Master Audit Risk Management: Best Practices for Defense Contractors
Discover best practices for effective audit risk management tailored for defense contractors.

Introduction
In the intricate world of defense contracting, understanding and managing audit risk is not merely a regulatory obligation; it’s a vital element of operational success. As frameworks like the Cybersecurity Maturity Model Certification (CMMC) evolve, they reshape compliance standards, presenting both challenges and opportunities for defense contractors.
How can organizations not only meet these compliance requirements but also bolster their resilience against emerging threats? This article explores essential strategies for mastering audit risk management, providing insights that empower defense contractors to excel in a demanding regulatory landscape.
Understand Regulatory Frameworks for Audit Risk Management
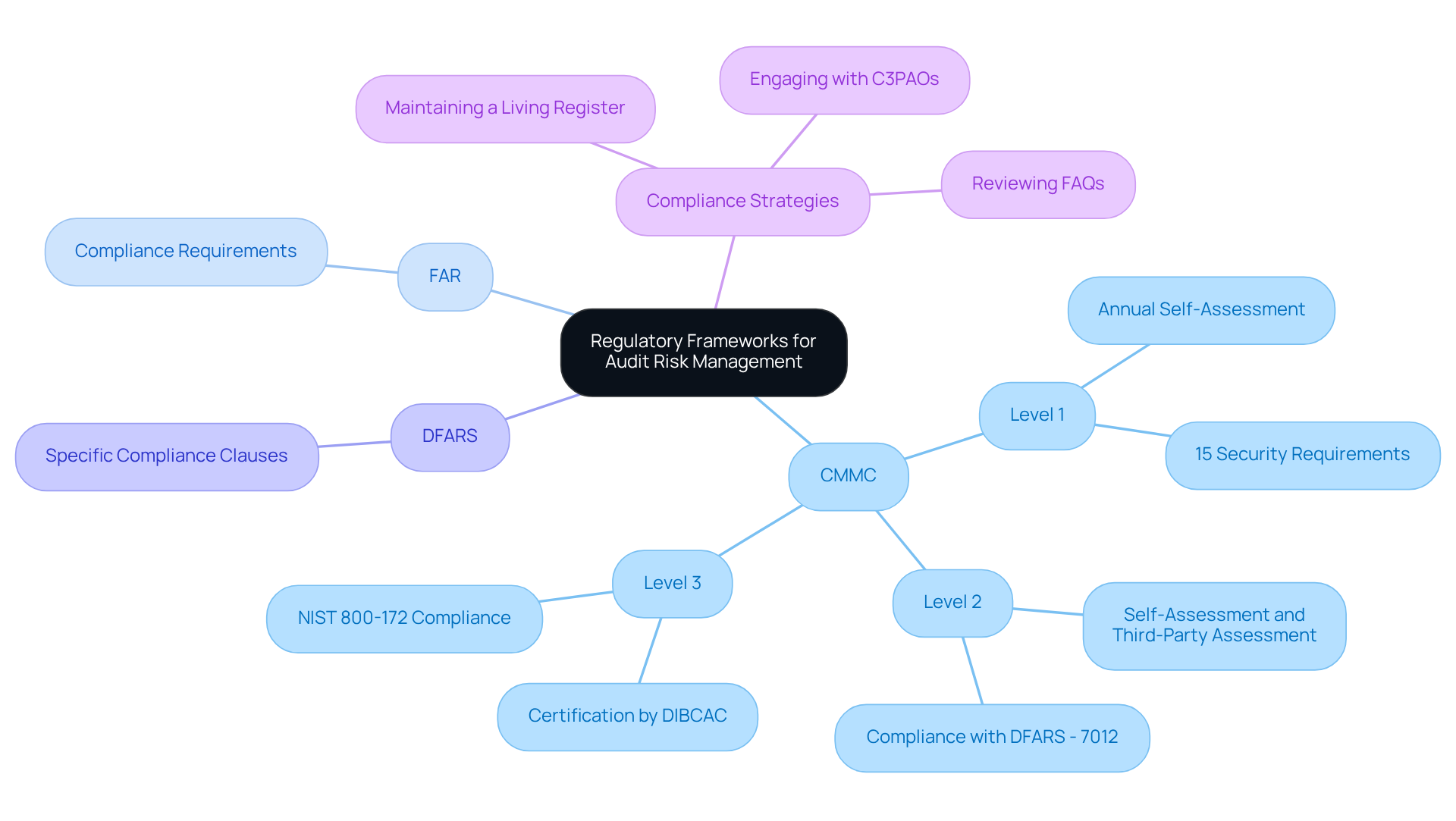
To effectively manage audit risk management, defense firms must first grasp the regulatory frameworks that govern their operations. The Cybersecurity Maturity Model Certification (CMMC) stands as a crucial standard, outlining the cybersecurity practices necessary for defense suppliers. Understanding the CMMC levels - ranging from basic cyber hygiene to advanced security practices - is vital. Furthermore, contractors should familiarize themselves with other regulations, such as the Federal Acquisition Regulation (FAR) and the Defense Federal Acquisition Regulation Supplement (DFARS), which impose specific compliance requirements.
