7 Steps to Remediate Risk in Cybersecurity for Defense Contractors
Learn how defense contractors can effectively remediate risk in cybersecurity with these 7 essential steps.

Overview
This article presents a comprehensive seven-step process for remediating cybersecurity risks tailored specifically for defense contractors. It underscores the critical need for systematic identification, assessment, and mitigation of vulnerabilities in today’s evolving threat landscape. By integrating the Cybersecurity Maturity Model Certification (CMMC) framework, this approach not only enhances compliance but also fortifies security posture.
Moreover, practical strategies for continuous monitoring and stakeholder engagement are essential components of this process. These strategies collectively empower organizations to proactively address vulnerabilities and adapt to emerging threats. As such, defense contractors are encouraged to implement these steps diligently to ensure robust cybersecurity measures are in place.
Introduction
In an age where cyber threats loom larger than ever, defense contractors face an uphill battle in safeguarding sensitive information against increasingly sophisticated attacks. The stakes are particularly high given the stringent regulations laid out by the Department of Defense, making effective risk remediation not just a best practice, but a necessity. This article delves into seven essential steps that defense contractors can take to systematically identify, assess, and mitigate cybersecurity risks, ensuring compliance while enhancing their overall security posture.
How can organizations navigate the complexities of risk remediation to not only meet regulatory demands but also fortify their defenses against potential breaches?
Understand Risk Remediation in Cybersecurity
