Essential Best Practices for Your IT Security Assessment
Master essential best practices for a comprehensive IT security assessment to enhance your defenses.

Introduction
As organizations increasingly depend on digital infrastructure, the necessity for robust IT security assessments has reached a critical juncture. These assessments not only pinpoint vulnerabilities but also lay the groundwork for fortifying an organization’s overall cybersecurity posture. Yet, many organizations find themselves grappling with how to define the scope and objectives of their assessments. This struggle can result in significant gaps in security and compliance.
So, how can organizations effectively navigate this intricate landscape? Ensuring that IT security assessments are thorough, efficient, and aligned with regulatory standards is paramount. By addressing these challenges head-on, organizations can enhance their security frameworks and safeguard their digital assets.
Define Scope and Objectives for IT Security Assessments
To effectively define the scope and objectives of your IT security assessment, it is essential to engage key stakeholders early in the process. This engagement not only gathers valuable input regarding critical assets and potential threats but also addresses regulatory requirements. By utilizing established frameworks such as NIST or ISO standards, you can significantly enhance the clarity and effectiveness of your scope definition.
Clearly specify which systems, information, and procedures will be included in the evaluation. Set measurable goals that align with your entity's risk management approach. For example, if your organization manages sensitive defense data, your objectives should focus on identifying vulnerabilities specific to that data and ensuring compliance with CMMC standards.
Documenting these elements provides a structured roadmap for the evaluation process and facilitates clear communication of expectations among all involved parties. Engaging stakeholders in this manner fosters collaboration and ensures that the assessment aligns with organizational goals. Ultimately, this approach enhances the effectiveness of your cybersecurity posture.
