9 Key Insights on Compliance Meaning in Cyber Security for Defense Contractors
Explore the compliance meaning in cyber security for defense contractors and ensure regulatory success.

Introduction
Understanding compliance in cybersecurity is crucial for defense contractors navigating the complex regulations that govern their operations. With the Department of Defense tightening its grip on cybersecurity standards, the stakes have never been higher. Organizations must protect sensitive information while securing lucrative contracts. This article explores nine key insights that illuminate the path to compliance, revealing both the challenges defense contractors face and the best practices that can lead to success.
How can these firms transform regulatory demands into a strategic advantage? What steps must they take to ensure they are not left behind in this evolving landscape? Let's delve into these critical questions and uncover actionable insights that can empower organizations to thrive in a challenging environment.
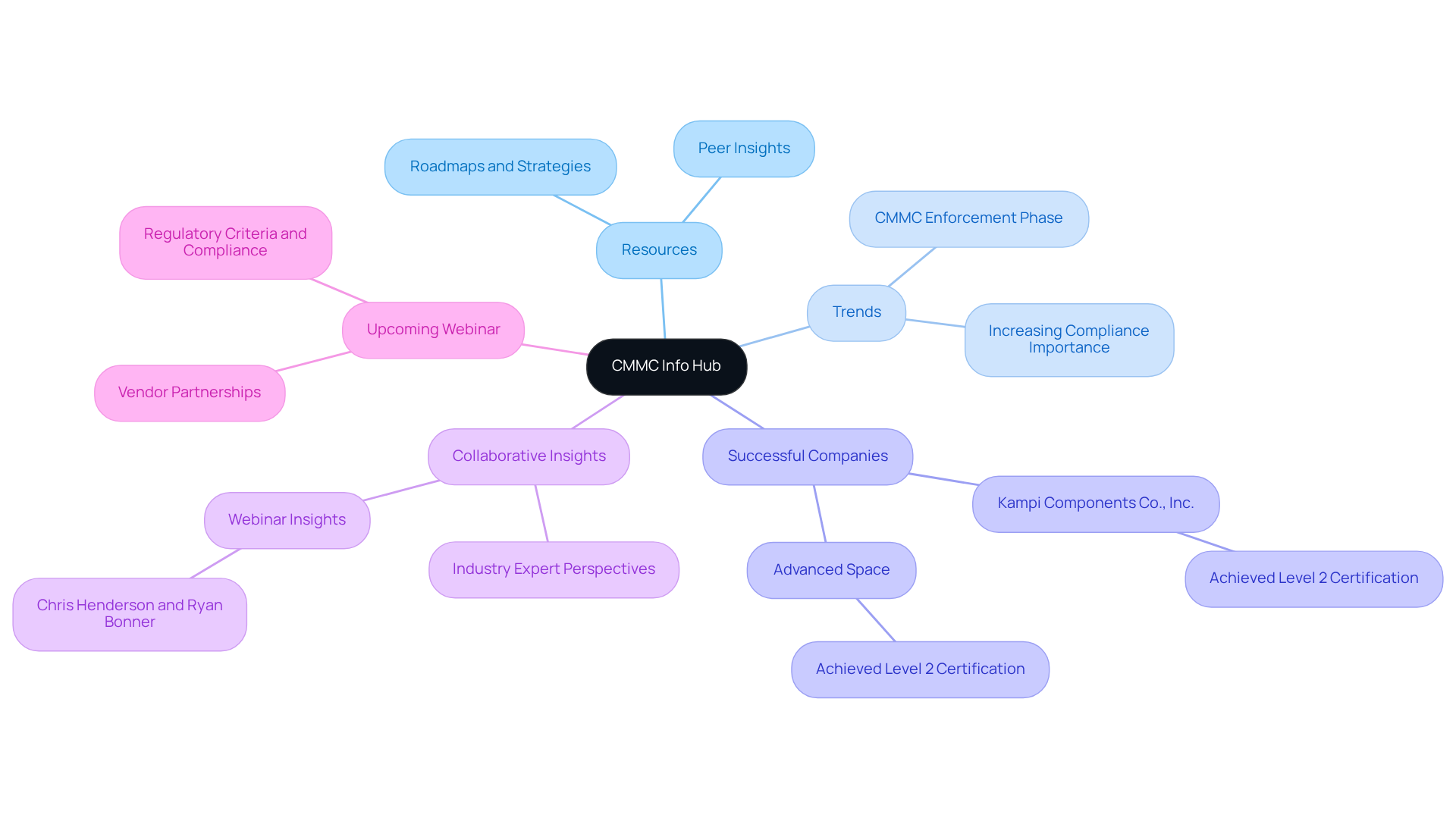
CMMC Info Hub: Your Essential Resource for Cybersecurity Compliance Insights
The information hub stands as a crucial resource for military suppliers aiming to achieve compliance with the Cybersecurity Maturity Model Certification (CMMC). This platform offers comprehensive roadmaps and actionable strategies tailored to the complexities of Department of Defense (DoD) cybersecurity requirements, ensuring organizations can effectively protect Controlled Unclassified Information (CUI). By concentrating on content related to certification standards, the Info Hub delivers practical insights that empower users to navigate their regulatory journey with confidence.