Remediating risk in cybersecurity is a critical process involving the systematic identification, assessment, and mitigation of risks to an organization's information systems. This process is particularly vital for defense contractors, given the stringent requirements imposed by the Department of Defense (DoD). Understanding the various types of risks—technical vulnerabilities, human factors, and operational weaknesses—is essential for effective management.
Familiarizing yourself with the Cybersecurity Maturity Model Certification (CMMC) framework is imperative, as it outlines specific practices and processes necessary for compliance. This foundational knowledge not only informs your remediation strategies but also aligns them with the latest CMMC updates for 2025, ensuring that your organization meets evolving standards.
By leveraging practical advice from the CMMC Info Hub, such as peer insights on risk evaluations and incident response strategies, defense contractors can enhance their cybersecurity posture. This proactive approach enables them to remediate risk while navigating compliance challenges more efficiently, ultimately strengthening their defense against potential threats.

Identify and Inventory Vulnerabilities
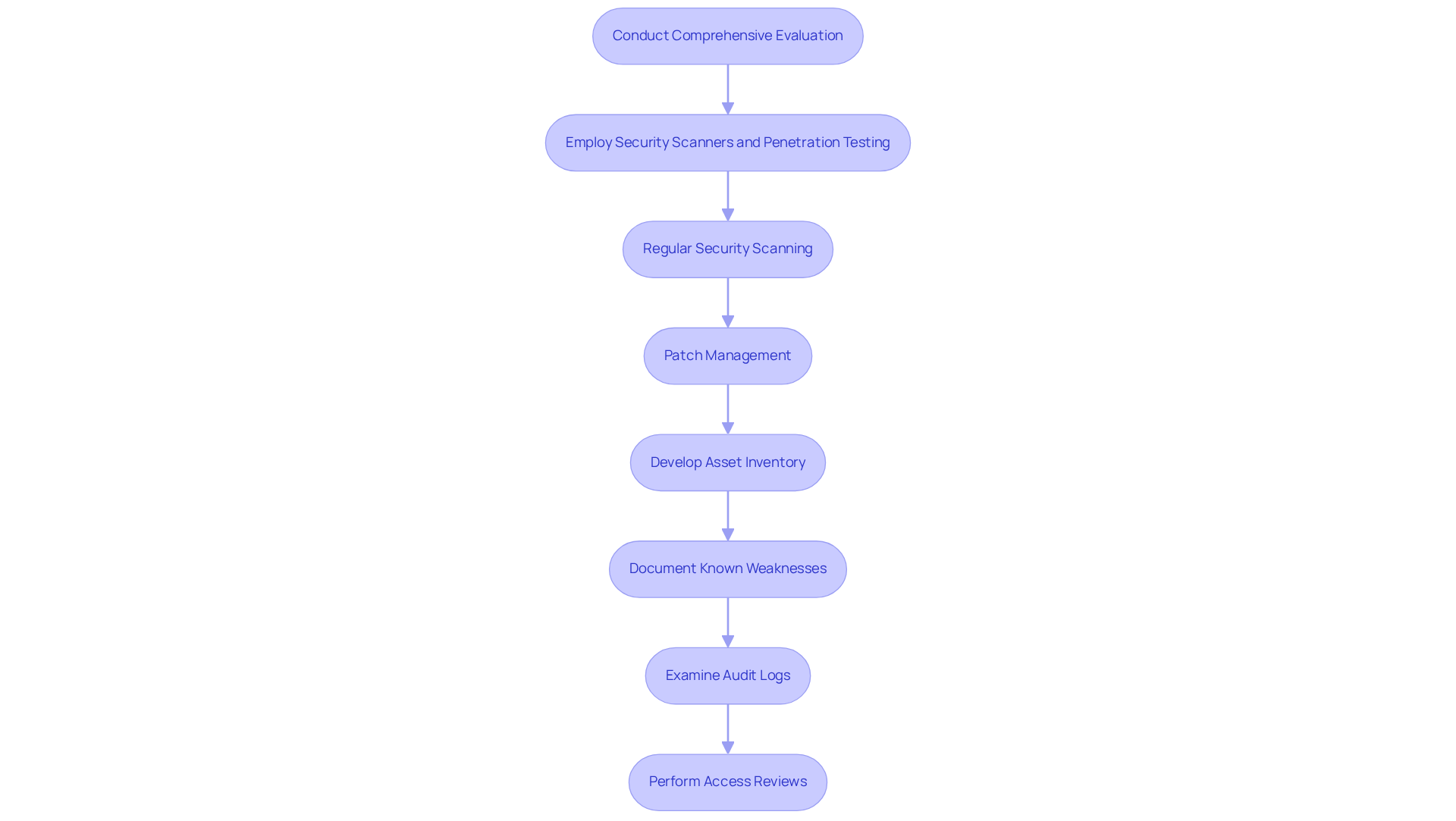
To effectively pinpoint weaknesses, it is crucial to conduct a comprehensive evaluation of your systems and processes to remediate risk. Start by employing tools such as security scanners and penetration testing to uncover any flaws. Regular security scanning is essential for detecting vulnerabilities, while prompt patch management ensures that systems and applications remain up-to-date.
Developing a detailed list of all assets—including hardware, software, and network components—is vital. Document any known weaknesses associated with these assets; this inventory will serve as a baseline for your remediation efforts. It allows you to track progress and prioritize actions effectively.
