How to Measure Cybersecurity Risk: A Step-by-Step Guide for Defense Contractors
Learn effective strategies for measuring cybersecurity risk in defense contracting.
Introduction
Understanding the complexities of cybersecurity risk measurement is crucial for defense contractors operating in a landscape filled with potential threats. Did you know that the average cost of a data breach in this sector can exceed $9 million? The stakes have never been higher. This guide explores essential methodologies and strategies that enable organizations to effectively quantify their cybersecurity vulnerabilities. As cyberattacks continue to escalate, how can defense contractors ensure their risk assessment processes are both comprehensive and adaptable to an ever-evolving threat environment?
Understand Cybersecurity Risk Measurement Fundamentals
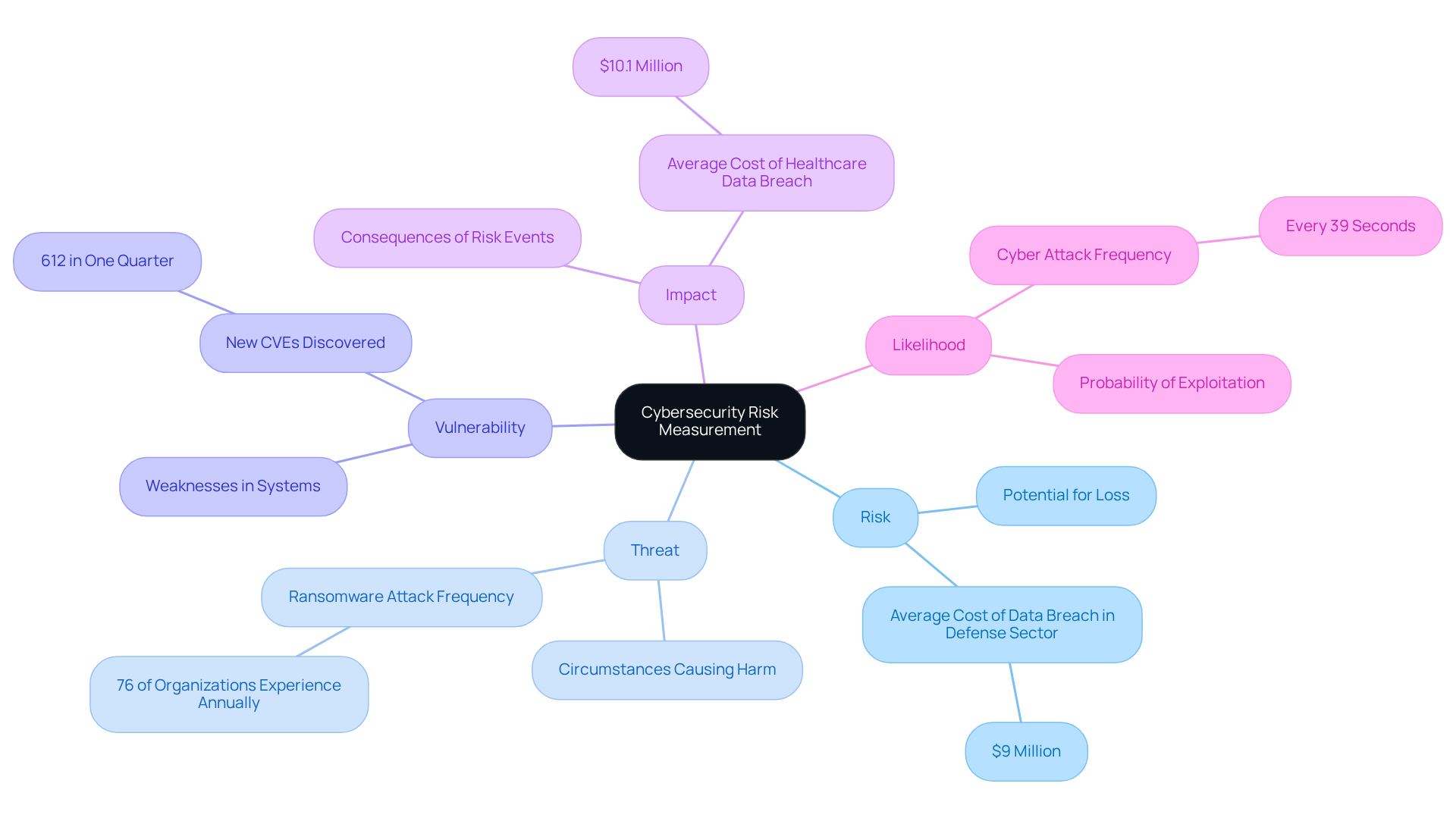
To effectively measure cybersecurity risk, understanding several key concepts is essential:
-
Risk: This refers to the potential for loss or damage when a threat exploits a vulnerability. In cybersecurity, threats often involve the loss of sensitive data or disruption of operational capabilities. For instance, did you know that the average cost of a data breach in the defense sector can exceed $9 million? This underscores the financial implications of inadequate risk management.
