5 Best Practices for Creating an Effective SSP Document
Discover effective strategies for creating an SSP document to enhance cybersecurity and compliance.

Introduction
Creating a robust System Security Plan (SSP) is crucial for organizations aiming to navigate the intricate landscape of cybersecurity compliance, especially under the rigorous standards of the Cybersecurity Maturity Model Certification (CMMC). This article will delve into best practices for developing an effective SSP document, emphasizing its vital role in protecting sensitive information and ensuring adherence to regulatory requirements.
But with numerous components to consider, how can organizations guarantee that their SSP not only fulfills compliance standards but also strengthens their overall cybersecurity posture?
Define the System Security Plan (SSP)
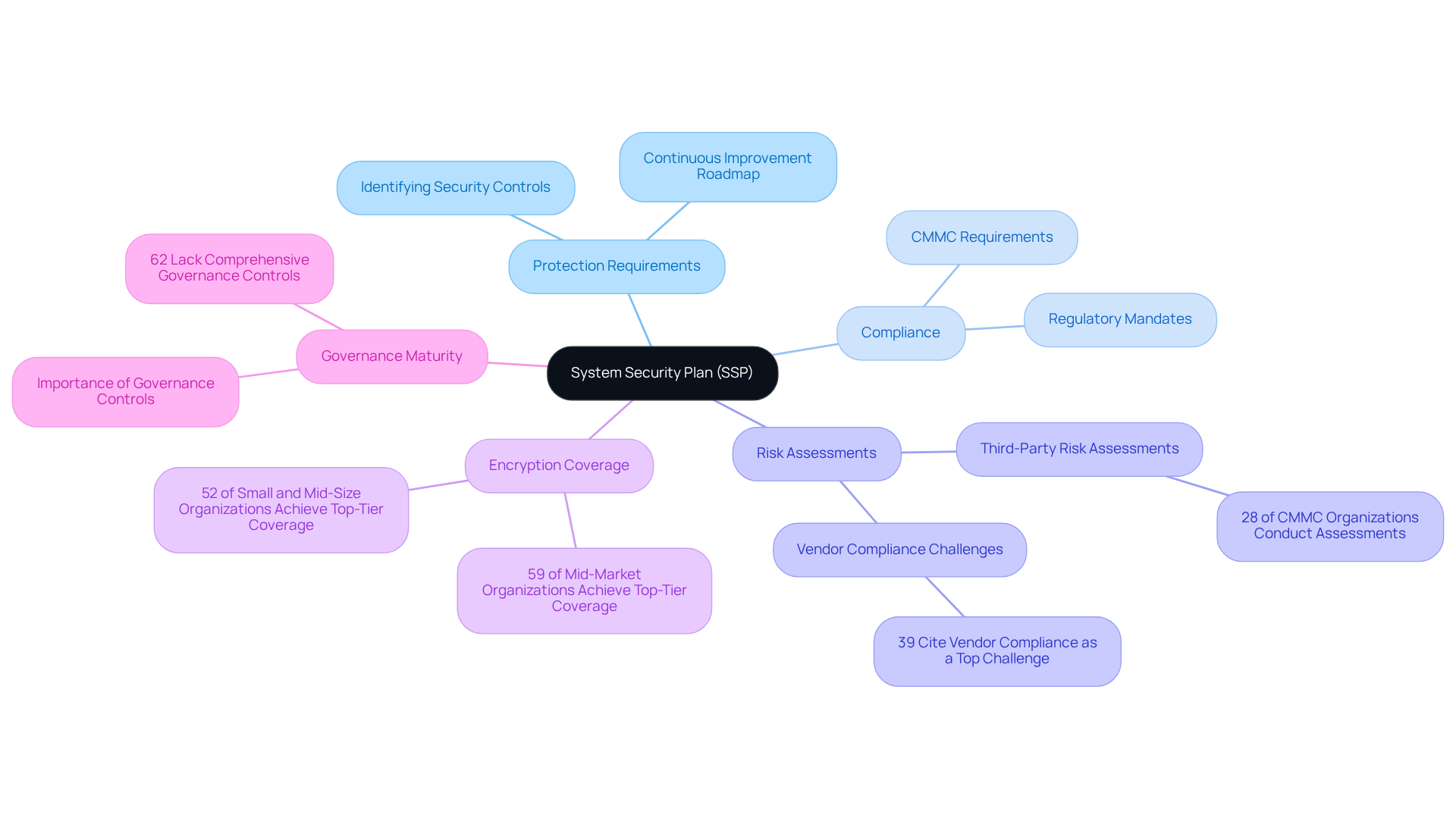
An SSP document is a vital resource that delineates an organization's protection requirements and the controls established to safeguard its information systems. It serves as a strategic framework for managing cybersecurity risks and ensuring compliance with regulatory mandates, particularly those set forth by the Department of Defense (DoD) under the Cybersecurity Maturity Model Certification (CMMC). An effective SSP not only identifies the protective measures in place but also acts as a roadmap for continuous improvement and compliance oversight, transforming confusion into clarity for defense contractors navigating the complexities of CMMC compliance.