Furthermore, routinely examining audit logs and performing access reviews will significantly enhance your risk management strategy. By incorporating these practices, you not only bolster your security posture but also create a proactive approach to compliance that helps to remediate risk.
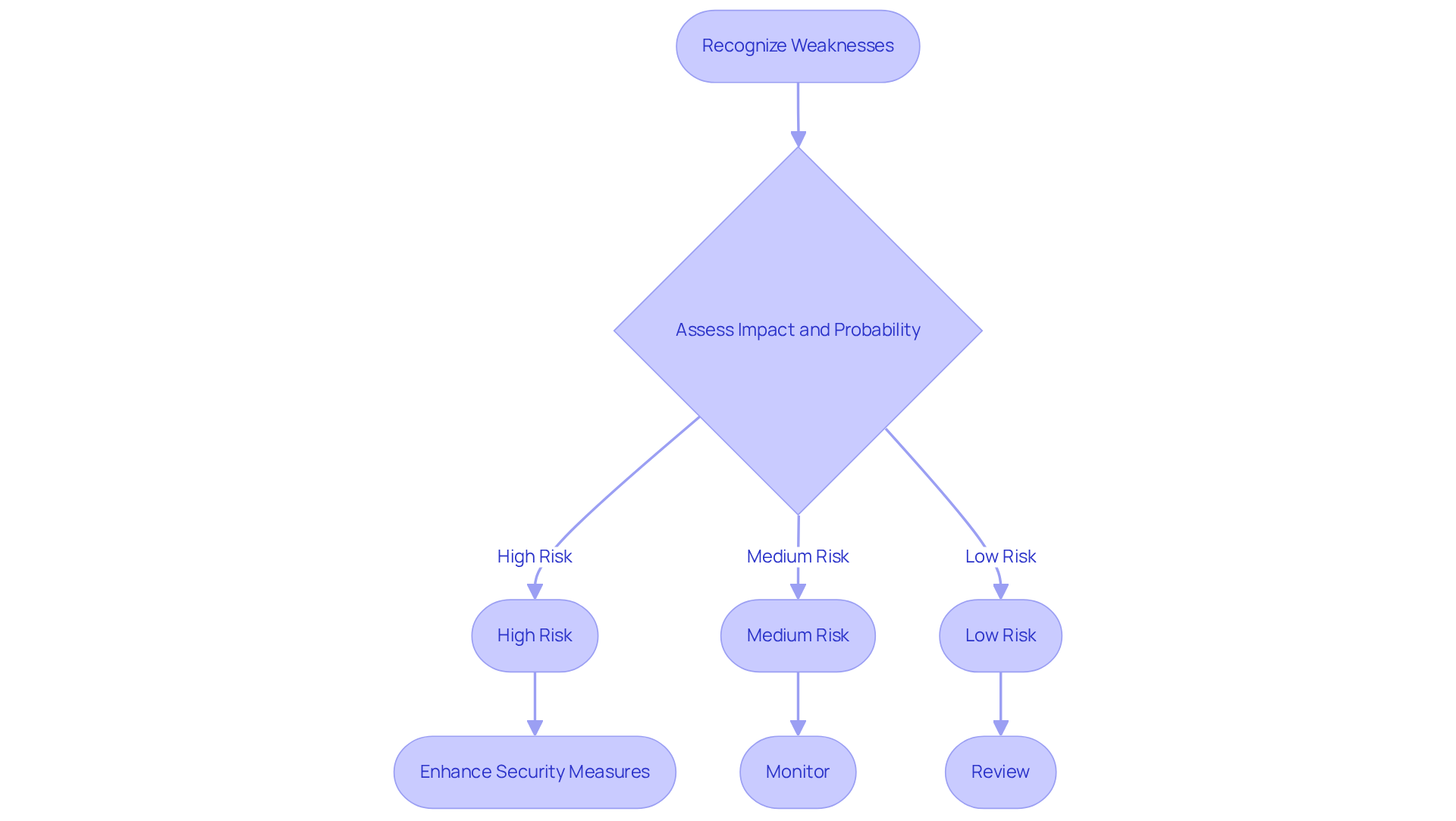
Classify and Prioritize Risks
Recognizing weaknesses is the first step; however, it is essential to categorize them based on their potential impact and probability of exploitation. By employing a likelihood-impact matrix as a decision analytics tool, organizations can effectively classify these risks as high, medium, or low. This prioritization is crucial. Concentrating on high-risk weaknesses significantly enhances adherence to regulations and fortifies an organization’s overall security stance. For instance, organizations utilizing integrated models have reported triage workflows that are 14 to 18 times more effective, underscoring the importance of directing efforts toward the most critical threats.
Methodically assessing weaknesses enables defense contractors to remediate risk and align their correction strategies with regulatory obligations and operational priorities. This process transforms confusion into understanding in their compliance efforts. As Shubham Jha aptly noted, 'The aim of vulnerability prioritization is to shift from considering every alert as a crisis and instead utilize logic, context, and intelligence in decision-making for resolutions.' Effective use of risk matrices not only streamlines the process to remediate risk but also fosters a proactive approach to cybersecurity.
Moreover, continuous monitoring and feedback loops are necessary to adapt to evolving threats. This adaptability is vital for safeguarding sensitive information and maintaining compliance with stringent standards. Organizations must recognize that a structured approach to vulnerability management not only helps to remediate risk but also enhances their overall security posture.
