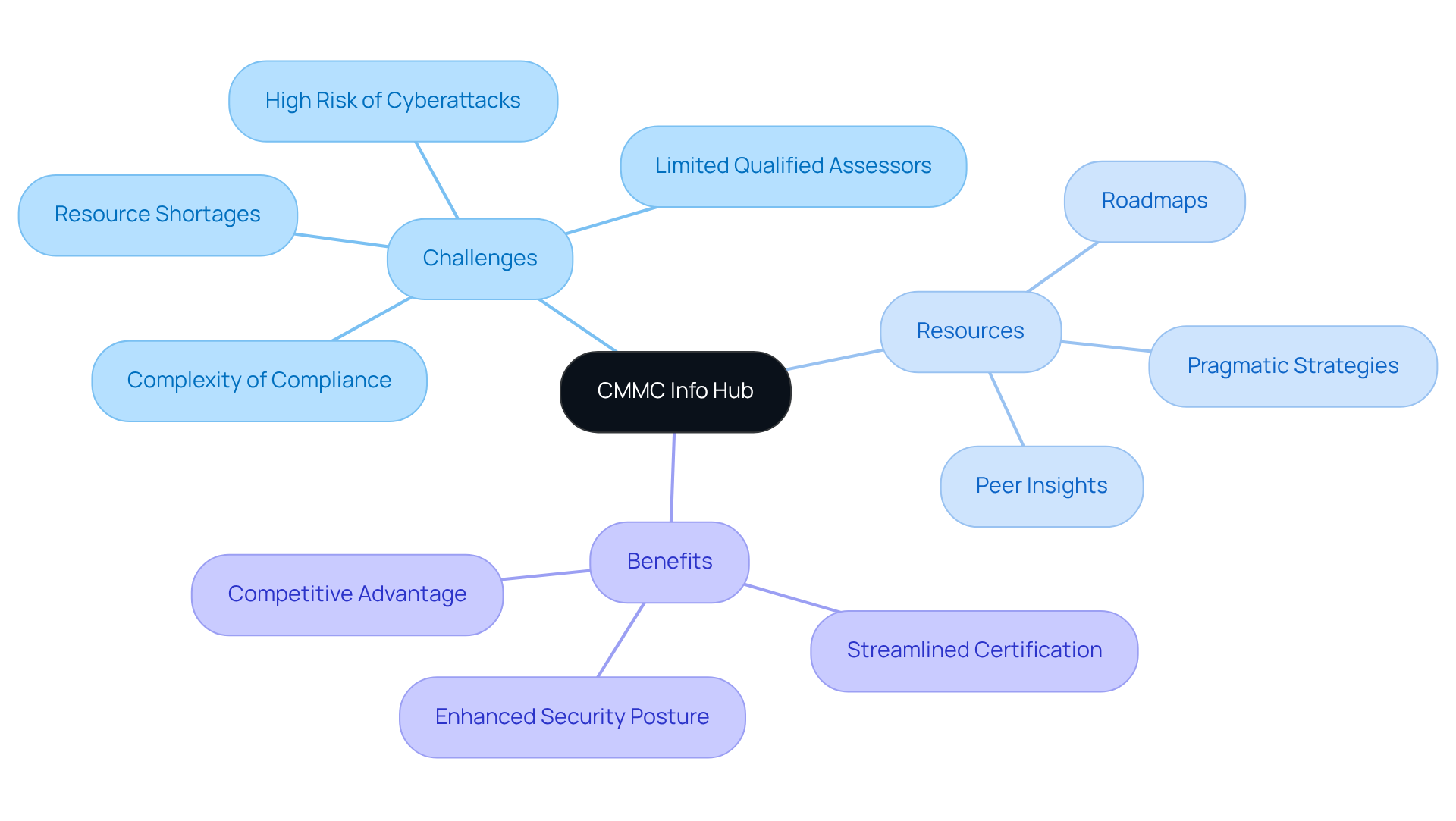
CMMC Info Hub: Your Essential Resource for CMMC Certification Requirements
CMMC Info Hub serves as a vital knowledge repository for organizations aiming to meet the CMMC certification requirements for compliance with the Cybersecurity Maturity Model Certification (CMMC). Are you facing challenges in navigating the complexities of DoD information security requirements? This Hub is specifically designed to address the practical obstacles encountered by defense suppliers. It offers comprehensive roadmaps, pragmatic strategies, and peer insights that empower suppliers to effectively maneuver through these intricacies.
With the alarming rise in breaches within the defense sector, the need for robust regulatory measures has never been more pressing. By providing access to proven practices, Info Hub simplifies regulatory processes and enhances security postures, ensuring that contractors meet the CMMC certification requirements necessary to secure defense contracts. This proactive approach not only mitigates risks but also positions organizations favorably in an increasingly competitive landscape where regulatory compliance is crucial for contract acquisition.