Did you know that 28% of CMMC organizations conduct formal third-party risk assessments? This statistic underscores the necessity of a robust SSP document in identifying and mitigating risks. Organizations that prioritize the development of a comprehensive SSP document are better positioned to meet CMMC requirements, as an incomplete SSP document may impede the completion of third-party assessments.
Successful implementation of SSPs has been observed across various organizations, with mid-market firms achieving an impressive 59% top-tier encryption coverage. This achievement highlights the effectiveness of structured security planning. The success of these initiatives is closely linked to governance maturity, which is essential for effective security and gaining a competitive edge in the defense market. As the DoD continues to refine the SSP document requirements, organizations must remain vigilant about the latest updates to ensure their plans align with evolving regulations. This proactive approach, supported by practical strategies and peer insights, not only enhances cybersecurity posture but also facilitates smoother navigation through the intricacies of CMMC regulations.
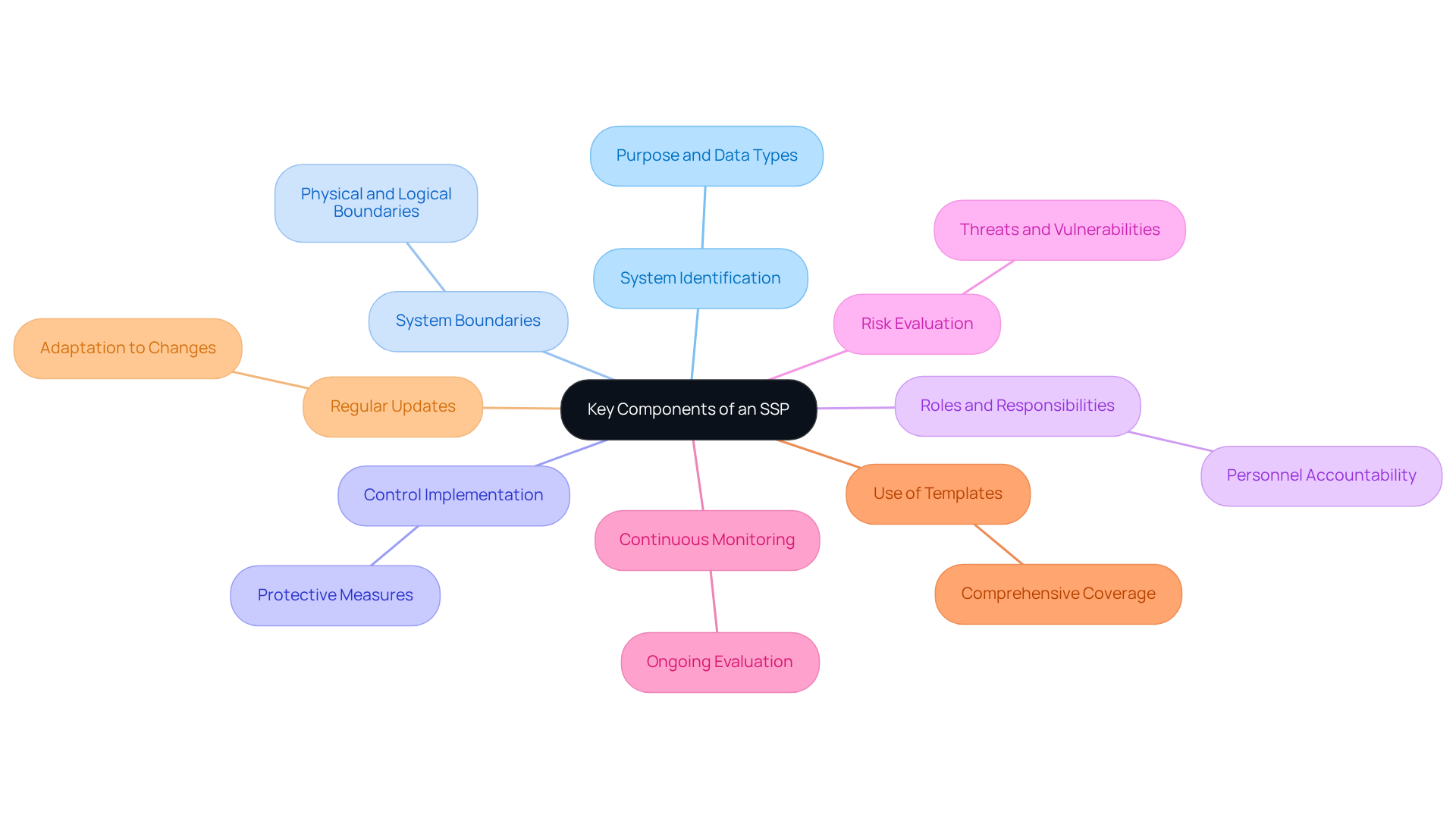
Identify Key Components of an SSP
An effective ssp document is crucial for ensuring compliance and robust cybersecurity practices. It serves as your ultimate guide to achieving CMMC compliance. Here are the essential components:
-
System Identification: Clearly articulate the system's purpose and the types of data it processes, including Controlled Unclassified Information (CUI).
-
System Boundaries: Define the physical and logical boundaries of the system. Specify what is included and excluded to prevent over-scoping or under-scoping.
