Crafting a Cybersecurity Assessment Report: Key Best Practices
Learn best practices for crafting an effective cybersecurity assessment report.

Introduction
In today's digital landscape, crafting a robust cybersecurity assessment report is not just important - it's essential. Organizations are confronted with an ever-evolving array of threats that can compromise their security. This article explores key best practices that empower organizations to effectively define the scope of their assessments, inventory their assets, evaluate vulnerabilities, and develop actionable mitigation plans. But with so many variables at play, how can organizations ensure their assessments not only identify risks but also lead to meaningful improvements in their cybersecurity posture?
To begin with, understanding the scope of your cybersecurity assessment is crucial. This involves identifying what assets need protection and the potential vulnerabilities that could be exploited. By inventorying assets, organizations can prioritize their efforts and allocate resources effectively. Furthermore, evaluating vulnerabilities allows for a comprehensive understanding of the risks at hand.
Ultimately, the goal is to develop actionable mitigation plans that not only address current threats but also anticipate future challenges. This proactive approach is vital for enhancing an organization's cybersecurity posture. Are you ready to take the necessary steps to safeguard your organization? Let's delve deeper into these best practices and ensure your cybersecurity assessments lead to substantial improvements.
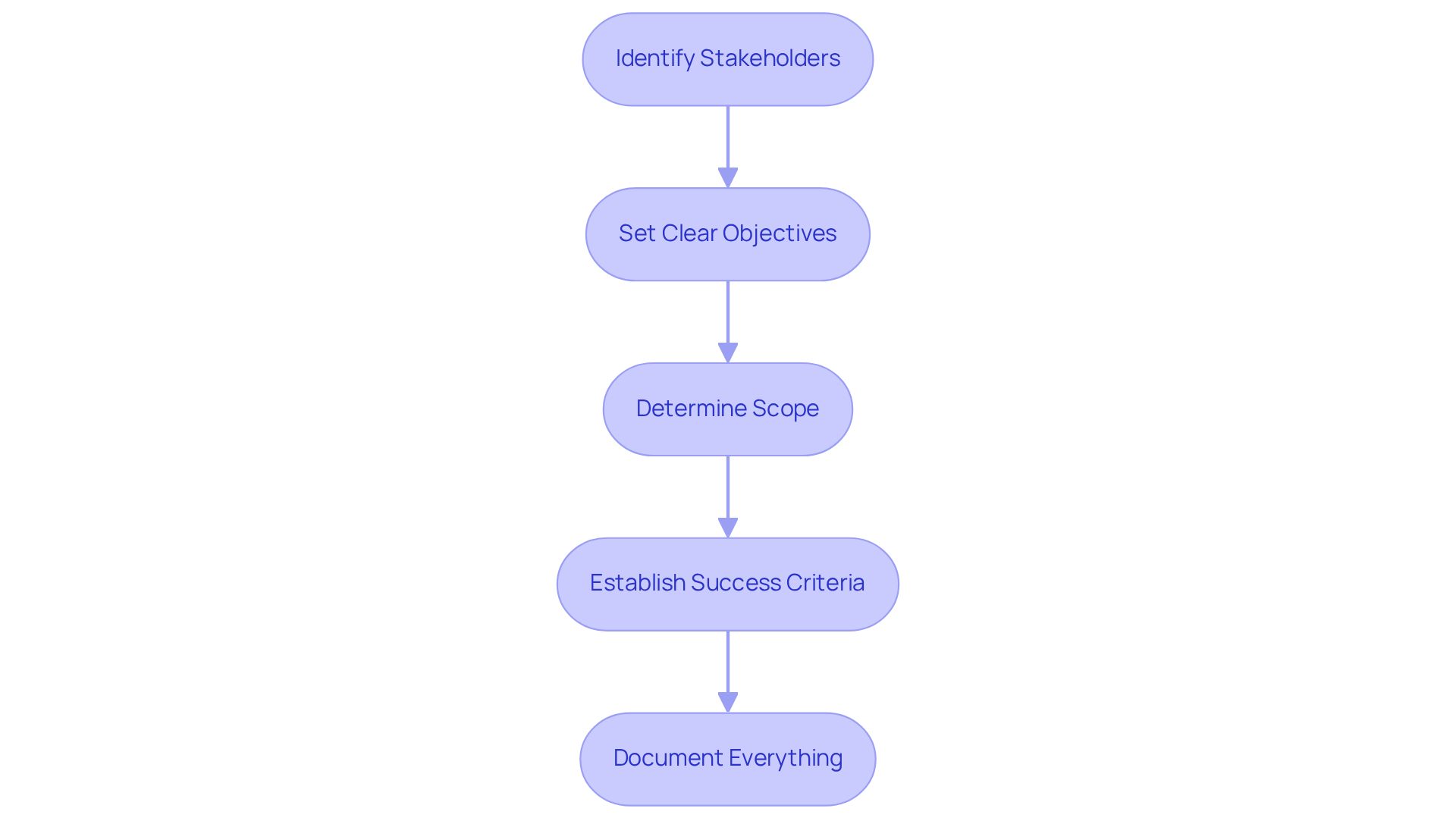
Define Scope and Objectives for the Assessment Report
To effectively define the scope and objectives of a cybersecurity assessment report, follow these essential steps:
-
Identify Stakeholders: Engage with key stakeholders, including IT personnel, management, and compliance officers. What do they anticipate from the evaluation? Gathering their input is crucial for a comprehensive understanding.
-
Set Clear Objectives: What should the evaluation achieve? Objectives may include identifying vulnerabilities, assessing compliance with regulations, or evaluating the effectiveness of current security measures. Clearly defined goals will guide the assessment process.
-
Determine Scope: Clearly outline the boundaries of the assessment. Specify which systems, procedures, and data will be included, and identify any exclusions to avoid scope creep. This clarity is vital for maintaining focus.
-
Establish Success Criteria: How will success be measured? Define specific metrics, such as the number of vulnerabilities identified or compliance levels achieved. This will provide a benchmark for evaluating the assessment's effectiveness.
-
Document Everything: Ensure that all defined objectives and scope details are documented and communicated to all stakeholders. This documentation is essential for maintaining alignment throughout the assessment process, fostering transparency and accountability.
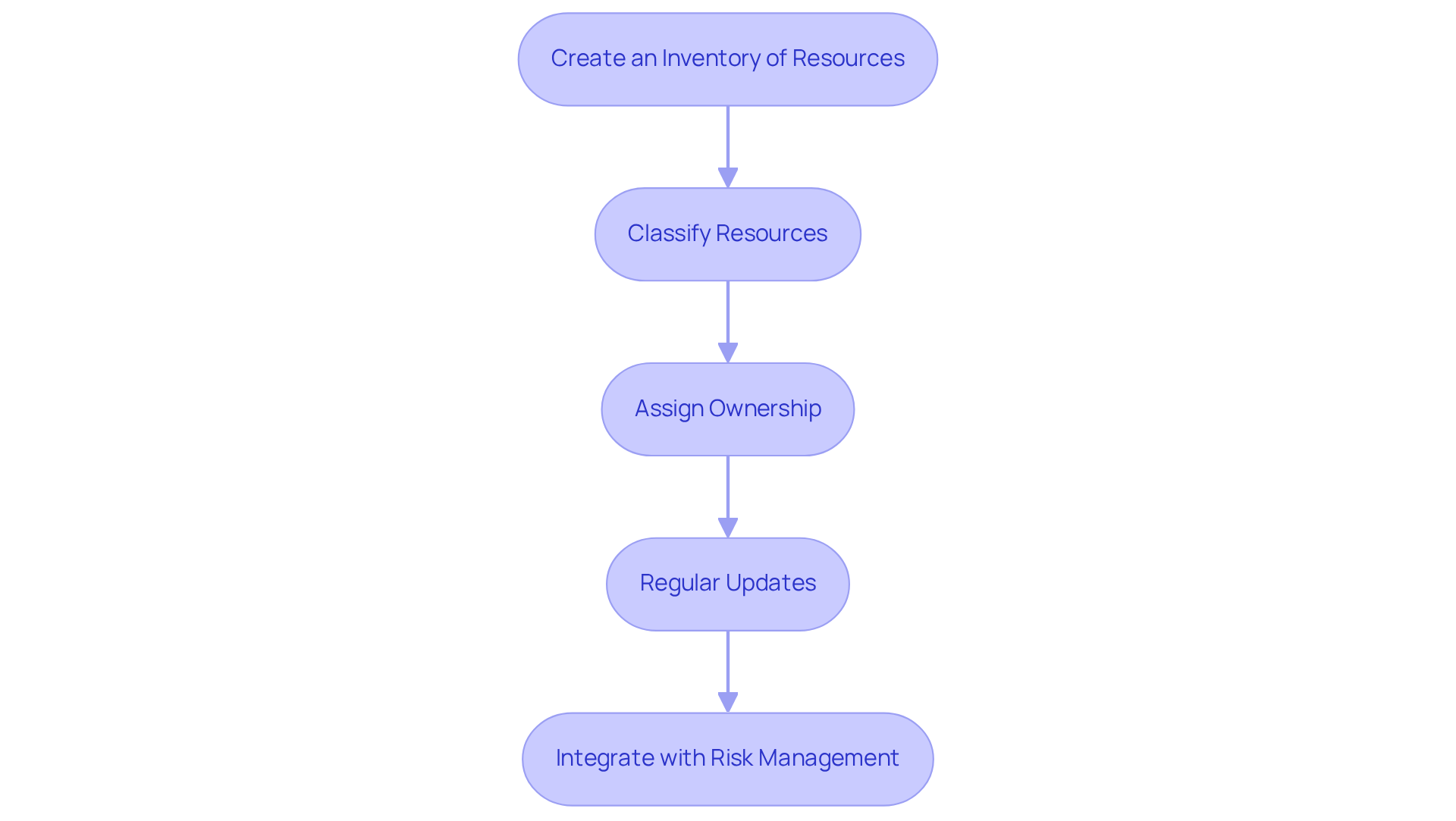
Inventory and Classify Assets for Comprehensive Coverage
To effectively inventory and classify assets, consider these essential practices:
-
Create an Inventory of Resources: Start by compiling a comprehensive list of all physical and digital resources, including hardware, software, data, and network components. Utilizing automated tools can streamline this process, making it more efficient and accurate.
-
Classify Resources: Next, categorize these resources based on their significance to your organization. This classification can be based on sensitivity-such as public, internal, or confidential-or by function, like critical infrastructure or operational systems. How does your organization currently classify its resources?
-
Assign Ownership: It's crucial to designate responsible individuals or teams for each resource. This accountability ensures that resources are managed and safeguarded effectively. Who in your organization is responsible for asset management?
-
Regular Updates: Implement a routine process for updating the inventory to reflect changes, such as new acquisitions or decommissioned systems. This practice helps maintain an accurate view of your organization's cybersecurity assessment report and overall security landscape. When was the last time your inventory was updated?
-
Integrate with Risk Management: Finally, ensure that your asset inventory is integrated into the overall risk management framework of your organization. This integration allows for better prioritization of security efforts based on asset criticality, as outlined in the cybersecurity assessment report. Are your security efforts aligned with your asset management strategy?