Recent trends indicate that adherence to cybersecurity standards is increasingly vital for defense contractors, as the Department of Defense mandates compliance for new contracts. Companies like Kampi Components Co., Inc. and Advanced Space exemplify successful execution of the cybersecurity maturity model, both achieving Level 2 certification and showcasing their commitment to robust cybersecurity practices.
CMMC Info Hub provides a wealth of resources, including peer insights that allow users to learn from the experiences of others within the regulatory landscape. This collaborative approach not only streamlines the regulatory process but also enhances the overall cybersecurity posture of organizations. Experts highlight the platform's effectiveness in transforming confusion into clarity, making it an indispensable resource for companies navigating the evolving regulatory environment.
Additionally, an upcoming webinar featuring Chris Henderson and Ryan Bonner will delve into regulatory criteria and compliance, offering further expert perspectives for service providers. As the initiative continues to evolve, the Info Hub remains dedicated to delivering the latest information and strategies, ensuring military suppliers are well-equipped to meet regulatory demands and secure future contracts.
Understanding Regulatory Compliance in Cybersecurity
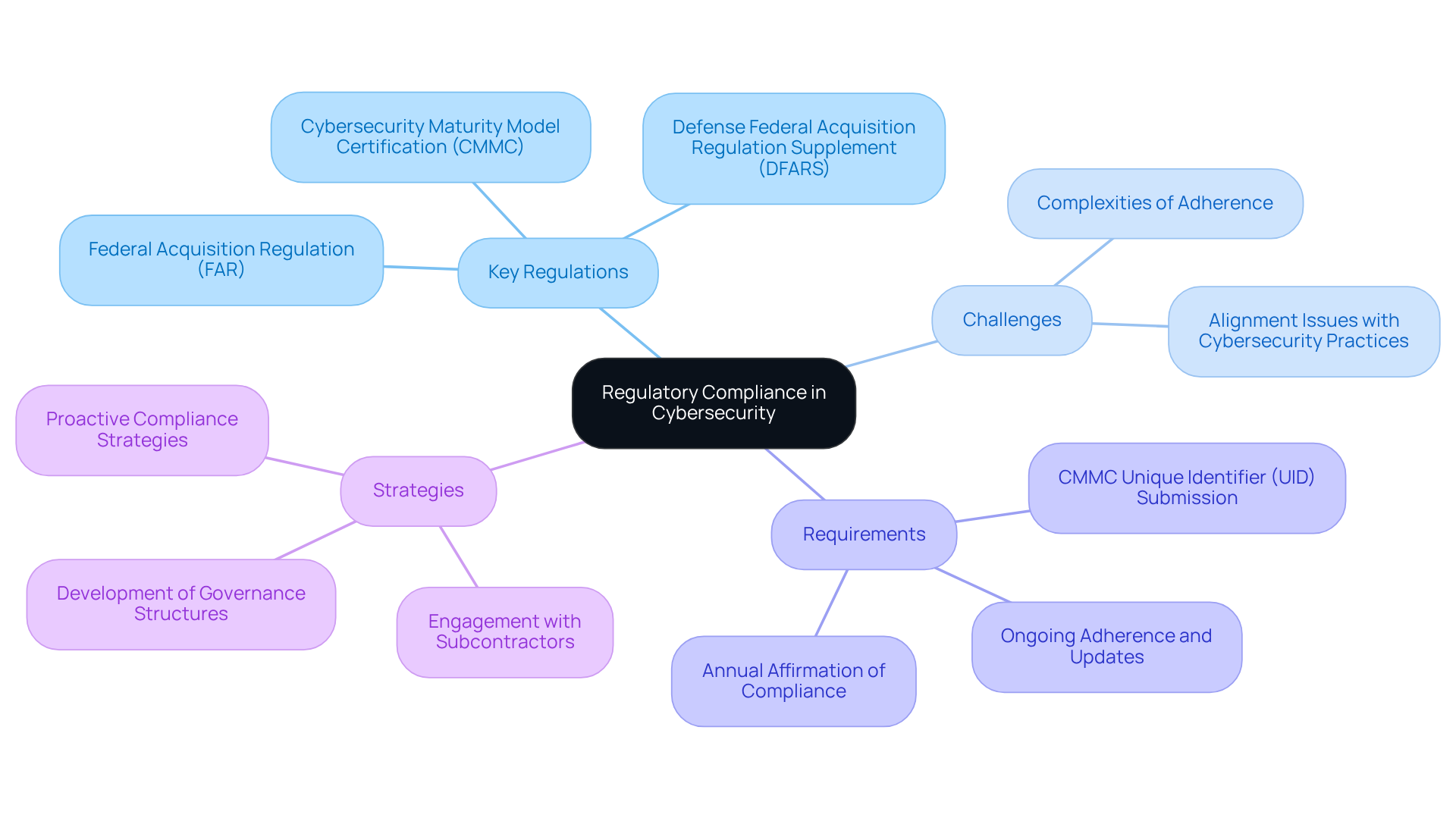
The compliance meaning in cyber security is crucial for protecting sensitive information. For suppliers in the security sector, this adherence primarily revolves around the Federal Acquisition Regulation (FAR), the Defense Federal Acquisition Regulation Supplement (DFARS), and the Cybersecurity Maturity Model Certification (CMMC). These regulations are not just bureaucratic hurdles; they are essential for securing and maintaining contracts while safeguarding sensitive data.