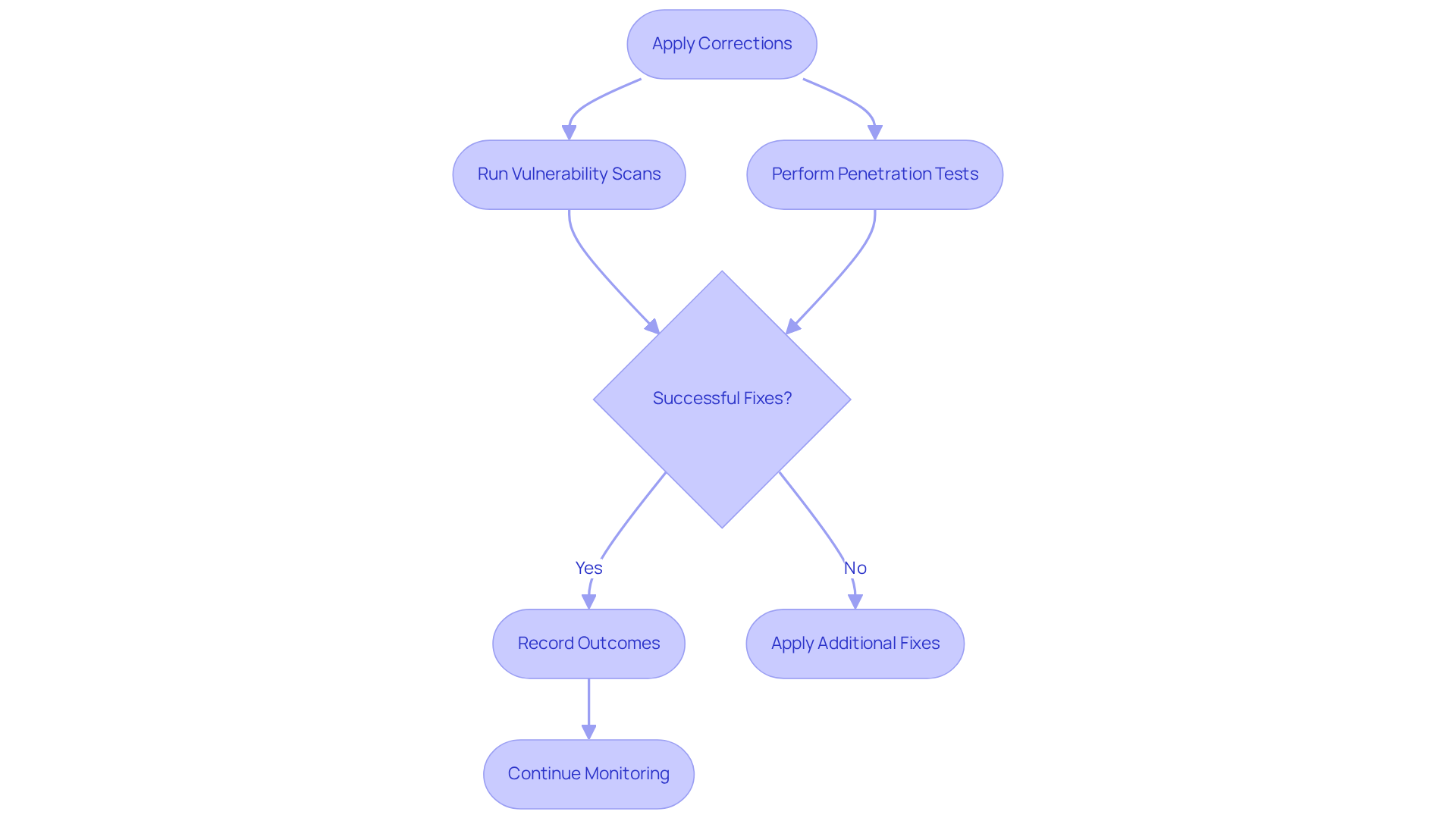
Apply Fixes to Vulnerabilities
Implement solutions for recognized weaknesses based on their priority classification. This process may include applying software patches, reconfiguring systems, or enhancing security protocols. It is crucial to record and evaluate these solutions to confirm their effectiveness; comprehensive documentation plays a key role in addressing security issues.
To sustain strong digital protection, continuous tasks such as performing regular security assessments and executing prompt patch management are essential. Collaborate closely with IT teams to ensure that all changes comply with organizational policies and regulatory requirements. This step is vital for strengthening your cybersecurity posture and helping to remediate risk. Remember, effective patch management is a cornerstone of defense contractor cybersecurity.

Verify Remediation Effectiveness
After applying corrections, it is essential to carry out follow-up evaluations to verify that weaknesses have been successfully addressed. This process may include re-running vulnerability scans or performing penetration tests to validate the success of the fixes. Recording the outcomes of these evaluations not only offers proof of adherence but also helps to remediate risk in future strategies.
Ongoing verification is crucial for maintaining a robust security posture. Organizations that incorporate follow-up evaluations into their protection measures can significantly enhance their resilience against emerging threats. In fact, studies indicate that 71% of organizations recognize the importance of penetration testing for compliance initiatives. This statistic underscores the necessity of these assessments in upholding cybersecurity standards.
As noted by industry experts, a proactive approach to follow-up assessments is essential for ensuring that security measures remain effective and aligned with evolving regulatory requirements. By prioritizing these evaluations, organizations can not only demonstrate compliance but also remediate risk and foster a culture of continuous improvement in their security practices.
