5 Steps for Cyber Security Audit and Compliance Success
Master the essentials of cyber security audit and compliance in five actionable steps.

Introduction
Crafting a robust cybersecurity audit isn’t just a regulatory checkbox; it’s a strategic imperative that safeguards your organization’s digital assets. This guide outlines five essential steps designed to streamline the audit process while enhancing compliance and security effectiveness. As organizations navigate the complexities of cybersecurity, they often grapple with critical questions:
- Are your audit objectives aligned with evolving threats?
- Are you truly addressing the most pressing vulnerabilities?
By exploring these steps, you’ll uncover how to fortify your cybersecurity posture and ensure resilient compliance in an ever-changing landscape.
Define Cybersecurity Audit Objectives and Scope
-
Identify Stakeholders: Engaging key participants - such as IT, regulatory, and management - is essential. Their insights are crucial for aligning the evaluation with organizational goals and regulatory requirements. Have you considered how their input can shape the review's focus?
-
Set Clear Objectives: Establish specific goals for the evaluation. These might include identifying vulnerabilities, ensuring compliance with regulations, or assessing the effectiveness of security controls during a cyber security audit and compliance. Clear objectives not only direct the evaluation process but also assist in measuring success. What specific outcomes do you aim to achieve?
-
Determine Scope: Define the boundaries of the examination. Which systems, processes, and locations will be included? This focused approach ensures effective resource allocation and thorough examination of critical areas. For instance, businesses must evaluate 18 specific cyber controls during evaluations, including authentication methods and access management, to meet compliance standards. Are you covering all necessary aspects?
-
Document Everything: Create a formal record outlining the objectives and scope. This ensures all stakeholders agree and understand the review's direction. Such documentation acts as a reference point during the evaluation process, upholding transparency and accountability. How will you ensure everyone is on the same page?
-
Review and Adjust: Be open to revising the objectives and scope based on stakeholder feedback or changes in the organizational environment. Routine evaluations help adjust to evolving security threats and regulatory demands, ensuring continuous adherence to cyber security audit and compliance as well as efficiency. As highlighted by information security experts, establishing clear evaluation goals is essential for navigating the complexities of compliance and improving your overall security stance. Are your goals adaptable to change?
Establish Audit Criteria and Benchmarks
-
Research Relevant Standards: Start by identifying the cybersecurity frameworks and standards that are most applicable to your organization, such as NIST or ISO 27001. These standards will serve as the foundation for your evaluation criteria, ensuring that your approach is both comprehensive and aligned with industry best practices.
-
Define Specific Metrics: Next, establish clear and measurable criteria for assessing the effectiveness of your security controls. Consider metrics like incident response times, vulnerability patching rates, and user access controls. These metrics will not only help you gauge performance but also drive improvements in your security posture.
-
Benchmark Against Industry Standards: It’s crucial to compare your organization’s current practices against established industry benchmarks. This comparison will help you identify gaps and areas for improvement, allowing you to enhance your security measures effectively.
-
Document Criteria: Create a formal document that outlines the established criteria and benchmarks. This documentation is essential for ensuring clarity among all audit participants and serves as a reference point for compliance efforts.
-
Review Regularly: Finally, make it a priority to periodically reassess your criteria and benchmarks. As technology and threats evolve, so too must your evaluation standards. Regular reviews will help ensure that your organization remains resilient and compliant in the face of changing cybersecurity landscapes.
Conduct Interviews and Documentation Reviews
-
Prepare Interview Questions: Begin by crafting a tailored set of inquiries for various roles within the organization. Focus on their understanding of security policies and practices, particularly how often they conduct a cyber security audit and compliance to evaluate and update these policies.
-
Schedule Interviews: Arrange discussions with key personnel, including IT staff, management, and end-users. This will help gather diverse perspectives on security practices and adherence to established policies.
-
Review Documentation: Gather and scrutinize pertinent documentation, such as security policies, incident response plans, and training materials. This assessment will gauge compliance and effectiveness regarding cyber security audit and compliance. Ensure policies are reviewed at least annually as part of a cyber security audit and compliance process, that there’s a formal method for proposing and approving changes, and that an archive of previous policy versions is maintained.
-
Take Detailed Notes: Meticulously document findings from interviews and reviews to capture all insights for analysis. This includes tracking version control and communication strategies related to policy changes.
-
Synthesize Information: Integrate insights from interviews and documentation to pinpoint patterns, strengths, and weaknesses in the organization’s cybersecurity posture. Pay particular attention to the effectiveness of their policy maintenance practices related to cyber security audit and compliance.
Perform Technical Assessment and Analysis
-
Select Assessment Tools: Start by identifying and choosing the right tools for weakness scanning, penetration testing, and configuration reviews that fit your organization's technology stack. The most effective tools integrate seamlessly with existing systems and provide robust protection against potential risks.
