How to Protect CUI: Essential Steps for Defense Contractors
Learn essential steps on how to protect CUI for defense contractors to enhance security.

Introduction
Understanding the complexities of Controlled Unclassified Information (CUI) is crucial for defense contractors operating within the national security landscape. Unauthorized disclosures can severely compromise sensitive data, making it essential for organizations to adopt strong protective measures. So, what steps can defense contractors take to not only protect this vital information but also ensure compliance with the ever-evolving federal regulations?
-
First, it’s important to recognize the significance of CUI in safeguarding national security. By implementing comprehensive security protocols, contractors can mitigate risks associated with data breaches. For instance, regular training sessions for employees on CUI handling can significantly reduce the likelihood of accidental disclosures.
-
Moreover, staying informed about the latest federal regulations is key. As these regulations evolve, so too must the strategies employed by defense contractors. Engaging with industry experts and utilizing available resources can provide invaluable insights into compliance requirements.
In conclusion, the responsibility of protecting CUI lies heavily on the shoulders of defense contractors. By taking proactive steps to enhance security measures and ensure compliance, organizations can not only safeguard sensitive information but also contribute to the overall integrity of national security.
Define Controlled Unclassified Information (CUI)
Controlled Unclassified Information (CUI) is a critical concept that refers to unclassified information created or possessed by the U.S. government, or by entities acting on its behalf, which requires specific safeguarding or dissemination controls. While CUI is not classified, its sensitivity means that unauthorized disclosure could potentially harm national security or other vital interests.
Understanding CUI is essential for defense providers. It encompasses various types of information, including:
- Technical data
- Proprietary information
- Personal data
All of which must be protected in accordance with federal regulations. Have you familiarized yourself with the CUI categories outlined in the CUI Registry? Doing so is crucial to ensure compliance with the necessary safeguarding requirements.
