Master Asymmetric Encryption: Key Insights for Defense Contractors
Enhance cybersecurity with key insights on asymmetric encryption for defense contractors.

Introduction
In today's rapidly evolving digital landscape, robust cybersecurity measures are more critical than ever, especially for defense contractors managing sensitive information. Asymmetric encryption stands out as a powerful public-key cryptography method that not only secures communications but also plays a pivotal role in meeting regulatory compliance standards. With cyber threats becoming increasingly sophisticated, one must ask: how can defense contractors effectively implement and integrate asymmetric encryption to bolster their security posture while navigating the complexities of modern data protection?
This question is not just a matter of compliance; it’s about safeguarding vital information and maintaining trust in an era where data breaches can have devastating consequences. By understanding the intricacies of asymmetric encryption and its application, defense contractors can enhance their security frameworks and ensure they meet the stringent requirements of regulatory bodies.
As we delve deeper into this topic, we will explore actionable insights and strategies that can empower defense contractors to take decisive steps towards fortifying their cybersecurity measures.
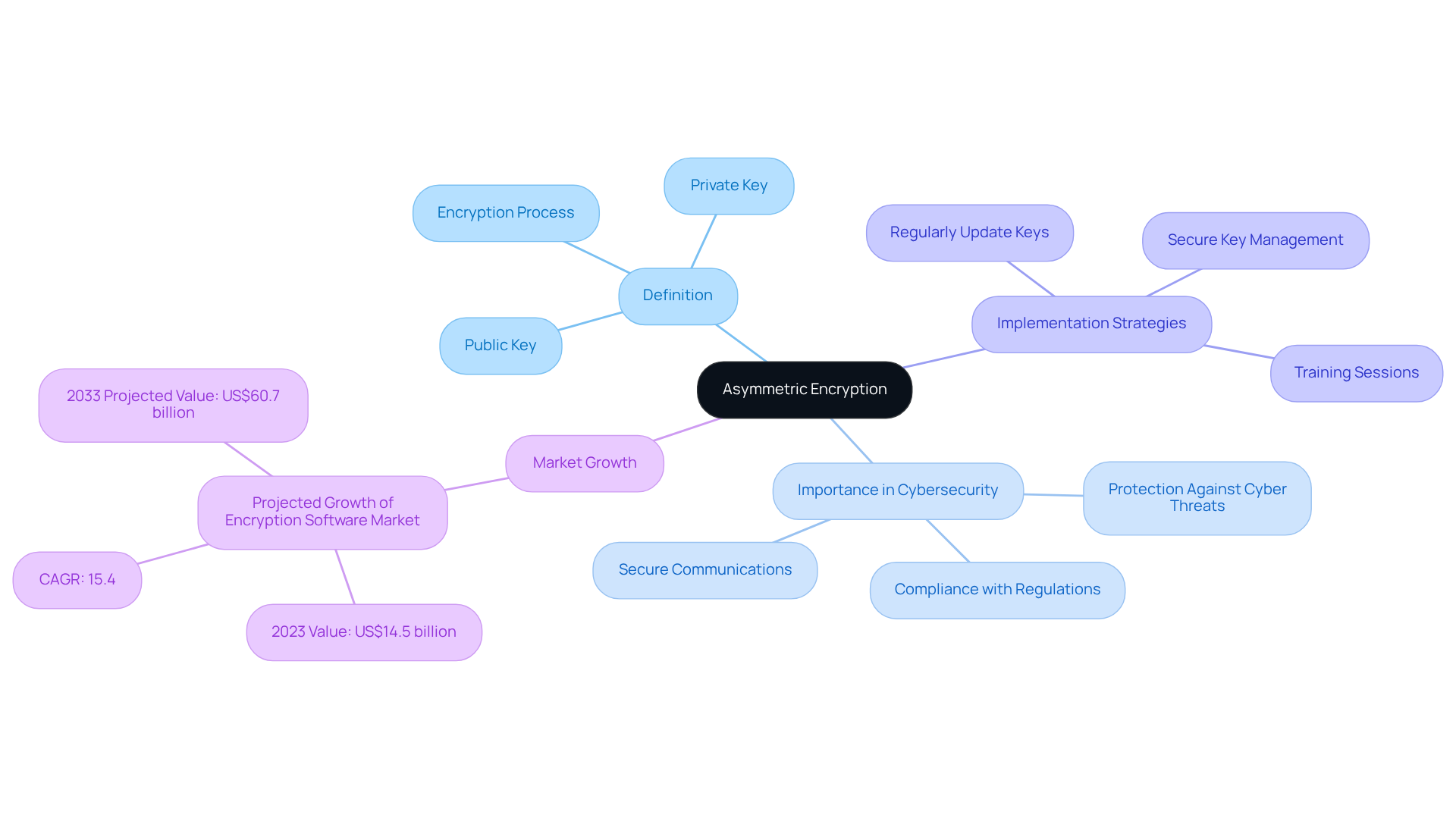
Define Asymmetric Encryption and Its Importance in Cybersecurity
