Best Practices for Network Configuration for CUI Compliance
Ensure compliance and protect sensitive data with effective network configuration for CUI.

Introduction
The increasing reliance on digital information underscores the critical importance of safeguarding Controlled Unclassified Information (CUI), especially within the defense sector. Organizations are confronted with an urgent need to implement effective network configurations that not only comply with stringent regulations but also protect sensitive data from rising cyber threats.
As breaches become more prevalent, the challenge lies in navigating the complexities of CUI compliance while ensuring robust security measures are firmly in place.
How can organizations effectively balance regulatory requirements with the imperative for enhanced cybersecurity to protect vital information?
Understand Controlled Unclassified Information (CUI)
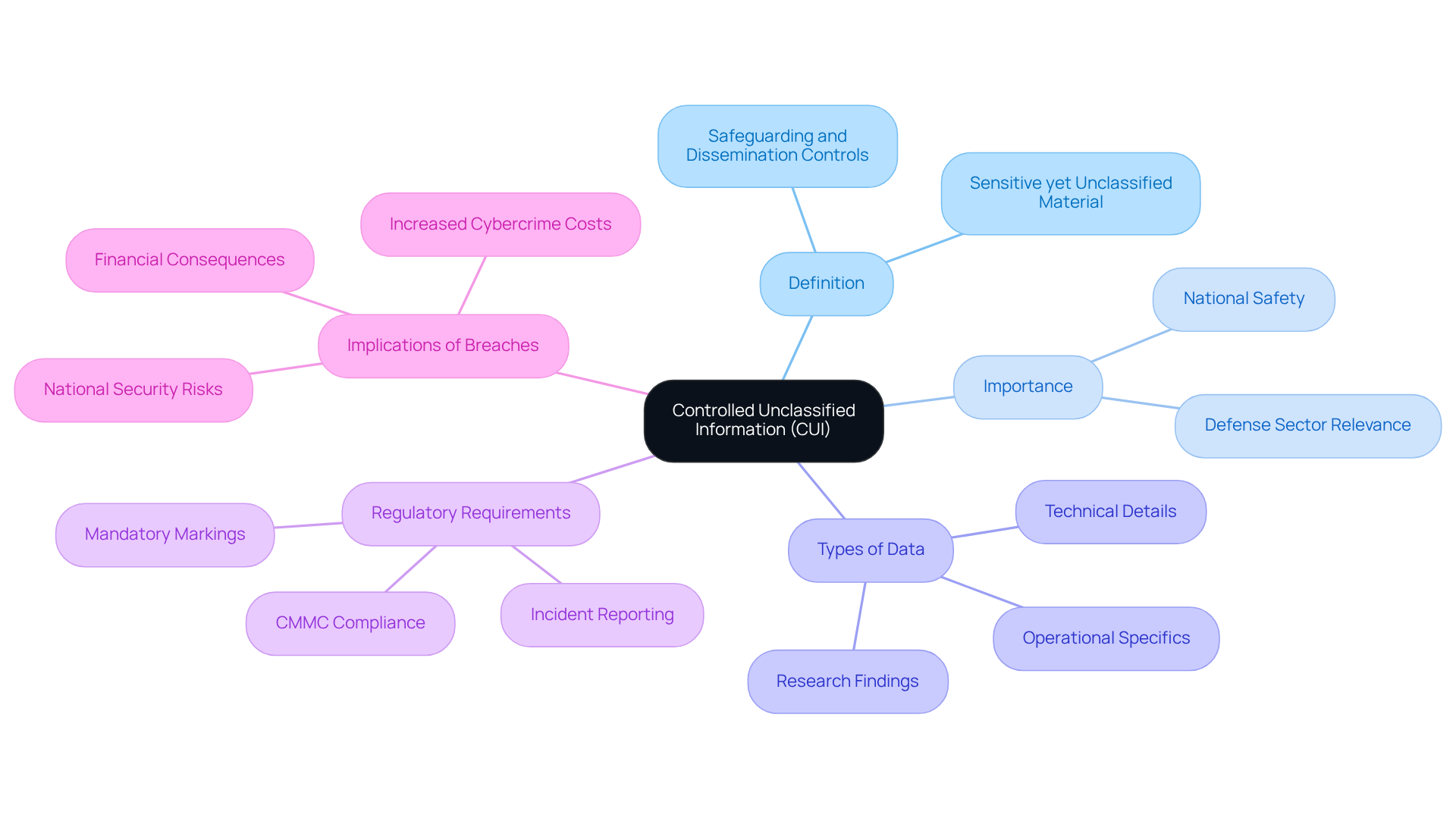
Controlled Unclassified Information (CUI) is sensitive yet unclassified material that demands safeguarding or dissemination controls as dictated by law, regulation, or government-wide policy. Why is CUI so crucial, especially in the defense sector? It encompasses a wide range of data types, including technical details, research findings, and operational specifics. If this information were to be disclosed, it could endanger national safety and the interests of the United States.