As we approach 2025, many defense suppliers are still grappling with the complexities of adhering to FAR and DFARS. Numerous organizations face challenges in aligning their cybersecurity practices with these stringent standards. Notably, the DFARS has introduced new clauses mandating vendors to implement specific cybersecurity measures. For instance, vendors must submit a Cybersecurity Maturity Model Certification Unique Identifier (UID) for systems handling Federal Contract Information (FCI) or Controlled Unclassified Information (CUI). This requirement underscores the importance of ongoing adherence throughout the contract lifecycle, as service providers must regularly update their adherence status in the Supplier Performance Risk System (SPRS).
Successful instances of suppliers adhering to FAR and DFARS often involve proactive engagement with their subcontractors to ensure compliance with CMMC requirements. This collaboration is vital, as prime contractors are responsible for verifying their subcontractors' adherence before contract awards. The compliance meaning in cyber security illustrates that the implications of regulatory adherence for defense firms in 2025 are significant; non-compliance can lead to serious risks, including potential liabilities under the False Claims Act and the loss of valuable contract opportunities.
Perspectives on the challenges of adhering to FAR and DFARS vary, but many industry experts stress the need for robust adherence strategies that can withstand scrutiny from contracting officers and regulatory agencies. The evolving regulatory landscape demands that contractors not only understand these regulations but also develop comprehensive governance structures to effectively navigate the complexities associated with compliance meaning in cyber security.
