Create Your Cyber Incident Response Playbook in 4 Simple Steps
Learn how to create an effective cyber incident response playbook in four easy steps.

Overview
Creating a cyber incident response playbook is crucial for any organization aiming to safeguard its digital assets. Why is this important? A well-structured playbook minimizes damage during incidents, enhances communication and reaction times, and ensures compliance with industry standards. Ultimately, it prepares organizations to effectively manage cybersecurity threats.
To develop an effective playbook, follow these four essential steps:
- Understand its importance
- Identify key components
- Develop a comprehensive strategy
- Regularly test and refine the plan
Each of these steps plays a vital role in ensuring that your organization is ready to respond swiftly and efficiently to cyber incidents.
Consider this: without a robust playbook, organizations may struggle to coordinate their response efforts, leading to increased damage and prolonged recovery times. By investing time in crafting a detailed playbook, you not only protect your assets but also foster a culture of preparedness within your team.
In conclusion, the necessity of a cyber incident response playbook cannot be overstated. Regular testing and refinement of the plan are essential to adapt to the ever-evolving threat landscape. Take action now to ensure your organization is equipped to handle cybersecurity challenges effectively.
Introduction
Crafting a robust cyber incident response playbook is no longer a luxury; it’s a necessity for organizations that want to safeguard their digital assets. This strategic document minimizes potential damage during a cyber crisis and enhances communication and compliance across teams. Yet, the challenge lies in developing a playbook that is both comprehensive and adaptable to the ever-evolving threat landscape.
How can organizations ensure their response strategies are effective and up-to-date, ready to tackle the next cybersecurity incident head-on? By prioritizing the creation of a dynamic playbook, organizations can not only prepare for potential threats but also foster a culture of resilience and proactive response.
In today’s digital age, the stakes are high. A well-crafted incident response plan can mean the difference between a minor setback and a catastrophic breach. Therefore, it’s crucial for organizations to invest time and resources into developing a playbook that evolves alongside emerging threats. This commitment not only protects valuable assets but also builds trust with stakeholders and clients.
Ultimately, the goal is clear: equip your organization with the tools and strategies necessary to respond effectively to cyber incidents. By doing so, you not only enhance your security posture but also position your organization as a leader in cybersecurity preparedness.
Understand the Importance of an Incident Response Playbook
A cyber incident response playbook is an essential document that outlines the procedures and protocols for managing cybersecurity events. It serves as a strategic guide, ensuring that all team members understand their roles and responsibilities during an event. The significance of having a playbook is profound:
- Minimizes Damage: A well-structured playbook enables rapid containment and mitigation of cyber incidents, significantly reducing potential losses. Organizations that have adopted incident response strategies have shown a marked reduction in the effects of breaches, allowing them to recover more swiftly.
- Ensures Compliance: For organizations pursuing CMMC certification, having a strategy document signals a strong commitment to best practices in information security and regulatory adherence. This is particularly crucial as the percentage of enterprises setting target windows for patching critical vulnerabilities has surged to 89%, reflecting a growing emphasis on proactive cybersecurity measures. The CMMC Info Hub provides practical strategies and peer insights that can guide defense contractors in achieving compliance with confidence.
- Enhances Communication: The cyber incident response playbook fosters effective communication among team members and stakeholders, ensuring that everyone is aligned during a crisis. This clarity is essential, especially when the average duration to detect a breach is 204 days, highlighting the necessity for coordinated actions.
- Enhances Reaction Time: With a cyber incident response playbook established, teams can respond more quickly and efficiently, which is vital for reducing the consequences of events. The execution of Endpoint Detection and Response (EDR) has increased to 91%, emphasizing the trend towards quicker detection and reaction capabilities.
Understanding the significance of an event management guide is crucial for creating a robust security strategy that conforms to CMMC standards. By customizing strategies to address specific threats, such as ransomware or phishing, organizations can enhance their preparedness and resilience against cyber threats.