-
Control Implementation: Detail the execution of protective measures. Cover technical, administrative, and physical safeguards necessary to protect sensitive information.
-
Roles and Responsibilities: Clearly outline the roles and responsibilities of personnel involved in maintaining and enforcing protective measures. This ensures accountability within the organization.
-
Risk Evaluation: Summarize the risk evaluation process. Identify potential threats and vulnerabilities that could affect the system's integrity.
-
Continuous Monitoring: Establish processes for ongoing observation and evaluation of protective measures. This ensures they remain effective and current in response to evolving threats.
-
Use of Templates: It is highly recommended to utilize templates when creating an SSP. This ensures that all required elements outlined in the ssp document are covered comprehensively, transforming confusion into clarity.
-
Regular updates and reviews of the ssp document are crucial. They help adapt to changes in the system environment and emerging cyber threats. Specific strategies for maintaining an effective SSP include scheduling quarterly reviews, incorporating feedback from security assessments, and ensuring alignment with frameworks like NIST 800-171 and CMMC.
By integrating these elements, defense contractors can develop a thorough SSP that not only satisfies regulatory standards but also improves their overall cybersecurity approach. An SSP is essential for organizations managing CUI. Failing to uphold an accurate SSP can result in regulatory risks and penalties under laws such as the False Claims Act.