Asymmetric encryption, commonly known as public-key cryptography, utilizes a dual-key system consisting of a public key that can be freely shared and a private key that is kept confidential by its owner. This innovative approach significantly enhances security by utilizing asymmetric encryption, allowing users to encrypt data with the public key, ensuring that only the holder of the corresponding private key can decrypt it. Why is this important? In the realm of cybersecurity, especially for contractors, it enables secure communications over potentially insecure channels, such as the internet.
To effectively implement asymmetric cryptography, defense contractors should consider several practical strategies:
- Regularly update cryptographic keys.
- Utilize secure key management practices.
- Conduct training sessions to ensure all personnel understand the importance of cryptography in safeguarding sensitive information.
Recent advancements in asymmetric encryption have further solidified its role as a cornerstone of modern data protection strategies, particularly in light of increasing cyber threats. For instance, the data protection software market is projected to grow from US$14.5 billion in 2023 to US$60.7 billion by 2033, reflecting a compound annual growth rate of 15.4%. This growth underscores the rising significance of data protection technologies in securing sensitive information and ensuring compliance with stringent regulatory standards set by the Department of Defense (DoD).
Experts emphasize that implementing robust security measures is not merely a technical requirement; it is a strategic necessity for defense contractors aiming to protect their information and maintain trust in their operations. Are you ready to take action and enhance your cybersecurity measures?
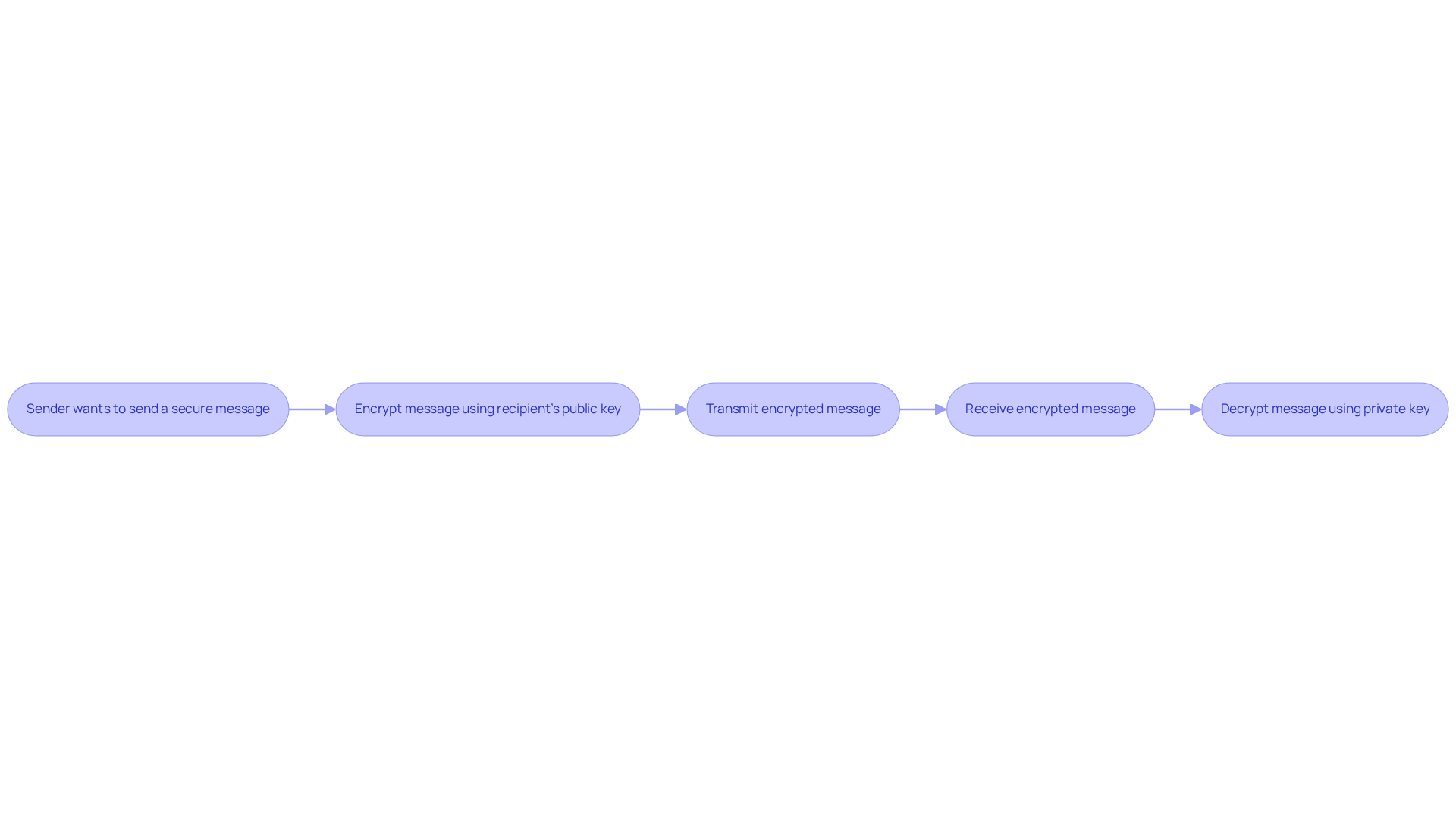
Explain How Asymmetric Encryption Functions: Key Pair Dynamics
Asymmetric encryption is a cornerstone of secure communication, relying on a mathematical relationship between public and private keys. When a sender wants to transmit a secure message, they encrypt the information using the recipient's public key. This method guarantees that only the recipient, who holds the corresponding private key, can decrypt the message. The security of this system hinges on the complexity of deriving the private key from the public key, a principle grounded in challenging mathematical problems. For example, RSA (Rivest-Shamir-Adleman) is a prominent example of asymmetric encryption that illustrates this principle.
Understanding this dynamic is crucial for contractors. It not only fortifies the security of communications and data exchanges but also plays a vital role in achieving CMMC compliance. By grasping these concepts, contractors can turn confusion into clarity, ensuring they meet essential cybersecurity standards.
To enhance compliance further, contractors should consider:
- Implementing regular training sessions focused on data protection techniques.
- Collaborating with colleagues to share insights on effective security strategies.
Are you ready to take the necessary steps to safeguard your communications and achieve compliance?
