Encrypting CUI in Cloud Storage: What the Rules Require
Best practices for cloud storage encryption to safeguard sensitive information in defense contracts.

Introduction
Cloud storage encryption is crucial for data protection, particularly for defense contractors handling sensitive information. As cybersecurity threats evolve, the need for strong encryption practices becomes undeniable, especially with the compliance deadlines set by the Cybersecurity Maturity Model Certification (CMMC) approaching in 2025. Despite the clear advantages of protecting Controlled Unclassified Information (CUI), many organizations face significant hurdles, including key management and regulatory compliance.
How can defense contractors effectively tackle these challenges? By securing their data, they not only protect vital information but also enhance their credibility in a competitive landscape. Understanding the complexities of encryption and compliance is essential for success in this sector.
Understand Cloud Storage Encryption and Its Importance
Cloud storage encryption is essential for converting information into a coded format that only authorized users can access. This process is crucial for defense contractors managing sensitive material, particularly in securing Controlled Unclassified Information (CUI) and ensuring compliance with Cybersecurity Maturity Model Certification (CMMC) requirements. By implementing robust security protocols, organizations can significantly reduce the risks associated with information breaches. Even if data is intercepted, it remains unreadable without the correct decryption keys, thus safeguarding the integrity of sensitive material.
The importance of encoding extends beyond mere information protection; it also ensures regulatory compliance, especially with Department of Defense (DoD) standards. As organizations prepare for the upcoming CMMC standards-linking contract awards to compliance evaluations starting November 10, 2025-adopting data protection measures becomes a strategic imperative. Recent statistics reveal that 82% of information breaches involve data stored in the cloud, highlighting the urgent need for cloud storage encryption as an effective protection strategy.
