Does CUI Need to Be Encrypted? Key Practices for Defense Contractors
Encryption is vital for protecting Controlled Unclassified Information (CUI). Does CUI need to be encrypted?

Introduction
Understanding the complexities of Controlled Unclassified Information (CUI) is essential for defense contractors navigating the intricate landscape of data protection. As the stakes for safeguarding sensitive information continue to rise, the pivotal question arises: does CUI require encryption? This article explores vital practices for effectively securing CUI, examining not only the necessity of encryption but also the strategies that can bolster compliance and enhance overall cybersecurity. With increasing regulatory scrutiny, how can defense contractors ensure they are adequately protecting this critical information against potential threats? Let's delve into the essential steps that can be taken to fortify your defenses.
Understand Controlled Unclassified Information (CUI) and Its Encryption Necessities
Controlled Unclassified Information (CUI) is unclassified information that requires safeguarding or dissemination controls as mandated by law, regulation, or government-wide policy. This sensitive information, while not classified, still demands protection to prevent unauthorized access and potential threats to national security. For defense contractors, understanding CUI is essential; mishandling this information can lead to severe repercussions, including contract loss and reputational damage.
The pivotal role of encryption in protecting CUI raises the question: does CUI need to be encrypted? By transforming understandable information into an encoded format, secure coding ensures that only authorized users with the correct decryption key can access the details. This process safeguards