9 Steps to Build Your IT Security Strategy Roadmap
Create a robust IT security strategy roadmap to enhance compliance and safeguard your organization.

Overview
The article titled "9 Steps to Build Your IT Security Strategy Roadmap" outlines crucial steps organizations must take to craft an effective IT security strategy. Why is this important? Assessing your current security posture is the first step. It allows you to identify vulnerabilities and understand where improvements are needed.
Next, defining clear objectives that align with your business goals is essential. This alignment ensures that your security measures support your overall mission rather than hinder it. Continuous monitoring and improvement of these measures are vital, especially as threats evolve. By staying proactive, you can fortify your defenses against cyber risks.
In summary, developing a robust IT security strategy is not just about compliance; it’s about safeguarding your organization’s future. Are you ready to take these steps? By implementing these strategies, you can create a resilient security framework that adapts to the ever-changing landscape of cyber threats.
Introduction
Building a robust IT security strategy roadmap is no longer just a recommendation; it has become a necessity for organizations navigating the complexities of today’s cyber landscape. With rising threats and stringent compliance requirements—particularly the Cybersecurity Maturity Model Certification (CMMC)—entities must adopt a proactive approach to safeguarding their assets. This article outlines nine essential steps that not only enhance security measures but also align them with overarching business goals.
How can organizations effectively transform their cybersecurity posture while ensuring compliance and resilience against evolving threats? By taking decisive action now, businesses can not only protect their assets but also position themselves for success in an increasingly challenging environment.
CMMC Info Hub: Your Guide to Cybersecurity Maturity Model Certification Compliance
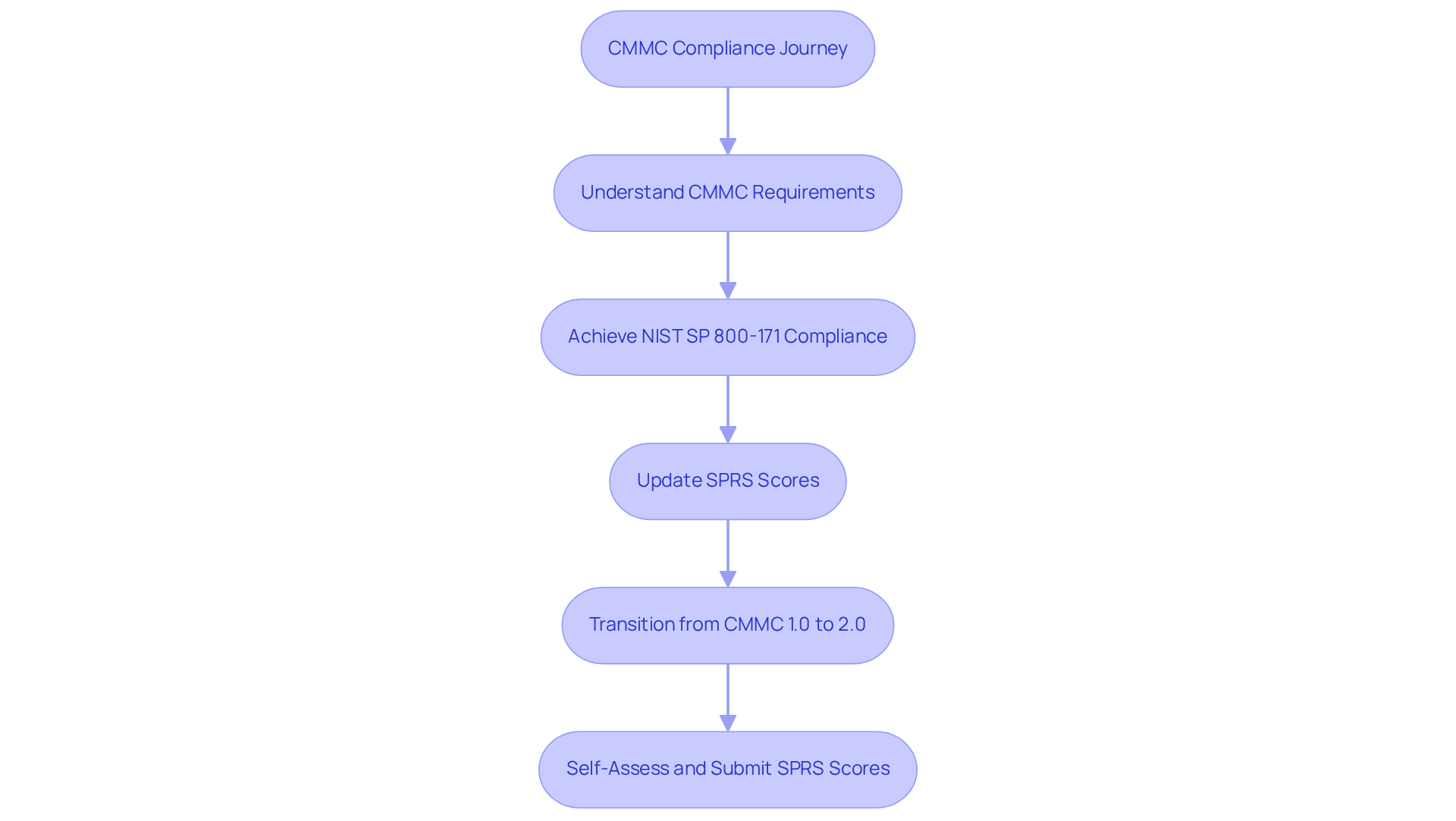
CMMC Info Hub serves as a vital knowledge base designed to assist entities in achieving compliance with the Cybersecurity Maturity Model Certification (CMMC). It provides structured guidance, detailed roadmaps, and practical strategies tailored to the complexities of DoD cybersecurity requirements as part of the IT security strategy roadmap. By leveraging insights from peers and experts, users can confidently navigate the compliance landscape, ensuring they meet the stringent standards necessary for securing defense contracts and safeguarding sensitive information.
The impact of CMMC compliance on defense contracts is significant, as it has become a mandatory requirement for all contractors, especially small and medium-sized businesses, due to rising cyber threats. CMMC Info Hub equips defense contractors with essential features, including comprehensive articles, guides, and actionable strategies that support the creation of an IT security strategy roadmap and facilitate successful assessments. This transformation from confusion to clarity empowers entities to approach compliance with assurance.
Successful implementation examples underscore the effectiveness of CMMC Info Hub's approach. For instance, experienced contractors are encouraged to maintain their NIST SP 800-171 compliance and ensure their Supplier Performance Risk System (SPRS) scores are up-to-date, positioning them favorably for upcoming mandatory compliance requirements. Furthermore, the transition from CMMC 1.0 to 2.0 has streamlined the compliance process, making it more accessible for businesses.
Recent updates emphasize the urgency of compliance, with the final DFARS rule integrating CMMC 2.0 into defense contracts, effective November 10, 2025. This rule mandates that all contractors self-assess and submit their scores in the SPRS, reinforcing the necessity of robust cybersecurity practices. As the DoD underscores the importance of cybersecurity in its contracting procedures, CMMC Info Hub remains an essential partner for entities aiming to enhance their cybersecurity posture and secure eligibility for defense contracts.
