5 Best Practices for Meeting SOX Cybersecurity Requirements
Explore essential practices for meeting SOX cybersecurity requirements and safeguarding financial data.

Introduction
The Sarbanes-Oxley Act (SOX) stands as a cornerstone of corporate governance, especially following the financial scandals that have eroded public trust. As organizations grapple with the complexities of compliance, grasping the cybersecurity implications of SOX is essential for protecting sensitive financial data. This article explores five best practices that not only ensure compliance with SOX cybersecurity requirements but also bolster overall security posture.
How can businesses effectively integrate these practices to mitigate risks and enhance stakeholder confidence in an increasingly digital landscape?
Understand the Sarbanes-Oxley Act and Its Cybersecurity Implications
The Sarbanes-Oxley Act (SOX), enacted in 2002 in response to high-profile economic scandals involving Enron, WorldCom, and Tyco, was designed to enhance corporate governance and accountability. At its core, SOX emphasizes the integrity of reporting, mandating robust internal controls over financial data. But what does this mean for organizations today? In the realm of online security, the SOX cybersecurity requirements necessitate that companies establish protocols to protect sensitive financial information from unauthorized access and breaches. This includes implementing IT General Controls (ITGCs) that ensure data integrity, confidentiality, and availability.
Moreover, CEOs and CFOs are required to certify the accuracy of financial records submitted to the SEC, underscoring the critical role of digital security in corporate governance. As we look ahead to 2026, the impact of SOX cybersecurity requirements on compliance remains profound. Organizations are increasingly recognizing the necessity of aligning their cybersecurity strategies with SOX cybersecurity requirements. For instance, many businesses are leveraging advanced technologies like robotic process automation (RPA) and AI-driven solutions to bolster their compliance efforts, minimizing manual errors and enhancing real-time monitoring.