To summarize, understanding how to protect CUI not only safeguards sensitive information but also enhances national security. Take the time to review the CUI Registry and understand how to protect CUI by implementing the required safeguards to uphold your responsibilities effectively.
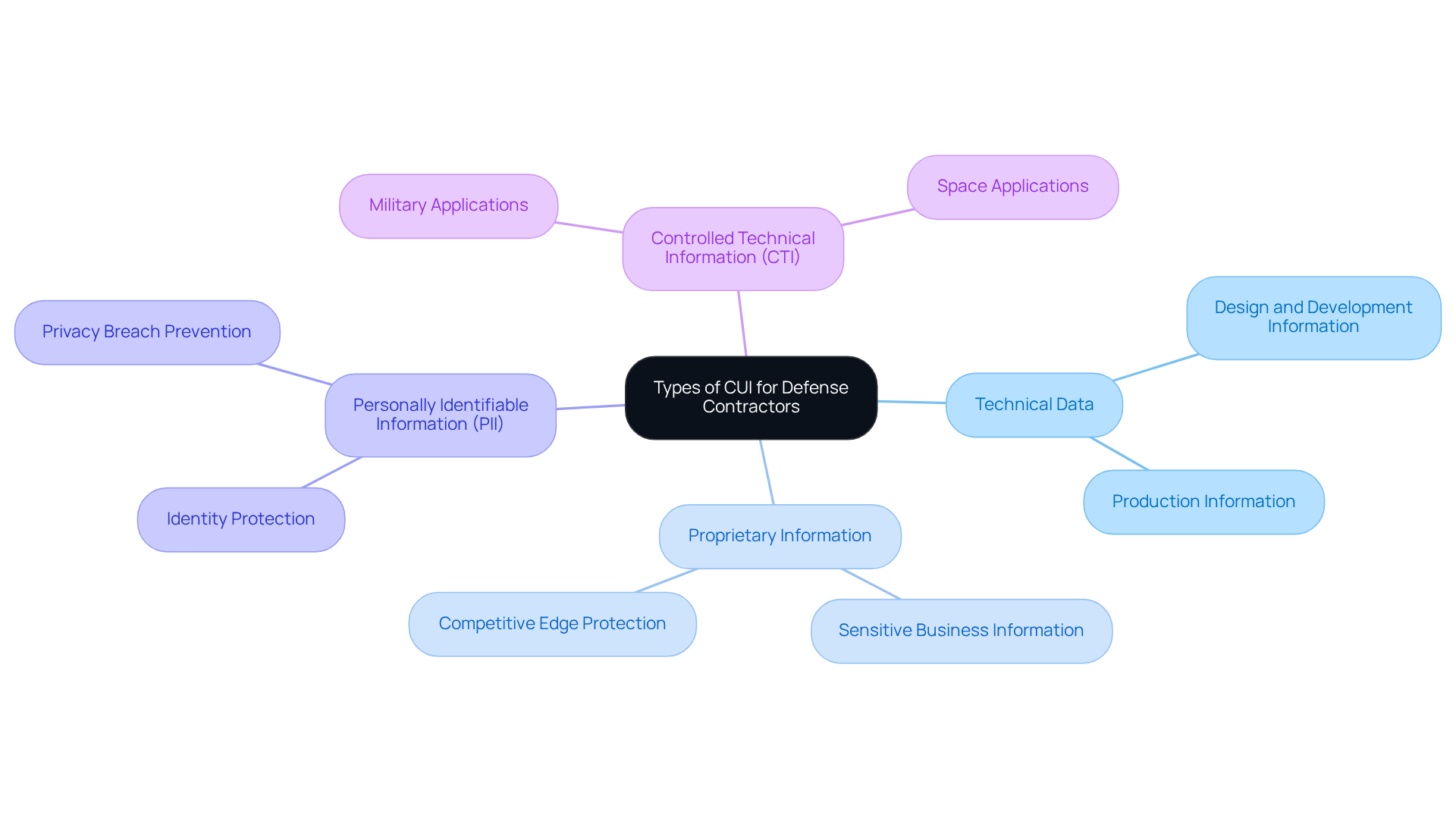
Identify Types of CUI Relevant to Defense Contractors
Defense suppliers must accurately identify the specific types of Controlled Unclassified Information (CUI) to understand how to protect CUI and implement effective protection measures. Why is this crucial? Understanding CUI is essential for safeguarding national security and maintaining organizational integrity. Common categories of CUI relevant to defense contractors include:
- Technical Data: This includes information related to the design, development, or production of defense systems, which is vital for national security.
- Proprietary Information: Sensitive business information that could provide a competitive edge if disclosed, making its protection essential for organizational integrity.
- Personally Identifiable Information (PII): Data that can identify an individual, such as social security numbers or personal addresses, requiring stringent protection to prevent identity theft and privacy breaches.
- Controlled Technical Information (CTI): Technical data with military or space applications that must be safeguarded due to its potential impact on national security.
Comprehending these categories is essential for builders to evaluate their data handling practices effectively. A significant data breach in 2011 compromised the medical histories of over 4.9 million military personnel, underscoring the critical need for robust protection measures. Cybersecurity specialists emphasize how to protect CUI, stating that newer companies entering the defense industry should implement strict training and data protection protocols to ensure adherence to regulations. By adopting these practices, builders can enhance their cybersecurity posture and meet the stringent requirements set forth by the Department of Defense. For further guidance, builders are encouraged to consult the FAQs and external resources available through CMMC Info Hub, a comprehensive resource for achieving compliance.