information during transmission and secures it at rest, aligning with regulations such as NIST SP 800-171 and the Cybersecurity Maturity Model Certification (CMMC). Adopting strong security practices not only reduces risks linked to information breaches and unauthorized disclosures but also enhances the overall cybersecurity posture of organizations.
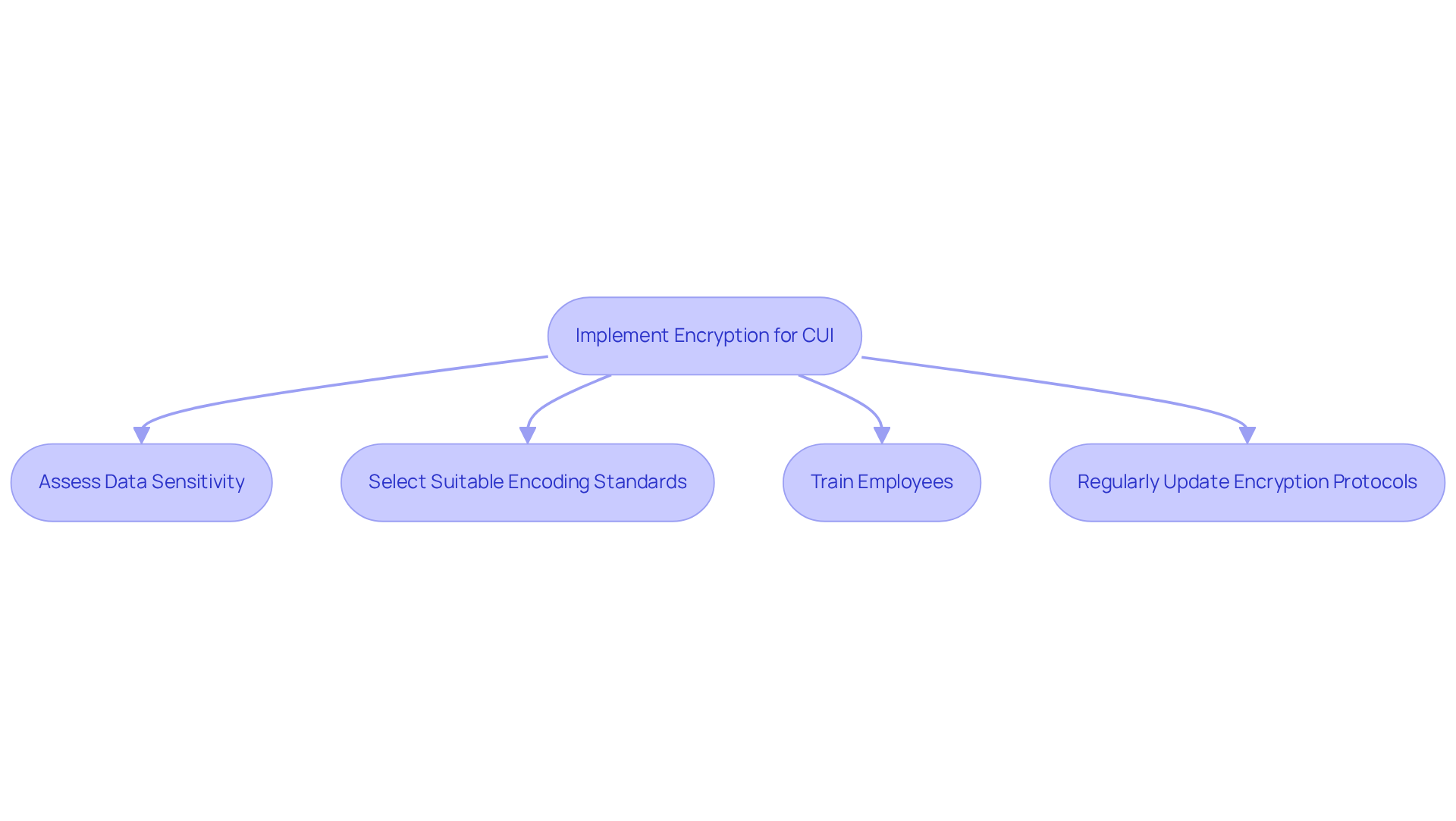
To effectively implement encryption for CUI, defense contractors can follow these practical strategies:
- Assess Data Sensitivity: Identify which data qualifies as CUI and necessitates protection.
- Select Suitable Encoding Standards: Utilize coding methods that comply with NIST guidelines.
- Train Employees: Ensure that all personnel understand the significance of data protection and how to use it effectively.
- Regularly Update Encryption Protocols: Stay current with technological advancements and regulatory changes.
Real-world examples underscore the importance of data protection in defense contracting. Organizations using FedRAMP-authorized storage solutions, like those provided by Virtru, can securely manage and share CUI while adhering to CMMC standards. This approach not only protects sensitive information but also demonstrates a commitment to cybersecurity best practices.
Experts emphasize that protecting CUI is not merely a regulatory requirement; it is a fundamental aspect of safeguarding national security. As the Department of Defense enforces stricter compliance measures, defense contractors must prioritize data protection to avoid the pitfalls of mishandling CUI. Neglecting to do so could result in substantial operational and financial repercussions, highlighting the essential need for effective information protection strategies in the defense sector.
