Best Practices for End to End Encryption in File Sharing
Implement best practices for end to end encryption file sharing to enhance security and compliance.

Introduction
End-to-end encryption (E2EE) stands as a cornerstone of secure file sharing, delivering a robust layer of protection that ensures data confidentiality from sender to recipient. In an era where cybersecurity compliance is paramount, understanding and implementing effective practices for E2EE is not just beneficial; it’s essential. Yet, many organizations face significant challenges when integrating this technology into their existing frameworks.
How can businesses effectively harness the power of end-to-end encryption while navigating the obstacles that accompany its implementation? This question is critical as organizations strive to protect sensitive information and maintain compliance in a complex digital landscape.
Understand End-to-End Encryption: Definition and Importance in File Sharing
End-to-end encryption stands as a formidable security protocol, safeguarding information right from the sender's device. This ensures that only the intended recipient can access the data, effectively preventing unauthorized access during transmission. Why is this crucial? Because secure file sharing relies on end-to-end encryption file sharing as a robust measure.
In the context of compliance with the Cybersecurity Maturity Model Certification (CMMC), end-to-end encryption is indispensable for protecting sensitive defense-related information from potential breaches. By adopting this method, organizations can significantly mitigate the risk of information leaks. In fact, a staggering 87% of information protection officers identify insider threats as their primary concern regarding data leakage. Moreover, 97% of data protection officers utilize end-to-end encryption file sharing to safeguard their data, highlighting its critical role in data protection.
Implementing end-to-end encryption file sharing not only aligns with compliance requirements for safeguarding Controlled Unclassified Information (CUI) but also reinforces the cybersecurity posture of organizations. Various case studies, including one titled 'Importance of End-to-End Encryption in Compliance,' illustrate this point effectively. Organizations that embrace this encryption method not only bolster their cybersecurity defenses but also ensure adherence to regulatory standards such as DFARS and NIST 800-171.