To protect CUI from unauthorized access and breaches, organizations must implement a network configuration for CUI that includes stringent security measures. This is not merely a suggestion; it aligns with the requirements set forth by the Department of Defense (DoD) and the Cybersecurity Maturity Model Certification (CMMC). As of December 2025, regulatory requirements have become more stringent, mandating that contractors report any suspected or confirmed CUI incident within eight hours of discovery. Additionally, all documents containing CUI must bear mandatory markings, with the CUI banner marking consistent across all pages.
Understanding the network configuration for CUI is the first step toward ensuring compliance and effectively safeguarding sensitive data. Recent trends reveal a troubling rise in CUI breaches, with global cybercrime costs projected to reach $10.5 trillion annually by 2025. This alarming statistic underscores the urgent need for robust cybersecurity measures. Protecting CUI is not just a regulatory obligation; it is a vital component of national defense. The integrity of this data directly impacts the defense industrial base and its ability to operate safely in an increasingly complex cyber environment.
Differentiate Between CUI Basic and CUI Specified
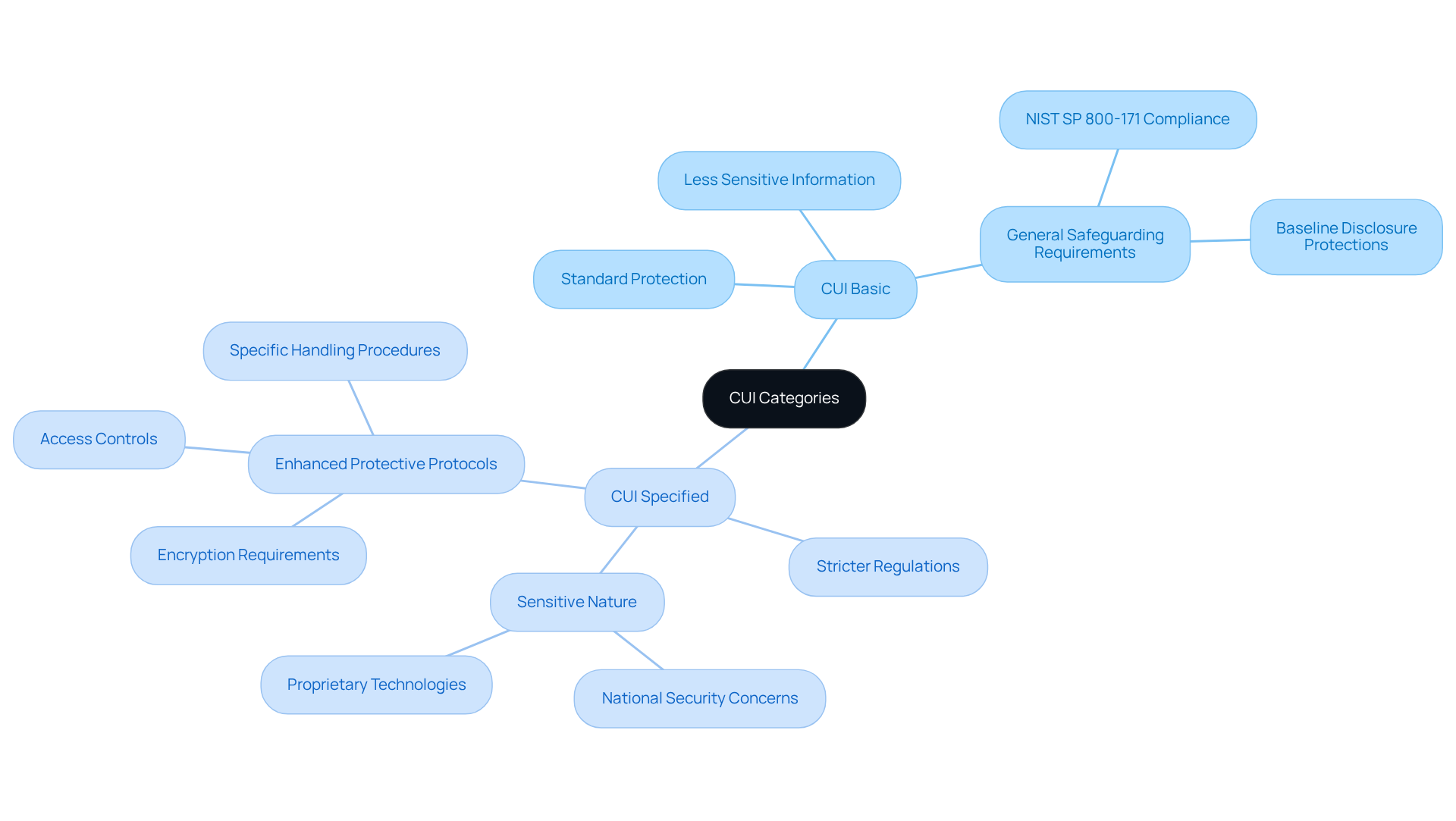
CUI is divided into two primary categories: CUI Basic and CUI Specified.
What’s the difference? CUI Basic includes data that necessitates a standard level of protection, adhering to general safeguarding requirements outlined by NIST SP 800-171. This category generally encompasses less sensitive information, such as regulated technical details, which necessitates basic protective measures without strict procedural controls.