In summary, leveraging the resources available through CMMC Info Hub can significantly streamline your path to fulfilling the CMMC certification requirements and bolster your organization's security framework. Don't wait - take action now to safeguard your future in the defense industry.
Understand the CMMC Framework and Its Requirements
The framework of CMMC certification requirements comprises three maturity levels, each with increasing cybersecurity requirements. Level 1 emphasizes the basic safeguarding of Federal Contract Information (FCI), requiring adherence to 15 fundamental controls that focus on essential cyber hygiene and physical security. In contrast, Level 2 addresses Controlled Unclassified Information (CUI), necessitating compliance with 93 additional practices that bolster data protection measures.
Understanding these levels is crucial for builders, as they dictate the specific controls and practices necessary to meet CMMC certification requirements. Familiarity with the framework not only prepares organizations for assessments but also aligns their cybersecurity strategies with the expectations of the Department of Defense.
Beginning in 2025, nearly all DoD solicitations will incorporate CMMC certification requirements for adherence to cybersecurity maturity models. This makes it imperative for suppliers to stay informed and proactive in their compliance efforts. Recent trends indicate that major defense firms are increasingly prioritizing compliance, with companies like Boeing and Lockheed Martin mandating specific certifications as prerequisites for contract awards.
This shift underscores the urgency for builders to comprehend and implement the necessary measures to secure their positions within the defense supply chain. Are you ready to take the next step? For further information, please refer to our FAQs and external resources linked below.
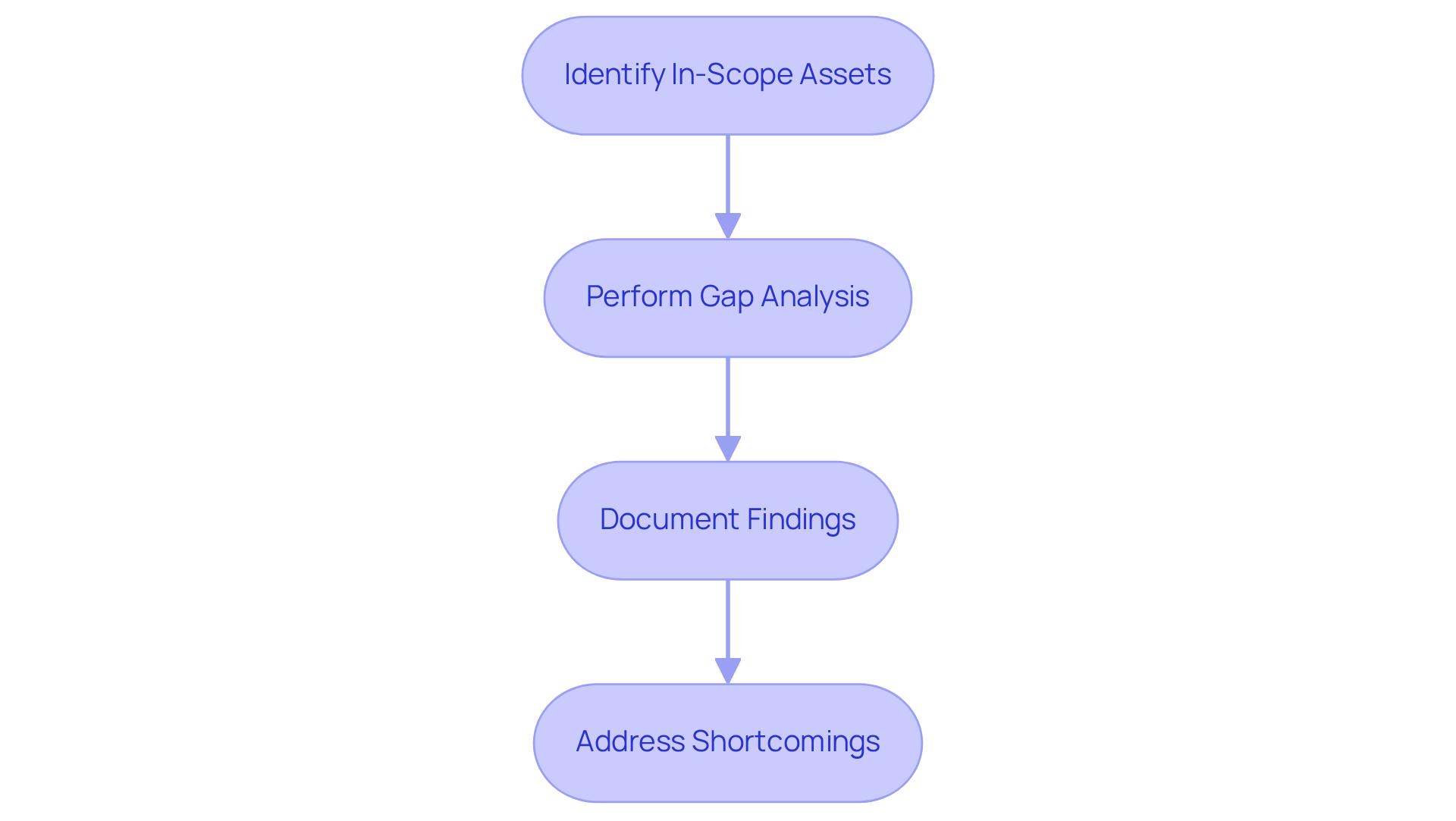
Conduct a Self-Assessment to Identify Compliance Gaps
Conducting a self-assessment is crucial for contractors aiming to align their cybersecurity practices with compliance standards. This process begins with identifying all in-scope assets, which is essential for understanding the extent of adherence. Both physical assets - like servers, workstations, and network devices - and virtual assets, including virtual machines and cloud-based services, must be tracked meticulously.