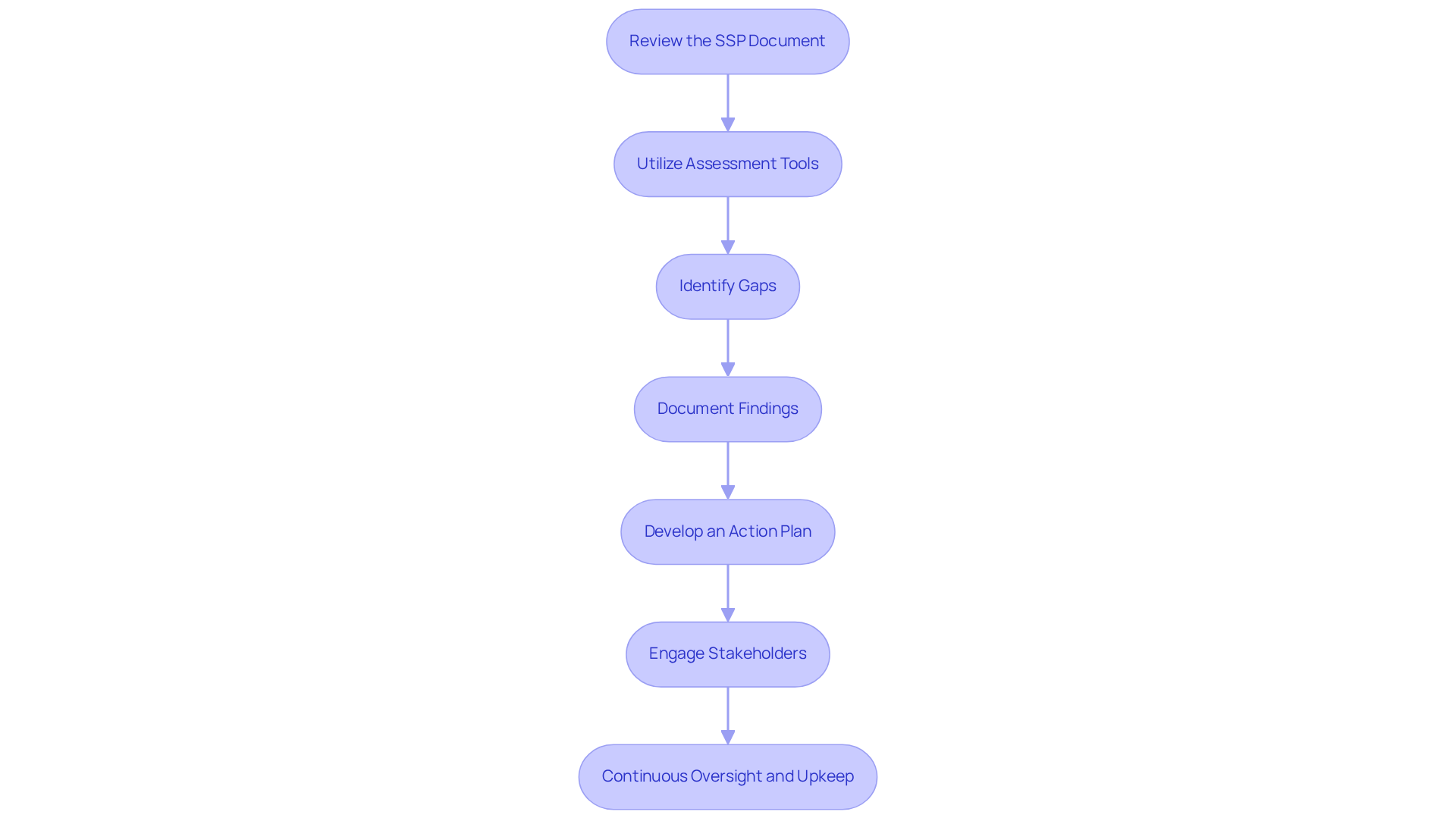
Conduct a Self-Assessment for Compliance
To effectively conduct a self-assessment for compliance with CMMC requirements, organizations should adhere to the following best practices:
-
Review the SSP document: Begin by carefully assessing the current System Security Plan (SSP document). This ensures it accurately reflects the existing security posture and the execution of necessary measures.