In contrast, CUI Specified is governed by stricter regulations due to its sensitive nature, often relating to national interests or proprietary technologies. This category requires enhanced protective protocols, including encryption, access controls, and specific handling procedures dictated by laws or government policies. For instance, information categorized under the International Traffic in Arms Regulations (ITAR) falls within the CUI Specified group, necessitating strict adherence to prevent unauthorized access and maintain national safety.
Why does this matter? Understanding these differences is crucial for organizations aiming to adopt suitable security measures and uphold adherence to CMMC requirements. Non-adherence can lead to significant penalties, including fines and loss of contract opportunities.
The CMMC Info Hub offers practical strategies and peer insights, such as customized training programs and verification checklists, to assist defense contractors in navigating these complexities. Recent statistics indicate that adherence rates for CUI Basic are typically higher than for CUI Specified. This highlights the necessity for defense contractors to prioritize conformity to the more rigorous standards of CUI Specified to effectively protect sensitive information.
Identify and Categorize CUI in Network Configurations
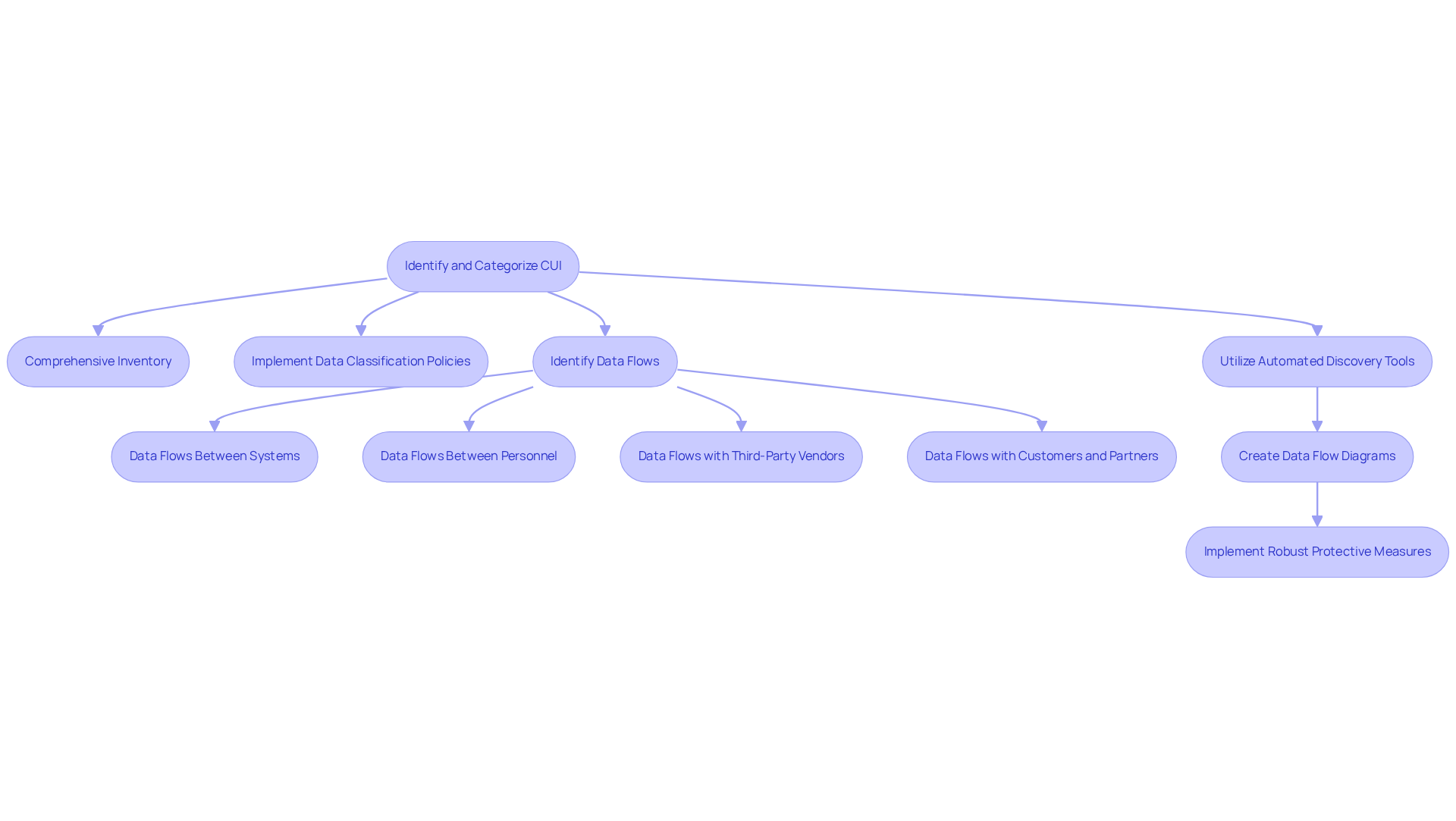
To effectively safeguard Controlled Unclassified Information (CUI), organizations must prioritize its identification and categorization within their network configuration for CUI. This begins with a comprehensive inventory of all data and systems that handle CUI, including databases, file servers, and communication channels. Implementing robust data classification policies is essential; these policies should clearly define what constitutes CUI and establish protocols for its marking and handling. For instance, organizations can implement a tiered classification system that categorizes CUI according to sensitivity and required protection levels. This enables customized protective measures that align with regulatory standards.
A critical step in this process is identifying all data flows of CUI within the environment. This includes:
- Data flows between systems (network communications)
- Data flows between personnel (email, file sharing)
- Data flows with third-party vendors (cloud services, managed services)
- Data flows with customers and partners (collaboration tools)
Creating data flow diagrams is a helpful way to visualize these flows and identify all assets in scope for the assessment. These diagrams ought to depict all systems that process, store, or transmit CUI, along with protective functions, connections between systems, external links, and boundary protection mechanisms such as firewalls and VPNs.
Utilizing automated data discovery tools significantly enhances the identification process, ensuring that all CUI is accurately accounted for and secured. Recent advancements in these tools have improved their efficiency, enabling organizations to quickly locate and classify CUI across various platforms. As highlighted by information protection specialists, effective data categorization policies not only aid in adherence but also reduce risks linked with mishandling sensitive information. By integrating these best practices into their network configuration for CUI, organizations can better protect CUI and maintain compliance with regulatory requirements.