Monitor and Document Remediation Progress
Establish a strong monitoring strategy to oversee the advancement of your corrective actions. Utilizing project management tools is essential for documenting actions taken, timelines, and outcomes. Frequent evaluations of this documentation will enable you to determine if remediation objectives are being achieved and help you to remediate risk by recognizing any new weaknesses that may emerge. As CISA emphasizes, effective documentation and tracking are crucial for upholding security standards.
Essential ongoing activities for CMMC adherence include:
- Conducting regular vulnerability scans to identify security weaknesses.
- Implementing timely patch management.
- Reviewing audit logs for signs of security incidents.
- Monitoring systems for configuration drift.
- Conducting access reviews to ensure appropriateness.
- Continuously monitoring for security incidents.
By leveraging successful project management tools, your organization can ensure it remains compliant with CMMC standards while enhancing its overall cybersecurity posture. Practical strategies and peer insights can further assist you in attaining CMMC adherence with confidence.
Report Progress to Stakeholders
Regularly update stakeholders—including management, IT teams, and regulatory officers—on the progress of corrective actions. Employ clear and concise reporting formats to effectively communicate progress, challenges, and next steps. This transparency not only cultivates trust but also ensures alignment with the organization's compliance objectives.
Engaging stakeholders in the process to remediate risk is essential for fostering a culture of cybersecurity awareness and accountability. How can we ensure that all parties are not just informed but actively involved? By integrating stakeholders into the conversation, we can enhance our collective commitment to compliance.
Ultimately, this proactive approach not only strengthens our cybersecurity posture but also reinforces the importance of accountability among all team members. Let us take decisive action to involve our stakeholders and drive our compliance initiatives forward.
Conclusion
Remediating risk in cybersecurity is not merely a regulatory obligation for defense contractors; it is a critical element in protecting sensitive information and preserving operational integrity. This guide systematically outlines the necessity of:
- Understanding risk
- Identifying vulnerabilities
- Classifying and prioritizing risks
- Implementing effective solutions to establish a robust cybersecurity posture
Key strategies include:
- Leveraging the Cybersecurity Maturity Model Certification (CMMC) framework
- Utilizing tools for vulnerability identification
- Adhering to a stringent monitoring and documentation process
Each step—from verifying remediation effectiveness to engaging stakeholders—plays an essential role in ensuring that defense contractors not only comply with standards but also cultivate a culture of accountability and continuous improvement.
The importance of these practices cannot be overstated. By adopting a proactive stance towards cybersecurity risk remediation, defense contractors can significantly enhance their resilience against emerging threats and build trust among stakeholders. It is imperative to take decisive action today to implement these strategies, thereby ensuring not only compliance but also the security and integrity of critical systems in an increasingly complex digital landscape.
Frequently Asked Questions
What is risk remediation in cybersecurity?
Risk remediation in cybersecurity is the systematic process of identifying, assessing, and mitigating risks to an organization's information systems, which is particularly important for defense contractors due to strict Department of Defense (DoD) requirements.
Why is understanding different types of risks important?
Understanding various types of risks—such as technical vulnerabilities, human factors, and operational weaknesses—is essential for effective risk management and remediation strategies.
What is the Cybersecurity Maturity Model Certification (CMMC)?
The CMMC is a framework that outlines specific practices and processes necessary for compliance with cybersecurity standards, helping organizations align their remediation strategies with evolving requirements.
How can defense contractors improve their cybersecurity posture?
Defense contractors can enhance their cybersecurity posture by leveraging practical advice from resources like the CMMC Info Hub, utilizing peer insights on risk evaluations, and adopting incident response strategies.
What tools can be used to identify vulnerabilities?
Tools such as security scanners and penetration testing are crucial for uncovering flaws in systems and processes, helping organizations to detect vulnerabilities effectively.
Why is regular security scanning important?
Regular security scanning is essential for detecting vulnerabilities and ensuring that systems and applications are kept up-to-date through prompt patch management.
What should be included in an inventory for vulnerability management?
A detailed inventory should include all assets—hardware, software, and network components—along with any known weaknesses associated with these assets to serve as a baseline for remediation efforts.
How can audit logs and access reviews enhance risk management?
Routinely examining audit logs and performing access reviews significantly improve risk management strategies by identifying potential security issues and ensuring compliance.