Identify Criteria for CUI Encryption Requirements
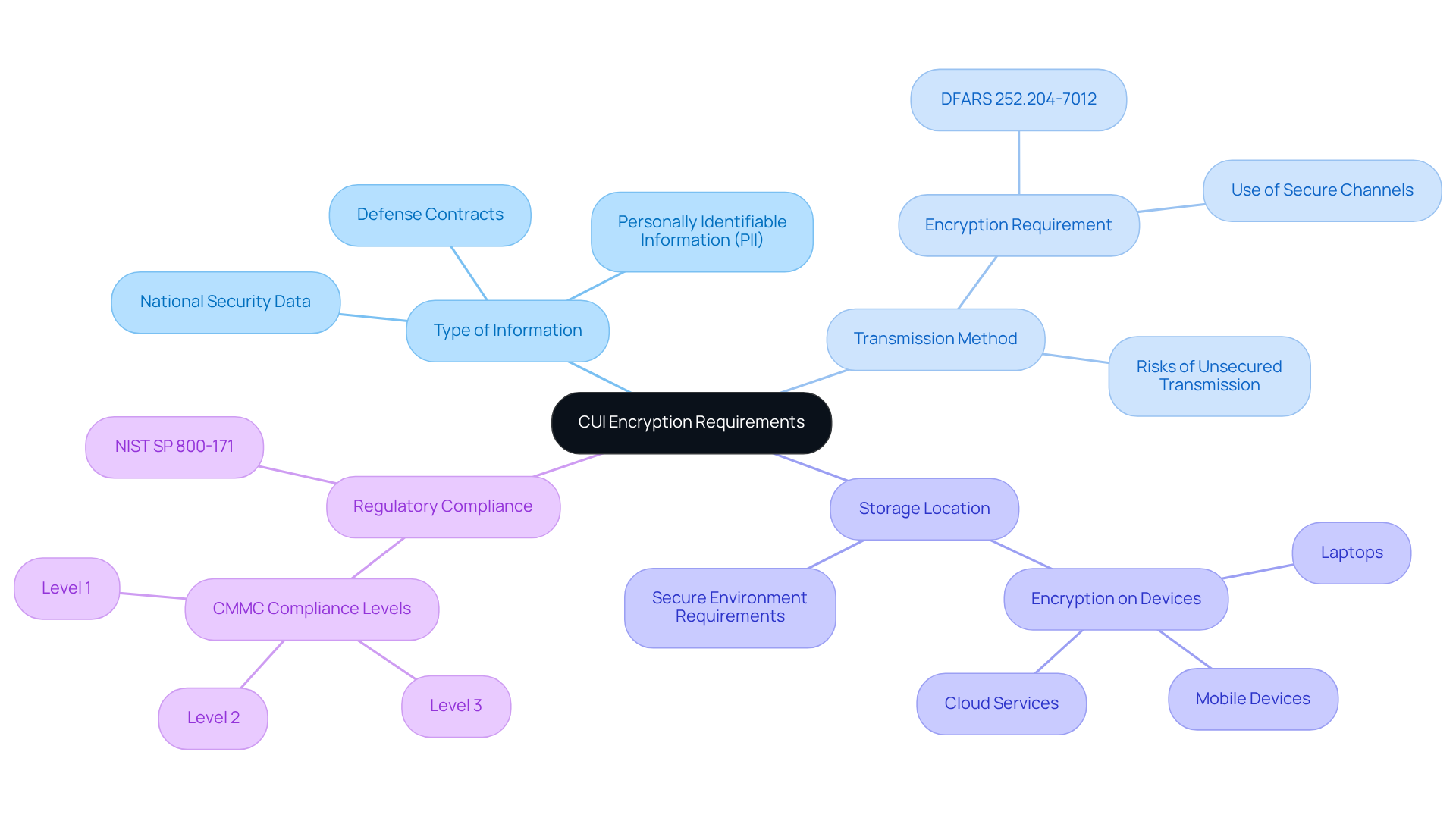
Understanding the criteria for Controlled Unclassified Information (CUI) security requirements is essential for any organization handling sensitive data. These requirements are primarily dictated by the nature of the information and the context in which it is managed. Here are the key factors to consider:
- Type of Information: CUI includes various categories, such as sensitive data related to national security, defense contracts, and personally identifiable information (PII). Each category has specific confidentiality requirements that must be adhered to.
- Transmission Method: When considering the transmission of CUI over unsecured channels like email or public networks, the question arises: does CUI need to be encrypted to prevent interception? Regulations, such as DFARS 252.204-7012, mandate the use of coding for CUI sent through email, highlighting the critical need to protect sensitive information during transmission.
- Storage Location: It is important to consider whether CUI needs to be encrypted when stored on devices or systems outside secure environments. This includes data on laptops, mobile devices, and cloud services, where the risk of unauthorized access is significantly heightened.
- Regulatory Compliance: Organizations must comply with standards established by NIST SP 800-171, which outlines specific data protection requirements for safeguarding CUI both in transit and at rest. Adhering to these standards is vital for maintaining the integrity and confidentiality of sensitive information.
By grasping these criteria, defense contractors can effectively evaluate their security requirements and implement the necessary measures to safeguard CUI. Are you ready to take action and ensure compliance?