Assess Your Current Security Posture: Identify Strengths and Weaknesses
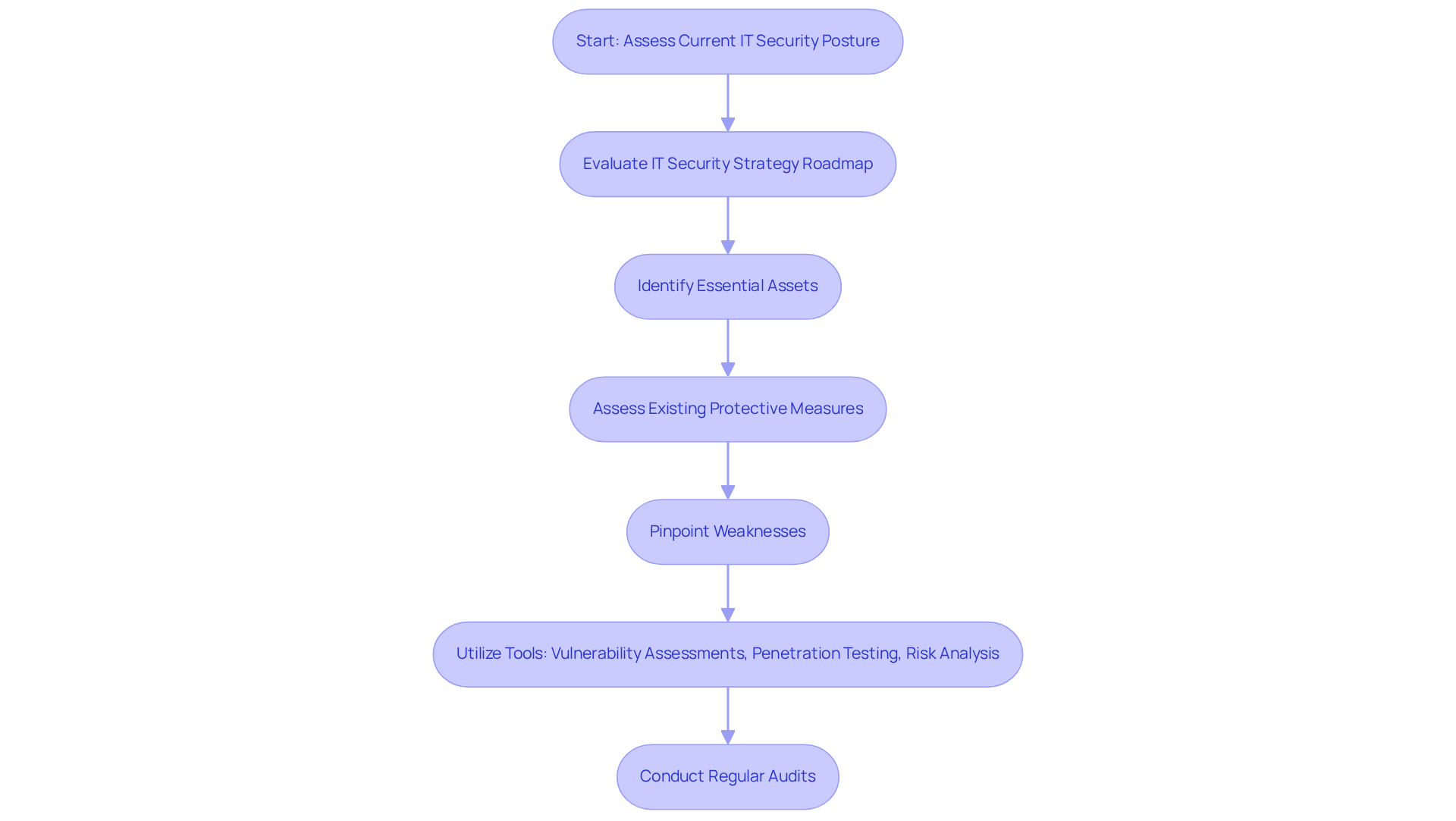
Begin with a thorough evaluation of your organization’s current IT security strategy roadmap. This crucial step in the IT security strategy roadmap involves identifying essential assets, assessing existing protective measures, and pinpointing weaknesses. Utilize tools such as vulnerability assessments, penetration testing, posture evaluations, and risk analysis frameworks to gain a comprehensive understanding of your strengths and vulnerabilities.
Why is this important? A staggering 61% of control leaders have reported breaches stemming from failed or misconfigured controls. This statistic underscores the necessity of conducting regular audits to prevent such breaches. Additionally, in 2022, an average of 19% of scanned software contained high or critical severity vulnerabilities. Prioritizing vulnerability management is essential to avoid backlogs; 47% of DevSecOps professionals believe that neglecting to prioritize vulnerabilities significantly contributes to these challenges.
Frequent evaluations and reviews are vital components of an effective IT security strategy roadmap. They help organizations adapt to evolving threats and ensure compliance with industry standards, ultimately enhancing their overall defense posture. By taking these proactive steps, you not only safeguard your assets but also fortify your organization against potential breaches.