Case studies indicate that over 21% of organizations have implemented cloud storage encryption for more than 60% of their classified data, effectively addressing both security and compliance challenges. Experts assert that data protection not only bolsters security but also enhances an organization's credibility and trustworthiness within the defense sector. As cyber threats continue to evolve, the proactive implementation of cloud storage encryption is not just a best practice; it is a fundamental element of a robust cybersecurity strategy.
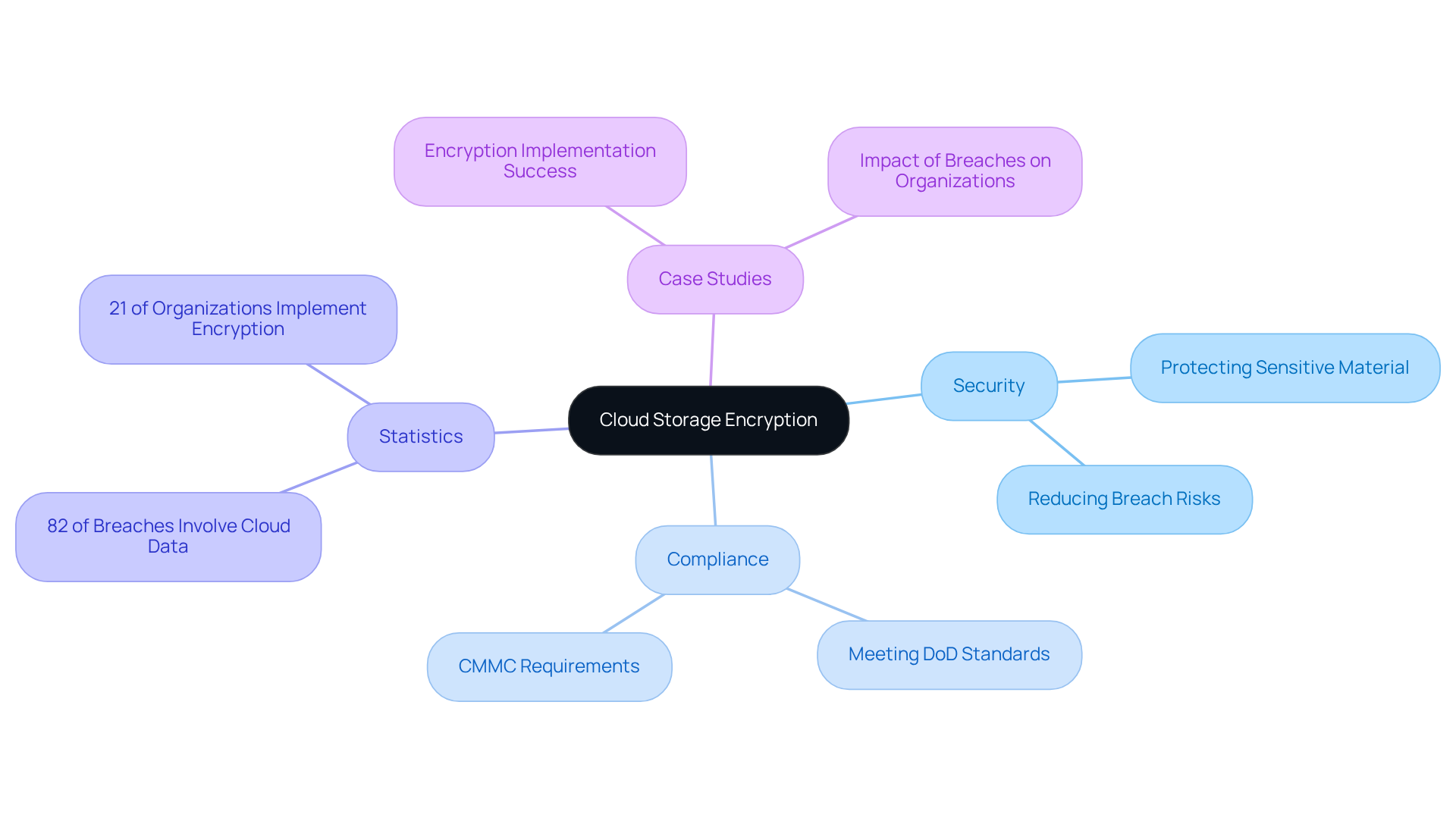
Implement Effective Encryption Strategies for Compliance
To achieve compliance with CMMC and protect sensitive information, organizations must adopt strong encoding strategies. Implementing robust coding methods, particularly AES-256, is crucial due to its widespread recognition for security. This symmetric encoding technique offers 2^256 potential combinations, rendering it resilient to brute-force assaults and a favored option for safeguarding information in regulated sectors.
Organizations should utilize both data-at-rest and data-in-transit protection to secure information throughout its lifecycle. This involves:
- Cloud storage encryption for information stored in cloud environments, such as AWS and Azure, which utilize AES-256 by default.
- The encryption of information transmitted over networks.
End-to-end safeguarding is also recommended, ensuring that data is encoded on the sender's side and only decoded by the intended recipient, thereby enhancing confidentiality.
Frequent updates to data protection protocols and performing comprehensive audits are essential for ensuring compliance and adjusting to changing security threats. For instance, organizations that fail to implement AES-256 risk significant fines and loss of trust. In the healthcare sector, HIPAA violations can cost up to $1.5 million annually. Additionally, common pitfalls include:
- Neglecting to update encryption protocols
- Failing to conduct regular audits, which can lead to vulnerabilities.
By following these strategies, as outlined in 'The Ultimate Guide to Achieving CMMC Compliance,' organizations can significantly bolster their data protection measures. This ensures they meet CMMC requirements and maintain a competitive edge in the defense contracting landscape. Practical strategies and peer insights, as emphasized in the CMMC Info Hub, act as a comprehensive resource for attaining cybersecurity maturity model certification.