-
Conduct Security Scans: Execute automated scans to uncover known weaknesses within your systems and applications. It's essential to document all findings meticulously, as this data is crucial for understanding your security posture and prioritizing remediation efforts. Remember, ongoing scanning is vital, especially since the landscape of vulnerabilities changes rapidly. Risk management automation tools can consistently scan, prioritize, and coordinate patch actions to address these weaknesses.
-
Perform Penetration Testing: Simulate real-world attacks on critical systems to evaluate the effectiveness of your security controls. This proactive approach helps identify potential weaknesses before adversaries can exploit them. Current trends show a shift towards more sophisticated techniques in penetration testing, particularly with the anticipated rise of AI-generated vulnerabilities by 2026. This underscores the need for adaptive strategies that reflect the evolving threat landscape.
-
Analyze Configuration Settings: Review your system configurations against industry best practices and regulatory requirements. Ensuring secure configurations is vital for minimizing attack surfaces and preventing unauthorized access. Regular audits of these settings are essential for ensuring cyber security audit and compliance, which helps uphold standards and strengthen overall security.
-
Compile Technical Findings: Document all technical assessment results, focusing on significant weaknesses and areas that require immediate attention. This collection not only aids in regulatory reporting but also serves as a guide for remediation efforts related to cyber security audit and compliance. Engaging with security scanning tools can simplify this process, enabling effective tracking and management of identified risks.
Document and Communicate Audit Findings
-
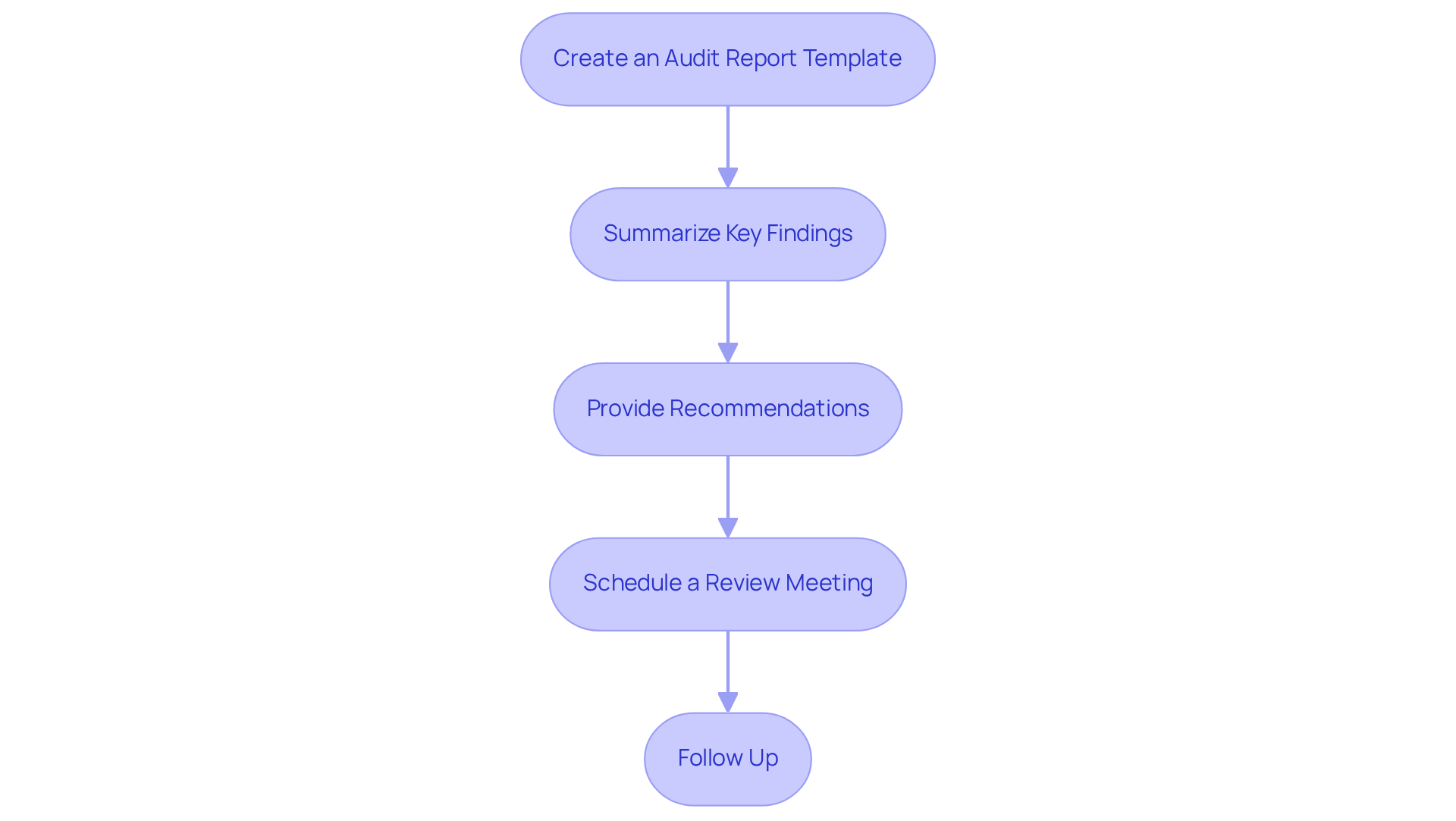
Create an Audit Report Template: Establishing a standardized template for documenting findings is crucial. This ensures consistency and clarity across all reports. The template for the cyber security audit and compliance should include sections for weaknesses, regulatory gaps, and suggestions to aid in clearer comprehension for stakeholders.