Next, a comprehensive gap analysis should be performed to evaluate current practices against the standards, particularly the 110 controls necessary for Level 2 adherence, which align with NIST SP 800-171 controls. Did you know that only 270 out of 80,000 defense suppliers currently hold final certification? This statistic underscores the urgency of addressing regulatory gaps. Cybersecurity professionals stress that a thorough gap analysis not only identifies areas needing improvement but also assists in crafting a targeted remediation plan.
By documenting findings and addressing identified shortcomings, service providers can enhance their overall security posture, making them better prepared for formal evaluations and more resilient against potential digital threats. This proactive approach is vital, especially as the Department of Defense mandates compliance for agreements. With the final acquisition rule for the Cybersecurity Maturity Model Certification program set to take effect on November 10, 2025, many suppliers are understandably concerned about missed opportunities due to looming deadlines.
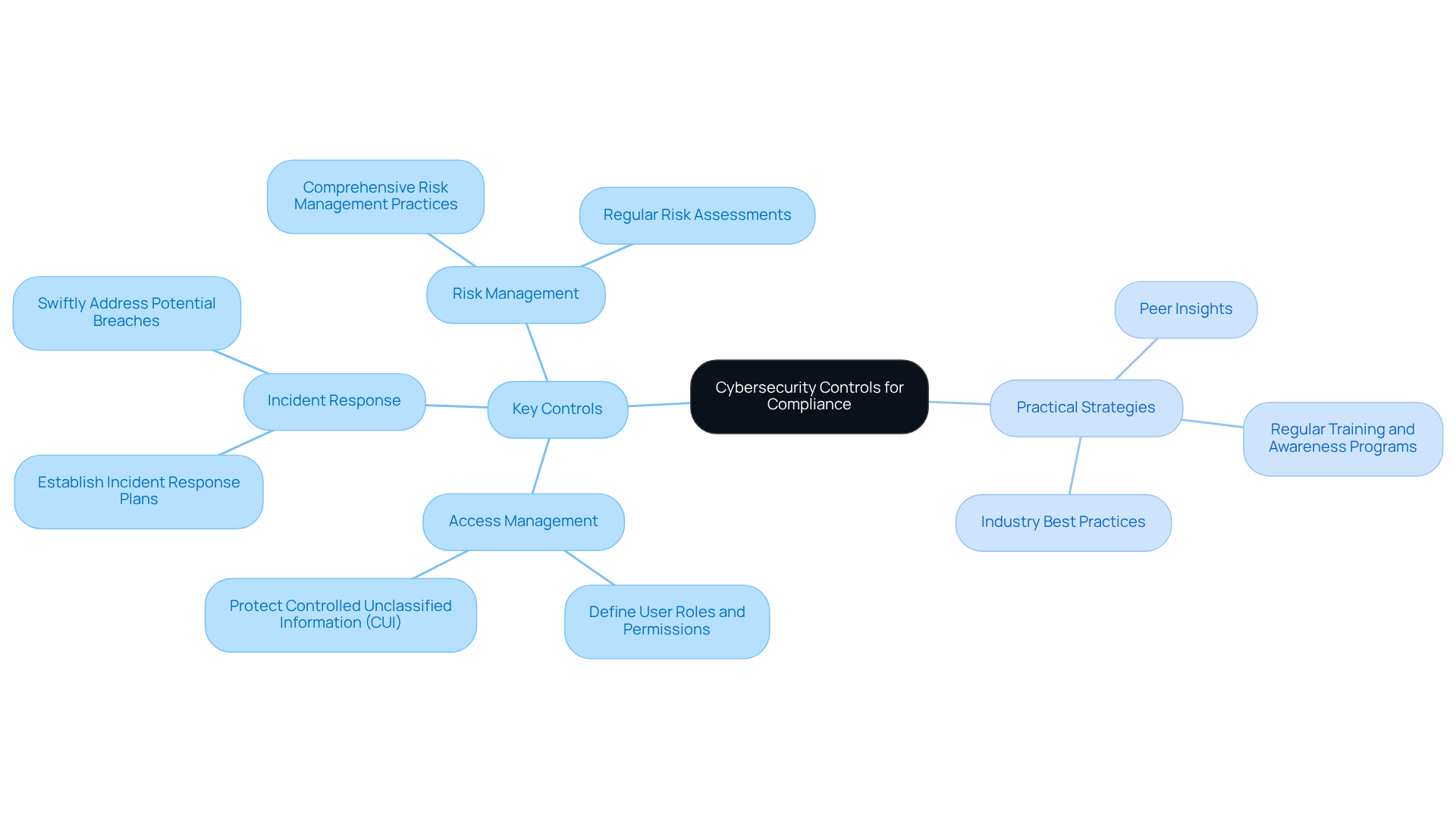
Implement Necessary Cybersecurity Controls for Compliance
Achieving compliance with the framework requires service providers to implement security measures tailored to their specific maturity level. Key controls include:
- Robust access management
- Effective incident response strategies
- Comprehensive risk management practices
Organizations must develop a detailed security plan that outlines the implementation of these controls, ensuring alignment with CMMC requirements. For example, effective access management involves defining user roles and permissions to protect Controlled Unclassified Information (CUI). Additionally, incident response plans should be established to swiftly and effectively address potential breaches.
To navigate this complex landscape, contractors can leverage practical strategies, such as:
- Drawing on peer insights
- Utilizing industry best practices
Regular training and awareness programs for employees are essential for maintaining compliance and fostering a culture of cybersecurity within the organization. This proactive approach not only strengthens the organization's security posture but also prepares them for the rigorous assessments required under CMMC. By effectively implementing these controls, builders can significantly reduce the risk of data breaches, which, according to recent statistics, can cost businesses in the defense sector an average of $5.46 million per incident. Moreover, as major defense contractors increasingly limit their subcontractor pool to those meeting Level 2 standards, the importance of these security measures cannot be overstated. Ultimately, a well-structured cybersecurity plan not only safeguards sensitive information but also enhances readiness for securing defense contracts.
Conclusion