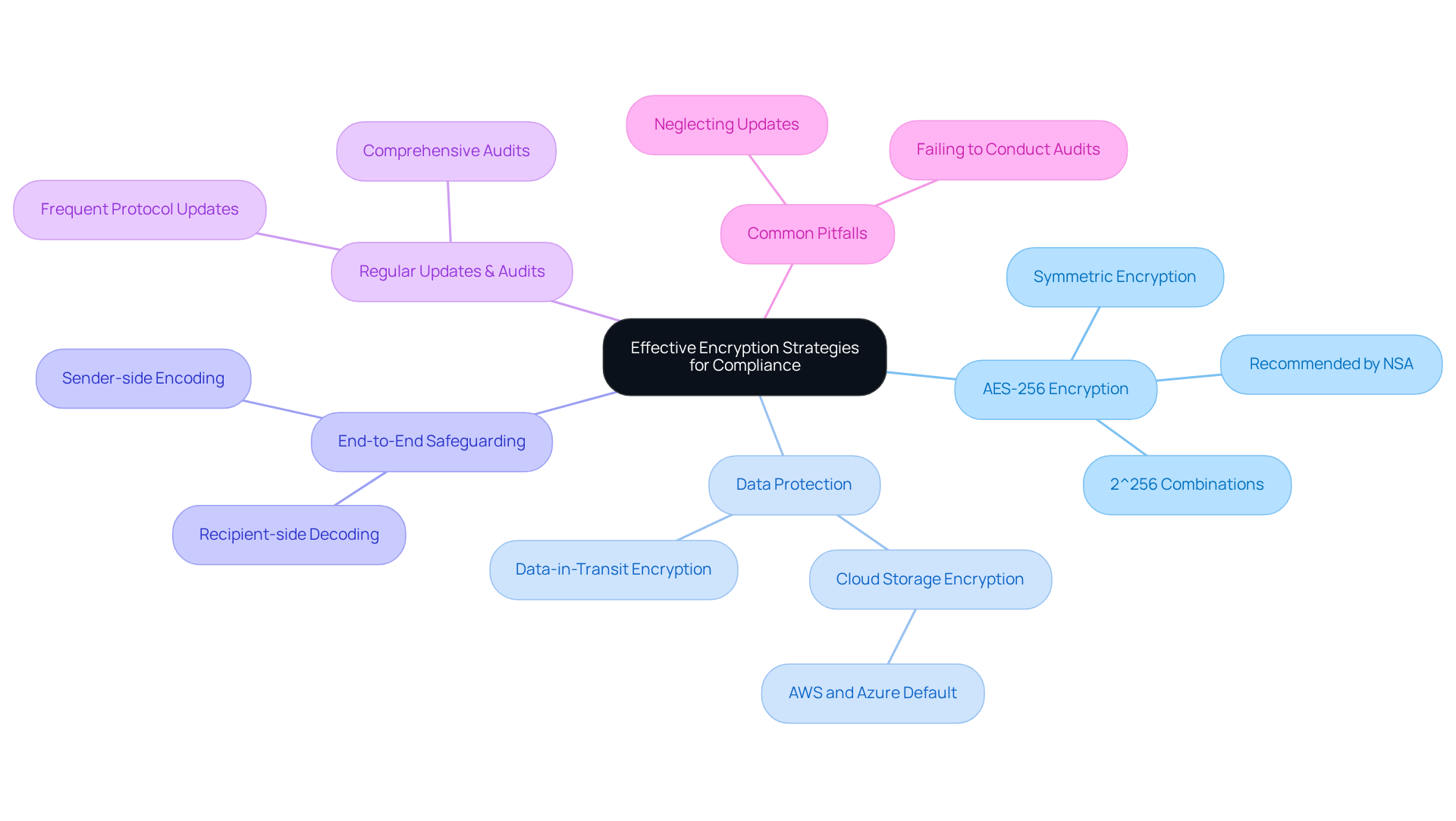
Navigate Challenges and Risks in Cloud Storage Encryption
Organizations face numerous challenges when implementing cloud storage encryption measures, such as key management, performance issues, and compliance with evolving regulations. One significant risk is the potential loss of encryption keys, which can render sensitive information inaccessible. To mitigate this risk, organizations must adopt robust key management practices, including the use of hardware security modules (HSMs) and the implementation of key rotation policies. Did you know that 88% of cloud breaches are attributed to human error? This statistic underscores the critical need for meticulous key management to prevent breaches.
Performance can also suffer due to cloud storage encryption processes, leading to delays in data access. To counter this, organizations should enhance their data protection strategies and consider utilizing dedicated security services, including cloud storage encryption, that minimize performance overhead. Furthermore, organizations that invest in effective key management strategies have significantly reduced the frequency of breaches. The average cost of a breach stands at USD 4.35 million, with the typical expense in a hybrid cloud environment reaching $3.61 million.