The Role of Industry Standards in Cybersecurity Compliance
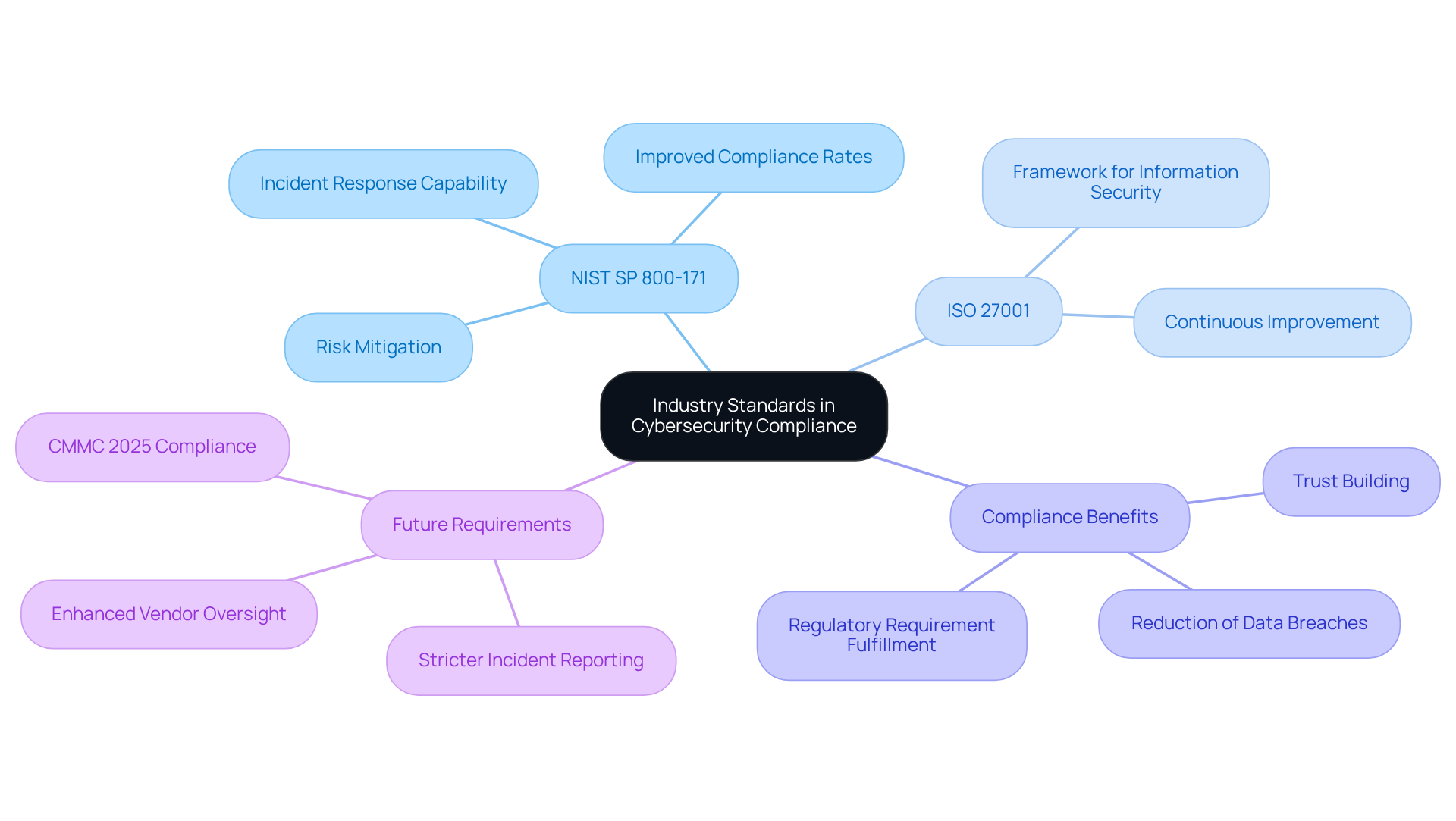
Industry standards are crucial in shaping cybersecurity adherence, providing essential benchmarks for organizations to follow. Standards such as NIST SP 800-171 and ISO 27001 offer comprehensive frameworks for managing sensitive information and effectively mitigating risks. By aligning with these standards, military suppliers can significantly enhance their security posture.