-
Threat: Any circumstance or event that has the potential to cause harm. This encompasses cyber attacks, natural disasters, and internal risks. Recent trends reveal that 76% of organizations encounter at least one ransomware attack each year. This statistic emphasizes the widespread nature of cyber risks.
-
Vulnerability: A weakness in a system that can be exploited by threats. Understanding these vulnerabilities is crucial for evaluating the threat linked to specific assets. For example, the discovery of over 612 new Common Vulnerabilities and Exposures (CVEs) in just one quarter highlights the ongoing challenges organizations face in maintaining secure systems.
-
Impact: The potential consequences of a risk event can be financial, reputational, or operational. The healthcare industry, for example, has experienced breaches amounting to an average of $10.1 million. This demonstrates the serious consequences of security incidents.
-
Likelihood: The probability that a danger will exploit a vulnerability. With a cyber attack occurring every 39 seconds, defense contractors must evaluate the probability of different threats to prioritize their security efforts effectively.
By grasping these concepts, defense contractors can begin to understand how to measure cybersecurity risk effectively. This understanding prepares them for more detailed evaluations and informed decision-making.
Select Appropriate Methodologies for Risk Measurement
Choosing the right methodology for how to measure cybersecurity risk is crucial for defense contractors. Are you aware of the key considerations that can guide your decision-making process?
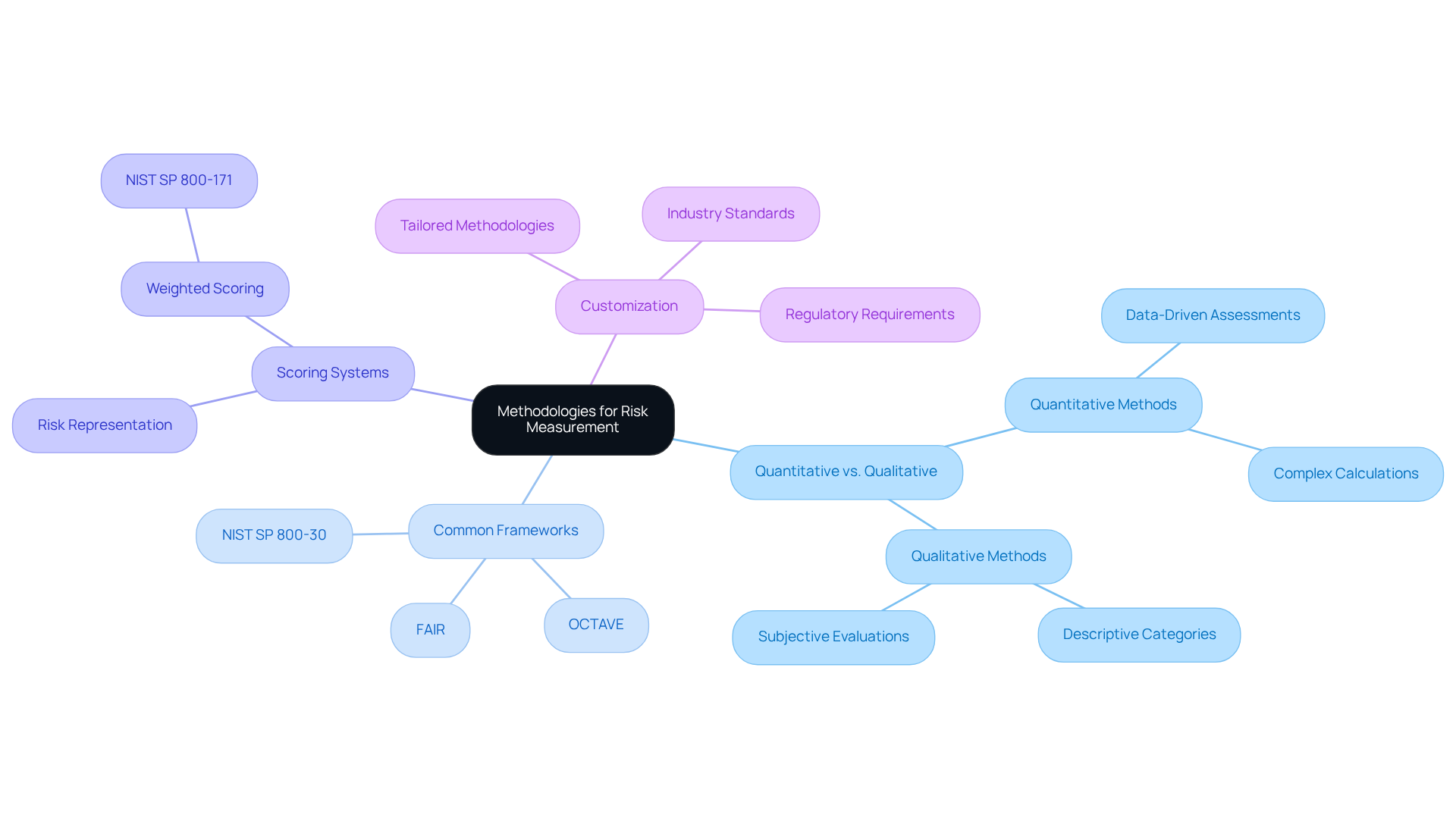