Staying informed about regulatory changes is vital for ensuring that data protection practices meet legal requirements. With 91% of organizations prioritizing cloud security posture management, proactive key management not only strengthens security but also fosters trust within the defense sector. By addressing these challenges head-on, organizations can refine their security strategies and effectively safeguard sensitive information.
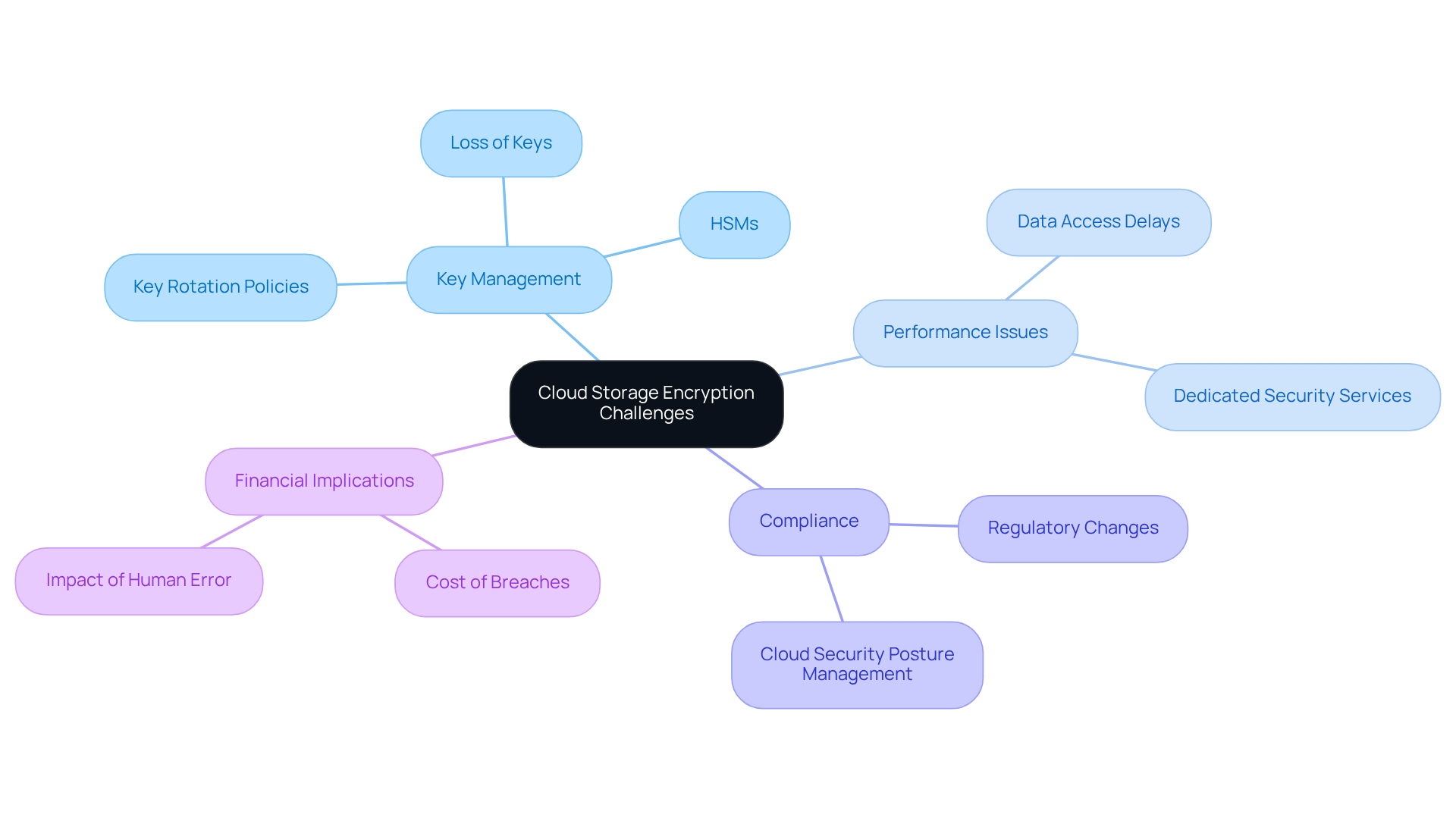
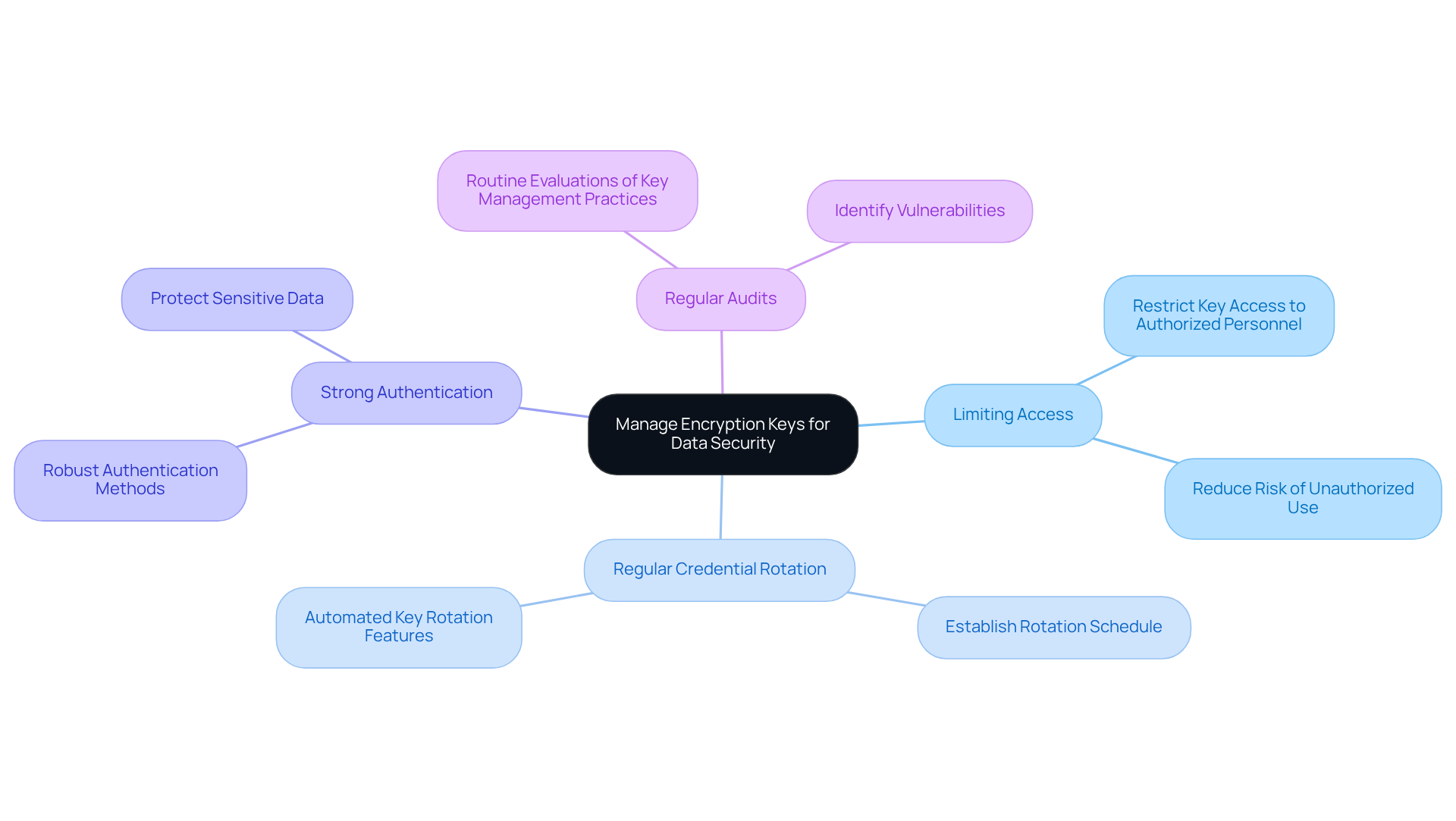
Manage Encryption Keys to Enhance Data Security
Effective key management is crucial for safeguarding encoded data, particularly in the context of cloud storage encryption for defense contracts and CMMC compliance. Organizations must implement a centralized management system (CMS) that ensures secure storage, access control, and thorough auditing of encryption materials, with an emphasis on cloud storage encryption, in line with the Ultimate Guide to Achieving CMMC Compliance. But what are the best practices to follow?