As the cybersecurity landscape evolves, the importance of end-to-end encryption in maintaining information integrity and confidentiality cannot be overstated. With 74% of information protection officers citing ransomware as their greatest concern, E2EE emerges as a vital defense mechanism against these emerging threats. Are you ready to enhance your organization's security measures?
Implement End-to-End Encryption: How It Works in Secure File Sharing
Implementing end to end encryption file sharing is crucial for safeguarding sensitive information. Here are the key steps to ensure effective implementation:
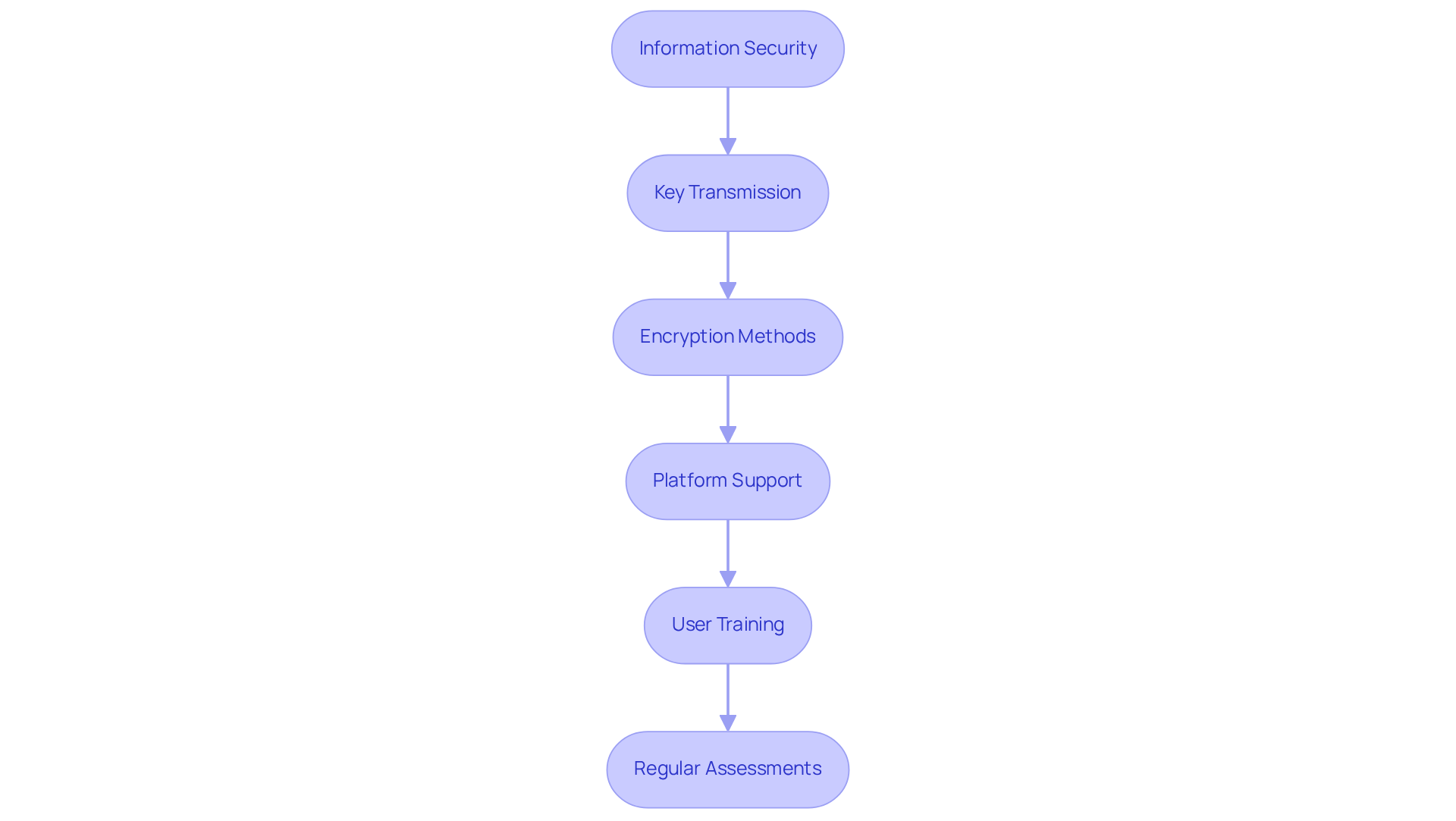
- Information Security: Initially, information is encoded on the sender's device using a distinctive coding key. This step is vital for protecting data from unauthorized access.
- Key Transmission: The coding key is then securely sent to the recipient, who uses it to decrypt the information on their device. This secure transmission is essential for maintaining confidentiality.
- Encryption Methods: Common algorithms utilized include AES-256 for data encoding and RSA for key exchange. These methods are industry standards that enhance security.
- Platform Support: Organizations must ensure that their file-sharing platforms support end to end encryption file sharing. This compatibility is necessary for seamless integration and protection.
- User Training: All users should be trained on how to utilize these features effectively. Proper training empowers users to leverage encryption fully.
- Regular Assessments: Routine evaluations of data protection practices can assist in upholding compliance with CMMC standards. Regular assessments help identify vulnerabilities and ensure ongoing security.
By mastering these technical implementation strategies outlined in 'The Ultimate Guide to Achieving CMMC Compliance,' defense contractors can significantly enhance their security posture. This proactive approach not only meets the requirements necessary for securing defense contracts but also fosters trust and reliability in their operations.