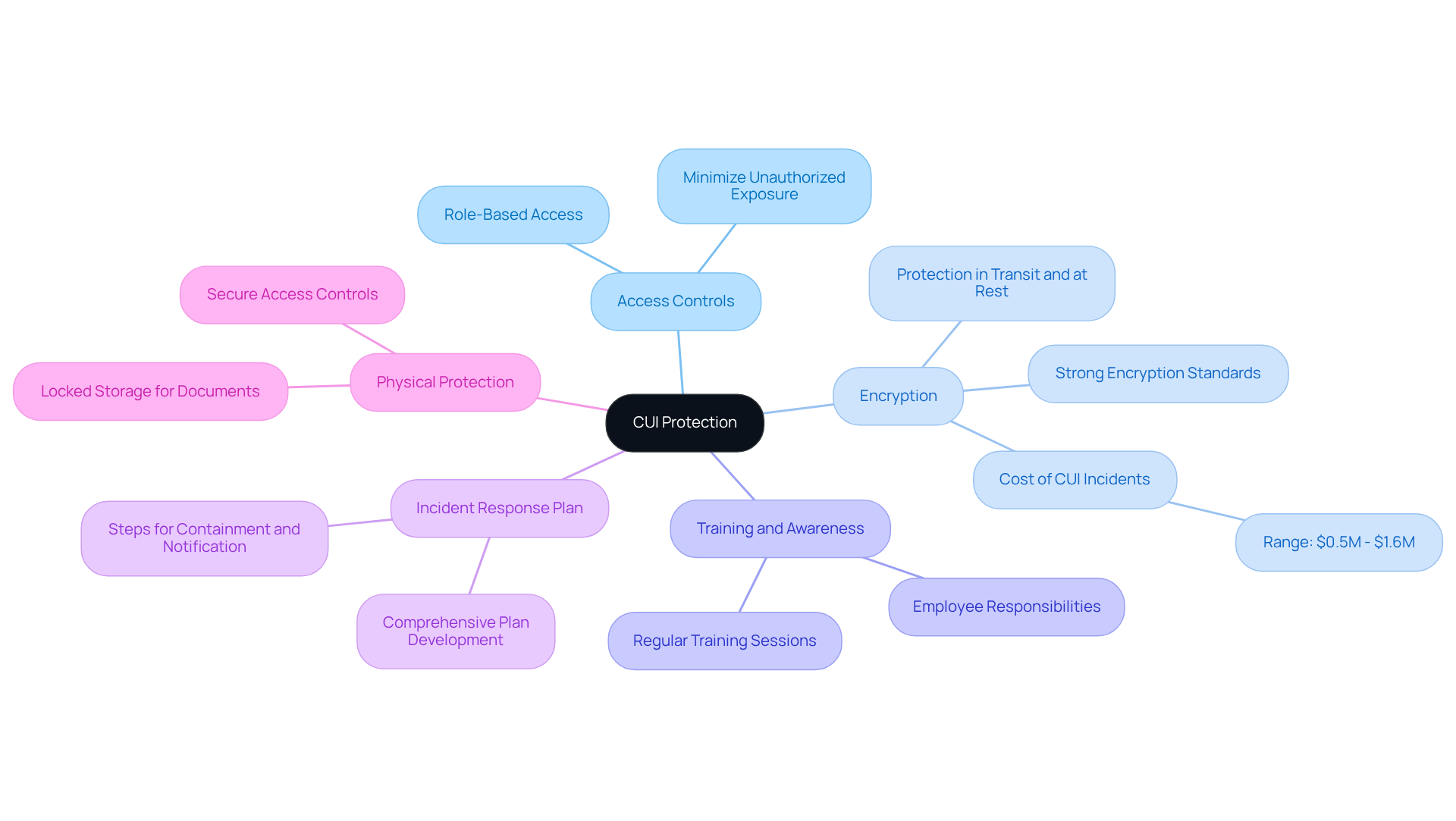
Implement Security Measures for CUI Protection
To effectively safeguard Controlled Unclassified Information (CUI), defense contractors must understand how to protect CUI by adopting essential security measures that not only protect sensitive data but also ensure compliance with federal regulations. Here are the key practices to implement:
-
Access Controls: Implement role-based access controls to restrict CUI access to authorized personnel only. This ensures that employees can only view information necessary for their specific job functions, minimizing the risk of unauthorized exposure.
-
Encryption: Utilize strong encryption standards to protect CUI both in transit and at rest. This is crucial for preventing unauthorized access and ensuring that sensitive data remains secure against potential breaches. Did you know that the cost of a serious CUI incident can range from $0.5 million to $1.6 million? This statistic underscores the importance of robust encryption practices.
-
Training and Awareness: Regularly conduct training sessions for employees focused on CUI handling and protective protocols. Ensuring that all staff members understand their responsibilities in protecting sensitive information is vital for maintaining a secure environment.
-
Incident Response Plan: Develop and maintain a comprehensive incident response plan to address potential data breaches involving CUI. This plan should clearly outline steps for containment, investigation, and notification, enabling a swift and effective response to incidents.
-
Physical Protection: Implement stringent physical protection measures, such as locked storage for physical documents containing CUI and secure access controls to facilities where CUI is processed. These measures are essential for preventing unauthorized physical access to sensitive information.