- Limiting Access: It's essential to restrict key access to authorized personnel only. This significantly reduces the risk of unauthorized use.
- Regular Credential Rotation: Establish a schedule for rotating credentials to minimize exposure and enhance security. Automated key rotation features can simplify this process, ensuring compliance with regulations like CMMC.
- Strong Authentication: Employ robust authentication methods for key retrieval. This reinforces security measures and protects sensitive data.
- Regular Audits: Conduct routine evaluations of key management practices to identify vulnerabilities and ensure secure management of access codes.
Utilizing cloud storage encryption through Customer-Managed Encryption Control (CMEK) allows organizations to maintain control over coded data, which is vital for meeting compliance requirements.
By prioritizing these practices, organizations can significantly strengthen their data security posture. For instance, early adopters of centralized key management systems have reported streamlined regulatory processes and reduced manual efforts in managing encryption keys. This proactive approach not only enhances security but also aligns with the stringent requirements of defense contracting, fostering greater trust among stakeholders.
As cybersecurity expert James Scott aptly noted, "There’s no silver bullet solution with cybersecurity; a layered defense is the only viable defense." By implementing a CKMS and adhering to best practices, organizations can build a resilient security framework that effectively protects sensitive information, particularly through the use of cloud storage encryption, while navigating the complexities of CMMC compliance.
Conclusion
Cloud storage encryption is crucial for protecting sensitive information in defense contracts, especially as organizations face the challenges of compliance with evolving standards like the Cybersecurity Maturity Model Certification (CMMC). By integrating robust encryption methods, organizations not only safeguard Controlled Unclassified Information (CUI) but also enhance their credibility and trustworthiness in a sector under increasing scrutiny.
What are the key practices for implementing effective encryption strategies? First, adopting AES-256 for data protection is essential. Additionally, diligent management of encryption keys is necessary to prevent unauthorized access. Organizations must also address common challenges, such as human error and performance issues. By taking a proactive approach to encryption, organizations can mitigate risks, bolster security, and ensure compliance with regulatory requirements, ultimately reducing the potential for costly breaches.
The importance of cloud storage encryption cannot be overstated. As the cybersecurity landscape evolves, organizations must prioritize comprehensive encryption strategies and effective key management practices. This commitment not only protects sensitive data but also positions organizations favorably in the competitive defense contracting arena. By meeting regulatory expectations, they maintain the trust of stakeholders. Embracing these best practices will pave the way for a more secure and compliant future in cloud storage management.
Frequently Asked Questions
What is cloud storage encryption?
Cloud storage encryption is the process of converting information into a coded format that can only be accessed by authorized users, ensuring the protection of sensitive data.
Why is cloud storage encryption important for defense contractors?
It is crucial for defense contractors to secure Controlled Unclassified Information (CUI) and ensure compliance with Cybersecurity Maturity Model Certification (CMMC) requirements, thereby reducing risks associated with information breaches.
How does cloud storage encryption help with regulatory compliance?
It ensures adherence to Department of Defense (DoD) standards and prepares organizations for upcoming CMMC standards that link contract awards to compliance evaluations starting November 10, 2025.
What are the statistics regarding information breaches in cloud storage?
Recent statistics indicate that 82% of information breaches involve data stored in the cloud, emphasizing the need for effective cloud storage encryption.
How many organizations have implemented cloud storage encryption for classified data?
Case studies show that over 21% of organizations have implemented cloud storage encryption for more than 60% of their classified data, addressing both security and compliance challenges.
What are the benefits of implementing cloud storage encryption?
It bolsters security, enhances an organization's credibility and trustworthiness within the defense sector, and is essential for a robust cybersecurity strategy in the face of evolving cyber threats.