Organizations familiar with NIST 800-171 controls often demonstrate improved compliance meaning in cyber security rates, which highlights the challenges in achieving full compliance. Adhering to these standards not only meets regulatory requirements but also builds trust with the Department of Defense and other stakeholders, which reflects the compliance meaning in cyber security. For example, organizations that implement NIST SP 800-171 controls can substantially reduce the likelihood of data breaches, as many incidents could have been prevented with proper adherence to these guidelines.
As the regulatory landscape evolves, particularly with the upcoming 2025 requirements, understanding and integrating these standards will be vital for contractors aiming to secure their position in the military supply chain. CMMC Info Hub provides practical strategies and peer insights to help navigate these complexities confidently.
Are you ready to take the necessary steps towards compliance? Embrace these standards to not only protect your organization but also to foster trust and reliability in your partnerships.
Establishing Internal Policies and Procedures for Compliance
Creating robust internal policies and procedures is crucial for compliance with cybersecurity regulations in the defense sector. Organizations must establish clear guidelines that define acceptable use, incident response protocols, and data protection measures. Did you know that only 37% of leaders in adherence feel confident in evaluating program effectiveness? This statistic underscores the necessity for clarity and consistency in messaging.
Efficient communication of these policies is essential. Regular training sessions play a vital role, as they not only enhance employee awareness of their responsibilities but also adapt to the evolving regulatory landscape. Successful security providers have implemented comprehensive training initiatives that emphasize the importance of cybersecurity awareness. This approach has led to improved adherence rates and a reduction in breach occurrences.
Moreover, organizations with well-defined cybersecurity policies demonstrate a higher level of readiness against regulatory challenges. By prioritizing internal processes and fostering a culture of compliance, military contractors can bolster their resilience against cyber threats while ensuring adherence to regulatory requirements.
In conclusion, the establishment of strong internal policies, coupled with ongoing training and clear communication, is not just a regulatory obligation; it is a strategic imperative for organizations in the defense sector.
Implementing Effective Auditing and Monitoring Practices
Implementing effective auditing and monitoring practices is crucial for maintaining cybersecurity adherence within defense contracting. Frequent audits are essential to assess compliance meaning in cyber security with established policies and regulatory requirements, ensuring that organizations remain aligned with standards. Ongoing observation of systems and processes is vital for detecting potential vulnerabilities and addressing any deviations from regulations promptly. Organizations that have adopted continuous monitoring practices report enhanced security postures, as they can proactively detect and respond to threats before they escalate.
To turn confusion into clarity, utilizing practical strategies and peer insights is crucial for attaining CMMC adherence with confidence. The integration of automated tools significantly boosts the efficiency and effectiveness of these monitoring practices. Automated monitoring systems, such as Security Information and Event Management (SIEM) platforms, provide real-time alerts and behavior analysis, allowing organizations to defend against cyber threats proactively. Case studies show that companies utilizing automated monitoring not only enhance their regulatory processes but also lessen the manual workload on security teams, allowing them to concentrate on strategic initiatives. This proactive method is essential in the changing environment of cybersecurity, where understanding the compliance meaning in cyber security is necessary due to the complexity of threats, requiring a strong and adaptable regulatory strategy. By adhering to the ultimate guide for attaining CMMC standards, military suppliers can master the requirements, implement necessary controls, and secure military contracts successfully.
Importance of Documentation and Reporting in Compliance
Documentation and reporting are essential elements of a robust regulatory program, particularly for defense contractors navigating the complexities of cybersecurity regulations. Organizations must maintain precise records of their adherence activities, including policies, procedures, and audit results. This documentation serves as critical evidence during audits and demonstrates compliance with regulatory requirements, such as those outlined by the Cybersecurity Maturity Model Certification (CMMC).
As we approach 2025, security providers must confirm adherence to specific safety standards, making regular updates on compliance status increasingly vital. This proactive approach not only helps organizations identify areas for improvement but also fosters accountability within their teams. By employing effective reporting techniques, builders can ensure they meet the evolving requirements of regulations, ultimately enhancing their readiness for Department of Defense contracts and safeguarding sensitive information.