-
Utilize Assessment Tools: Leverage assessment instruments and checklists aligned with NIST 800-171 standards. These tools streamline the assessment process and provide a clear framework for evaluation, making it easier to gauge compliance.
-
Identify Gaps: Conduct a thorough comparison of current practices against CMMC requirements to pinpoint any adherence gaps. Many organizations struggle to align their measures with CMMC standards, leading to significant vulnerabilities. Are you aware of where your organization stands?
-
Document Findings: Meticulously record the results of the self-assessment, highlighting identified gaps and areas needing improvement. Proper documentation is critical for maintaining a reliable assessment process and ensuring transparency.
-
Develop an Action Plan: Formulate a comprehensive action plan to address deficiencies, prioritizing actions based on risk and potential impact. This proactive strategy is crucial for reducing regulatory risks and enhancing your overall cybersecurity posture.
-
Engage Stakeholders: Involve relevant stakeholders throughout the assessment process. This ensures comprehensive coverage and fosters buy-in for necessary changes. Collaboration can significantly enhance the effectiveness of the self-assessment and facilitate smoother implementation of improvements.
-
Continuous Oversight and Upkeep: After the self-evaluation, continue overseeing and maintaining the protective measures implemented for CMMC adherence. This includes conducting regular vulnerability scans, timely patch management, reviewing audit logs for signs of security incidents, monitoring for configuration drift, conducting access reviews, and continuously monitoring for security incidents.
By following these steps, organizations can effectively identify regulatory gaps and enhance their readiness for CMMC certification. Ultimately, this positions them for success in securing defense contracts.