- Quantitative vs. Qualitative: Quantitative methods leverage numerical values to assess potential issues, while qualitative methods rely on descriptive categories. Consider your data availability and the level of detail required for your assessments.
- Common Frameworks: Familiarize yourself with established frameworks such as NIST SP 800-30, FAIR (Factor Analysis of Information Risk), and OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation). Each framework has its strengths and is tailored for different types of assessments.
- Scoring Systems: Establish scoring systems that accurately represent the degree of danger associated with various threats and vulnerabilities. For example, the NIST SP 800-171 assessment procedure employs a weighted scoring system to evaluate threats to Controlled Unclassified Information (CUI).
- Customization: Tailor your chosen methodology to fit the specific context of your organization. Consider factors such as industry standards, regulatory requirements, and organizational goals.
By thoughtfully selecting a methodology, defense contractors can ensure that their evaluations effectively demonstrate how to measure cybersecurity risk in a precise and relevant manner. This strategic approach not only enhances compliance but also strengthens overall cybersecurity posture.
Implement Controls Based on Risk Assessment Results
After evaluating hazards, the next phase is to implement suitable measures to mitigate those threats, particularly regarding how to measure cybersecurity risk for CMMC compliance. Here’s how to proceed:
-
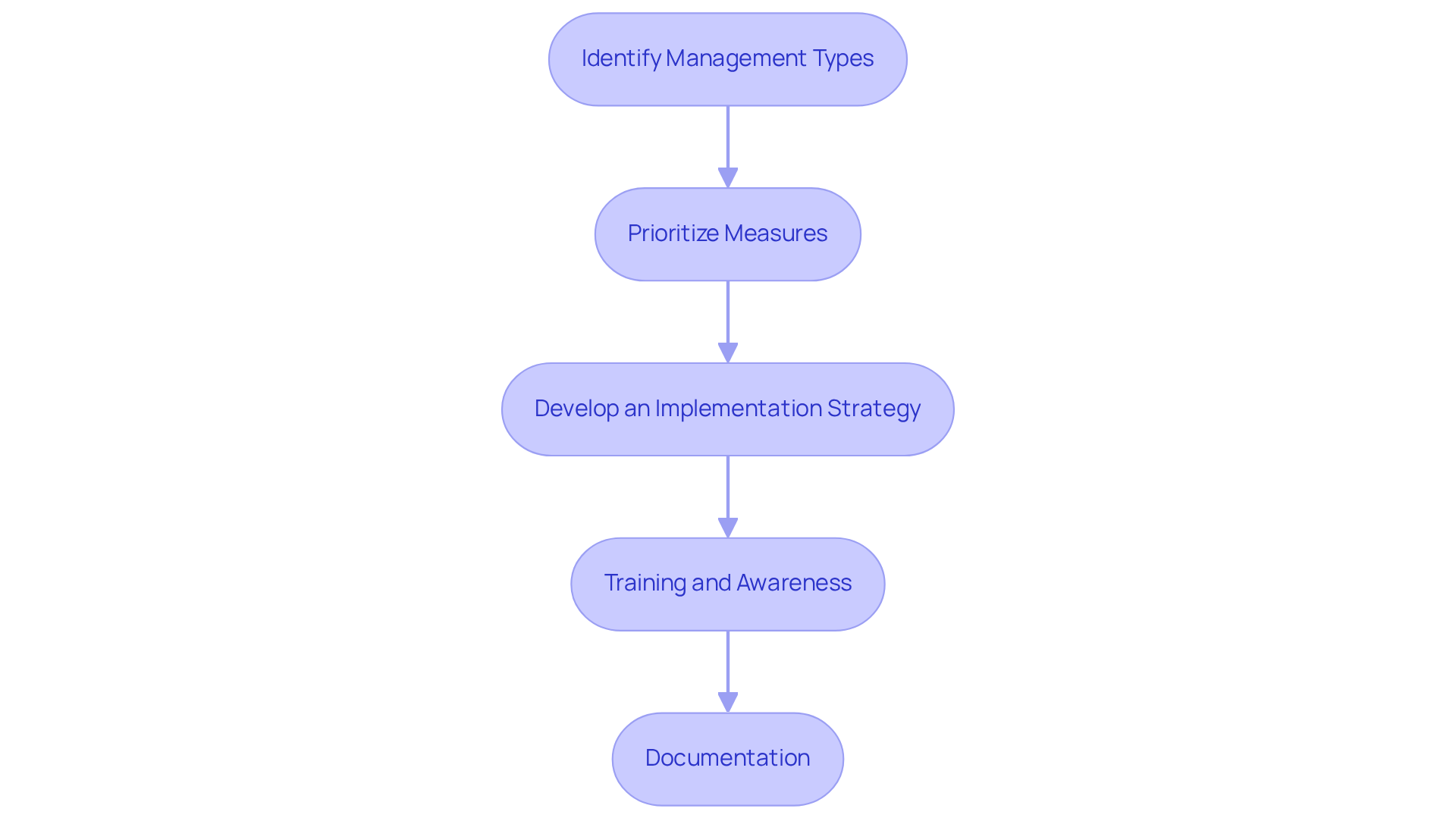
Identify Management Types: Understand the various types of measures available, including preventive, detective, and corrective measures. Each category serves a distinct function in managing uncertainties. Preventive measures aim to stop incidents before they arise, detective measures focus on recognizing incidents as they occur, and corrective measures are intended to tackle and resolve problems after an incident.
-
Prioritize Measures: Based on the risk assessment results, prioritize which measures to implement first. Concentrate on high-risk areas that could severely impact your organization. For instance, over 80% of aerospace and defense organizations experienced breaches in the past year, and there has been a staggering 300% increase in cyberattacks in this sector since 2018. Addressing vulnerabilities in these areas is critical for achieving CMMC compliance. Consider leveraging strategies from "The Ultimate Guide to Achieving CMMC Compliance" to effectively tackle these vulnerabilities.
-
Develop an Implementation Strategy: Create a detailed plan outlining how each measure will be implemented, including timelines, responsible parties, and required resources. This structured approach ensures that all stakeholders are aligned and accountable, which is essential for understanding how to measure cybersecurity risk and meeting CMMC requirements. Incorporate insights from the user manual to enhance the effectiveness of your plan.
-
Training and Awareness: Ensure that all employees are educated on the new measures and understand their roles in upholding cybersecurity. This is vital for the efficiency of any established measures. Did you know that 60% of small enterprises that experience a cyberattack cease operations within six months? The overall expense of cybercrimes to small businesses is estimated at $2.4 billion annually. A well-informed workforce is crucial for understanding how to measure cybersecurity risk in relation to compliance with CMMC standards.