-
Summarize Key Findings: It’s essential to clearly highlight the most critical vulnerabilities and compliance gaps identified during the cyber security audit and compliance process. Each finding must be contextualized to illustrate its significance and potential impact on the organization’s security stance. How can these vulnerabilities affect your operations?
-
Provide Recommendations: Offer actionable recommendations to address the identified issues, prioritizing them based on risk and impact. This approach not only assists in prompt remediation but also supports long-term strategic planning for cyber security audit and compliance enhancements. What steps can you take today to mitigate these risks?
-
Schedule a Review Meeting: Organize a meeting with key stakeholders to present the findings. This discussion should focus on the implications of the audit results and foster a collaborative environment for addressing the identified issues. Engaging stakeholders is vital for effective resolution.
-
Follow Up: Implement a follow-up process to track the progress of recommendations. Regular assessments of improvements over time are crucial for ensuring that the organization maintains cyber security audit and compliance while also being resilient against emerging cybersecurity threats. Are you prepared to adapt to new challenges?
Conclusion
Establishing a robust framework for cybersecurity audits and compliance is not just essential; it’s a necessity for organizations determined to protect their digital assets. Are you ready to take the necessary steps? By defining clear objectives and scope, documenting findings, and effectively communicating results, organizations can significantly enhance their security posture and ensure compliance with regulatory standards. This structured approach minimizes risks and fosters a culture of continuous improvement in cybersecurity practices.
Key insights from the article underscore the importance of engaging stakeholders, setting measurable benchmarks, conducting thorough interviews, and performing technical assessments. Each of these steps is pivotal in identifying vulnerabilities and ensuring that your organization is prepared to tackle emerging threats. Regular reviews of audit criteria and findings are crucial for maintaining compliance and adapting to the ever-evolving cybersecurity landscape.
As organizations navigate the complexities of cybersecurity, prioritizing these audit processes is imperative. Implementing these best practices will not only help meet compliance requirements but also build a resilient security framework. Taking proactive measures today will pave the way for a more secure future, highlighting the critical nature of cybersecurity audits in safeguarding organizational integrity.
Frequently Asked Questions
What are the key objectives to define for a cybersecurity audit?
Key objectives include identifying vulnerabilities, ensuring compliance with regulations, and assessing the effectiveness of security controls.
Why is it important to identify stakeholders in a cybersecurity audit?
Engaging key participants such as IT, regulatory, and management is essential for aligning the evaluation with organizational goals and regulatory requirements.
How should the scope of a cybersecurity audit be determined?
The scope should define the boundaries of the examination, including which systems, processes, and locations will be included to ensure effective resource allocation and thorough examination.
What specific cyber controls should businesses evaluate during audits?
Businesses must evaluate 18 specific cyber controls, including authentication methods and access management, to meet compliance standards.
Why is documentation important in a cybersecurity audit?
Documentation creates a formal record of the objectives and scope, ensuring all stakeholders agree and understand the review's direction, promoting transparency and accountability.
How can organizations adapt their audit objectives and scope?
Organizations should be open to revising objectives and scope based on stakeholder feedback or changes in the organizational environment to address evolving security threats and regulatory demands.
What cybersecurity frameworks and standards should be researched for audit criteria?
Organizations should identify frameworks and standards such as NIST or ISO 27001 that are most applicable to them, as these serve as the foundation for evaluation criteria.
What specific metrics should be defined for assessing security controls?
Metrics may include incident response times, vulnerability patching rates, and user access controls to gauge performance and drive improvements.
Why is benchmarking against industry standards important?
Benchmarking helps identify gaps and areas for improvement by comparing current practices against established industry benchmarks, enhancing security measures effectively.
How often should audit criteria and benchmarks be reviewed?
Audit criteria and benchmarks should be reassessed periodically to ensure they remain relevant and effective in the face of evolving technology and threats.