By adopting these best practices, defense contractors can significantly enhance their understanding of how to protect CUI. This not only reduces the risk of costly incidents but also maintains the integrity of sensitive data, ensuring adherence to federal regulations.
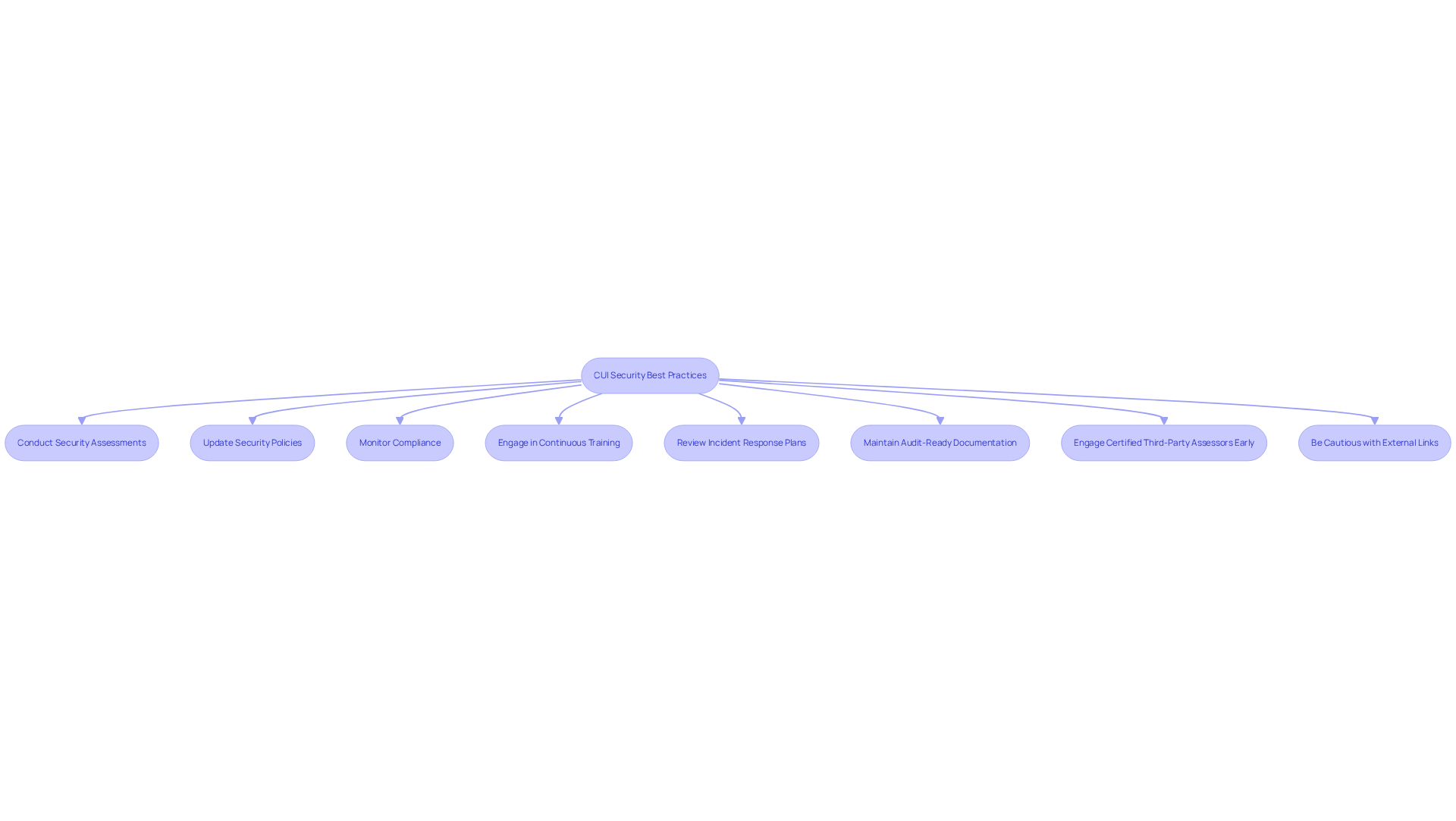
Conduct Regular Assessments and Updates for CUI Security
Regular assessments and updates are crucial for understanding how to protect CUI within defense contracting. To ensure compliance and enhance security, organizations should implement the following best practices:
-
Conduct Security Assessments: Regularly perform security assessments to evaluate the effectiveness of existing security measures. Employing frameworks like NIST SP 800-171 is essential for directing this assessment process, especially as regulatory requirements evolve.