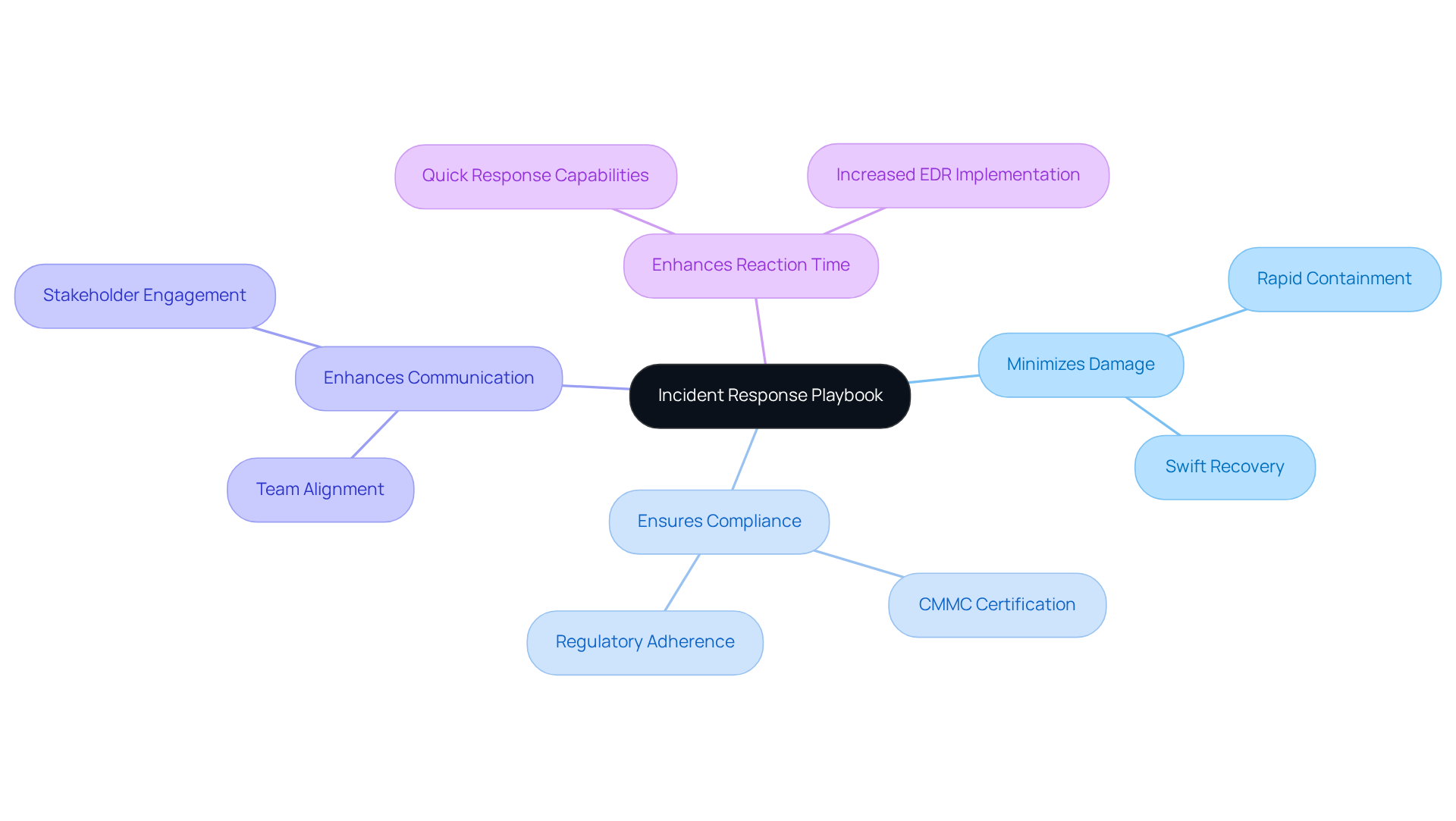
Identify Key Components of Your Playbook
Creating an effective incident response playbook is crucial for ensuring your organization is ready to tackle cybersecurity incidents efficiently. Here are the essential components:
-
Incident Identification: How do you detect and report incidents? Clearly defining these methods is vital. Utilize monitoring tools and establish user reporting mechanisms to ensure timely awareness of potential threats. Consider this: statistics show that 31% of organizations have reported experiencing a data breach. This underscores the importance of robust event identification techniques.
-
Roles and Responsibilities: Who does what during an incident? Outlining the duties of each team member involved in the event management process is essential. Studies reveal that organizations with clearly defined roles react more efficiently to events. As Allison Dunn aptly states, "Cybersecurity isn’t an IT issue—it’s a leadership issue," emphasizing the critical role of leadership in defining these responsibilities.
-
Response Procedures: What steps will you take when an incident occurs? Create comprehensive, sequential procedures tailored for different types of incidents, such as data breaches, malware infections, or denial-of-service attacks. This organized approach simplifies the reaction process and minimizes confusion during critical moments.
-
Communication Plan: How will you communicate during an incident? Establish a robust communication strategy for both internal and external stakeholders. This plan should detail how to notify affected parties and regulatory bodies, ensuring transparency and compliance with legal obligations.