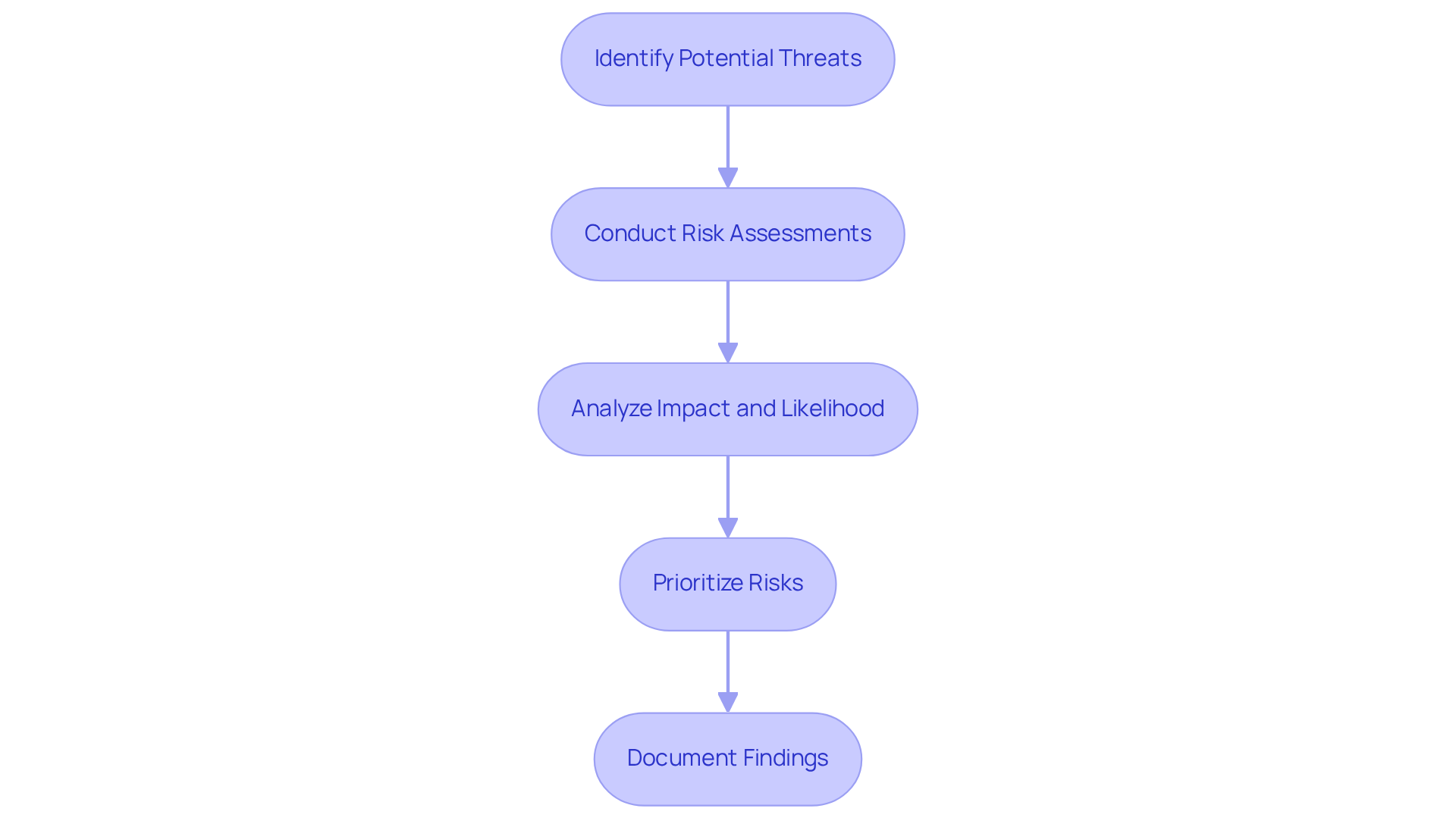
Evaluate Threats and Vulnerabilities to Identify Risks
To effectively evaluate threats and vulnerabilities, follow these essential steps:
-
Identify Potential Threats: Begin by researching and documenting potential threats that could impact your organization. Consider both external threats, such as cyberattacks and natural disasters, and internal threats, including insider threats and system failures. What vulnerabilities could you be overlooking?
-
Conduct Risk Assessments: Utilize various tools and methodologies to pinpoint weaknesses within your systems and processes. This may involve penetration testing, security scanning, and a thorough review of security configurations. Are your current measures sufficient to protect against identified threats?