Adopt Best Practices for E2EE in File Sharing: Strategies for Compliance and Security
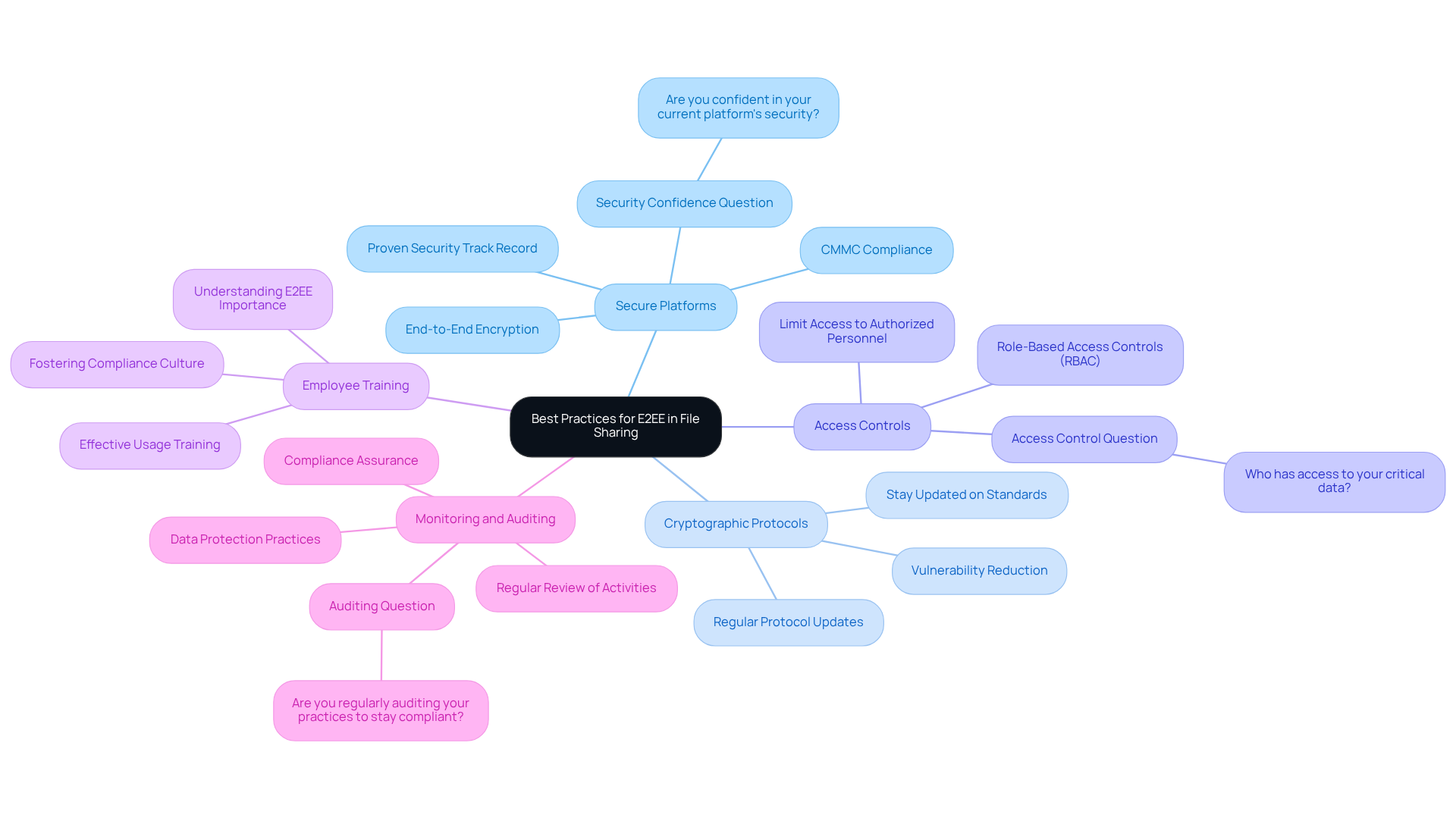
To effectively implement robust security in file sharing and achieve CMMC compliance, organizations must adopt the following best practices:
-
Choose secure platforms for file sharing that offer strong end to end encryption file sharing and have a proven security track record that meets CMMC requirements. Are you confident in your current platform's security?
-
Consistently refresh cryptographic protocols: Stay updated on the latest cryptographic standards and regularly update your protocols. This is essential for reducing vulnerabilities and ensuring compliance.
-
Implement strong access controls: Limit access to sensitive files to authorized personnel only. Utilize role-based access controls (RBAC) to enhance security and meet compliance standards. Who has access to your critical data?
-
Conduct regular training to ensure that all employees understand the importance of end to end encryption file sharing and how to use it effectively. This fosters a culture of compliance and security awareness within your organization.
-
Monitor and audit: Regularly review file sharing activities and data protection practices. This ensures compliance with CMMC and other regulatory requirements, transforming confusion into clarity in your security strategy. Are you regularly auditing your practices to stay compliant?