-
Documentation: Maintain thorough records of all measures implemented, including their purpose, effectiveness, and any incidents related to them. This documentation is essential for compliance audits and future assessments, especially as CMMC compliance becomes a mandatory requirement for all DoD contracts.
By systematically applying controls, defense contractors can significantly reduce their security vulnerabilities and enhance their overall safety stance. This proactive approach ensures they remain competitive and compliant in a rapidly evolving threat environment.
Establish Continuous Monitoring and Reassessment Processes
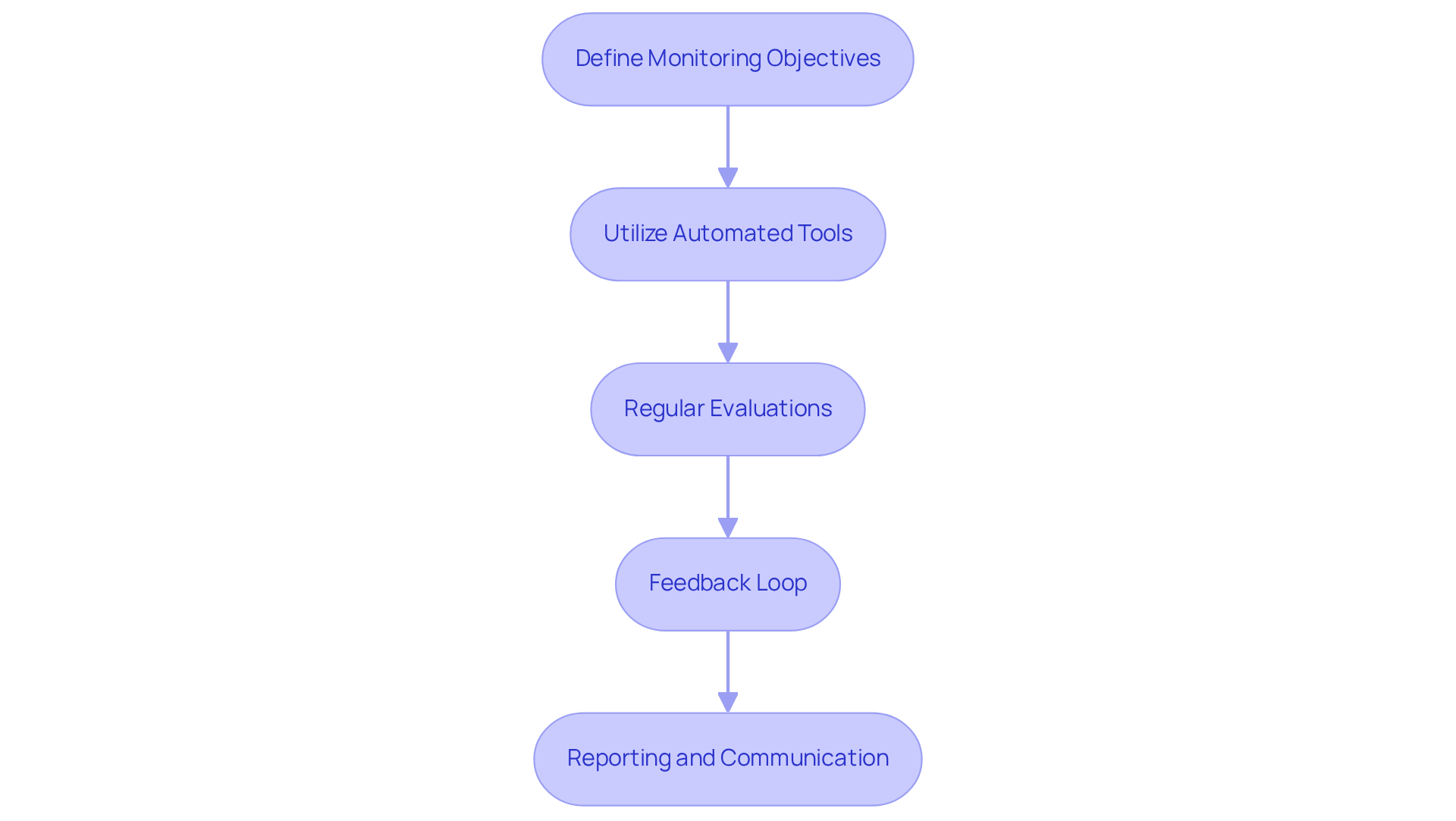
To effectively manage cybersecurity risks, organizations must understand how to measure cybersecurity risk through continuous monitoring and reassessment processes.