Implement Security Controls for CUI Protection
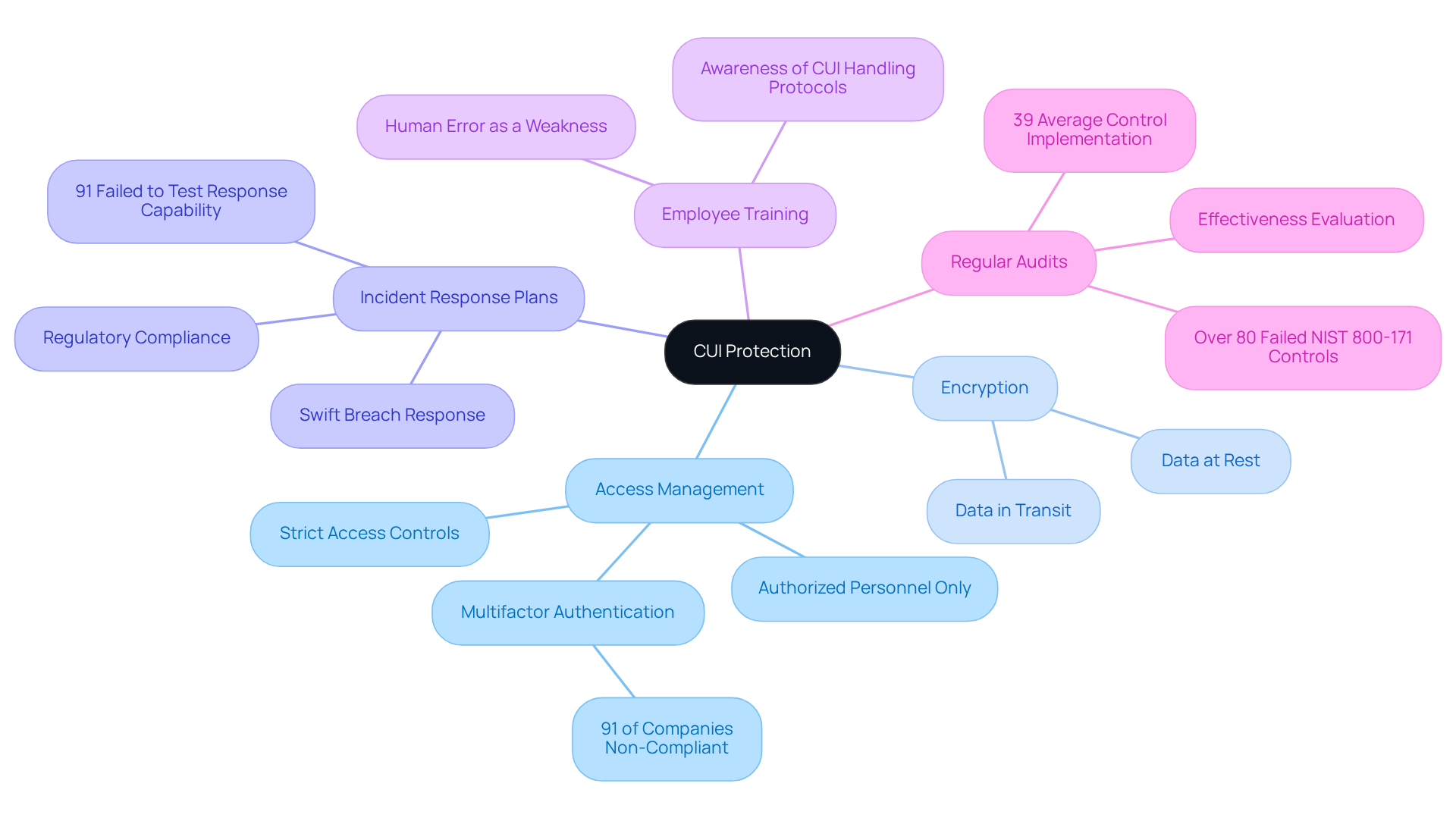
To effectively protect Controlled Unclassified Information (CUI), organizations must establish a comprehensive network configuration for CUI that includes a set of security controls. Access management is critical; only authorized personnel should have access to CUI, ensuring that sensitive information is safeguarded against unauthorized use. Current trends highlight the necessity of multifactor authentication and strict access controls. Did you know that 91% of companies have failed to implement these essential measures? This statistic underscores the urgency of addressing these vulnerabilities.
Encryption is equally vital. It secures data both at rest and in transit, preventing interception and unauthorized access. Organizations should also create strong incident response plans to swiftly tackle potential breaches. This minimizes damage and ensures adherence to regulatory requirements. Frequent training for employees is crucial to enhance awareness regarding CUI handling protocols, as human error continues to be a major weakness in cybersecurity.