Define Clear Security Objectives: Align IT Security with Business Goals
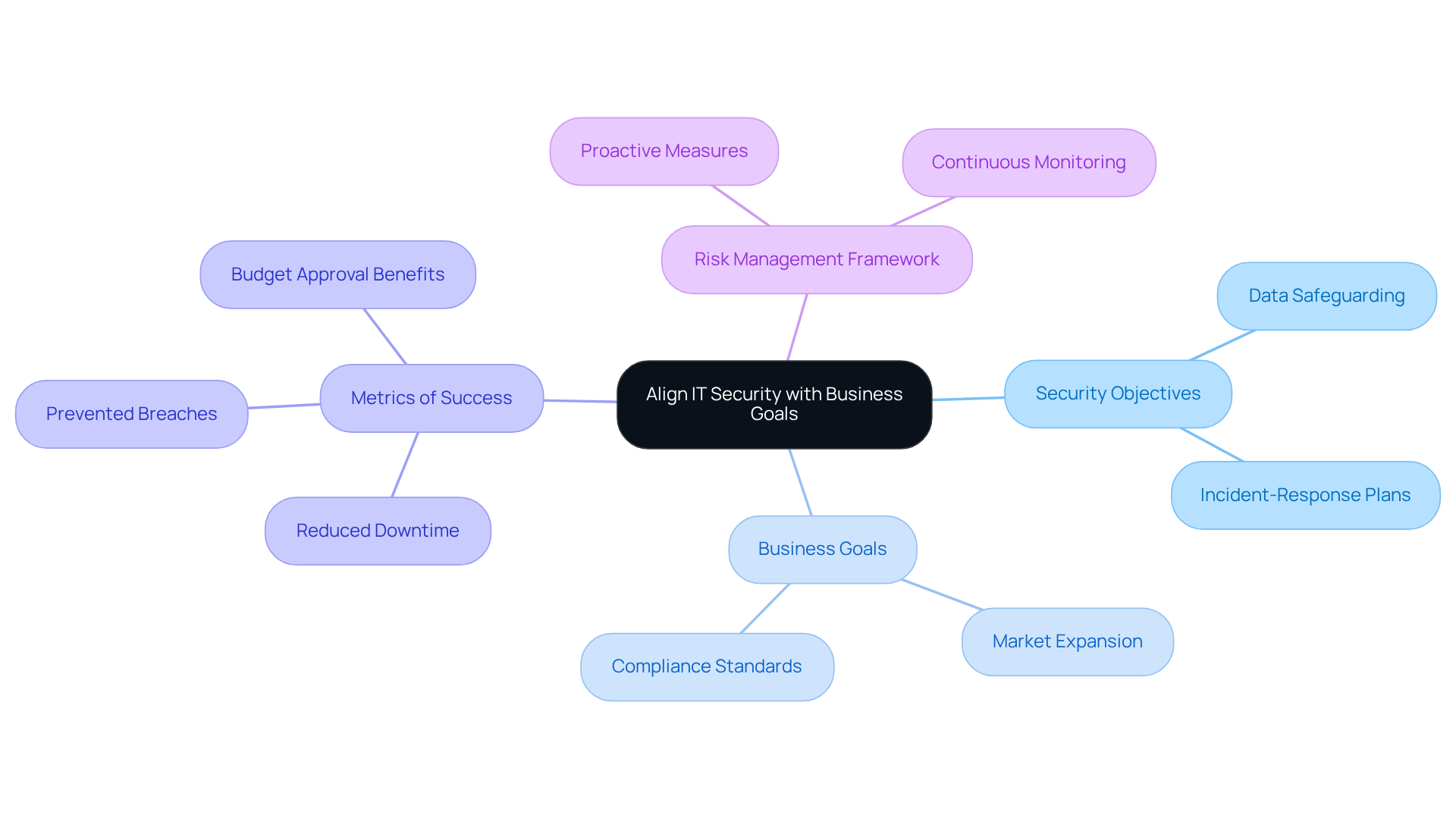
Setting clear protection objectives that align with your company's business aims is essential for fostering resilience. This process begins with a thorough understanding of your organization's mission, vision, and values, and how protection can bolster these objectives. For example, if your company plans to enter new markets, your protective strategy must specifically address the associated challenges, such as data safeguarding and compliance issues.
By integrating IT protection with business goals, organizations can create a cohesive risk management framework that not only safeguards assets but also enhances overall resilience. This alignment is critical; organizations that successfully weave cybersecurity into their business strategies are better equipped to adapt to evolving threats and seize growth opportunities. Alarmingly, only 37% of organizations have established incident-response plans, underscoring the urgent need for proactive protective measures.
Metrics like reduced downtime and prevented breaches further highlight the value of this approach, demonstrating how protective initiatives can drive business success and enhance leadership visibility during quarterly reviews. As Tushar Richabadas aptly states, "Aligning cybersecurity with business needs is probably the top requirement of effective cybersecurity that we often fail to deliver."
Moreover, organizations that track savings through dashboards and board reports achieve faster and more substantial budget approvals, showcasing the tangible benefits of aligning protection with business objectives.
In conclusion, prioritizing the alignment of cybersecurity with business goals not only fortifies your organization against threats but also positions it for sustainable growth.
Develop a Risk Management Strategy: Prioritize Security Initiatives
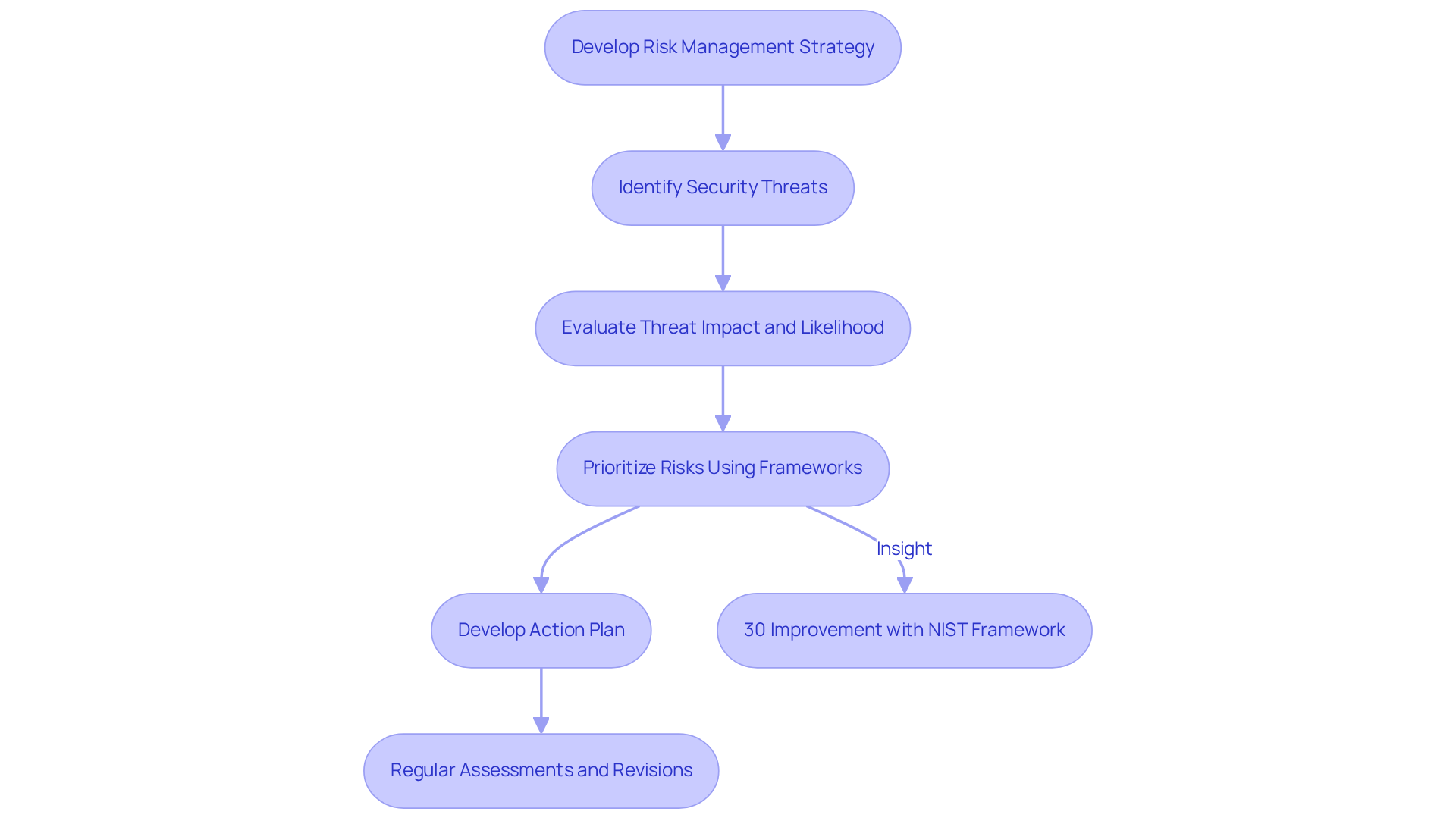
To effectively safeguard your organization, it's essential to create a robust IT security strategy roadmap that systematically identifies, evaluates, and prioritizes security threats. Have you considered utilizing established frameworks like NIST or FAIR? These frameworks allow you to assess threats based on their potential impact and likelihood of occurrence, ensuring a comprehensive understanding of your risk landscape.