This shift not only strengthens the control environment but also mitigates risks associated with financial reporting. Real-world examples underscore the importance of SOX compliance in protecting financial data. Organizations that have integrated comprehensive security measures into their SOX programs report improved documentation practices and heightened audit committee involvement-both essential for maintaining stakeholder trust.
In summary, the SOX cybersecurity requirements for safeguarding financial data necessitate a proactive approach to digital security. This ensures that organizations not only comply with regulatory standards but also enhance their overall security posture. By understanding and implementing these requirements, companies can avoid penalties and foster trust with stakeholders, ultimately contributing to a more secure economic landscape.
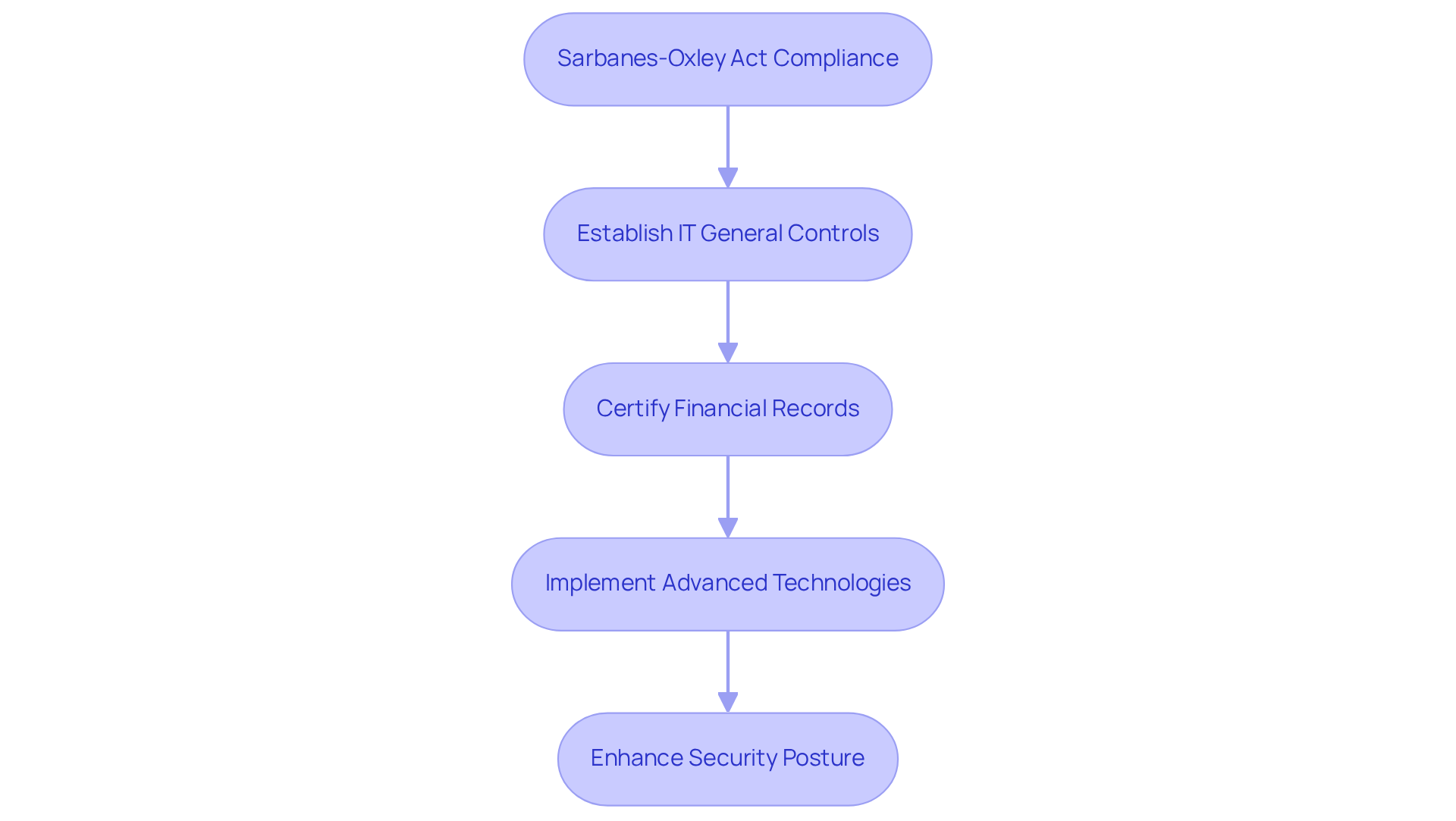
Implement Essential Cybersecurity Controls for SOX Compliance
To achieve SOX compliance, organizations must implement essential cybersecurity controls that adhere to the SOX cybersecurity requirements, which are critical safeguards for financial integrity. Consider the following:
- Access Controls: Establish strict access controls to limit who can view and modify monetary data. This includes role-based access and multi-factor authentication (MFA) to enhance security.
- Data Encryption: Encrypt sensitive monetary data both at rest and in transit to protect it from unauthorized access.
- Audit Trails: Maintain comprehensive logs of all access and modifications to monetary data, ensuring that any unauthorized changes can be traced and addressed.
- Incident Response Plans: Develop and regularly update incident response plans to quickly address any breaches or security incidents that may compromise financial data.
By implementing these controls, organizations can significantly reduce their risk of non-compliance and enhance their overall cybersecurity posture to align with SOX cybersecurity requirements. Are you ready to take the necessary steps to protect your financial data?
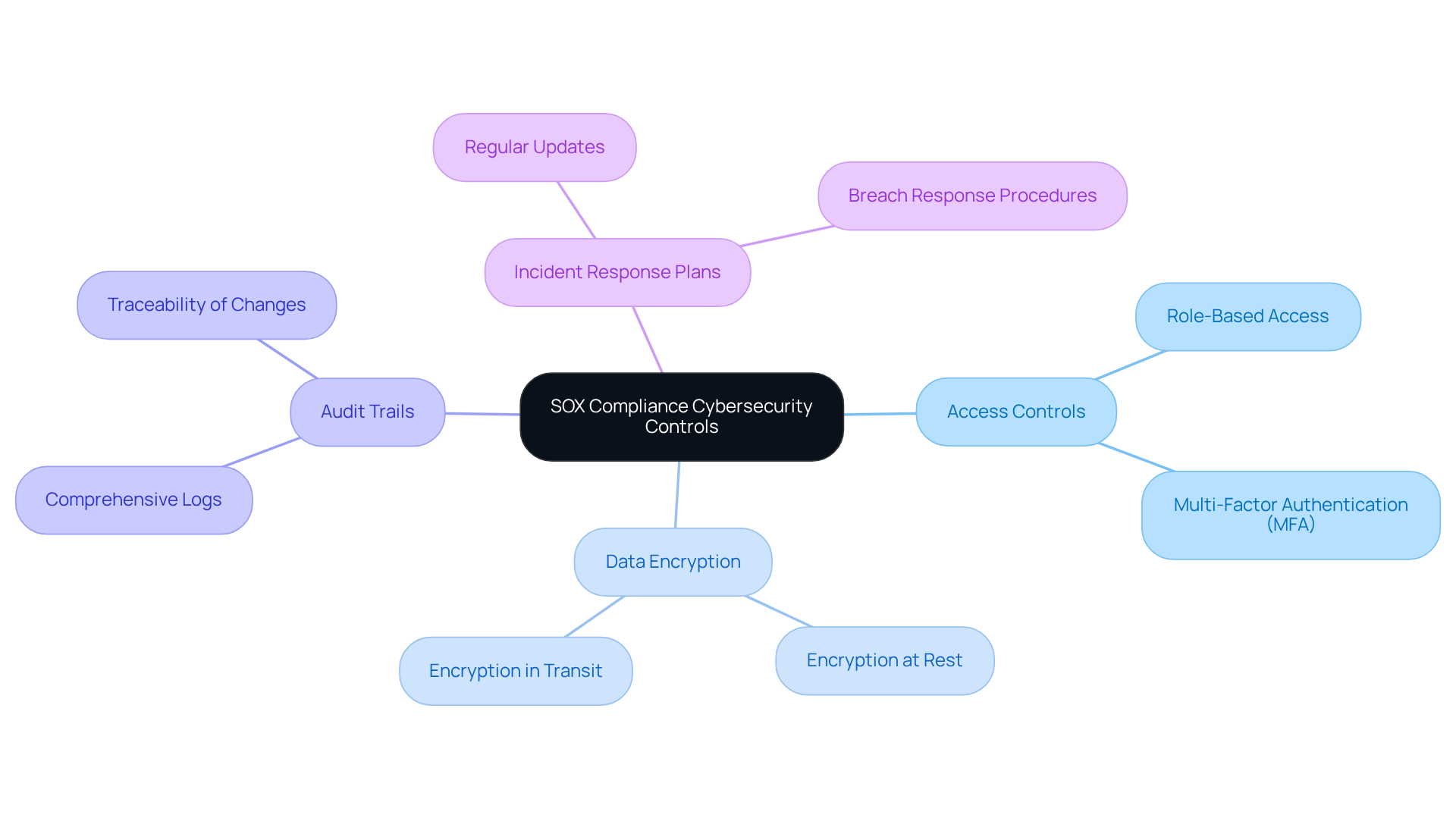