-
Post-Incident Review: What did you learn from the incident? Incorporate a systematic process for reviewing and analyzing events after they occur. This evaluation is crucial for recognizing lessons learned and refining strategies for future actions. For instance, a logistics firm increased its security expenditure by 15% after a near miss with ransomware, illustrating the importance of learning from past events.
By integrating these elements, your incident management playbook will be comprehensive and tailored to meet your organization's unique security needs, ultimately strengthening your overall security posture.
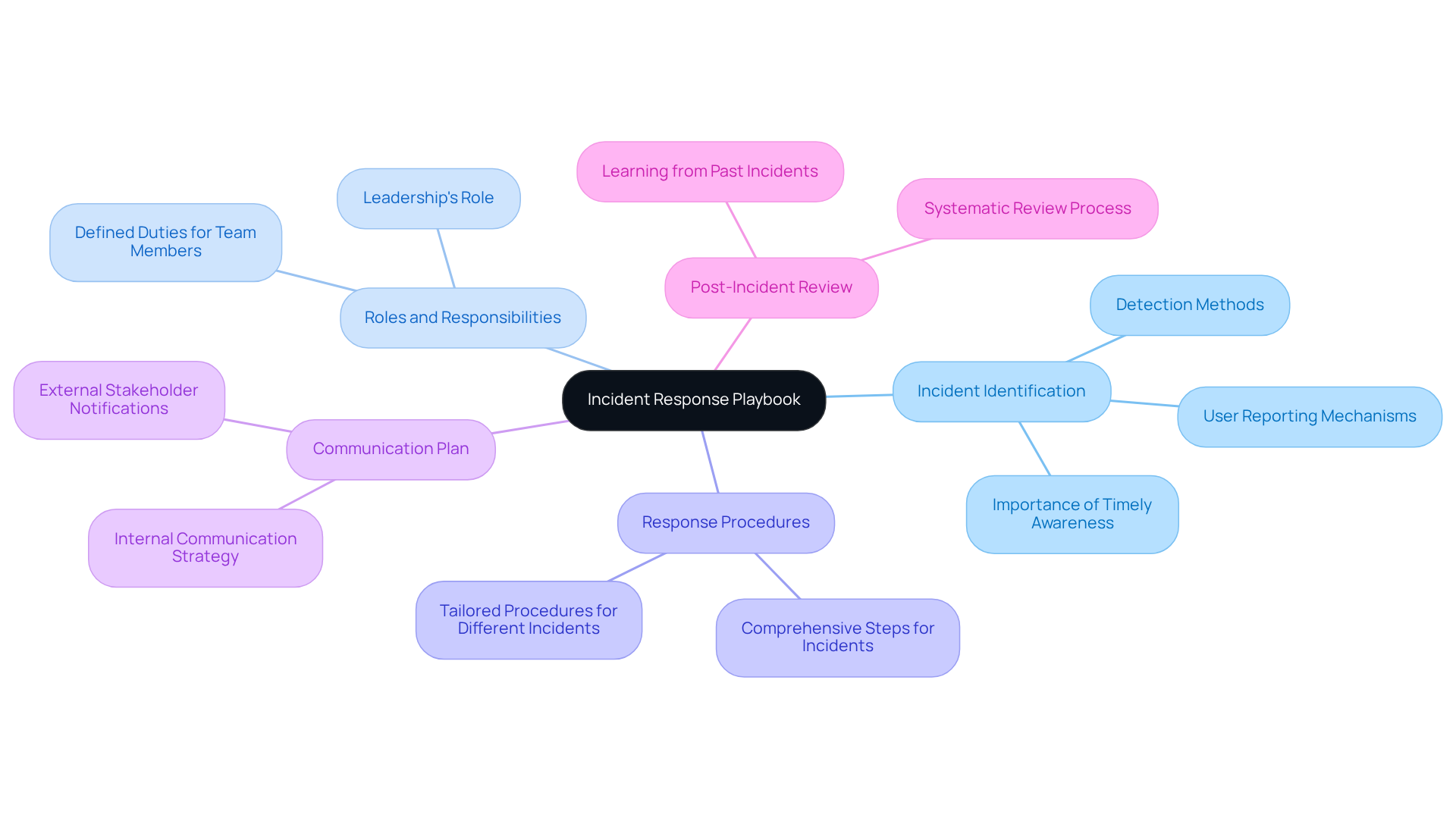
Develop Your Incident Response Strategy
Developing your cyber incident response playbook is crucial for safeguarding your organization against cybersecurity threats. Here are several key steps to consider:
-
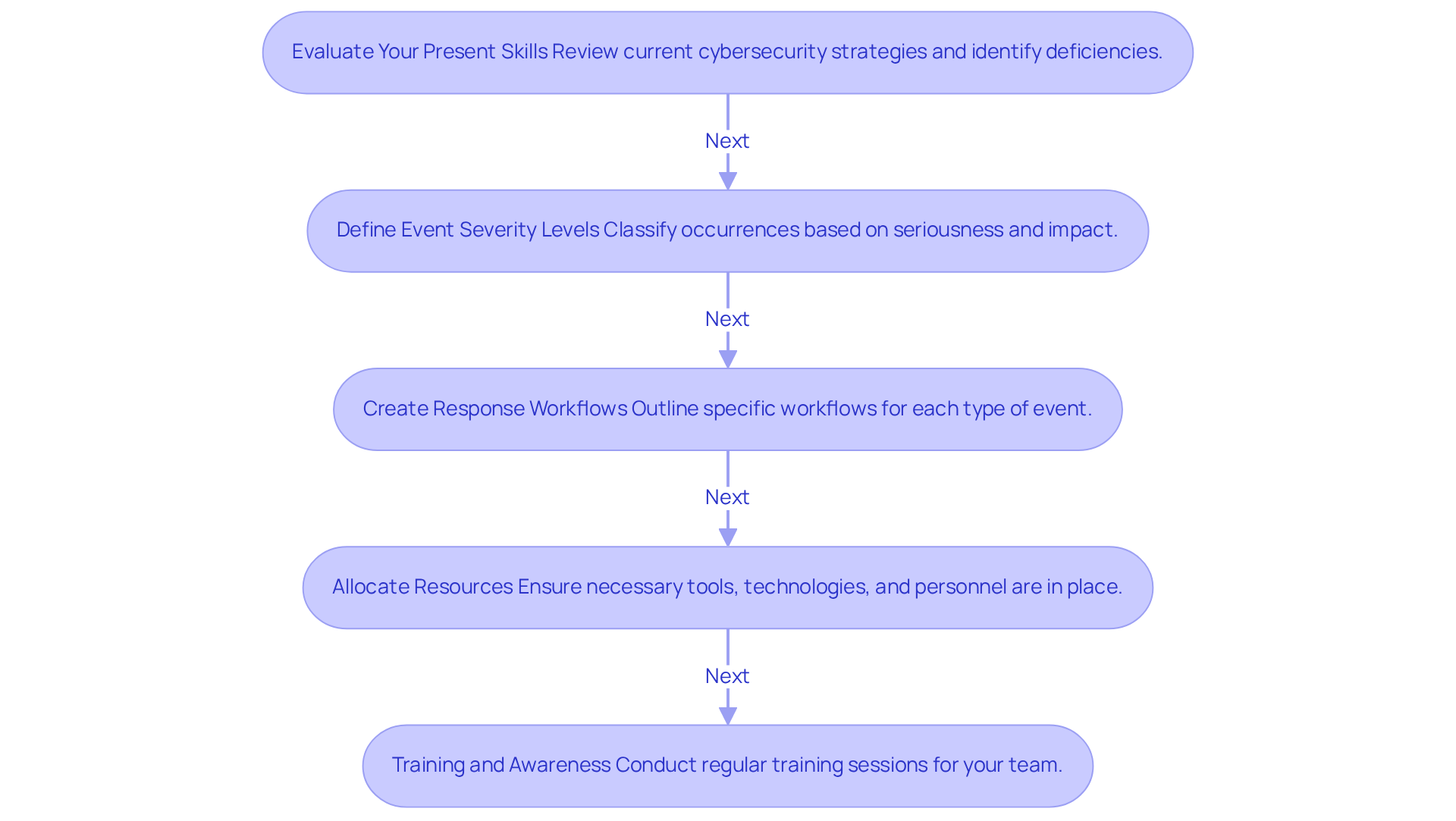
Evaluate Your Present Skills: Start by reviewing your current cybersecurity strategies and crisis management capabilities. What deficiencies can you identify? This evaluation is essential for understanding where improvements are needed.
-
Define Event Severity Levels: Classify occurrences based on their seriousness and potential impact on your organization. How will this classification aid in prioritizing your responses? By establishing clear severity levels, you can ensure that your team reacts appropriately to each situation.
-
Create Response Workflows: For each type of event, outline specific workflows detailing the steps to be taken, including escalation procedures. This clarity will empower your team to act decisively when it matters most.
-
Allocate Resources: Ensure that you have the necessary tools, technologies, and personnel in place to implement your strategy effectively. Are your resources aligned with your response needs? Proper allocation is vital for a successful incident response.
