Master Cyber Security Compliance Software: Best Practices for Defense Contractors
Explore best practices for selecting and implementing cyber security compliance software for defense contractors.

Introduction
Navigating the intricate landscape of defense contracting demands a solid grasp of cybersecurity compliance, especially as regulations continue to evolve. Organizations must not only become well-versed in the Cybersecurity Maturity Model Certification (CMMC) but also choose and implement the appropriate compliance software to meet rigorous standards. Alarmingly, many defense contractors remain unaware of these critical requirements. This knowledge gap presents a significant challenge, underscoring the necessity for effective integration of compliance solutions.
What best practices can organizations adopt to enhance awareness, streamline software selection, and optimize ongoing compliance efforts in this vital sector? By addressing these questions, we can pave the way for a more secure and compliant future.
Understand Cybersecurity Compliance Requirements for Defense Contracts
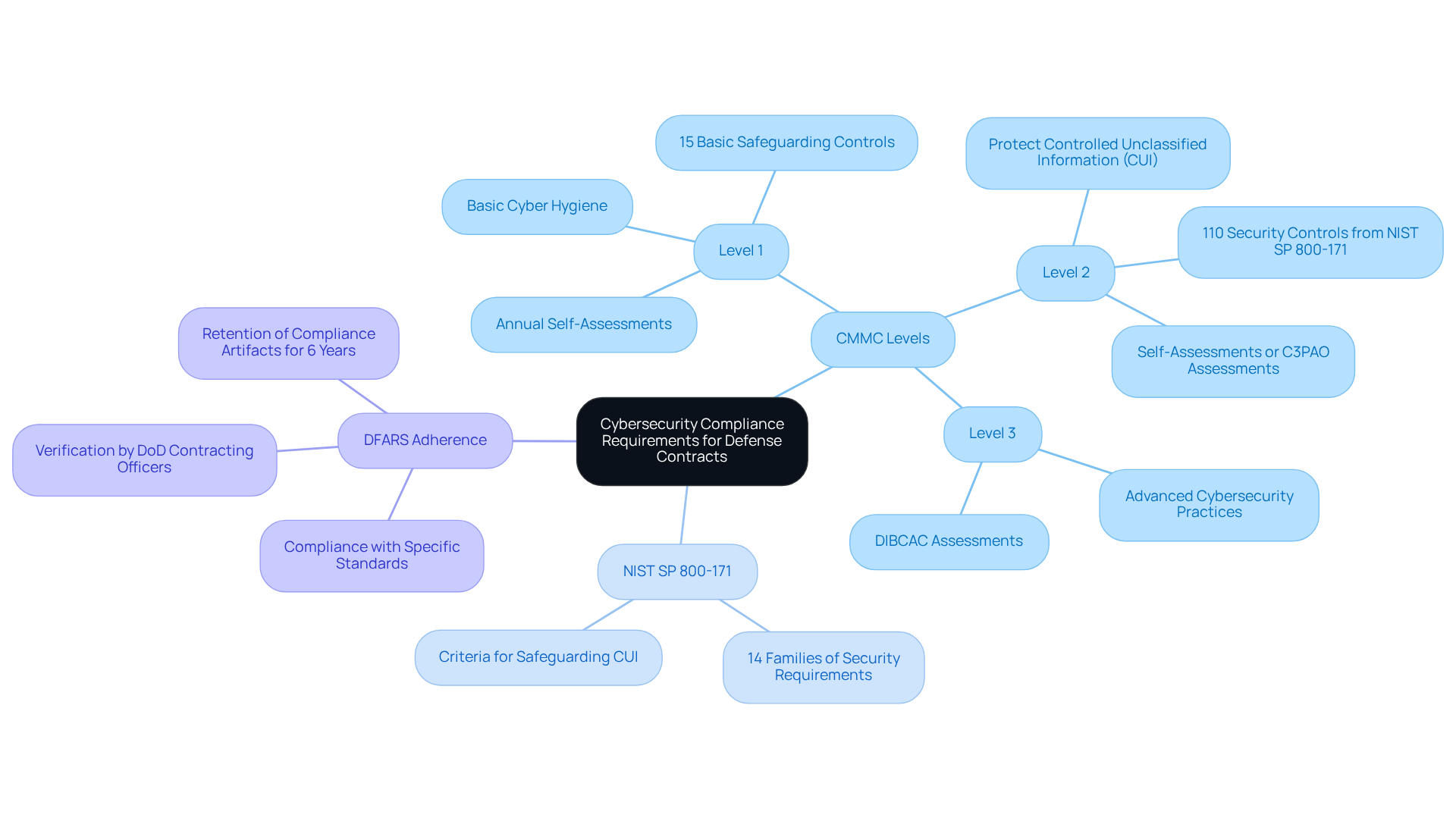
To effectively navigate the landscape of defense contracting, organizations must first grasp the specific requirements for cyber security compliance software set forth by the Department of Defense (DoD). Understanding the Cybersecurity Maturity Model Certification (CMMC) framework is crucial, as it outlines the necessary practices and processes for safeguarding Controlled Unclassified Information (CUI) through the implementation of cyber security compliance software.