Establish Continuous Monitoring and Auditing Practices
Ongoing monitoring and auditing are essential for a robust strategy that meets SOX cybersecurity requirements. Organizations must embrace the following best practices:
-
Conduct Regular Audits: Schedule periodic audits to evaluate the effectiveness of internal controls and identify any weaknesses that may have developed since the last review. This proactive approach not only sustains adherence but also enhances overall control environments. Did you know that a recent survey revealed 21% of C-Suite executives view regulatory adherence as their top strategic priority over the next 18 months? This statistic underscores the significance of these audits.
-
Implement Automated Monitoring Tools: Leverage automated tools to continuously monitor access to financial systems. This enables real-time detection of anomalies or unauthorized activities. Research indicates that automation can significantly enhance SOX cybersecurity requirements by improving accuracy, consistency, and efficiency in internal controls and evidence collection. Consequently, this lowers audit risk and boosts preparedness for audits.
-
Review and Update Policies: Regularly assess and update cybersecurity policies and procedures to align with changes in the regulatory landscape and emerging threats. This guarantees that organizations remain adaptable and responsive to new regulatory requirements.
-
Engage Third-Party Auditors: Consider hiring external auditors for an objective assessment of adherence efforts. Insights from external sources reveal that 48% of participating CISOs view ensuring third-party adherence to security requirements as a major challenge. Their insights can help identify areas for improvement and reinforce accountability within the organization.
By adopting these practices, organizations can effectively navigate the complexities of SOX regulations while complying with SOX cybersecurity requirements. The shift towards ongoing surveillance and automated solutions is becoming increasingly essential, as regulators now expect real-time reporting of anomalies and strong proof of adherence.