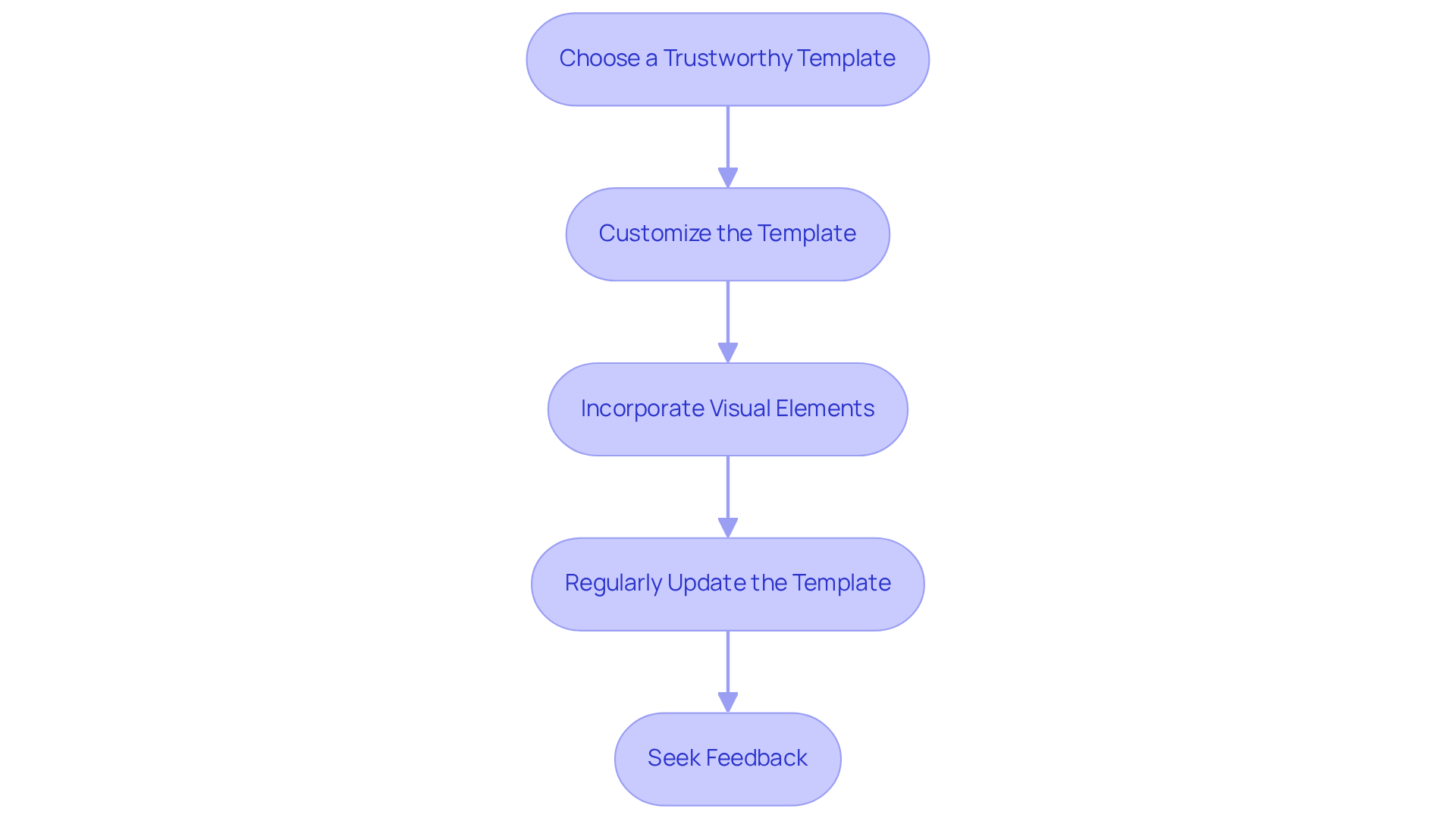
Utilize Effective SSP Templates
An effective SSP document template can significantly elevate the quality and compliance of your documentation. Here’s how to leverage SSP templates effectively:
- Choose a Trustworthy Template: Opt for templates recognized by industry experts, such as those from NIST or CMMC-specific resources. This choice ensures credibility and adherence to standards.
- Customize the Template: Tailor the template to reflect your organization’s unique needs. Customization should accurately represent all relevant systems and controls, moving beyond generic content to ensure specificity in control implementation. Organizations that frequently modify their SSP document templates often report improved adherence results.
- Incorporate Visual Elements: Enhance readability by integrating diagrams, tables, and charts. Visual aids can effectively communicate complex information, making it easier for stakeholders to grasp key details within the SSP document.
- Regularly Update the Template: Keep the template current by frequently updating it to reflect changes in regulatory requirements or organizational practices. A living document approach is essential, allowing for ongoing adjustments in response to evolving threats and regulatory changes.
- Seek Feedback: Engage cross-functional stakeholders in reviewing the template. This collaborative method ensures that the SSP document addresses the requirements of all pertinent parties and aligns with regulatory objectives, ultimately improving the organization’s security stance.
By following these best practices, organizations can create effective SSP documents that not only comply with regulatory standards but also act as strategic tools for managing cybersecurity risks.