Are you ready to take the necessary steps to secure your organization? By prioritizing stakeholder engagement and adhering to established frameworks, you can build a robust IT security assessment that not only meets compliance standards but also strengthens your defenses against potential threats.
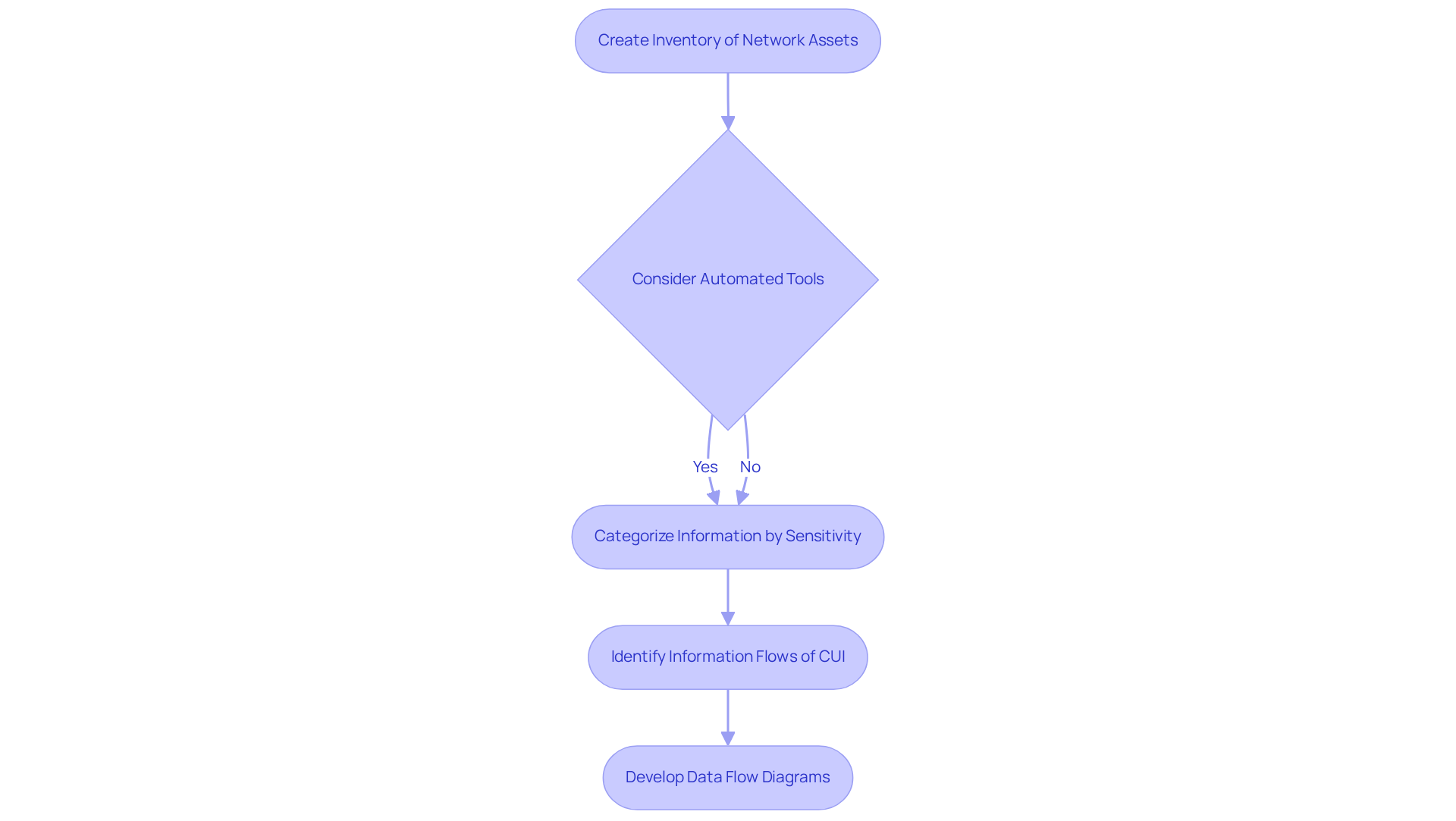
Inventory Network Assets and Identify Sensitive Data
Begin by creating a comprehensive inventory of all network assets, including hardware, software, and information repositories. Have you considered how automated tools can streamline this process? They can significantly enhance both accuracy and efficiency. In fact, around 46% of organizations do not utilize automated tools for asset inventory, highlighting a major opportunity for improvement in managing sensitive information effectively.
Once your inventory is in place, categorize the information based on sensitivity levels. Prioritize items that demand the highest level of protection, such as personally identifiable information (PII) and classified defense information. A robust classification system is essential for an IT security assessment, as it allows organizations to tailor security measures according to the sensitivity of the information.
Moreover, it’s vital to identify all information flows of Controlled Unclassified Information (CUI) during your IT security assessment within your environment. This includes flows between systems, personnel, third-party vendors, and customers. Developing data flow diagrams can help visualize these flows and pinpoint all relevant assets, including systems that handle, store, or transmit CUI, along with their security functions and external connections.
As cybersecurity expert Lavanya Chandrasekharan aptly states, "Without a reliable inventory, you will always be blindsided by unknown elements." Regular updates to this inventory are crucial to adapt to changes in the network environment and ensure compliance with evolving regulations.