Implement Effective Encryption Strategies for CUI
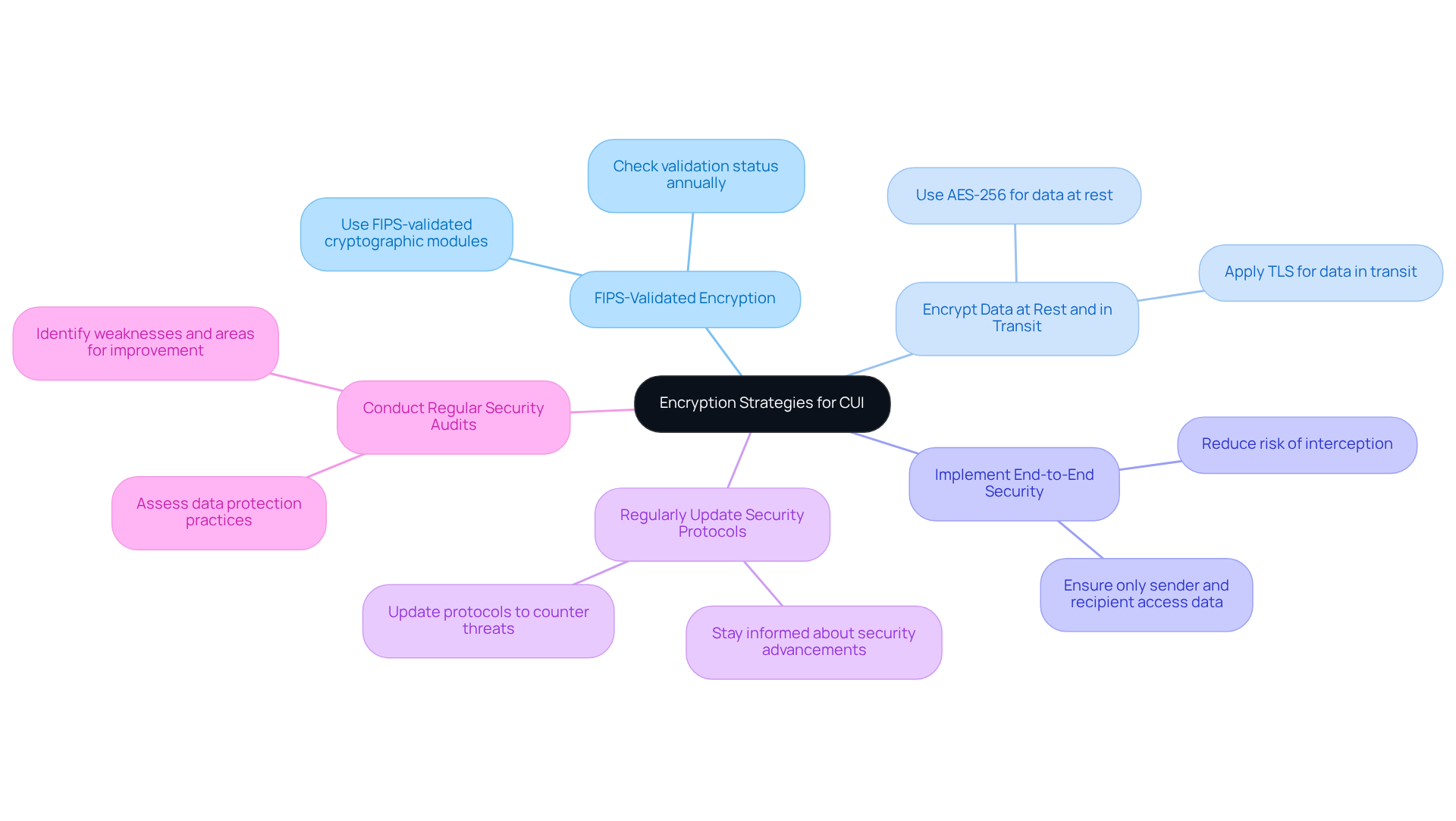
To effectively implement encryption strategies for Controlled Unclassified Information (CUI) and achieve CMMC compliance, defense contractors must follow these essential practices:
-
Use FIPS-Validated Encryption: All cryptographic protections for CUI must utilize FIPS-validated cryptographic modules according to the latest Department of Defense (DoD) standards. This compliance not only guarantees that the security technology is robust but also meets stringent government requirements, which is crucial for maintaining eligibility for Department of Defense contracts.
-
Encrypt Data at Rest and in Transit: It is important to consider if and when does CUI need to be encrypted, both when stored and during transmission. Employ strong encoding algorithms, such as AES-256, for data at rest, and apply Transport Layer Security (TLS) for data in transit. This dual-layer protection is vital for safeguarding sensitive information against unauthorized access, which raises the question: does CUI need to be encrypted?
-
Implement End-to-End Security: For sensitive communications involving CUI, adopt end-to-end security solutions. This approach ensures that only the sender and intended recipient can access the data, significantly reducing the risk of interception during transmission.
-
Regularly Update Security Protocols: Stay informed about the latest advancements in security technologies and update protocols as necessary to counter emerging threats and vulnerabilities. Regular updates are essential for maintaining a strong security posture. Additionally, contractors should verify the validation status of cryptographic modules at least once a year to ensure compliance with CMMC requirements.
-
Conduct Regular Security Audits: Consistently assess data protection practices and adherence to CUI regulations through thorough security audits. These assessments help identify potential weaknesses and areas for improvement, ensuring that organizations remain compliant with evolving standards.