-
Analyze Impact and Likelihood: For each identified threat and vulnerability, assess the potential impact on your organization and the likelihood of occurrence. You can accomplish this using qualitative or quantitative risk evaluation methods. How would your organization fare if a significant threat were to materialize?
-
Prioritize Risks: Based on your analysis, prioritize risks to focus on those that pose the greatest threat to your organization. This prioritization will guide the development of effective mitigation strategies. Which risks demand your immediate attention?
-
Document Findings: Ensure that all findings from the evaluation procedure are documented clearly in the assessment report. This documentation will provide a solid foundation for future risk management efforts. How will you leverage these findings to enhance your organization's security posture?
Develop a Mitigation Plan Based on Assessment Findings
To develop an effective mitigation plan, it’s crucial to follow these best practices:
-
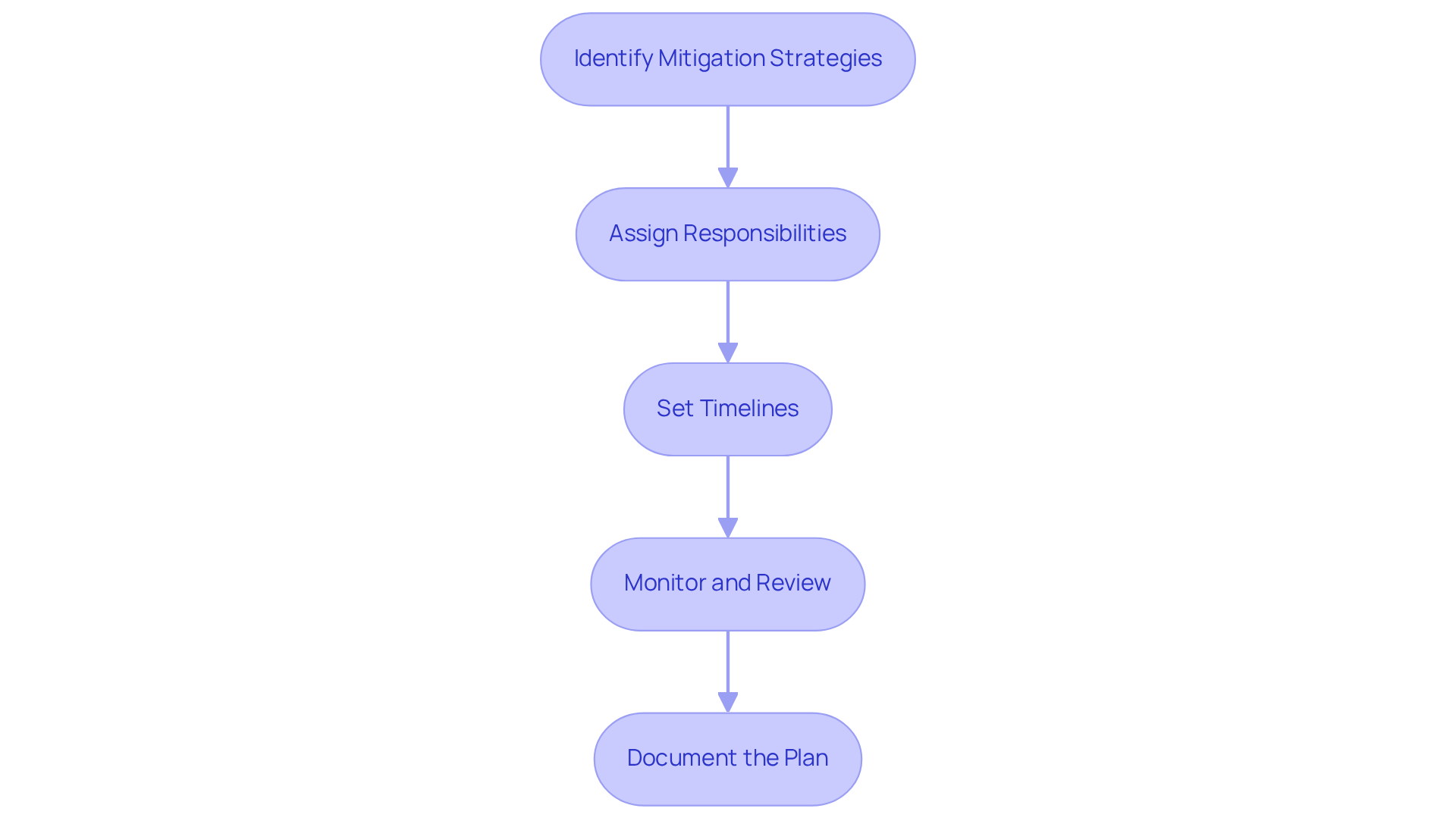
Identify Mitigation Strategies: For each prioritized risk, pinpoint appropriate mitigation strategies. This could involve implementing technical controls, enhancing policies and procedures, or providing employee training. What strategies will best address your specific risks?