Key components include:
- CMMC Levels: It's essential to understand the tiered levels of CMMC, ranging from Level 1 (basic cyber hygiene) to Level 5 (advanced/progressive). Each level has specific practices and processes that must be implemented.
- NIST SP 800-171: This standard details the criteria for safeguarding CUI and is a vital element of CMMC adherence. Organizations should familiarize themselves with the 14 families of security requirements outlined in the cyber security compliance software document.
- DFARS Adherence: The Defense Federal Acquisition Regulation Supplement (DFARS) mandates adherence to specific cybersecurity standards for defense contractors. Understanding these regulations is vital for maintaining eligibility for government contracts through the use of cyber security compliance software.
As of 2026, a significant percentage of defense contractors remain unfamiliar with the cybersecurity maturity model certification framework. This highlights the urgent need for increased awareness and education. Practical instances show that organizations actively engaging with security standards not only improve their readiness for regulations but also strengthen their overall cybersecurity posture. By understanding these criteria, organizations can enhance their preparedness for regulatory evaluations and position themselves advantageously in the competitive defense contracting environment.
Select Tailored Cybersecurity Compliance Software Solutions
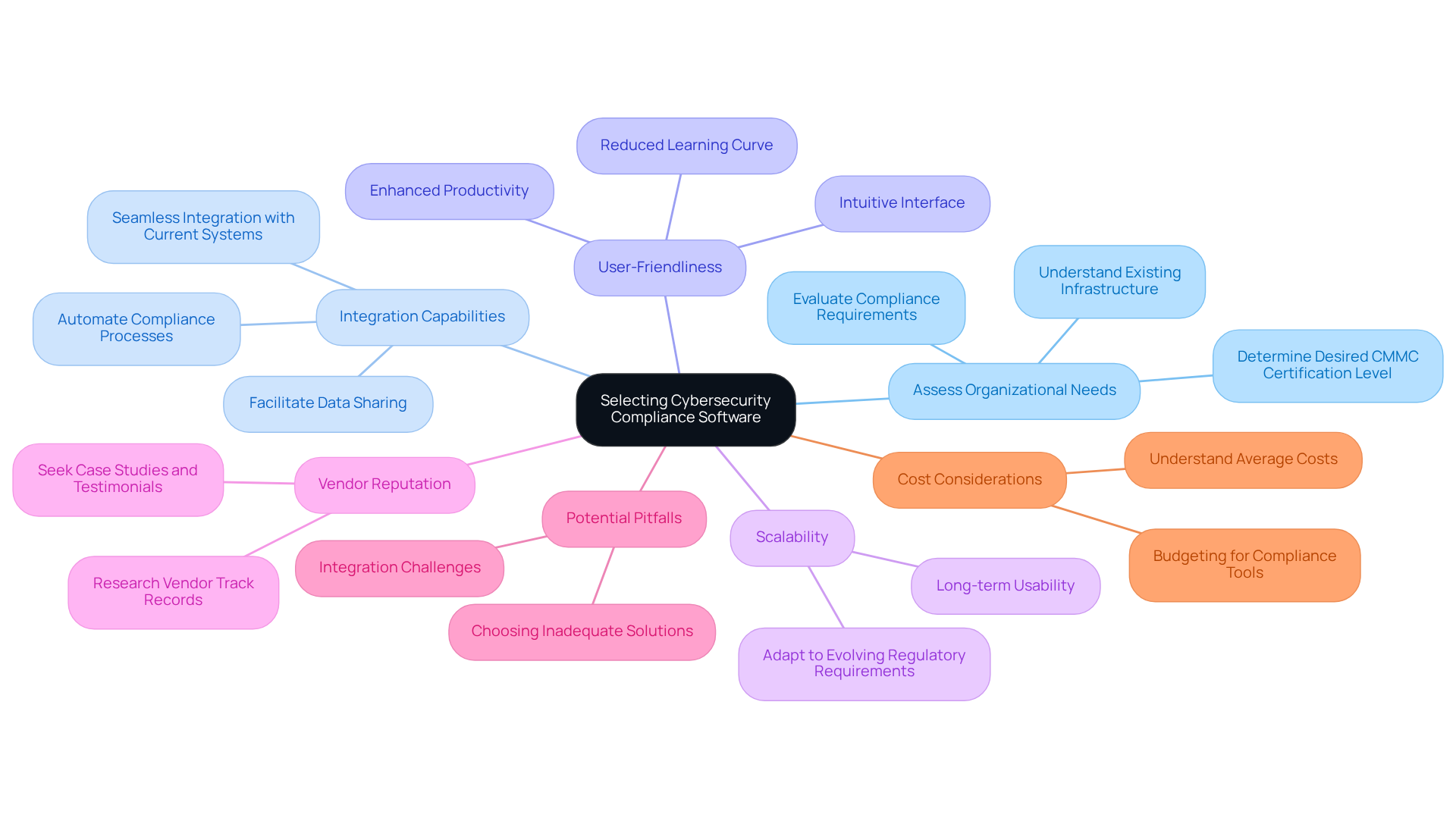
Choosing the right cyber security compliance software is crucial for defense contractors who want to effectively meet security standards. To turn confusion into clarity and achieve compliance with confidence, consider these essential strategies:
- Assess Organizational Needs: Begin by evaluating your organization's specific compliance requirements, existing infrastructure, and the desired level of CMMC certification. This assessment will guide your program selection process and clarify your path forward.