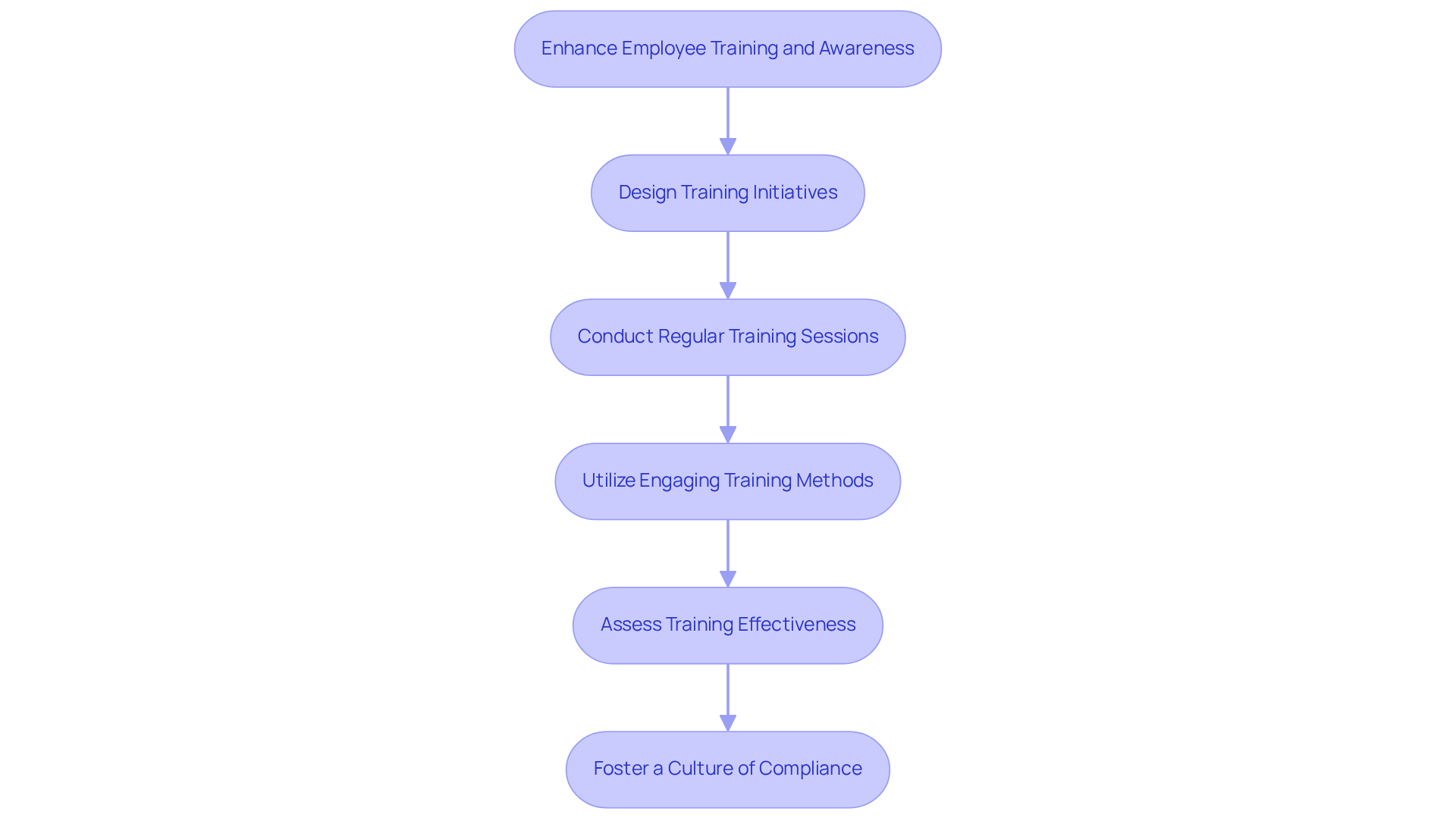
Enhance Employee Training and Awareness on Compliance
To cultivate a robust culture of compliance and security awareness, organizations must implement effective practices that resonate with their teams:
-
Start by designing training initiatives that encompass SOX cybersecurity requirements, information security best practices, and the specific responsibilities of employees in upholding regulations. This approach ensures that every team member understands their role in safeguarding sensitive information, emphasizing the foundational importance of policies and procedures as mandated by the CMMC framework.
-
Conducting regular training sessions is crucial to keep employees informed about the latest online security threats and the SOX cybersecurity requirements. This ongoing education reinforces their understanding of responsibilities and highlights the critical role of established policies and procedures in their daily tasks.
-
Utilize Engaging Training Methods: Leverage interactive training techniques, such as simulations and gamification, to boost engagement and retention. These methods not only make learning enjoyable but also enhance the practical application of knowledge in real-world scenarios.
-
Assess Training Effectiveness: Regularly evaluate the impact of training programs through quizzes and participant feedback. This evaluation helps identify areas for enhancement, ensuring that training remains relevant and effective in addressing regulatory challenges.