This approach should include a detailed action plan as part of the IT security strategy roadmap for addressing high-priority challenges. By doing so, your entity can efficiently mitigate risks while optimizing resource allocation. Regular assessments and revisions to your IT security strategy roadmap are crucial. As the threat landscape evolves and business environments change, following an IT security strategy roadmap is key to staying agile.
For instance, organizations that have adopted the NIST framework report an average of 30% improvement in their assessment processes. This statistic underscores the framework's effectiveness in prioritizing protective initiatives. Moreover, the recent updates to the NIST Risk Management Framework emphasize a more agile approach, enabling organizations to respond swiftly to emerging threats and vulnerabilities.
By embracing these frameworks, businesses can ensure that their protective initiatives are not only prioritized effectively but also aligned with best practices in risk management. Are you ready to enhance your security posture and take action today?
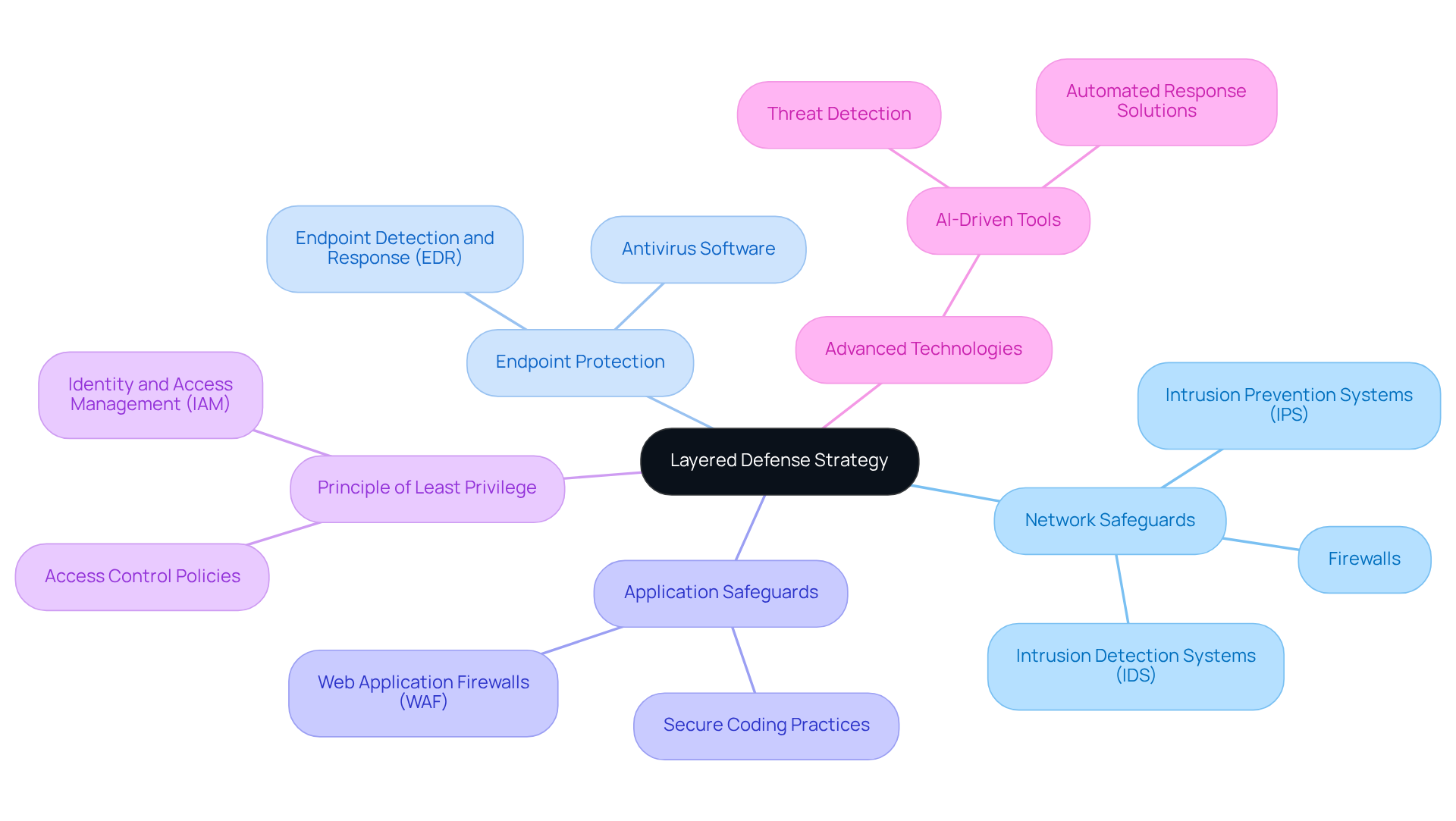
Build a Layered Defense Strategy: Enhance Security Through Multiple Measures
Implementing a layered defense strategy, often referred to as defense-in-depth, is crucial for fortifying your organization's security posture. This multifaceted approach involves deploying various protective measures across multiple layers, such as network safeguards, endpoint protection, and application safeguards. For example, integrating firewalls, intrusion detection systems (IDS), and antivirus software creates a robust defense framework. This strategy ensures that if one layer is compromised, others remain intact, significantly reducing the risk of successful cyberattacks.
Organizations are increasingly recognizing the effectiveness of defense-in-depth strategies. A recent report revealed that while 83% of organizations employ endpoint protection, only 5% have embraced microsegmentation. This highlights a considerable gap in proactive measures. Another critical component is the principle of least privilege, which restricts user access to only necessary resources. By limiting potential exposure, this principle acts as a safeguard, ensuring that even if an attacker gains access, their ability to navigate the network is severely restricted.
Moreover, the integration of advanced technologies, such as AI-driven tools, is becoming essential. While AI can enhance threat detection, it is not without flaws; concerns about its accuracy and explainability persist. As Chris Boehm, Field CTO, noted, "AI is not 100% accurate... in the end, it almost seems like it's confused or giving false positives." Security leaders must balance AI-driven automation with human oversight to avoid complacency.
The defense-in-depth strategy is not merely an abstract concept; it is a practical necessity in today's complex risk landscape and is essential for an effective IT security strategy roadmap. As cyber threats evolve, organizations must follow an IT security strategy roadmap that integrates traditional protective measures with advanced technologies to ensure comprehensive safeguarding. This layered approach not only bolsters resilience against attacks but also equips organizations to respond effectively to incidents, thereby protecting sensitive information and ensuring operational continuity. With global cybersecurity spending projected to reach $212 billion in 2025, investing in a layered defense strategy is more urgent than ever.