-
Assign Responsibilities: Designate individuals or teams responsible for executing each mitigation strategy. Clear accountability is key to ensuring timely action. Who will take charge of these critical tasks?
-
Set Timelines: Establish realistic timelines for implementing mitigation strategies. This helps track progress and ensures prompt risk management. Don’t forget to incorporate ongoing monitoring practices like vulnerability scanning and patch management into your timeline for CMMC compliance. How will you measure your progress?
-
Monitor and Review: Implement a robust process for monitoring the effectiveness of your mitigation strategies. Regular reviews are essential to assess their impact and make necessary adjustments, including continuous incident monitoring and log reviews. Are your strategies working as intended?
-
Document the Plan: Ensure that the mitigation plan is thoroughly documented in the cybersecurity assessment report. This provides a clear roadmap for addressing identified risks and enhances the organization's cybersecurity posture. How will you ensure that everyone is on the same page?
By following these steps, you can create a comprehensive mitigation plan that not only addresses risks but also strengthens your organization’s overall cybersecurity framework.
Conclusion
Crafting a comprehensive cybersecurity assessment report is not just beneficial; it’s essential for organizations looking to bolster their security posture. By clearly defining the scope and objectives, conducting thorough asset inventories, evaluating potential threats and vulnerabilities, and developing effective mitigation strategies, organizations can establish a robust framework to safeguard their digital assets.
Key steps include:
- Engaging stakeholders to set clear objectives
- Systematically classifying assets
- Prioritizing risks based on their potential impact
Each of these practices contributes to a more informed and strategic approach to cybersecurity. Are you allocating your resources efficiently and effectively? Documenting findings and strategies not only fosters accountability but also serves as a valuable reference for future assessments.
The significance of a well-crafted cybersecurity assessment report cannot be overstated. As cyber threats continue to evolve, organizations must remain proactive in their defenses. By implementing the best practices outlined, businesses can protect their assets and build a resilient security culture that adapts to emerging challenges. Taking these steps today will lay the foundation for a safer digital environment tomorrow.
Frequently Asked Questions
What are the essential steps to define the scope and objectives of a cybersecurity assessment report?
The essential steps include identifying stakeholders, setting clear objectives, determining the scope, establishing success criteria, and documenting everything.
Who should be engaged as stakeholders in the assessment process?
Key stakeholders include IT personnel, management, and compliance officers. Their input is crucial for a comprehensive understanding of the evaluation.
What should the objectives of the cybersecurity assessment achieve?
Objectives may include identifying vulnerabilities, assessing compliance with regulations, or evaluating the effectiveness of current security measures.
Why is it important to determine the scope of the assessment?
Determining the scope is vital to outline the boundaries of the assessment, specify which systems, procedures, and data will be included, and identify exclusions to avoid scope creep.
How can success be measured in a cybersecurity assessment?
Success can be measured by defining specific metrics, such as the number of vulnerabilities identified or compliance levels achieved, which provide a benchmark for evaluating the assessment's effectiveness.
Why is documentation important in the assessment process?
Documentation is essential for maintaining alignment throughout the assessment process and fosters transparency and accountability by ensuring that all defined objectives and scope details are communicated to all stakeholders.