Address NIST 800-171 Controls
Integrating NIST 800-171 measures into your SSP document is crucial for demonstrating compliance with CMMC requirements. Here’s how to effectively address these controls:
-
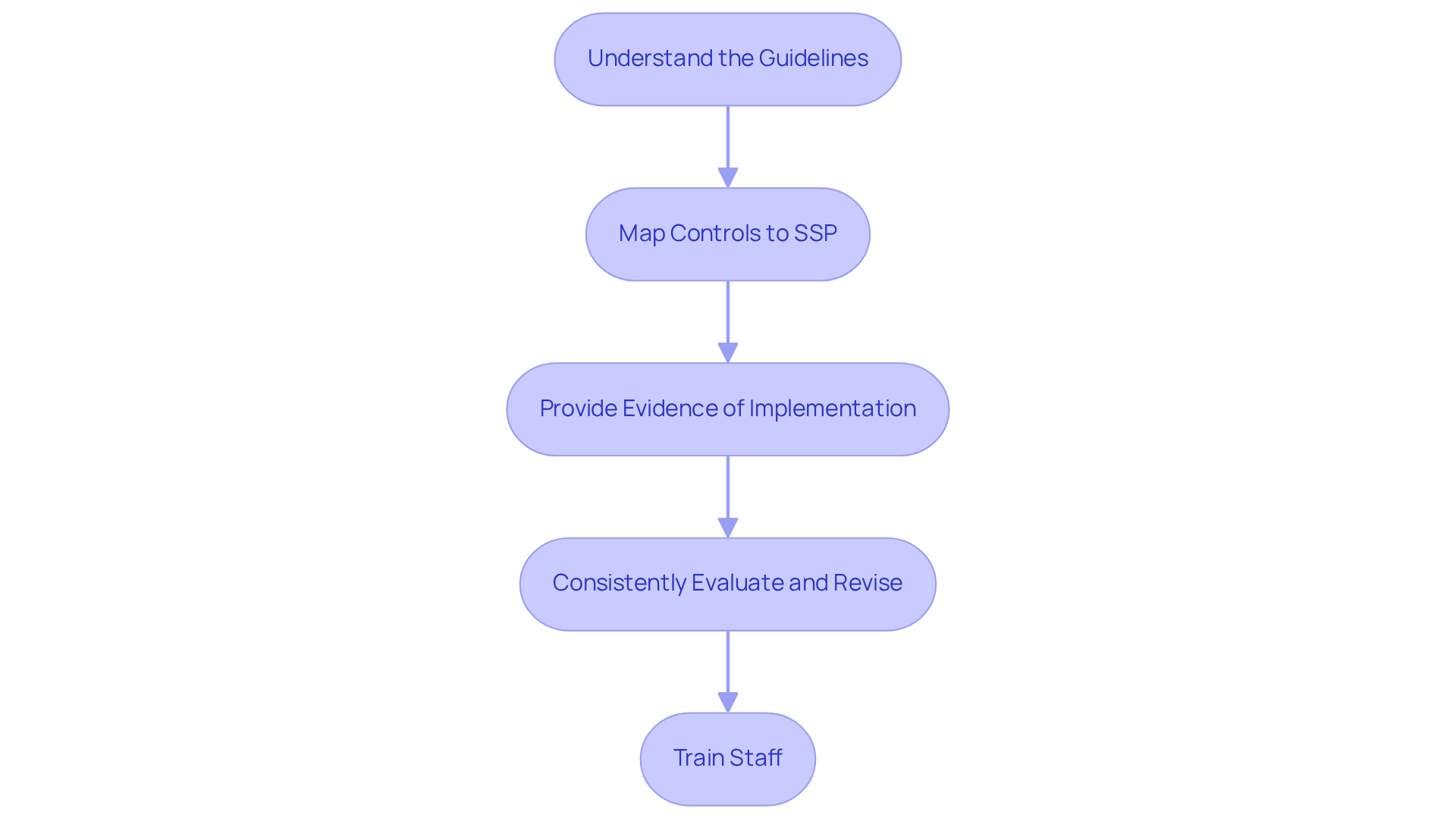
Understand the Guidelines: Start by familiarizing yourself with the 14 families of measures outlined in NIST 800-171. These encompass critical areas such as access management, incident response, and risk evaluation. This foundational knowledge is essential for compliance.
-
Map controls to the SSP document sections by aligning each measure with the relevant parts of your SSP document. This mapping ensures that implementation specifics are clearly recorded, aiding in a thorough understanding of how each measure is applied within your organization.
-
Provide Evidence of Implementation: Include supporting documentation that illustrates how each measure is implemented and maintained. This evidence is vital for audits and evaluations, showcasing your commitment to regulations.