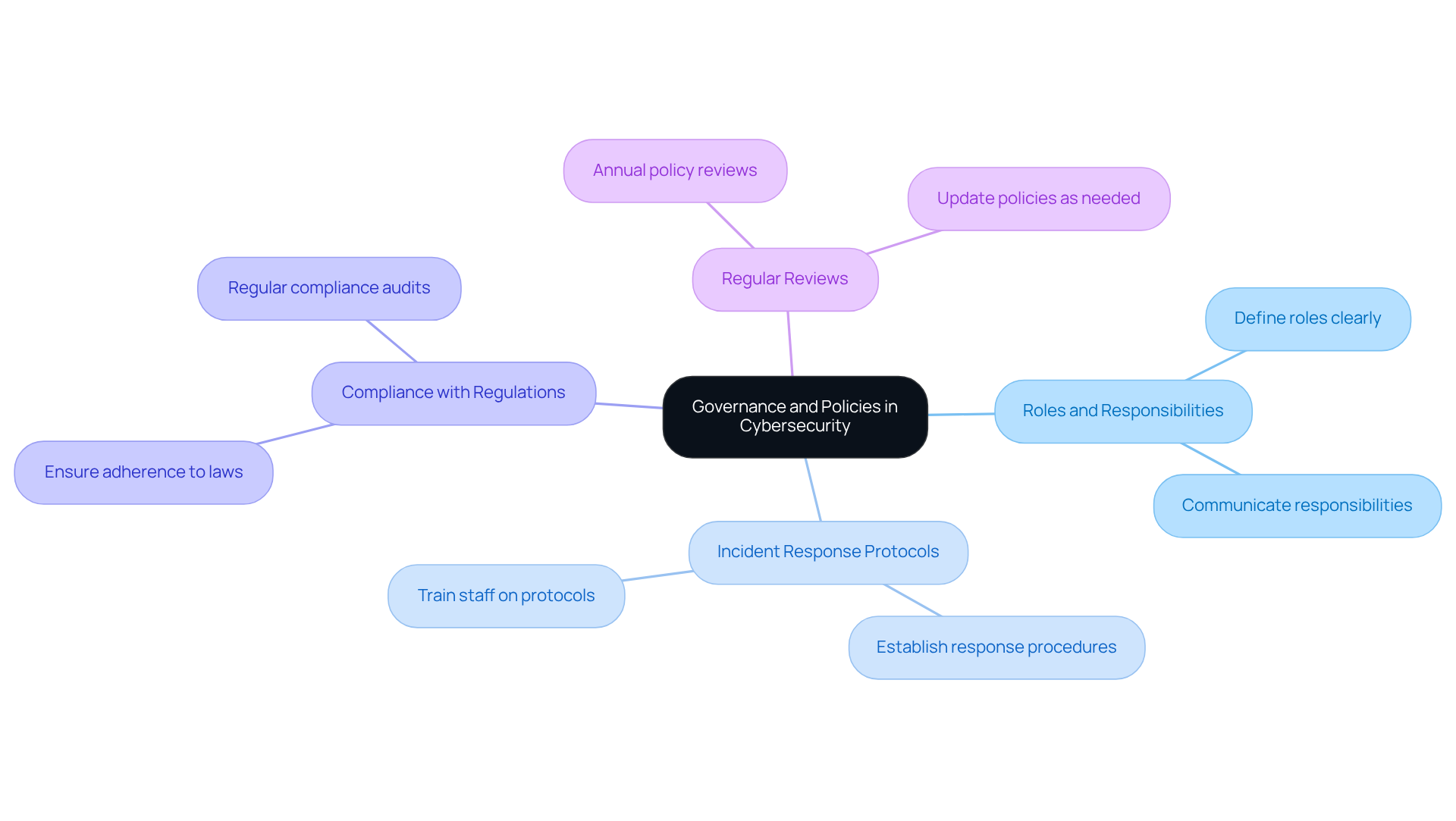
Establish Governance and Policies: Standardize Security Practices
Establishing robust governance structures and protective policies is essential for normalizing safety practices across your organization. This initiative should:
- Clearly define roles and responsibilities.
- Establish incident response protocols.
- Ensure compliance with applicable regulations.
Regular reviews and updates of these policies are crucial to adapt to the evolving threat landscape and organizational changes. Policies should be reviewed at least annually, with a formal process for proposing and approving changes to keep them current and effective.
Maintaining version control of policies and archiving previous versions is vital for accountability and historical reference. How well do your team members understand their roles in upholding cybersecurity? Effective communication of policy changes to all affected personnel fosters a culture of compliance and awareness. Not only does effective governance enhance protective measures, but it also cultivates accountability among team members.
As emphasized by NIST, the IT security strategy roadmap is a critical component of enterprise management, highlighting the importance of integrating protective policies into the broader organizational strategy. Moreover, instituting regular training and refreshers can significantly improve employee awareness and compliance with protocols. This ultimately leads to enhanced operational efficiency and resilience.
In summary, by prioritizing strong governance and protective policies, your organization can create a safer environment that not only meets compliance standards but also empowers employees to actively participate in safeguarding cybersecurity.
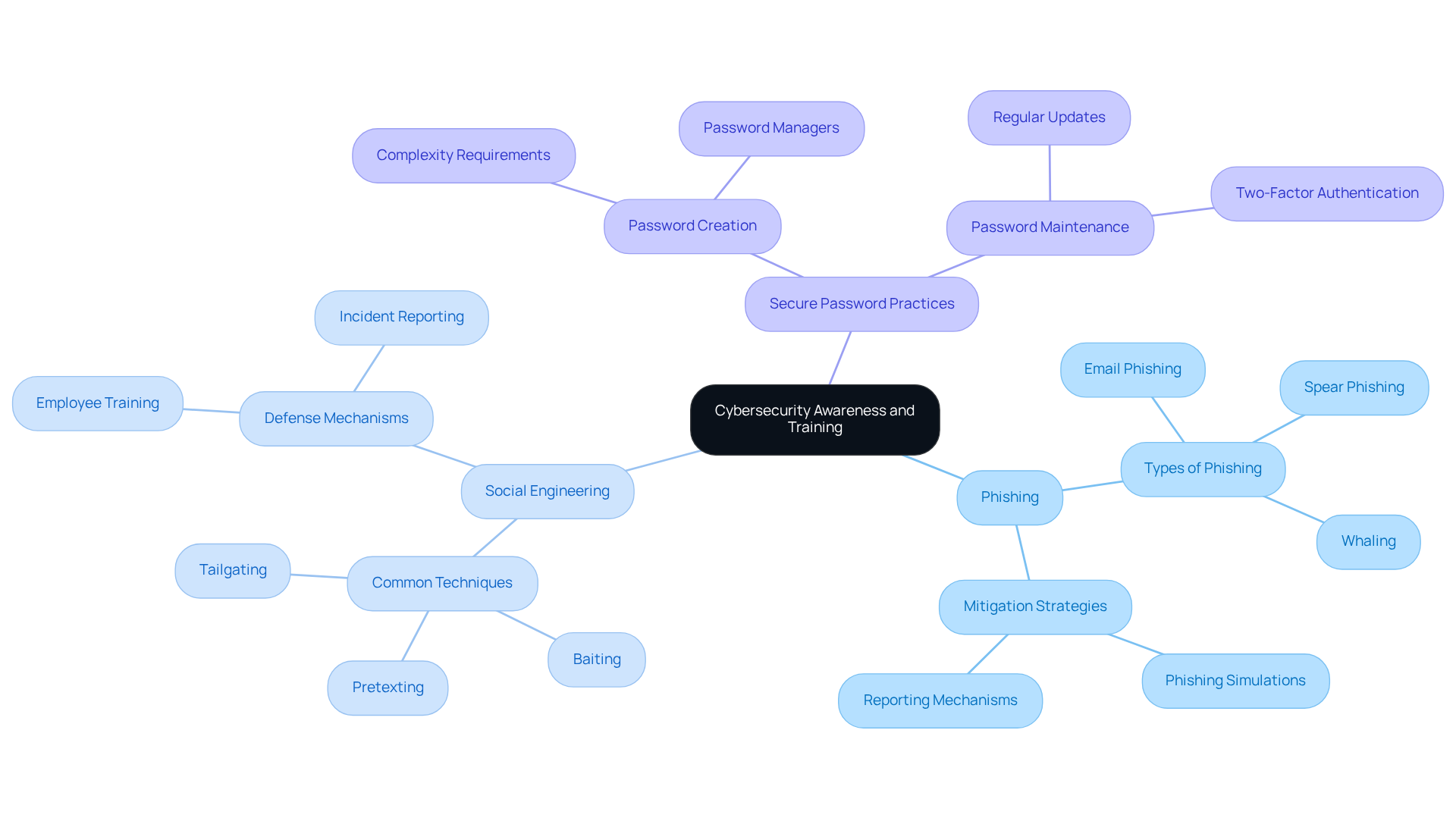
Invest in Security Awareness and Training: Empower Employees Against Threats
Establishing a robust awareness and training initiative is crucial for informing staff about potential cyber risks and effective methods to mitigate them. This training should encompass essential topics such as:
- Phishing
- Social engineering
- Secure password practices
Regularly updating training resources to reflect the latest risks and trends in cybersecurity is vital.