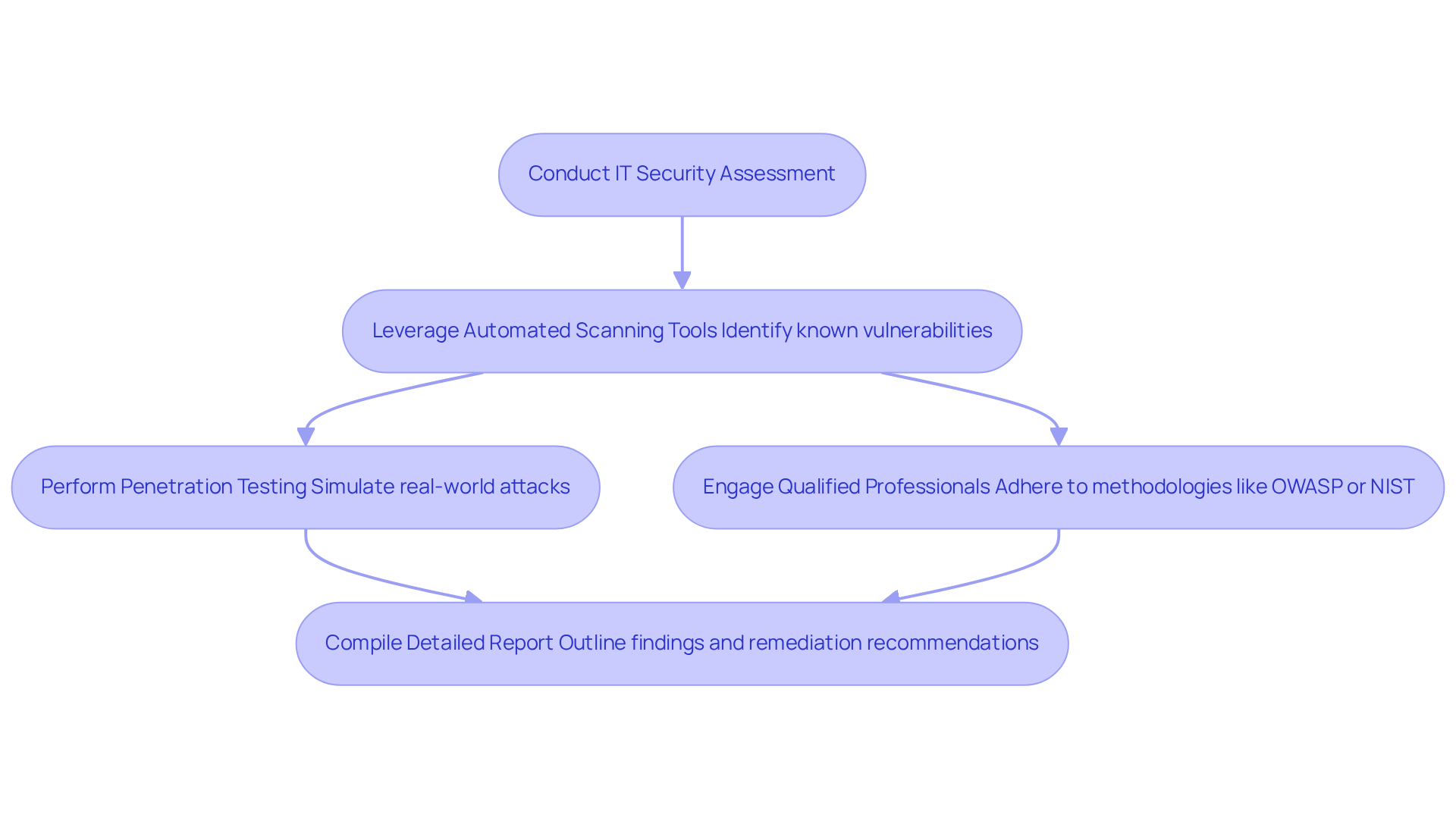
Conduct Vulnerability Analysis and Penetration Testing
To conduct a thorough IT security assessment, begin by leveraging automated scanning tools that identify known vulnerabilities within your systems. This initial step is crucial for establishing a solid foundation. Next, penetration testing simulates real-world attacks, allowing you to perform an IT security assessment of the effectiveness of your security controls. Have you engaged qualified professionals or certified ethical hackers? It's essential that they adhere to established methodologies such as OWASP or NIST in their IT security assessment. For instance, in regulated sectors like finance and healthcare, where penetration testing adoption exceeds 70%, IT security assessment frameworks are frequently employed to ensure comprehensive evaluations.
After testing, compile a detailed report outlining your findings. This report should include the severity of each vulnerability and actionable remediation recommendations. If a critical vulnerability is identified in a web application, prioritize its remediation to mitigate potential exploitation. Consistently planned evaluations not only help sustain a strong security stance but also support compliance with IT security assessment and CMMC standards. Did you know that 82% of entities perform penetration tests primarily for risk evaluation and correction?