By prioritizing employee training and awareness, organizations can significantly reduce the risk of regulatory breaches stemming from human error. This proactive approach ultimately enhances their overall cybersecurity posture, fostering a culture of compliance that is both resilient and responsive.
Foster Collaboration Among Stakeholders for Effective Compliance
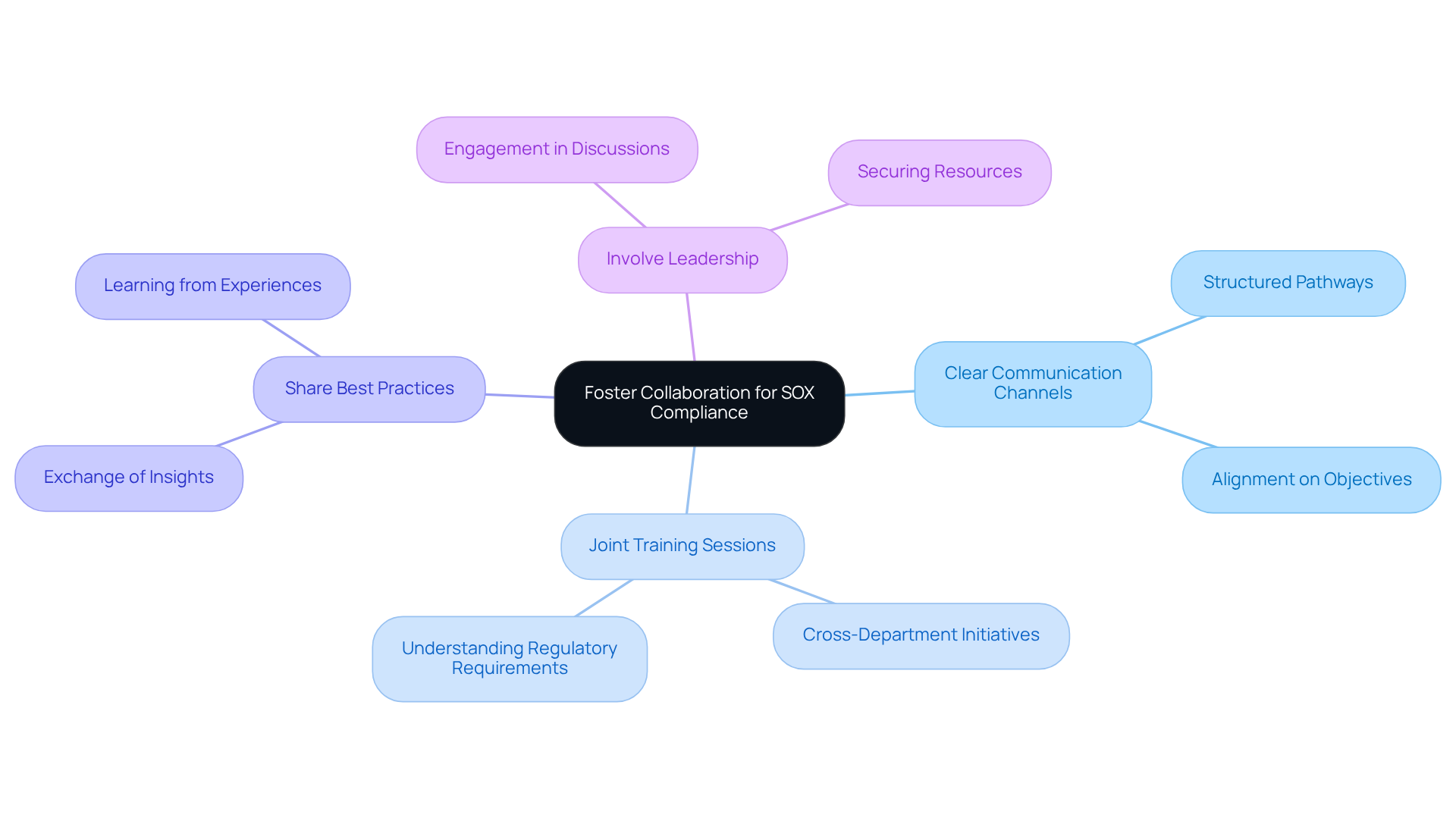
Collaboration among stakeholders is crucial for achieving SOX adherence. Organizations must adopt the following best practices:
- Establish Clear Communication Channels: Develop structured communication pathways between finance, IT, and regulatory teams. This ensures alignment on regulatory objectives and responsibilities.