Grasping these frameworks allows organizations to align their compliance strategies with regulatory expectations, significantly enhancing audit risk management and reducing the risk of non-adherence during evaluations. For instance, maintaining a living register of potential issues, updated every three months, can help organizations stay compliant and demonstrate their commitment to regulatory adherence during evaluations.
Moreover, defense contractors are encouraged to review FAQs regarding CMMC compliance and leverage external resources for additional support. This thorough approach to oversight challenges not only enhances compliance but also fosters a culture of accountability and diligence within the organization.
Implement Effective Risk Assessment Strategies
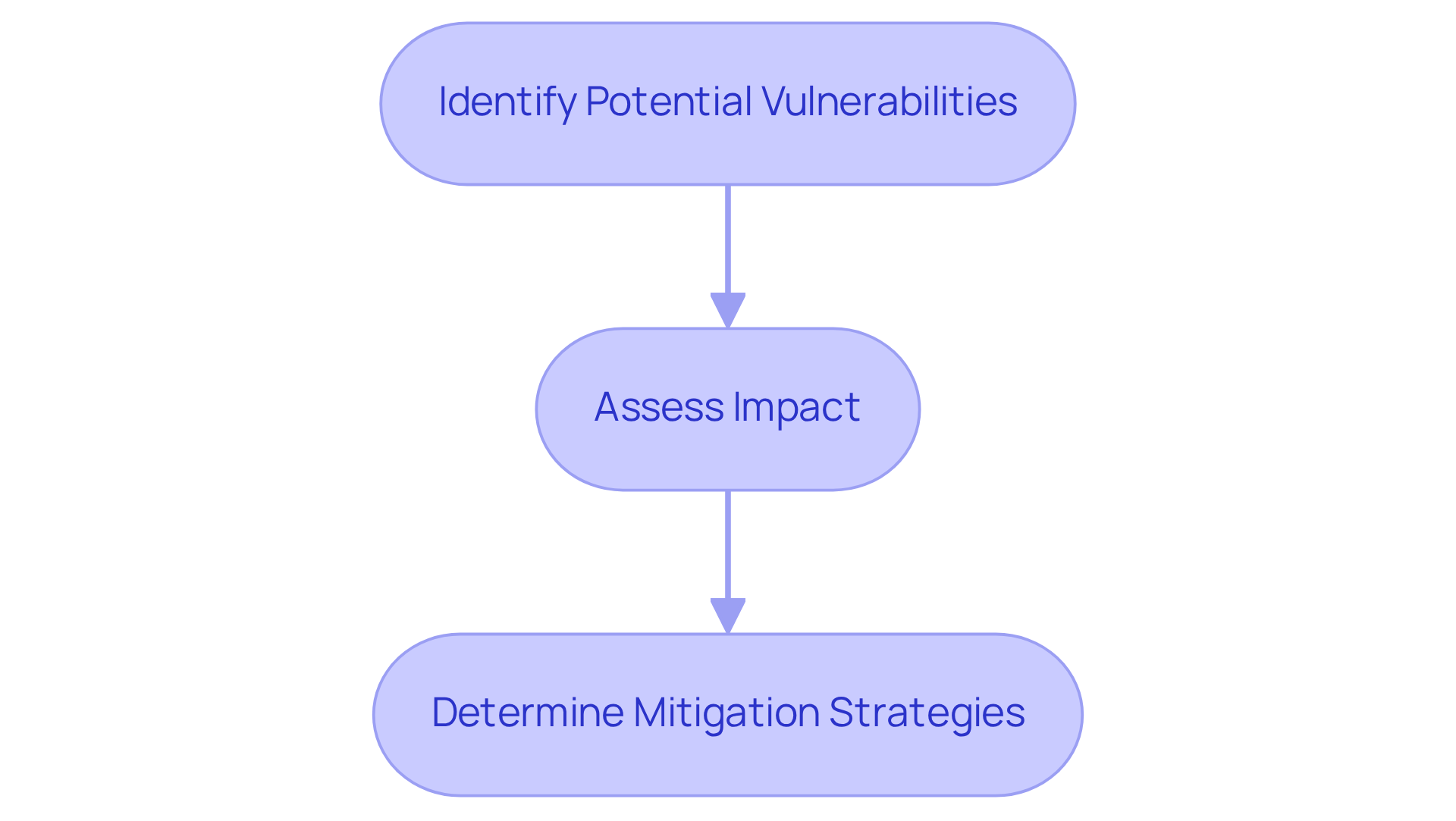
Effective threat evaluation strategies are essential for a robust audit risk management plan. Contractors must recognize potential issues early in the project lifecycle, particularly during the proposal stage. Have you considered how a danger matrix can help prioritize threats based on their potential impact and likelihood? As Warren Buffett wisely noted, "Danger arises from not understanding what you’re doing," underscoring the necessity of grasping uncertainties in project management.