By fostering a culture of awareness, you empower employees to act as the first line of defense against cyber threats. This proactive approach significantly enhances your organization’s overall security posture. Are your staff equipped with the knowledge they need to recognize and respond to these threats?
Consider the impact of a well-informed team: statistics show that organizations with comprehensive cybersecurity training experience fewer breaches. By prioritizing this initiative, you not only protect your assets but also cultivate a sense of responsibility among your employees.
In conclusion, make it a priority to implement and continuously improve your cybersecurity training programs. This commitment will not only safeguard your organization but also instill confidence in your workforce, ensuring they are prepared to face the evolving landscape of cyber threats.
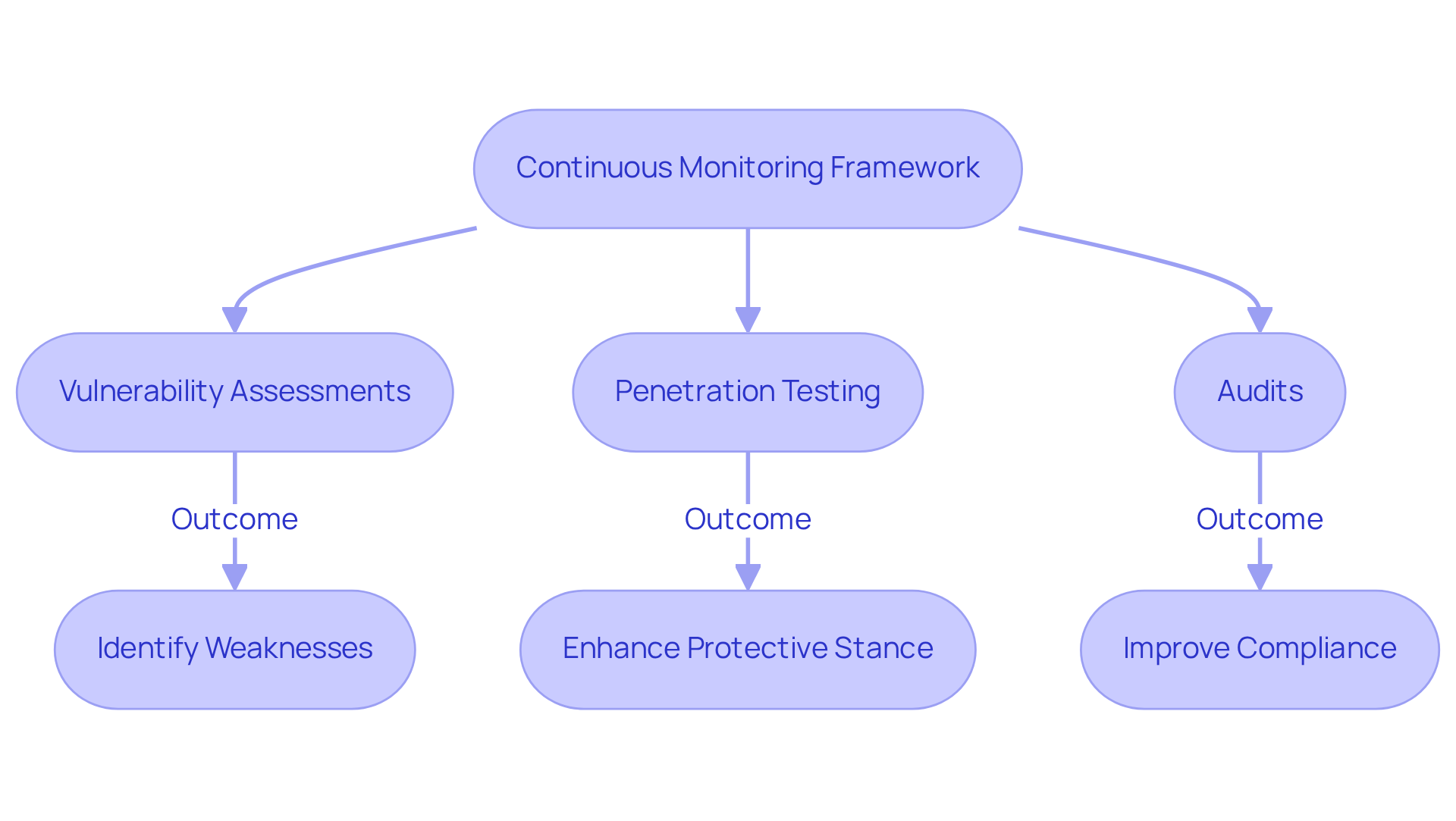
Monitor, Test, and Improve Continuously: Adapt to Evolving Threats
Creating a continuous monitoring and testing framework is crucial for regularly evaluating your organization's IT security strategy roadmap. This framework should encompass:
- Vulnerability assessments
- Penetration testing
- Audits to pinpoint weaknesses and identify areas for improvement
Have you considered how automated tools can enable real-time observation of safety events and incidents? They significantly enhance your capacity to react quickly to threats.
Remarkably, entities that conduct routine vulnerability evaluations—averaging at least quarterly—report substantial enhancements in their protective stance. For instance, a recent study revealed that companies performing regular penetration tests were able to lower their vulnerability exposure by up to 30%. As cyber threats evolve, the ongoing evaluation and enhancement of the IT security strategy roadmap become essential for effective protective measures. This ensures that defenses remain robust and effective against new challenges.