- Define Monitoring Objectives: What aspects of your security posture will you monitor? Clearly outline key areas such as network traffic, user behavior, and adherence to security policies. This clarity sets the foundation for effective monitoring.
- Utilize Automated Tools: Have you considered implementing automated monitoring tools? These tools can provide real-time alerts for suspicious activities or potential breaches, significantly enhancing your ability to respond quickly to threats.
- Regular Evaluations: How often do you evaluate your cybersecurity vulnerabilities? Frequent assessments are crucial for understanding how to measure cybersecurity risk. This includes evaluating the effectiveness of current strategies and recognizing any new threats that may have emerged.
- Feedback Loop: Are you creating a feedback loop? Insights gained from monitoring and reassessments should inform future risk assessments and control implementations. This iterative process is vital for learning how to measure cybersecurity risk and enhancing your information security strategy.
- Reporting and Communication: Do you have clear reporting mechanisms in place? Establishing these ensures that findings from monitoring and reassessments are communicated to relevant stakeholders, keeping decision-makers informed and ready to take necessary actions.
By implementing continuous monitoring and reassessment processes, defense contractors can maintain a proactive stance against cybersecurity threats and ensure ongoing compliance with CMMC requirements. For further guidance, refer to our FAQs and external resources that provide additional insights into best practices and compliance strategies.
Conclusion
Measuring cybersecurity risk is not just important; it’s essential for defense contractors. This process directly impacts their ability to safeguard sensitive information and uphold operational integrity. By grasping the core concepts of risk, threats, vulnerabilities, impact, and likelihood, organizations can establish a solid framework for effectively evaluating and managing cybersecurity risks.
In this guide, we’ve explored key methodologies for risk measurement. Selecting the right frameworks and scoring systems tailored to specific organizational contexts is crucial. Moreover, implementing controls based on comprehensive risk assessments is vital. Prioritizing these measures and cultivating a culture of cybersecurity awareness among employees cannot be overlooked. Continuous monitoring and reassessment processes are equally important, as they allow organizations to adapt to the ever-evolving threat landscape.
The significance of measuring cybersecurity risk, especially in the defense industry, cannot be overstated. The stakes are high, and a proactive, systematic approach to risk measurement and management is necessary. By doing so, defense contractors can enhance their compliance with industry standards like CMMC and protect their operations from potential cyber threats. Embracing these best practices will ultimately fortify their cybersecurity posture, ensuring resilience in the face of emerging challenges.
Frequently Asked Questions
What is cybersecurity risk?
Cybersecurity risk refers to the potential for loss or damage when a threat exploits a vulnerability, often involving the loss of sensitive data or disruption of operational capabilities.
What constitutes a threat in cybersecurity?
A threat is any circumstance or event that has the potential to cause harm, which includes cyber attacks, natural disasters, and internal risks.
How prevalent are ransomware attacks?
Recent trends indicate that 76% of organizations encounter at least one ransomware attack each year, highlighting the widespread nature of cyber risks.
What is a vulnerability in the context of cybersecurity?
A vulnerability is a weakness in a system that can be exploited by threats, making it essential to understand these vulnerabilities to evaluate the associated risks.
Can you provide an example of recent vulnerabilities?
In just one quarter, over 612 new Common Vulnerabilities and Exposures (CVEs) were discovered, illustrating the ongoing challenges organizations face in maintaining secure systems.
What is the impact of cybersecurity risks?
The impact of a cybersecurity risk event can be financial, reputational, or operational. For instance, the healthcare industry has experienced breaches with an average cost of $10.1 million.
How is likelihood defined in cybersecurity risk measurement?
Likelihood refers to the probability that a threat will exploit a vulnerability, with cyber attacks occurring every 39 seconds, necessitating effective evaluation by defense contractors.
Why is understanding these concepts important for defense contractors?
Grasping these concepts allows defense contractors to measure cybersecurity risk effectively, preparing them for more detailed evaluations and informed decision-making.