Frequent vulnerability evaluations and active participation in audit risk management can significantly enhance threat identification. For instance, a contractor might implement a three-step vulnerability assessment process:
- Identifying potential vulnerabilities
- Assessing their impact
- Determining appropriate mitigation strategies
Furthermore, the Department of Defense's new threat oversight framework emphasizes automation and continuous monitoring, simplifying these processes.
Designating responsibility for uncertainties to specific team members ensures accountability and fosters a culture of proactive oversight. By formalizing these strategies, organizations can create a comprehensive threat profile that not only aids in compliance but also enhances overall operational resilience. Are you ready to take action and implement these strategies for a more secure project environment?
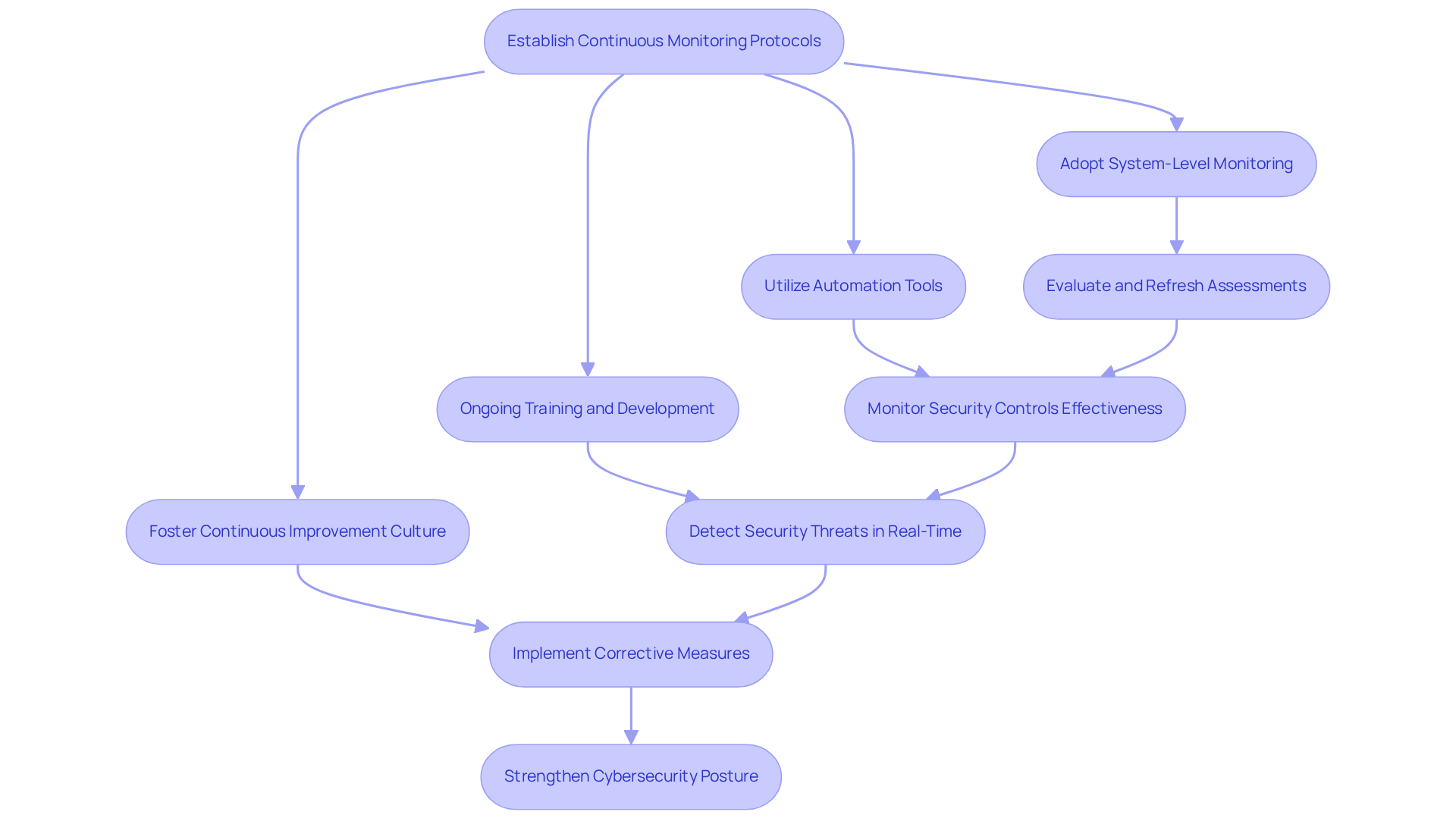
Establish Continuous Monitoring and Improvement Protocols
Ongoing observation and enhancement are vital for a successful oversight management strategy. Organizations must adopt a system-level continuous monitoring approach to ensure that security controls remain effective over time. This involves regularly evaluating and refreshing assessments, as well as utilizing automation tools to improve monitoring procedures.