Best Practices for Achieving Security Compliance
To achieve security standards, organizations must adopt several best practices, especially those relevant for defense contractors. Routine risk evaluations are essential. They help recognize vulnerabilities and ensure that security measures adhere to the compliance meaning in cyber security as it relates to regulatory standards. In fact, organizations that perform regular risk evaluations at least once a year can significantly improve their security stance and adherence rates.
Implementing a robust training program for employees is equally important. Regular awareness training educates staff on recognizing cyber threats, such as phishing attempts, which account for over 80% of reported security incidents. This proactive approach not only reduces the likelihood of breaches but also fosters a culture of security awareness within the organization.
Employing automated regulatory management tools simplifies processes and lessens the complexity linked to regulatory activities. Automation is increasingly recognized as an effective method to reduce expenses and ease audit fatigue. In fact, 65% of regulatory professionals believe it improves efficiency.
Interacting with industry colleagues and participating in regulatory forums offers valuable insights and assistance. Groups that collaborate with others in the security sector often uncover best practices and innovative solutions to shared regulatory challenges.
Successful examples of risk assessments in defense contractors highlight the importance of these strategies. For instance, organizations that have incorporated AI into their regulatory programs report improved visibility into risks and enhanced control over regulatory processes. This trend underscores the growing recognition of compliance meaning in cyber security as a strategic enabler, with 77% of global C-suite leaders acknowledging its contribution to overall business objectives.
In summary, a comprehensive strategy that encompasses regular risk evaluations, staff training, automation, and peer involvement is crucial for defense contractors aiming to achieve and uphold cybersecurity standards.
Conducting Regular Security Audits and Assessments
Frequent security audits and evaluations are essential for identifying weaknesses and ensuring compliance with cybersecurity regulations. Organizations should establish a structured schedule for these audits, ideally conducting them at least annually or after significant changes to systems or processes. These evaluations not only assess the effectiveness of existing controls but also pinpoint areas that require improvement.
Have you considered the benefits of engaging third-party auditors? Their impartial perspective can significantly enhance the credibility of the audit process. In fact, organizations with well-developed regulatory programs are 2.3 times more likely to meet regulatory audit deadlines, underscoring the value of external insights. Moreover, external audits can uncover sophisticated security threats that internal teams might overlook, leading to more robust security protocols.
For instance, regular audits have proven critical for schools and nonprofits, helping them identify vulnerabilities and strengthen incident response plans. By prioritizing these evaluations, contractors can significantly enhance their cybersecurity posture and improve their success rates in meeting regulations. Don't wait - implement a structured audit schedule today to safeguard your organization.
Implementing Strong Access Controls for Compliance
Implementing strong access controls is not just important; it's essential for achieving cybersecurity compliance within the framework's guidelines. Have you considered how a least privilege access model could transform your organization? By granting employees only the permissions necessary for their specific roles, you significantly reduce the risk of unauthorized access and potential data breaches.
Moreover, multi-factor authentication (MFA) serves as a critical enhancement to security. Its successful application across various industries, including military contracting, showcases its effectiveness in safeguarding sensitive information. Conducting regular audits of access permissions is vital to meet established requirements and understand the compliance meaning in cyber security. This ensures adherence to policies and allows for adjustments in response to personnel changes.
But it doesn’t stop there. Fostering a culture of security awareness through employee training on the significance of access controls can greatly strengthen your organization's cybersecurity posture. As highlighted in 'The Ultimate Guide to Achieving CMMC Adherence,' staying informed about the latest trends - like mobile access credentials and decentralized identity verification - is crucial for contractors aiming to uphold regulations and protect their assets. Are you ready to take the necessary steps to enhance your compliance efforts?
Developing an Incident Response Plan for Compliance Readiness
Creating a robust incident response strategy is essential for regulatory preparedness in contracting. This plan must clearly outline the procedures for detecting, containing, eradicating, and recovering from cybersecurity incidents. Did you know that organizations conducting regular tests of their incident response plans at least quarterly can respond to incidents 35% faster? Yet, only 30% of organizations routinely test their plans, revealing a significant gap in preparedness.