-
Update Security Policies: Security policies and procedures must be reviewed and updated frequently to align with changes in regulations, technology, and organizational practices. This proactive approach helps mitigate risks associated with outdated protocols.
-
Monitor Compliance: Continuous monitoring of compliance with CUI safeguarding requirements is vital. Organizations should promptly address any identified gaps to maintain adherence to the latest standards. Remember, non-compliance can lead to significant penalties, including bid ineligibility.
-
Engage in Continuous Training: Ongoing training for employees is crucial to keep them informed about the latest protective practices and emerging threats related to CUI. Investing in human capital not only enhances knowledge but also strengthens the overall defense posture of the organization.
-
Review Incident Response Plans: Regular testing and updating of incident response plans ensure their effectiveness. Staff should be familiar with their roles during a security incident, which is critical for minimizing damage and ensuring a swift recovery.
-
Maintain Audit-Ready Documentation: Ensure that all documentation, including System Security Plans and incident response records, is kept up to date and readily available for audits. This is essential for demonstrating adherence to CMMC requirements.
-
Engage Certified Third-Party Assessors Early: Involve certified third-party assessors in the adherence process as soon as possible to avoid scheduling risks and ensure thorough evaluations.
-
Be Cautious with External Links: When accessing additional resources, be aware that external links may lead to sites beyond our control. We do not endorse these sites and cannot guarantee their content or availability. Always verify the credibility of external resources before relying on them.
By adhering to these practices, defense contractors can maintain a robust security posture, which includes understanding how to protect CUI from unauthorized access and disclosure. As the landscape of cybersecurity continues to evolve, organizations that treat compliance as an ongoing program will be better positioned to adapt and thrive.
Conclusion
Understanding and protecting Controlled Unclassified Information (CUI) is not just important; it’s essential for defense contractors who handle sensitive data. While CUI is unclassified, mishandling it can lead to significant risks. Protecting CUI serves national security interests and ensures compliance with federal regulations, reinforcing the integrity of the defense contracting ecosystem.
This guide outlines key strategies for safeguarding CUI.
- Identify the relevant types of CUI.
- Implement robust security measures, including access controls and encryption.
- Conduct regular assessments to ensure ongoing protection.
Each of these measures plays a vital role in mitigating risks associated with unauthorized disclosure of sensitive information. Staying updated with evolving regulations and technologies is crucial for maintaining compliance and security.
In conclusion, the responsibility of protecting CUI lies firmly with defense contractors. A proactive and informed approach to data handling is necessary. By investing in comprehensive training, adhering to best practices, and regularly assessing security measures, organizations can protect their sensitive information and contribute to the broader mission of national security. It’s imperative for all stakeholders in the defense industry to prioritize CUI protection, ensuring a secure and resilient environment for everyone involved.
Frequently Asked Questions
What is Controlled Unclassified Information (CUI)?
Controlled Unclassified Information (CUI) refers to unclassified information created or possessed by the U.S. government or entities acting on its behalf that requires specific safeguarding or dissemination controls due to its sensitivity.
Why is CUI important?
CUI is important because unauthorized disclosure of this information could potentially harm national security or other vital interests, making its protection essential.
What types of information are considered CUI?
CUI encompasses various types of information, including technical data, proprietary information, and personal data, all of which must be protected according to federal regulations.
How can organizations ensure compliance with CUI requirements?
Organizations can ensure compliance by familiarizing themselves with the CUI categories outlined in the CUI Registry and implementing the necessary safeguarding requirements.
What is the CUI Registry?
The CUI Registry is a resource that outlines the categories of CUI and provides guidance on how to protect such information in accordance with federal regulations.
How does protecting CUI enhance national security?
Protecting CUI safeguards sensitive information, which in turn helps to enhance national security by preventing unauthorized access and potential threats.