By following these practical strategies and insights, defense contractors can transform confusion into clarity. This approach effectively navigates the complexities of CMMC regulations and secures defense contracts. Think of it as a comprehensive roadmap to DoD cybersecurity compliance, guiding entities through the essential steps to achieve and uphold compliance.
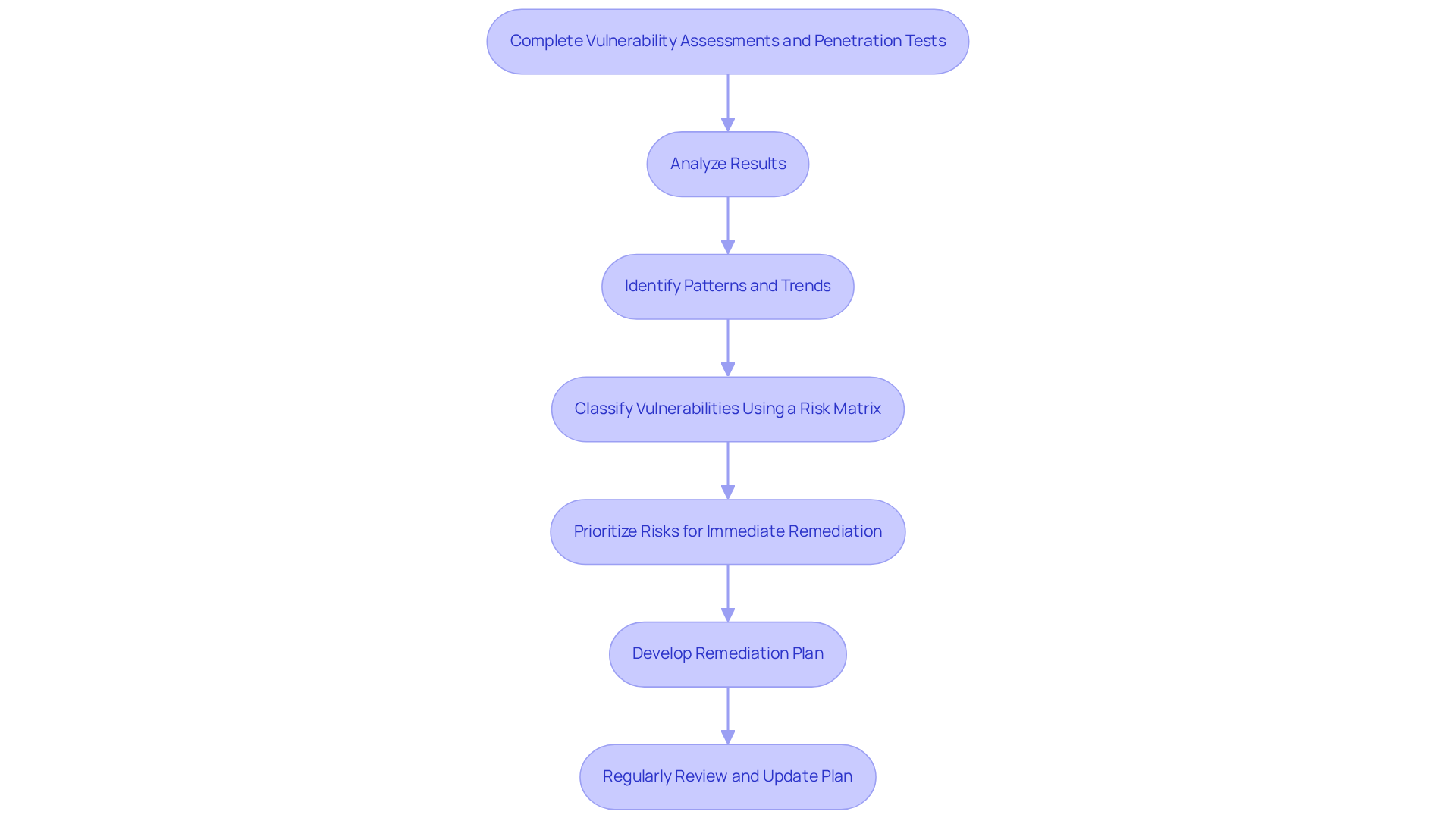
Analyze Results and Prioritize Risks for Effective Remediation
After completing vulnerability assessments and penetration tests, it’s crucial to analyze the results of the IT security assessment. This analysis aids in identifying patterns and trends in your IT security assessment. Have you considered how a risk matrix can classify vulnerabilities based on their severity and potential impact? For example, vulnerabilities that could lead to data breaches or significant operational disruptions should be prioritized for immediate remediation.