-
Consistently Evaluate and Revise: Regularly assess the effectiveness of the measures and update the SSP as necessary. This proactive approach guarantees that your security practices remain aligned with evolving compliance requirements and organizational changes.
-
Train Staff: Ensure that all relevant personnel are educated on the mechanisms and their significance in upholding regulations and protecting sensitive information. A well-informed team is essential for effective implementation and adherence to security protocols.
By following these steps, organizations can seamlessly integrate NIST 800-171 controls into their SSP document, enhancing their compliance posture and readiness for CMMC assessments.
Conclusion
Creating an effective System Security Plan (SSP) is essential for organizations navigating the complexities of cybersecurity compliance, especially under the stringent requirements of the Cybersecurity Maturity Model Certification (CMMC). A well-structured SSP not only clarifies an organization’s security measures but also serves as a strategic guide for continuous improvement and risk management. By prioritizing the development of a comprehensive SSP, organizations can enhance their readiness for audits and third-party assessments, positioning themselves for success in the defense contracting space.
Key components of an effective SSP include:
- System Identification: Clearly defining the systems in scope.
- Control Implementation: Establishing necessary security controls.
- Continuous Monitoring: Regularly assessing the effectiveness of these controls.
Each element plays a crucial role in ensuring compliance with regulatory standards and addressing potential vulnerabilities. Furthermore, conducting regular self-assessments and utilizing effective templates are vital practices that help organizations identify gaps and maintain up-to-date documentation. By integrating NIST 800-171 controls, organizations can further solidify their compliance posture and demonstrate their commitment to protecting sensitive information.
Ultimately, the significance of a robust SSP cannot be overstated. As cybersecurity threats continue to evolve, organizations must remain proactive in their approach to compliance and risk management. Embracing best practices in SSP development and maintenance not only safeguards sensitive data but also fosters a culture of accountability and resilience. Engaging with these practices empowers organizations to navigate the complexities of cybersecurity with confidence and clarity, ensuring they remain competitive in an increasingly regulated landscape.
Frequently Asked Questions
What is a System Security Plan (SSP)?
An SSP is a document that outlines an organization's protection requirements and the controls established to safeguard its information systems. It serves as a strategic framework for managing cybersecurity risks and ensuring compliance with regulatory mandates, particularly those set by the Department of Defense (DoD) under the Cybersecurity Maturity Model Certification (CMMC).
Why is an SSP important for organizations?
An SSP is vital for identifying and mitigating cybersecurity risks, ensuring compliance with CMMC requirements, and providing clarity for defense contractors navigating complex regulations. It acts as a roadmap for continuous improvement and compliance oversight.
What are the key components of an effective SSP?
The key components include: - System Identification: Purpose and data types processed, including Controlled Unclassified Information (CUI). - System Boundaries: Definition of physical and logical boundaries of the system. - Control Implementation: Details on protective measures, including technical, administrative, and physical safeguards. - Roles and Responsibilities: Outlining personnel roles in maintaining protective measures. - Risk Evaluation: Summary of potential threats and vulnerabilities. - Continuous Monitoring: Processes for ongoing evaluation of protective measures. - Use of Templates: Utilizing templates to cover required elements comprehensively. - Regular Updates: Importance of updating and reviewing the SSP to adapt to changes and emerging threats.
How does governance maturity relate to the success of SSP implementation?
Governance maturity is essential for effective security and gaining a competitive edge in the defense market. Organizations with mature governance structures are better equipped to implement successful SSPs and achieve compliance.
What are the consequences of not maintaining an accurate SSP?
Failing to uphold an accurate SSP can lead to regulatory risks and potential penalties under laws such as the False Claims Act, which can negatively impact an organization's compliance status and cybersecurity posture.
How often should an SSP be reviewed and updated?
It is recommended to schedule quarterly reviews of the SSP, incorporate feedback from security assessments, and ensure alignment with frameworks like NIST 800-171 and CMMC to maintain its effectiveness against evolving cyber threats.