-
Training and Awareness: Conduct regular training sessions for your team to familiarize them with the guidelines and ensure they understand their roles during an event. How prepared is your team to handle incidents? Continuous training fosters confidence and competence.
By creating a clear cyber incident response playbook for handling incidents, you enable your organization to react efficiently to cybersecurity threats. Take action now to fortify your defenses and ensure your team is ready to respond.
Test and Refine Your Playbook Regularly
To maintain the effectiveness of your incident response playbook, regular testing and refinement are crucial.
-
Conduct Simulations: Implement tabletop exercises and realistic simulations to practice your response procedures. These activities not only help identify weaknesses but also enhance team preparedness by familiarizing members with the dynamics of actual events. Effective simulations should evolve dynamically, reflecting the unpredictable nature of real cyber threats and avoiding reliance on pre-scripted scenarios.
-
Review After Events: After any cybersecurity incident, conduct a thorough review to evaluate the effectiveness of your response. This post-incident analysis should focus on understanding root causes, assessing the impact on affected systems, and documenting incident metrics. Moreover, sharing results with stakeholders ensures transparency and promotes enhancements in your strategy, including lessons learned from real-world situations.
-
Stay Informed: Continuously monitor the latest cybersecurity threats and trends. A modern strategy must address current risks, including emerging attack vectors such as ransomware and supply chain vulnerabilities. Regularly revisiting your threat landscape will help ensure your organization is prepared for evolving challenges.
-
Solicit Feedback: Encourage team members to provide input on the guide and suggest enhancements based on their experiences. Involving various stakeholders, including both offensive and defensive security groups, fosters a culture of ongoing improvement and ensures that the guidelines incorporate practical knowledge from those on the front lines of crisis management.
By committing to these practices, you ensure that your incident response playbook evolves alongside your organization and the ever-changing cybersecurity landscape, ultimately enhancing your resilience against potential threats.
Conclusion
Creating a cyber incident response playbook isn’t just a best practice; it’s a necessity for organizations that want to safeguard their digital assets and maintain operational integrity. A well-structured playbook equips teams with the knowledge and procedures needed to respond effectively to cybersecurity incidents. This ultimately minimizes damage, ensures compliance, and enhances communication during crises.
What are the critical components of an effective playbook? It includes:
- Incident identification
- Clearly defined roles
- Response procedures
- Communication plans
- Post-incident reviews
Moreover, developing a tailored incident response strategy is vital. This involves:
- Evaluating existing capabilities
- Defining event severity levels
- Creating specific workflows
- Allocating resources
- Conducting regular training
Continuous testing and refinement of the playbook are essential to adapt to the evolving threat landscape and ensure that teams are prepared for real-world scenarios.
The significance of a cyber incident response playbook cannot be overstated. Organizations must prioritize the development and regular updating of their playbooks to enhance resilience against cyber threats. By taking proactive steps to create, test, and refine their incident response strategies, businesses can protect their data and foster a culture of security awareness and preparedness among their teams. Embracing these practices will lead to a stronger cybersecurity posture and a more secure organizational environment.
Frequently Asked Questions
What is a cyber incident response playbook?
A cyber incident response playbook is a document that outlines the procedures and protocols for managing cybersecurity events, serving as a strategic guide for team members to understand their roles and responsibilities during an incident.
Why is having a cyber incident response playbook important?
Having a playbook is important because it minimizes damage by enabling rapid containment and mitigation of incidents, ensures compliance with regulatory standards, enhances communication among team members, and improves reaction time to cyber threats.
How does a playbook minimize damage during a cyber incident?
A well-structured playbook allows for quick containment and mitigation of cyber incidents, significantly reducing potential losses and enabling organizations to recover more swiftly from breaches.
What role does a playbook play in ensuring compliance?
For organizations pursuing CMMC certification, a playbook signals a commitment to best practices in information security and regulatory adherence, which is crucial as more enterprises focus on proactive cybersecurity measures.
How does a playbook enhance communication during a cyber incident?
The playbook fosters effective communication among team members and stakeholders, ensuring everyone is aligned during a crisis, which is essential given the long average duration to detect a breach.
In what ways does a playbook improve reaction time to incidents?
With a playbook in place, teams can respond more quickly and efficiently to cyber incidents, which is vital for reducing the consequences of such events.
What specific threats can organizations prepare for using a playbook?
Organizations can customize their incident response strategies within the playbook to address specific threats such as ransomware or phishing, thereby enhancing their preparedness and resilience against cyber threats.