By employing these strategies, organizations can significantly enhance their ability to safeguard CUI and ensure compliance with regulatory mandates. This not only secures their operations within the defense supply chain but also aligns with the ultimate goal of achieving CMMC certification. For further insights and practical strategies, refer to "The Ultimate Guide to Achieving CMMC Compliance," which provides detailed guidance on navigating these requirements effectively.
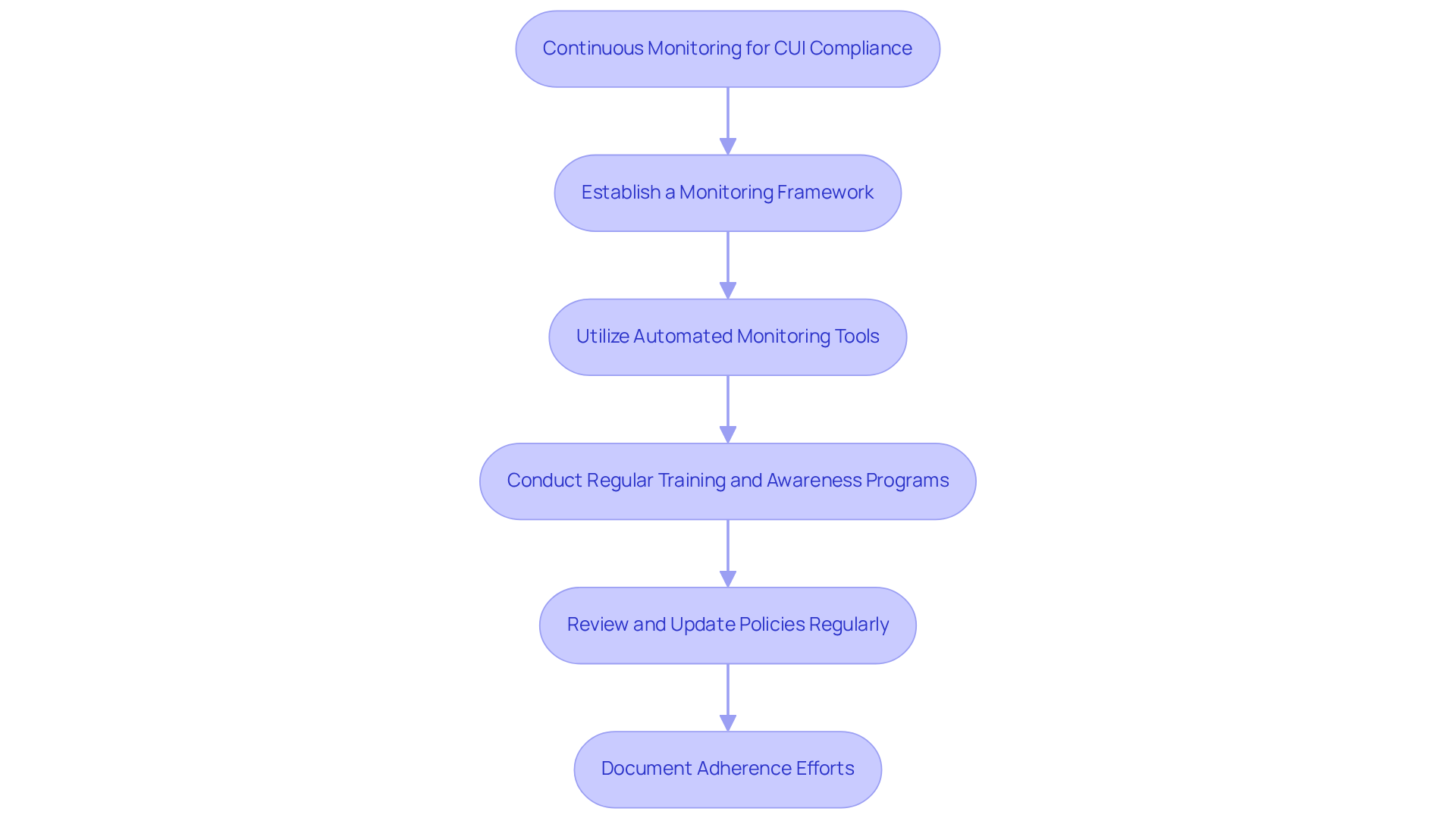
Maintain Compliance Through Continuous Monitoring of CUI Encryption
Ongoing observation of Controlled Unclassified Information (CUI) protection is essential for ensuring compliance and safeguarding sensitive data. Defense contractors must adopt the following best practices to enhance their security posture:
-
Establish a Monitoring Framework: Develop a comprehensive monitoring strategy that includes regular evaluations of data protection practices, adherence to regulations, and the effectiveness of security controls. This proactive approach not only identifies vulnerabilities but also reinforces compliance.