- Conduct Joint Training Sessions: Facilitate joint training initiatives across departments. This promotes understanding and cooperation regarding regulatory requirements, fostering a unified approach.
- Share Best Practices: Encourage departments to exchange insights gained from regulatory efforts. This enhances overall effectiveness and allows teams to learn from each other's experiences.
- Involve Leadership: Actively engage leadership in regulatory discussions. This underscores the significance of compliance and secures the necessary resources for adherence initiatives.
By fostering cooperation among stakeholders, organizations can create a unified strategy for regulatory adherence. This approach not only leads to better results but also strengthens the regulatory framework. As Paul Koziarz points out, "Without a regulatory framework, some organizations might not adopt any security measures at all (or at least until it is too late)."
Moreover, integrating evaluations of sox cybersecurity requirements and data privacy into SOX programs is essential. The costs associated with a security breach can far exceed the expenses of establishing regulatory protocols. For instance, Ullico's collaboration with Cherry Bekaert illustrates how effective teamwork can yield successful compliance outcomes, enhancing both operational efficiency and stakeholder confidence.
Conclusion
The Sarbanes-Oxley Act (SOX) serves as a vital framework for organizations looking to bolster their cybersecurity measures and uphold the integrity of financial reporting. Have you considered how SOX impacts your cybersecurity strategy? By grasping the implications of SOX, companies can adopt essential practices that not only ensure regulatory compliance but also strengthen defenses against potential breaches. In today’s digital landscape, where safeguarding sensitive financial information is paramount, this proactive approach is crucial.
To meet SOX cybersecurity requirements effectively, organizations should focus on several key strategies:
- Establishing robust access controls
- Utilizing data encryption
- Maintaining comprehensive audit trails
- Developing effective incident response plans
Continuous monitoring and regular audits are essential to reinforce compliance efforts, enabling organizations to adapt to evolving threats and regulatory expectations. Additionally, fostering a culture of compliance through employee training and collaboration among stakeholders is vital. Everyone must understand their role in protecting financial data.
Ultimately, prioritizing SOX compliance transcends merely avoiding penalties; it’s about building trust with stakeholders and contributing to a more secure economic environment. Organizations that adopt these best practices will not only meet regulatory standards but also enhance their overall cybersecurity posture. Are you ready to navigate the complexities of today’s regulatory landscape? Taking action now to implement these strategies can yield significant long-term benefits, underscoring the critical role of cybersecurity in corporate governance.
Frequently Asked Questions
What is the Sarbanes-Oxley Act (SOX)?
The Sarbanes-Oxley Act, enacted in 2002, was designed to enhance corporate governance and accountability in response to economic scandals involving companies like Enron and WorldCom. It emphasizes the integrity of financial reporting and mandates robust internal controls over financial data.
What are the cybersecurity implications of SOX?
SOX requires organizations to establish protocols to protect sensitive financial information from unauthorized access and breaches, necessitating the implementation of IT General Controls (ITGCs) to ensure data integrity, confidentiality, and availability.
What responsibilities do CEOs and CFOs have under SOX?
CEOs and CFOs are required to certify the accuracy of financial records submitted to the SEC, highlighting the importance of digital security in corporate governance.
How are organizations aligning their cybersecurity strategies with SOX requirements?
Organizations are increasingly leveraging advanced technologies like robotic process automation (RPA) and AI-driven solutions to enhance compliance efforts, minimize manual errors, and improve real-time monitoring.
What are some essential cybersecurity controls for SOX compliance?
Essential cybersecurity controls include:
- Access Controls: Limiting access to monetary data through role-based access and multi-factor authentication (MFA).
- Data Encryption: Encrypting sensitive monetary data both at rest and in transit.
- Audit Trails: Maintaining comprehensive logs of access and modifications to monetary data.
- Incident Response Plans: Developing and regularly updating plans to address any breaches or security incidents.
What benefits do organizations gain from implementing SOX cybersecurity measures?
Organizations that integrate comprehensive security measures into their SOX programs report improved documentation practices, heightened audit committee involvement, and a stronger overall security posture, which helps maintain stakeholder trust.
Why is it important for organizations to comply with SOX cybersecurity requirements?
Complying with SOX cybersecurity requirements helps organizations avoid penalties, enhances their security posture, and fosters trust with stakeholders, contributing to a more secure economic landscape.