- Integration Capabilities: Ensure the software can seamlessly integrate with your current systems and processes. This capability facilitates data sharing and simplifies regulatory workflows by utilizing cyber security compliance software, thereby reducing complexity. Automating compliance processes through cyber security compliance software can save time and minimize human error, making integration vital for clarity in compliance efforts.
- User-Friendliness: Opt for applications that feature an intuitive and easy-to-navigate interface. A user-friendly design can significantly reduce the learning curve for your team, enhancing overall productivity and confidence in using the application.
- Scalability: Select solutions that can grow alongside your organization. As regulatory requirements evolve, your cyber security compliance software should adapt without necessitating a complete redesign, ensuring long-term usability and clarity in future regulatory strategies.
- Vendor Reputation: Conduct thorough research on potential vendors and their track records within the defense contracting sector. Seek out case studies or testimonials from similar organizations to evaluate their effectiveness and reliability. For instance, NeQter Labs offers a unified platform that centralizes regulatory components, simplifying the regulatory process for contractors.
- Potential Pitfalls: Be aware of common obstacles in selecting regulatory tools, such as the risk of choosing a solution that doesn't fully meet your needs or fails to integrate effectively with existing systems. This can lead to increased complexity and inefficiencies, making it essential to approach the selection process with clarity.
- Cost Considerations: Understanding the average costs associated with regulatory tools is crucial for budgeting. For example, the expenses related to SOC 2 Type 1 preparation and certification can reach approximately $91,000 for firms with fewer than 50 employees, highlighting the need for a clear financial strategy.
By carefully selecting regulatory tools, such as cyber security compliance software, that align with your organizational needs, you can enhance your ability to meet CMMC requirements and bolster your cybersecurity posture.