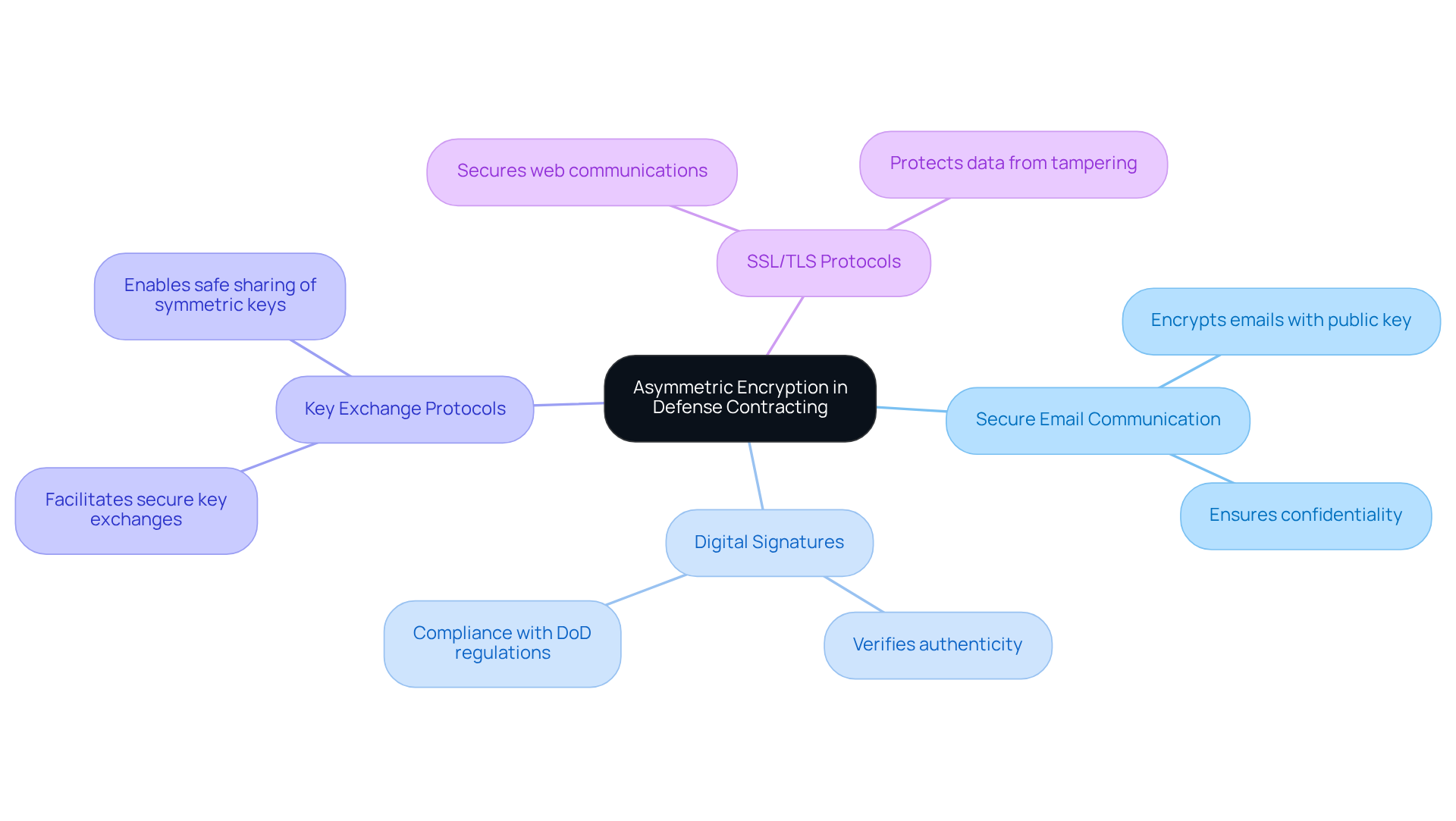
Identify Use Cases for Asymmetric Encryption in Defense Contracting
Asymmetric encryption plays a crucial role in defense contracting, serving various essential functions:
-
Secure Email Communication: By encrypting emails with the recipient's public key, only the intended recipient can access the message. This method effectively protects sensitive information from interception, ensuring confidentiality.
-
Digital Signatures: Organizations can verify the authenticity and integrity of documents by signing them with a private key. This practice is vital for compliance with Department of Defense (DoD) regulations, reinforcing trust in communications.
-
Key Exchange Protocols: Asymmetric encryption facilitates secure key exchanges, allowing parties to share symmetric keys safely for bulk information encoding. This process is fundamental in maintaining secure communications.