For example, contractors can leverage platforms like IPKeys Cyber-Lab-as-a-Service (CLaaS)®, which provides near real-time insights into compliance status and risk exposure. This innovation significantly reduces preparation time from six weeks to just three days.
Moreover, fostering a culture of continuous improvement encourages teams to consistently review evaluation results and implement corrective measures swiftly. Prioritizing ongoing training and development equips staff to adapt to evolving regulations and emerging threats. This proactive approach not only enhances compliance but also strengthens the overall cybersecurity posture of the organization.
As cybersecurity professionals emphasize, continuous monitoring allows organizations to detect potential security threats in real-time. This capability enables swift and effective responses, ultimately leading to a remarkable 40% reduction in compliance-related costs compared to traditional audit methods.
Is your organization ready to embrace this proactive strategy? By investing in continuous monitoring and improvement, you can not only meet compliance requirements but also fortify your defenses against ever-evolving cyber threats.
Conclusion
Mastering audit risk management is crucial for defense contractors who need to navigate the complexities of regulatory compliance and security threats. Understanding the intricate regulatory frameworks and implementing effective risk assessment strategies can significantly strengthen defenses against potential audit failures and cybersecurity threats.
Key insights in this article highlight the necessity of grasping regulations such as the Cybersecurity Maturity Model Certification (CMMC) and the Federal Acquisition Regulation (FAR). Establishing continuous monitoring and improvement protocols is vital to ensure that defense contractors stay vigilant and responsive to evolving challenges. By prioritizing proactive measures like regular vulnerability assessments and leveraging automation tools, organizations can develop a resilient audit risk management strategy that not only meets compliance requirements but also enhances overall operational effectiveness.
Ultimately, the journey to successful audit risk management hinges on a commitment to continuous improvement and accountability. Defense contractors should adopt these best practices and cultivate a culture of diligence within their teams. This approach not only safeguards their operations but also contributes to the broader goal of enhancing security across the defense industry. Embracing these strategies will pave the way for a more secure and compliant future in an increasingly complex regulatory landscape.
Frequently Asked Questions
What is the importance of understanding regulatory frameworks in audit risk management for defense firms?
Understanding regulatory frameworks is crucial for defense firms to effectively manage audit risk, as it helps align their compliance strategies with regulatory expectations and reduces the risk of non-adherence during evaluations.
What is the Cybersecurity Maturity Model Certification (CMMC)?
The CMMC is a standard that outlines the necessary cybersecurity practices for defense suppliers, ranging from basic cyber hygiene to advanced security practices.
What are the levels of the CMMC?
The CMMC levels range from basic cyber hygiene practices to advanced security practices, each level representing a different degree of cybersecurity maturity.
What other regulations should contractors familiarize themselves with besides CMMC?
Contractors should also familiarize themselves with the Federal Acquisition Regulation (FAR) and the Defense Federal Acquisition Regulation Supplement (DFARS), which impose specific compliance requirements.
How can organizations demonstrate their commitment to regulatory adherence?
Organizations can maintain a living register of potential issues, updated every three months, to help stay compliant and demonstrate their commitment to regulatory adherence during evaluations.
What additional resources are available for defense contractors regarding CMMC compliance?
Defense contractors are encouraged to review FAQs regarding CMMC compliance and leverage external resources for additional support in understanding and meeting compliance requirements.
How does a thorough approach to oversight benefit defense contractors?
A thorough approach to oversight enhances compliance, fosters a culture of accountability and diligence within the organization, and helps address oversight challenges effectively.