Training employees on their specific roles within the incident response framework is vital for minimizing response times and reducing potential damage. Companies with documented incident response plans incur 58% lower costs per breach compared to those without structured protocols. Furthermore, organizations that implement changes based on past incidents can reduce future incident rates by 50%. This highlights the importance of not just having a plan but actively refining it through regular drills and post-incident reviews.
In the contracting sector, where strict adherence to cybersecurity regulations is paramount, the compliance meaning in cyber security, along with a clearly outlined incident response plan, can significantly enhance an organization's resilience against cyber threats. By prioritizing these strategies and following the ultimate guide to achieving CMMC compliance, defense contractors can navigate the complexities of compliance meaning in cyber security more effectively and safeguard sensitive information.
Conclusion
The importance of compliance in cybersecurity for defense contractors is paramount. As organizations face the complexities of regulations like the Cybersecurity Maturity Model Certification (CMMC), grasping and implementing these standards is crucial for protecting sensitive information and ensuring contract eligibility. Compliance transcends being a mere checkbox; it stands as a strategic necessity that fortifies the overall security posture and operational integrity of defense suppliers.
Key insights have surfaced throughout this discussion, underscoring the vital role of industry standards, robust internal policies, and effective auditing practices. The significance of thorough documentation and continuous training cannot be overstated, as these components cultivate a culture of compliance and readiness. Moreover, the development of a comprehensive incident response plan is essential, enabling organizations to react swiftly and effectively to potential cyber threats.
As the regulatory landscape evolves, defense contractors must take proactive measures toward compliance. By embracing best practices, engaging with industry resources, and fostering collaboration, organizations can not only enhance their adherence to regulations but also build trust with stakeholders. Prioritizing cybersecurity compliance is not just about meeting requirements; it secures a place in the military supply chain and contributes to a safer digital environment.
Are you ready to take the necessary steps toward compliance? The time to act is now.
Frequently Asked Questions
What is the purpose of the CMMC Info Hub?
The CMMC Info Hub serves as a crucial resource for military suppliers to achieve compliance with the Cybersecurity Maturity Model Certification (CMMC), offering roadmaps and strategies tailored to Department of Defense (DoD) cybersecurity requirements.
Why is compliance with cybersecurity standards important for defense contractors?
Compliance with cybersecurity standards is vital for defense contractors because the Department of Defense mandates it for new contracts, ensuring the protection of Controlled Unclassified Information (CUI) and securing contract opportunities.
What resources does the CMMC Info Hub provide?
The CMMC Info Hub offers a wealth of resources, including peer insights, practical strategies, and expert perspectives to help users navigate the regulatory landscape and enhance their cybersecurity posture.
What are the key regulations that defense suppliers must adhere to?
Defense suppliers must primarily adhere to the Federal Acquisition Regulation (FAR), the Defense Federal Acquisition Regulation Supplement (DFARS), and the Cybersecurity Maturity Model Certification (CMMC).
What are some challenges faced by defense suppliers in achieving compliance?
Many defense suppliers struggle with aligning their cybersecurity practices with FAR and DFARS standards, particularly with new clauses mandating specific cybersecurity measures and the requirement to submit a Cybersecurity Maturity Model Certification Unique Identifier (UID).
How does non-compliance affect defense contractors?
Non-compliance can lead to serious risks, including potential liabilities under the False Claims Act and the loss of valuable contract opportunities.
What industry standards are important for cybersecurity compliance?
Important industry standards include NIST SP 800-171 and ISO 27001, which provide frameworks for managing sensitive information and mitigating risks.
How can adherence to industry standards benefit organizations?
Adhering to industry standards not only helps meet regulatory requirements but also builds trust with the Department of Defense and reduces the likelihood of data breaches.
What upcoming event is mentioned that will provide further insights into regulatory compliance?
An upcoming webinar featuring Chris Henderson and Ryan Bonner will discuss regulatory criteria and compliance, offering expert perspectives for service providers.
How can organizations prepare for the evolving regulatory landscape?
Organizations should understand and integrate industry standards, develop robust adherence strategies, and utilize resources like the CMMC Info Hub to navigate the complexities of compliance confidently.