Navigate Challenges of End-to-End Encryption: Limitations and Considerations
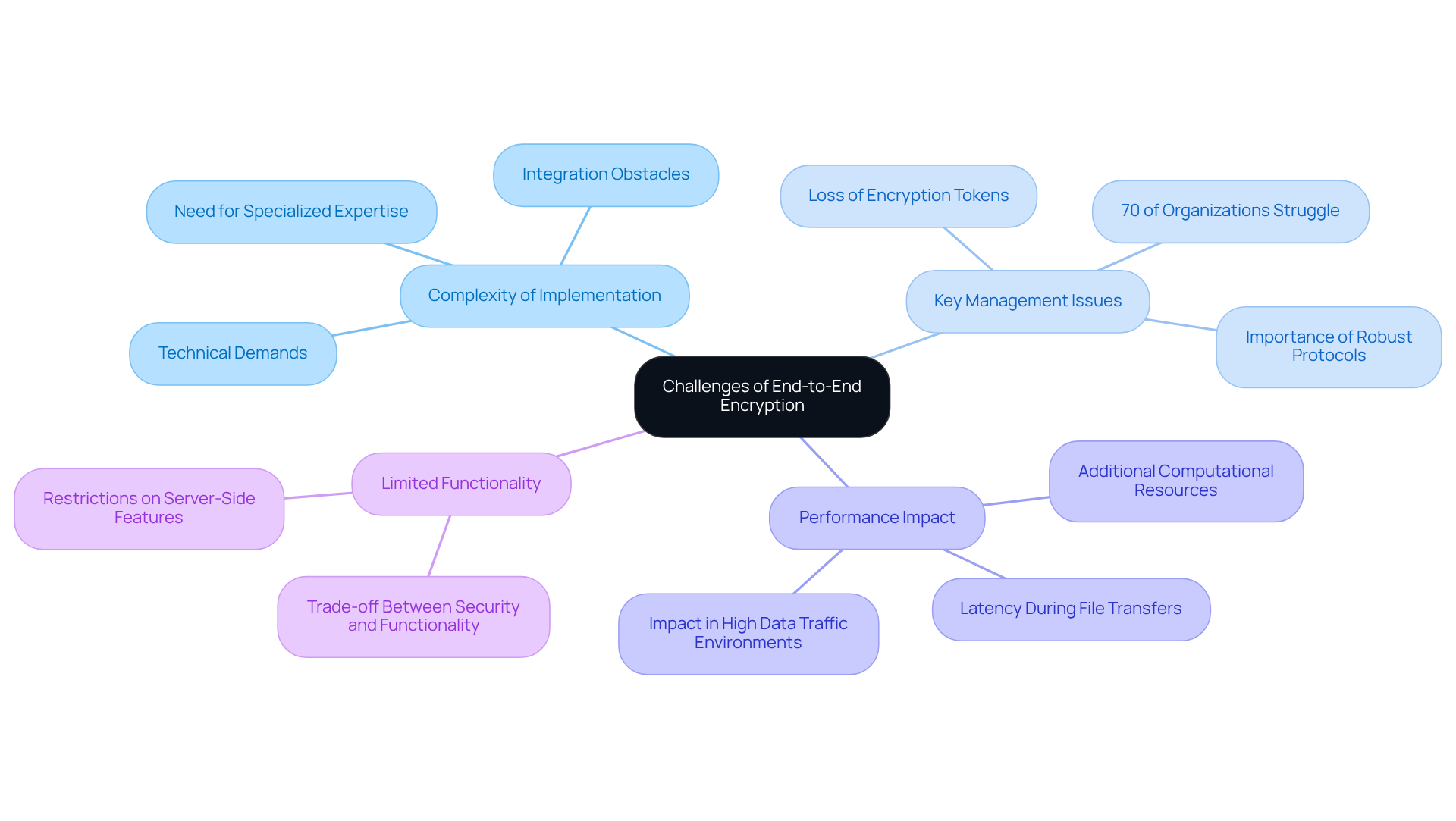
While end-to-end encryption offers significant security benefits, organizations face several challenges in its effective implementation. Understanding these challenges is crucial for making informed decisions regarding end-to-end encryption file sharing needs.