-
Utilize Automated Monitoring Tools: Implement automated tools to continuously track data access, security status, and compliance with CUI regulations. These tools can generate real-time alerts for unauthorized access or potential breaches, significantly enhancing your security measures.
-
Conduct Regular Training and Awareness Programs: Provide thorough training for all staff on the importance of CUI protection and the specific security protocols in place. Ongoing education fosters a culture of security awareness and vigilance, empowering employees to act as the first line of defense.
-
Review and Update Policies Regularly: Consistently review and revise data protection policies and procedures to align with evolving regulations, technological advancements, and organizational needs. Staying current is crucial for maintaining compliance and effectiveness.
-
Document Adherence Efforts: Maintain detailed records of all adherence activities, including data protection practices, monitoring efforts, and incident responses. This documentation is vital for audits and demonstrating compliance to regulatory authorities.
By implementing these continuous monitoring practices, defense contractors can ensure their encryption measures are effective and compliant, particularly regarding the question of whether CUI does need to be encrypted. This not only protects sensitive information but also maintains trust with stakeholders.
Conclusion
Understanding the necessity of encrypting Controlled Unclassified Information (CUI) is critical for defense contractors navigating regulatory landscapes. Why is this important? The protection of CUI is not just a matter of compliance; it’s a fundamental responsibility to safeguard sensitive information that could impact national security. Effective encryption strategies are essential in mitigating risks associated with unauthorized access and ensuring the integrity of data throughout its lifecycle.
To implement CUI encryption effectively, consider these key practices:
- Assess data sensitivity.
- Select appropriate encoding standards.
- Conduct regular training for personnel.
Additionally, utilizing FIPS-validated encryption and employing automated monitoring tools can significantly enhance security measures. Regular audits and updates to policies ensure that organizations remain compliant with evolving regulations, thereby safeguarding their operations and reputation within the defense sector.
In conclusion, prioritizing the encryption of CUI is not merely a regulatory obligation; it’s a crucial step in protecting national security interests. Defense contractors are encouraged to adopt these best practices and continuously evaluate their security frameworks. By doing so, they not only comply with necessary guidelines but also foster a culture of security awareness that empowers employees and protects sensitive information effectively. Taking proactive steps today ensures a secure tomorrow in the ever-evolving landscape of defense contracting.
Frequently Asked Questions
What is Controlled Unclassified Information (CUI)?
Controlled Unclassified Information (CUI) is unclassified information that requires safeguarding or dissemination controls as mandated by law, regulation, or government-wide policy. It is sensitive information that needs protection to prevent unauthorized access and potential threats to national security.
Why is understanding CUI important for defense contractors?
Understanding CUI is essential for defense contractors because mishandling this information can lead to severe repercussions, including contract loss and reputational damage.
Does CUI need to be encrypted?
Yes, CUI needs to be encrypted to protect it during transmission and secure it at rest. Encryption ensures that only authorized users with the correct decryption key can access the information.
What regulations align with the encryption of CUI?
The encryption of CUI aligns with regulations such as NIST SP 800-171 and the Cybersecurity Maturity Model Certification (CMMC).
What are some strategies for implementing encryption for CUI?
Effective strategies for implementing encryption for CUI include: Assessing data sensitivity to identify which data qualifies as CUI. Selecting suitable encoding standards that comply with NIST guidelines. Training employees on the significance of data protection and how to use encryption effectively. Regularly updating encryption protocols to stay current with technological advancements and regulatory changes.
What examples illustrate the importance of data protection in defense contracting?
Organizations using FedRAMP-authorized storage solutions, such as those provided by Virtru, can securely manage and share CUI while adhering to CMMC standards. This approach protects sensitive information and demonstrates a commitment to cybersecurity best practices.
Why is protecting CUI considered a fundamental aspect of national security?
Protecting CUI is fundamental to national security because it helps safeguard sensitive information from unauthorized access. As the Department of Defense enforces stricter compliance measures, prioritizing data protection is crucial for defense contractors to avoid operational and financial repercussions.