By embracing a proactive strategy for protection, organizations can more effectively safeguard their assets and uphold compliance with industry standards. Are you ready to take action? Implementing these practices not only strengthens your defenses but also positions your organization as a leader in cybersecurity compliance.
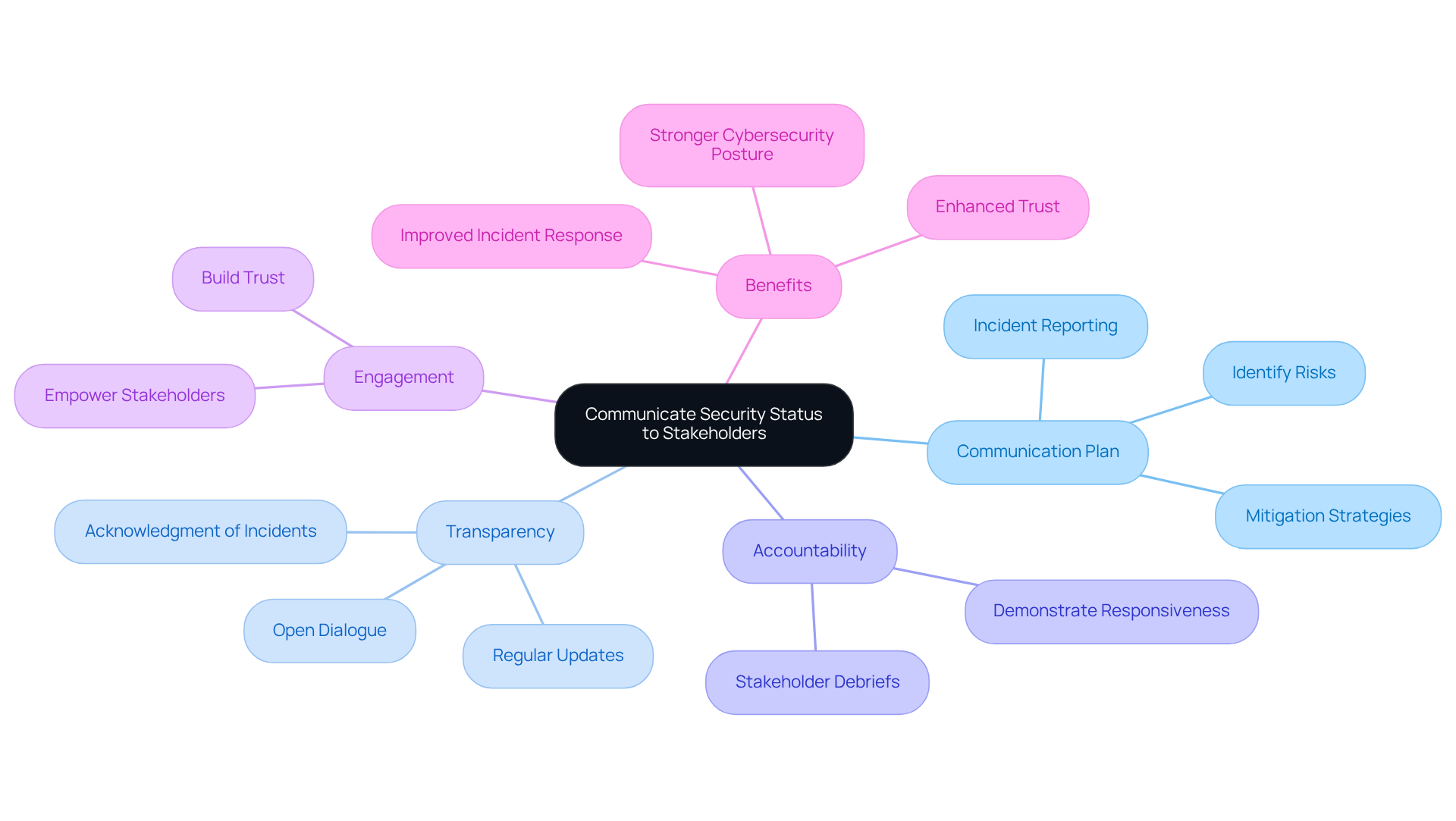
Communicate Security Status to Stakeholders: Foster Transparency and Accountability
To ensure stakeholders are consistently informed about the entity's safety status, it's crucial to create a robust communication plan. This plan should cover potential risks, incidents, and mitigation efforts. By using clear and concise language, complex safety concepts can be made accessible to non-technical stakeholders.
Fostering an environment of transparency allows entities to share both successes and challenges in their cybersecurity initiatives. This approach not only builds trust but also actively engages stakeholders in protective measures, reinforcing their commitment to a safe operational environment. Transparency in communication is vital; it enables organizations to demonstrate accountability and responsiveness, ultimately boosting stakeholder confidence in their cybersecurity posture.
As Katerina Megas aptly states, "Effective communication is the next step towards a more secure connected ecosystem." Furthermore, the US National Institute of Standards and Technology emphasizes that "system security should not depend on the secrecy of the implementation or its components," highlighting the necessity for open dialogue. Companies that prioritize transparency tend to perform better during incidents, as recent findings suggest. For instance, the experience of Cox Automotive illustrates the risks associated with inadequate communication.
By adopting these principles, entities can significantly enhance their cybersecurity stance. Are you ready to implement a communication strategy that not only informs but also empowers your stakeholders?