-
Complexity of Implementation: Implementing end-to-end encryption can be technically demanding, requiring specialized expertise and resources. Organizations often encounter obstacles when integrating E2EE into existing systems, complicating the deployment process.
-
Key Management Issues: Proper management of encryption tokens is essential; losing a token can lead to irreversible data loss. Research indicates that nearly 70% of organizations struggle with key management, highlighting the need for robust protocols to create, store, and rotate credentials securely. As Trevor Jackins, Senior Digital Marketing Manager at Splashtop, emphasizes, "Effective key management, including secure generation, storage, and rotation of these keys, is critical to prevent attackers from gaining access to encrypted data by stealing or duplicating keys." Without effective key management, the security of end-to-end encryption can be severely compromised.
-
Performance Impact: End-to-end encryption may introduce latency during file transfers, potentially diminishing user experience. The processes of encryption and decryption require additional computational resources, which can slow down operations, particularly in high data traffic environments.
-
Limited Functionality: Certain features, such as server-side search or content scanning, may be restricted due to the nature of end-to-end encryption. Organizations must weigh whether the trade-off in functionality is acceptable given the enhanced security that E2EE provides.
Organizations should carefully evaluate these challenges against the security advantages of end-to-end encryption file sharing. By addressing key management issues and understanding the implications of E2EE, businesses can better safeguard sensitive information while maintaining operational efficiency.
Conclusion
End-to-end encryption (E2EE) stands as a fundamental pillar for secure file sharing, ensuring that sensitive information is shielded from unauthorized access as it travels from sender to recipient. This critical security measure not only protects data integrity but also plays a vital role in meeting industry compliance standards, making it indispensable for organizations that manage sensitive information.
Understanding and effectively implementing E2EE is paramount. Key strategies include:
- Selecting secure platforms
- Refreshing cryptographic protocols
- Enforcing strong access controls
- Providing user training
- Conducting regular audits
These strategies are essential, yet organizations may encounter challenges such as implementation complexity, key management issues, performance impacts, and potential functionality limitations. Recognizing and navigating these challenges is crucial for maintaining robust security while optimizing operational efficiency.
Ultimately, adopting best practices for end-to-end encryption in file sharing transcends mere technical necessity; it represents a proactive commitment to fostering a culture of security and compliance within organizations. By prioritizing E2EE, businesses can significantly bolster their cybersecurity posture, safeguard sensitive data, and cultivate trust with clients and stakeholders. Embracing these practices is essential for anyone serious about protecting their information in an increasingly complex digital landscape.
Frequently Asked Questions
What is end-to-end encryption (E2EE)?
End-to-end encryption is a security protocol that protects information from the sender's device to the intended recipient, ensuring that only the recipient can access the data and preventing unauthorized access during transmission.
Why is end-to-end encryption important for file sharing?
It is crucial for secure file sharing as it safeguards sensitive information during transmission, significantly mitigating the risk of unauthorized access and data breaches.
How does end-to-end encryption relate to compliance with the Cybersecurity Maturity Model Certification (CMMC)?
End-to-end encryption is essential for protecting sensitive defense-related information, helping organizations comply with CMMC requirements and reducing the risk of information leaks.
What percentage of information protection officers are concerned about insider threats?
A staggering 87% of information protection officers identify insider threats as their primary concern regarding data leakage.
How prevalent is the use of end-to-end encryption among data protection officers?
97% of data protection officers utilize end-to-end encryption file sharing to safeguard their data, indicating its critical role in data protection.
What benefits does implementing end-to-end encryption provide to organizations?
It aligns with compliance requirements for safeguarding Controlled Unclassified Information (CUI), enhances cybersecurity posture, and helps organizations adhere to regulatory standards such as DFARS and NIST 800-171.
What emerging threats does end-to-end encryption help defend against?
End-to-end encryption is a vital defense mechanism against emerging threats such as ransomware, with 74% of information protection officers citing it as their greatest concern.
Are there case studies that support the importance of end-to-end encryption?
Yes, various case studies, including one titled 'Importance of End-to-End Encryption in Compliance,' illustrate how organizations benefit from adopting end-to-end encryption for enhancing cybersecurity and compliance.