-
SSL/TLS Protocols: Underpinning secure web communications, asymmetric encryption ensures that data transmitted over the internet remains confidential and tamper-proof, safeguarding critical information.
These applications illustrate the versatility and necessity of asymmetric encryption in upholding robust cybersecurity practices within defense contracting. By implementing these strategies, organizations can enhance their security posture and ensure compliance with industry standards.
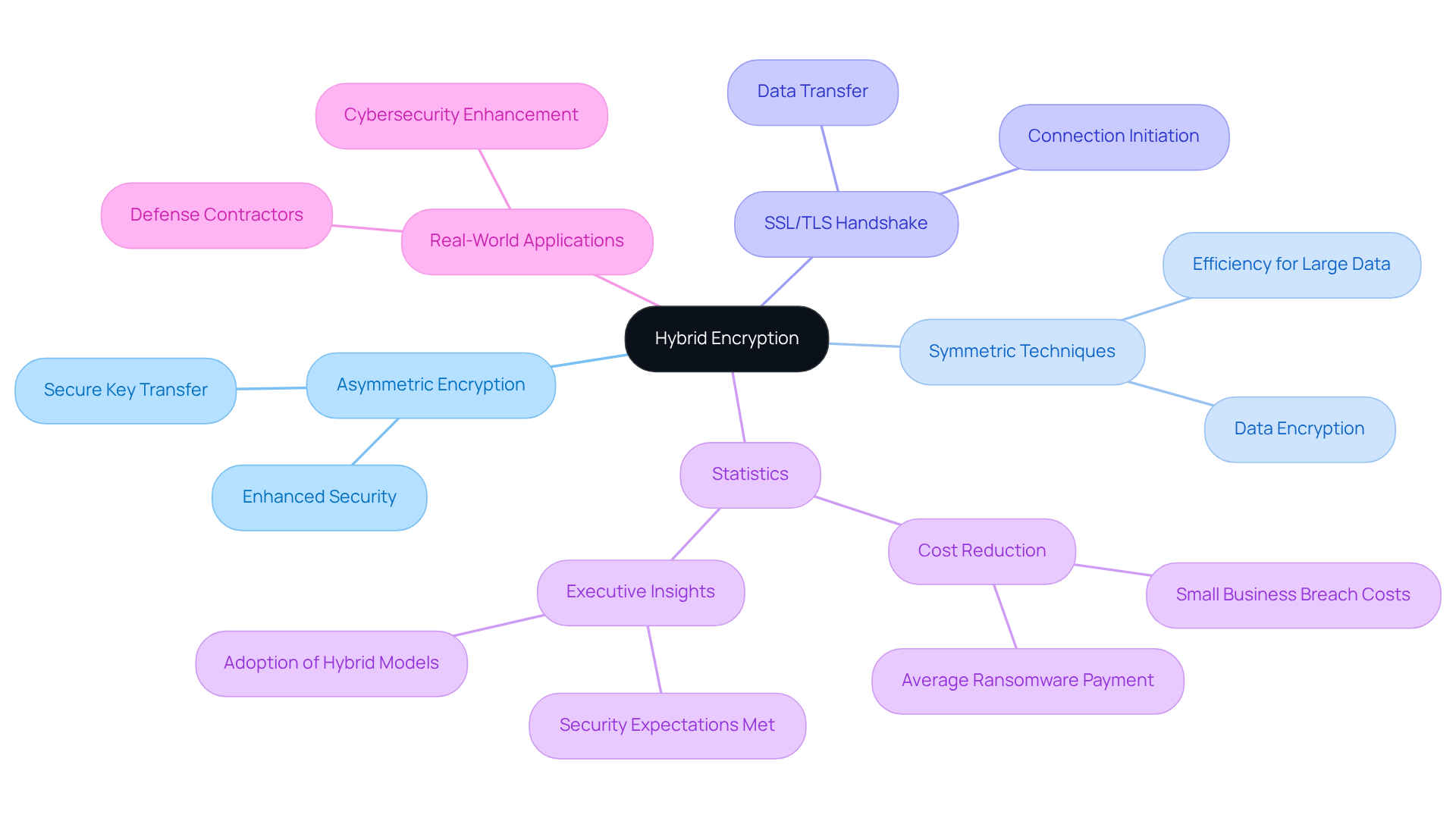
Integrate Asymmetric Encryption with Symmetric Methods for Enhanced Security
The integration of asymmetric encryption with symmetric techniques establishes a robust security framework that capitalizes on the strengths of both methods. In this hybrid model, asymmetric encryption primarily facilitates the secure transfer of symmetric keys, which are subsequently employed to encrypt the actual data. This synergy harnesses the efficiency of symmetric techniques - ideal for managing large data volumes - alongside the enhanced security provided by asymmetric encryption methods, which safeguard key exchanges.