Conducting regular audits and assessments is essential for evaluating the effectiveness of these controls. Reports indicate that over 80% of companies assessed failed to implement key controls from the NIST 800-171 framework. This highlights the need for ongoing vigilance and improvement. By implementing effective network configuration for CUI and adopting these best practices, organizations can significantly reduce the risk of unauthorized access to CUI and enhance their overall cybersecurity posture. This not only aligns with CMMC requirements but also ensures readiness for defense contracts.
Monitor and Assess Network Configurations for Compliance
To ensure compliance with CMMC and protect Controlled Unclassified Information (CUI), organizations must establish a robust network configuration for CUI, along with a monitoring and assessment framework. Why is this crucial? Continuous monitoring tools are vital for tracking network activity and spotting anomalies that may signal breaches. These tools not only enhance visibility into network operations but also enable timely responses to potential threats.
Regular assessments are essential for evaluating the effectiveness of security controls and identifying areas needing improvement. Organizations should remain vigilant about updates to CMMC requirements, adapting their practices to meet evolving standards. By fostering a culture of adherence and proactive monitoring, organizations can significantly bolster their network configuration for CUI and maintain eligibility for defense contracts.
Current compliance assessment rates reveal that many organizations still struggle with the complexities of CUI protection. This highlights the urgent need for robust strategies and tools to navigate this critical landscape effectively. Are you ready to take action and enhance your compliance efforts?
Conclusion
Implementing effective network configuration for Controlled Unclassified Information (CUI) is crucial for safeguarding sensitive data and ensuring compliance with stringent regulatory requirements. Organizations must recognize the critical nature of CUI, especially in sectors where national security is at stake. By understanding the nuances of CUI, including the distinctions between CUI Basic and CUI Specified, organizations can adopt appropriate security measures tailored to the sensitivity of the information they handle.
Key strategies outlined in this article include:
- Identification and categorization of CUI
- Implementation of robust security controls
- Continuous monitoring and assessment of network configurations
These practices not only align with the Cybersecurity Maturity Model Certification (CMMC) requirements but also significantly enhance an organization's overall cybersecurity posture. The alarming rise in CUI breaches underscores the urgency for organizations to prioritize these best practices to protect sensitive information and mitigate risks associated with unauthorized access.
In conclusion, the responsibility to secure Controlled Unclassified Information lies with every organization that handles it. By embracing a proactive approach to network configuration and compliance, organizations can protect national interests while fostering a culture of security awareness and resilience. The time to act is now-organizations must take decisive steps to implement these best practices and ensure they are equipped to meet the challenges of safeguarding CUI in an increasingly complex cyber landscape.
Frequently Asked Questions
What is Controlled Unclassified Information (CUI)?
Controlled Unclassified Information (CUI) is sensitive yet unclassified material that requires safeguarding or dissemination controls as mandated by law, regulation, or government-wide policy.
Why is CUI important in the defense sector?
CUI is crucial in the defense sector because it includes various types of data, such as technical details and operational specifics, which, if disclosed, could jeopardize national safety and U.S. interests.
What measures must organizations take to protect CUI?
Organizations must implement a network configuration for CUI that includes stringent security measures, in compliance with the Department of Defense (DoD) and Cybersecurity Maturity Model Certification (CMMC) requirements.
What are the new regulatory requirements for CUI as of December 2025?
As of December 2025, contractors must report any suspected or confirmed CUI incidents within eight hours of discovery, and all documents containing CUI must have mandatory markings consistent across all pages.
What are the two categories of CUI?
The two categories of CUI are CUI Basic and CUI Specified.
What is the difference between CUI Basic and CUI Specified?
CUI Basic includes less sensitive information requiring standard protection measures, while CUI Specified involves more sensitive data that mandates stricter regulations and enhanced protective protocols.
Can you provide an example of CUI Specified?
An example of CUI Specified is information governed by the International Traffic in Arms Regulations (ITAR), which requires strict adherence to prevent unauthorized access.
Why is it important for organizations to understand the differences between CUI Basic and CUI Specified?
Understanding these differences is crucial for organizations to adopt appropriate security measures and ensure compliance with CMMC requirements, as non-adherence can result in fines and loss of contract opportunities.
What resources are available to assist defense contractors with CUI compliance?
The CMMC Info Hub offers practical strategies, peer insights, customized training programs, and verification checklists to help defense contractors navigate CUI compliance complexities.