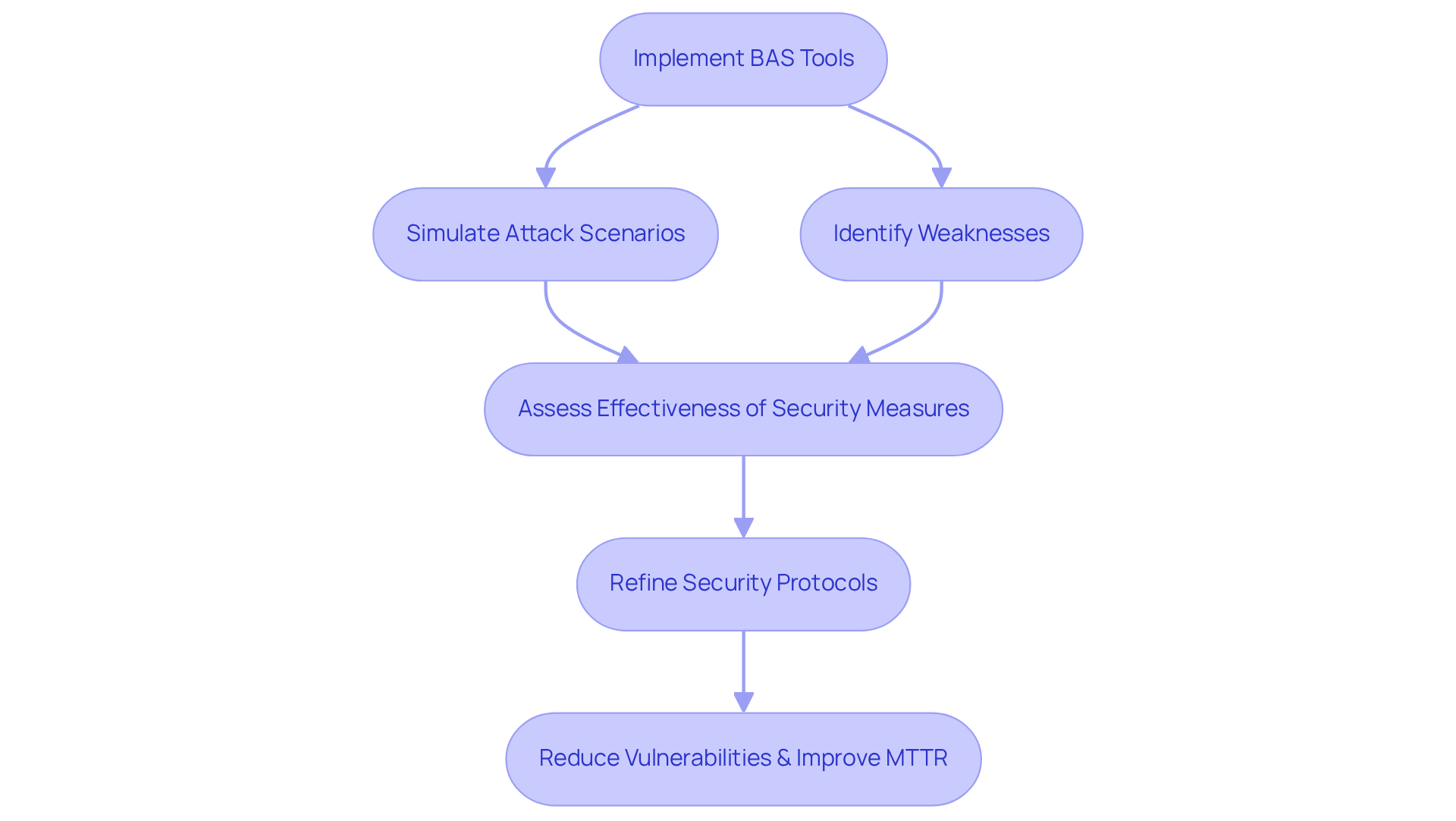
Utilize Breach and Attack Simulation Tools: Validate and Improve Security Posture
Integrating Breach and Attack Simulation (BAS) tools into your protection strategy is essential for validating and enhancing your defensive posture. These tools simulate real-world attack scenarios, enabling organizations to identify weaknesses and assess the effectiveness of their security measures. Regular simulations not only test incident response capabilities but also yield critical insights for refining security protocols based on actual performance.
Consider this: organizations that have adopted BAS tools have dramatically reduced critical vulnerabilities, decreasing from 9,500 to just 1,350. Additionally, they improved their Mean Time to Remediate (MTTR) from 45 days to an impressive 13 days. This proactive approach empowers teams to address vulnerabilities before they can be exploited, significantly bolstering defenses against potential cyber threats.
As industry experts emphasize, the IT security strategy roadmap should focus on moving from merely implementing protective measures to demonstrating their effectiveness through simulations, which is vital for building trust with stakeholders and ensuring resilience against evolving threats. Furthermore, BAS tools play a crucial role in regulatory compliance by aligning results with frameworks like NIST and ISO 27001, showcasing readiness and meeting audit requirements.
The speed and intelligence of BAS tools, as highlighted by Picus Security, enable security teams to validate defenses and prioritize actions that mitigate real-world risks. Are you ready to elevate your security strategy? Embrace BAS tools to not only protect your organization but also to instill confidence in your stakeholders.
Conclusion
Building a comprehensive IT security strategy roadmap is essential for organizations aiming to navigate the complexities of cybersecurity effectively. This roadmap not only enhances compliance with regulations like CMMC but also fortifies the organization against evolving cyber threats. By integrating structured guidance and actionable insights, entities can develop a robust framework that aligns IT security with business objectives, fostering resilience and operational continuity.
Key steps include:
- Assessing current security postures
- Defining clear security objectives
- Prioritizing risk management initiatives
- Implementing layered defense strategies
Governance, continuous training, and transparent communication with stakeholders are crucial for enhancing the overall security posture. Moreover, the integration of advanced tools such as Breach and Attack Simulation (BAS) empowers organizations to validate their defenses and adapt to emerging threats effectively.
Ultimately, organizations must recognize that a proactive and well-structured IT security strategy is not merely a compliance requirement but a critical component of sustainable growth and trust. By committing to continuous improvement and fostering a culture of security awareness, businesses can protect their assets and empower their workforce to be vigilant against potential threats. Taking these steps ensures a fortified defense against cyber risks, positioning the organization for success in an increasingly digital landscape.
Frequently Asked Questions
What is the purpose of the CMMC Info Hub?
The CMMC Info Hub serves as a knowledge base to assist entities in achieving compliance with the Cybersecurity Maturity Model Certification (CMMC), providing structured guidance, detailed roadmaps, and practical strategies for DoD cybersecurity requirements.
Why is CMMC compliance important for defense contractors?
CMMC compliance is mandatory for all contractors, especially small and medium-sized businesses, due to increasing cyber threats. It ensures that contractors meet stringent standards necessary for securing defense contracts and protecting sensitive information.
What features does the CMMC Info Hub offer to defense contractors?
The CMMC Info Hub offers comprehensive articles, guides, and actionable strategies that support the creation of an IT security strategy roadmap and facilitate successful assessments for compliance.
How has the transition from CMMC 1.0 to 2.0 affected the compliance process?
The transition from CMMC 1.0 to 2.0 has streamlined the compliance process, making it more accessible for businesses.
What is the significance of the final DFARS rule related to CMMC?
The final DFARS rule, effective November 10, 2025, integrates CMMC 2.0 into defense contracts and mandates that all contractors self-assess and submit their scores in the Supplier Performance Risk System (SPRS), highlighting the importance of robust cybersecurity practices.
What initial steps should organizations take to assess their current security posture?
Organizations should conduct a thorough evaluation of their current IT security strategy, identifying essential assets, assessing existing protective measures, and pinpointing weaknesses using tools like vulnerability assessments and risk analysis frameworks.
Why is it important to regularly evaluate and review IT security strategies?
Regular evaluations and reviews help organizations adapt to evolving threats, ensure compliance with industry standards, and enhance their overall defense posture, ultimately safeguarding assets against potential breaches.
How can organizations align their IT security objectives with business goals?
Organizations can set clear protection objectives that align with their mission, vision, and values, integrating IT protection into their business strategies to create a cohesive risk management framework that enhances resilience.
What metrics can demonstrate the value of aligning cybersecurity with business objectives?
Metrics such as reduced downtime and prevented breaches can highlight the effectiveness of protective initiatives, showcasing how they drive business success and enhance leadership visibility during reviews.
What is the overall benefit of prioritizing the alignment of cybersecurity with business goals?
Prioritizing this alignment not only fortifies organizations against threats but also positions them for sustainable growth by enabling them to adapt to challenges and seize opportunities.