Consider the SSL/TLS handshake: here, asymmetric encryption initiates a secure connection through key exchange, after which symmetric cryptography takes over for the transfer of information. This integration is particularly vital for defense contractors, as it not only ensures adherence to stringent security standards but also optimizes performance.
Statistics reveal that organizations employing hybrid coding models experience a significant reduction in data breach costs, with the average expense of a breach for small businesses ranging from $120,000 to $1.24 million. Furthermore, 93% of executives believe that adopting advanced coding methods, including hybrid models, has met or exceeded their security expectations.
Real-world applications of hybrid encryption in defense contracting underscore its effectiveness in safeguarding sensitive information, thereby bolstering overall cybersecurity posture. Are you ready to enhance your security measures? Embracing hybrid encryption could be the key to protecting your organization.
Conclusion
Asymmetric encryption is a cornerstone of cybersecurity, especially for defense contractors. By utilizing a dual-key system, it guarantees secure communication over insecure channels, protecting sensitive information vital to national security. This method not only strengthens data protection but also meets compliance standards set by regulatory bodies, underscoring the need for defense contractors to implement these advanced cryptographic solutions.
This article has explored the functionality of asymmetric encryption, its various applications in defense contracting, and how it strategically integrates with symmetric methods to enhance security. From securing email communications and enabling digital signatures to facilitating key exchanges and supporting SSL/TLS protocols, the versatility of asymmetric encryption is undeniable. Moreover, the importance of robust key management practices and ongoing training is crucial for ensuring the effectiveness of these security measures.
Given the escalating complexity of cyber threats, adopting advanced cryptographic techniques is not merely advisable; it is essential. Defense contractors must act decisively: by embracing asymmetric encryption alongside symmetric methods, organizations can significantly bolster their cybersecurity posture, safeguard sensitive information, and uphold trust in their operations. The time to act is now; the security of critical data and adherence to industry standards hinge on this imperative.
Frequently Asked Questions
What is asymmetric encryption?
Asymmetric encryption, also known as public-key cryptography, is a method that uses a dual-key system consisting of a public key, which can be shared freely, and a private key, which is kept confidential by its owner.
How does asymmetric encryption enhance security?
It allows users to encrypt data with the public key, ensuring that only the holder of the corresponding private key can decrypt it, thereby significantly enhancing security in communications.
Why is asymmetric encryption important in cybersecurity?
It is crucial for secure communications over potentially insecure channels, such as the internet, especially for contractors who need to protect sensitive information.
What practical strategies should defense contractors consider for implementing asymmetric cryptography?
Defense contractors should regularly update cryptographic keys, utilize secure key management practices, and conduct training sessions to ensure personnel understand the importance of cryptography.
What is the projected growth of the data protection software market?
The data protection software market is projected to grow from US$14.5 billion in 2023 to US$60.7 billion by 2033, reflecting a compound annual growth rate of 15.4%.
Why is the implementation of robust security measures essential for defense contractors?
Implementing robust security measures is a strategic necessity for defense contractors to protect their information and maintain trust in their operations, especially in light of increasing cyber threats.