Navigating the complexities of CMMC certification requirements is not just essential; it’s a critical imperative for contractors in the defense sector. Understanding the CMMC framework, conducting thorough self-assessments, and implementing robust cybersecurity controls are foundational steps toward achieving compliance. By leveraging resources like the CMMC Info Hub, organizations can streamline their compliance efforts, securing their position in a competitive landscape where regulatory adherence is paramount.
Key insights reveal the necessity of familiarizing oneself with the three maturity levels of the CMMC. Recognizing the urgency of self-assessments to identify compliance gaps is crucial, as is the implementation of tailored cybersecurity measures. With the compliance deadline approaching in 2025, proactive strategies are essential - not only to enhance security postures but also to prepare contractors for the evolving demands of defense contracts.
Reflecting on this journey, CMMC certification transcends mere regulatory compliance; it’s a vital step toward safeguarding sensitive information and ensuring organizational resilience. Contractors must take decisive action now, utilizing the tools and resources at their disposal. This approach will not only help meet compliance standards but also enable them to thrive in an increasingly security-conscious environment. Embracing these steps will protect their interests and contribute to the overall integrity of the defense supply chain.
Frequently Asked Questions
What is the purpose of the CMMC Info Hub?
The CMMC Info Hub serves as a knowledge repository for organizations aiming to meet the CMMC certification requirements for compliance with the Cybersecurity Maturity Model Certification (CMMC).
Who is the CMMC Info Hub designed for?
The Hub is specifically designed for defense suppliers facing challenges in navigating the complexities of DoD information security requirements.
What resources does the CMMC Info Hub provide?
The Hub offers comprehensive roadmaps, pragmatic strategies, and peer insights to help suppliers effectively navigate CMMC certification requirements.
Why is CMMC certification important for defense contractors?
CMMC certification is crucial for defense contractors as it ensures compliance with regulatory measures aimed at enhancing security and mitigating risks in the defense sector.
How does the CMMC Info Hub help organizations improve their security posture?
By providing access to proven practices and simplifying regulatory processes, the Info Hub enhances security postures and helps contractors meet the necessary CMMC certification requirements.
What are the benefits of leveraging resources from the CMMC Info Hub?
Leveraging resources from the CMMC Info Hub can streamline the path to fulfilling CMMC certification requirements and bolster an organization's security framework.
What should organizations do to safeguard their future in the defense industry?
Organizations are encouraged to take action now by utilizing the resources available through the CMMC Info Hub to ensure compliance and secure defense contracts.