Next, develop a remediation plan that outlines specific actions, timelines, and responsible parties for addressing each identified risk. Regularly reviewing and updating this plan is essential to reflect changes in the threat landscape and organizational priorities. By taking a proactive approach to risk management, organizations can enhance their cybersecurity posture and ensure compliance with CMMC standards.
In summary, understanding and addressing vulnerabilities is not just a best practice; it’s a necessity for safeguarding your organization.
Conclusion
Establishing a comprehensive IT security assessment is crucial for safeguarding your organization’s assets and ensuring compliance with industry standards. Have you considered how stakeholder engagement, a detailed asset inventory, and systematic vulnerability analysis can significantly enhance your cybersecurity posture? By emphasizing these best practices, you not only address immediate security concerns but also build a resilient framework for ongoing protection against evolving threats.
This article outlines critical strategies that can transform your approach to IT security. Start by:
- Defining clear objectives
- Utilizing automated tools for asset management
- Conducting thorough vulnerability assessments and penetration tests
Each of these components plays a vital role in creating a structured approach to identifying and mitigating risks. Regularly updating your inventory and remediation plans, along with prioritizing vulnerabilities based on their potential impact, ensures that your organization remains agile in the face of new challenges.
The importance of a well-executed IT security assessment cannot be overstated. As threats continue to evolve, organizations must take proactive measures to protect sensitive information and maintain compliance with regulations such as CMMC. By adopting these best practices, you can navigate the complexities of IT security assessments and cultivate a culture of security that is integral to your operational success. Are you ready to take the next step in fortifying your organization’s cybersecurity?
Frequently Asked Questions
Why is it important to engage stakeholders in the IT security assessment process?
Engaging stakeholders early in the IT security assessment process gathers valuable input regarding critical assets and potential threats, and addresses regulatory requirements.
What frameworks can be utilized to enhance the clarity of the scope definition in IT security assessments?
Established frameworks such as NIST or ISO standards can be utilized to significantly enhance the clarity and effectiveness of the scope definition.
What should be clearly specified in the scope of an IT security assessment?
It is essential to clearly specify which systems, information, and procedures will be included in the evaluation.
How should objectives be set for an IT security assessment?
Objectives should be measurable and aligned with the entity's risk management approach, focusing on specific vulnerabilities and compliance requirements.
What is an example of setting objectives for an organization managing sensitive data?
For an organization managing sensitive defense data, objectives should focus on identifying vulnerabilities specific to that data and ensuring compliance with CMMC standards.
What is the benefit of documenting the scope and objectives of an IT security assessment?
Documenting these elements provides a structured roadmap for the evaluation process and facilitates clear communication of expectations among all involved parties.
How does stakeholder engagement affect the effectiveness of the cybersecurity posture?
Engaging stakeholders fosters collaboration and ensures that the assessment aligns with organizational goals, ultimately enhancing the effectiveness of the cybersecurity posture.
What steps should organizations take to secure themselves regarding IT security assessments?
Organizations should prioritize stakeholder engagement and adhere to established frameworks to build a robust IT security assessment that meets compliance standards and strengthens defenses against potential threats.