Implement and Integrate Compliance Software Effectively
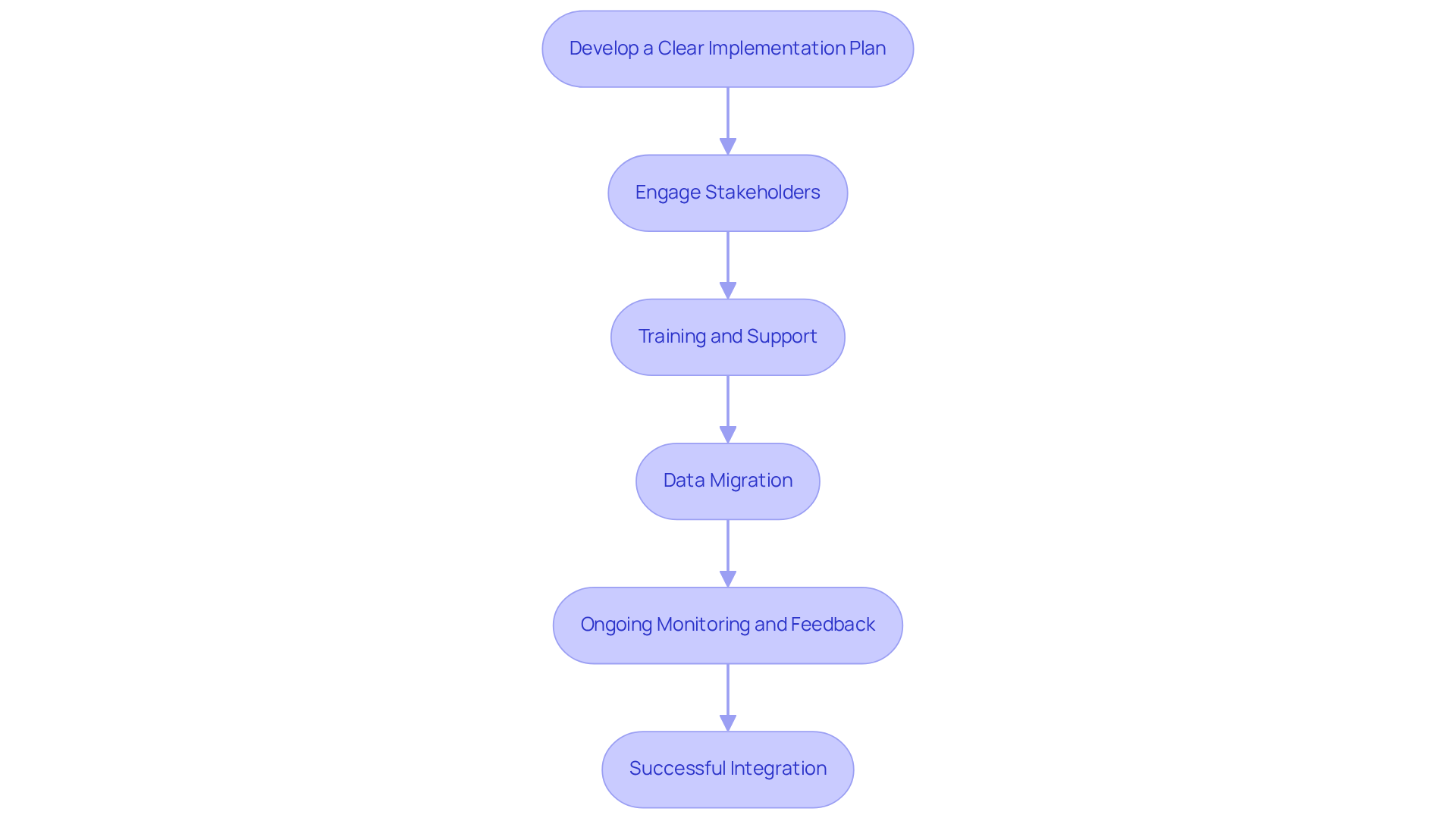
Once you've selected the right cyber security compliance software, effective implementation and integration become crucial for success. Here are best practices to ensure a smooth transition:
- Develop a Clear Implementation Plan: Start by outlining the necessary steps for implementation, including timelines, responsibilities, and milestones. A structured plan keeps the project on track and ensures accountability.
- Engage Stakeholders: Involve key stakeholders from various departments early in the process. Their insights can help identify potential challenges and ensure that the system meets the needs of all users. By engaging stakeholders, you promote a sense of ownership, which can significantly improve the adoption rate of the application.
- Training and Support: Comprehensive training for all users is essential to ensure they understand how to utilize the application effectively. Ongoing support should also be available to address any questions or issues that arise post-implementation. Research indicates that organizations with strong training programs see a notable enhancement in application usage and adherence results.
- Data Migration: Carefully plan the migration of existing data into the new system. It's vital to maintain data integrity and handle sensitive information securely during the transition. A well-executed data migration strategy minimizes disruptions and boosts user confidence in the new system.
- Ongoing Monitoring and Feedback: After implementation, consistently track the system's performance and collect feedback from users. This proactive approach helps identify areas for enhancement and ensures that the system remains compliant with regulatory standards. Regular feedback cycles can lead to iterative improvements, making the system more effective over time.
By following these best practices, organizations can ensure that their cyber security compliance software is effectively integrated into their operations, significantly enhancing their ability to meet CMMC standards.
Manage and Optimize Compliance Software for Continuous Improvement
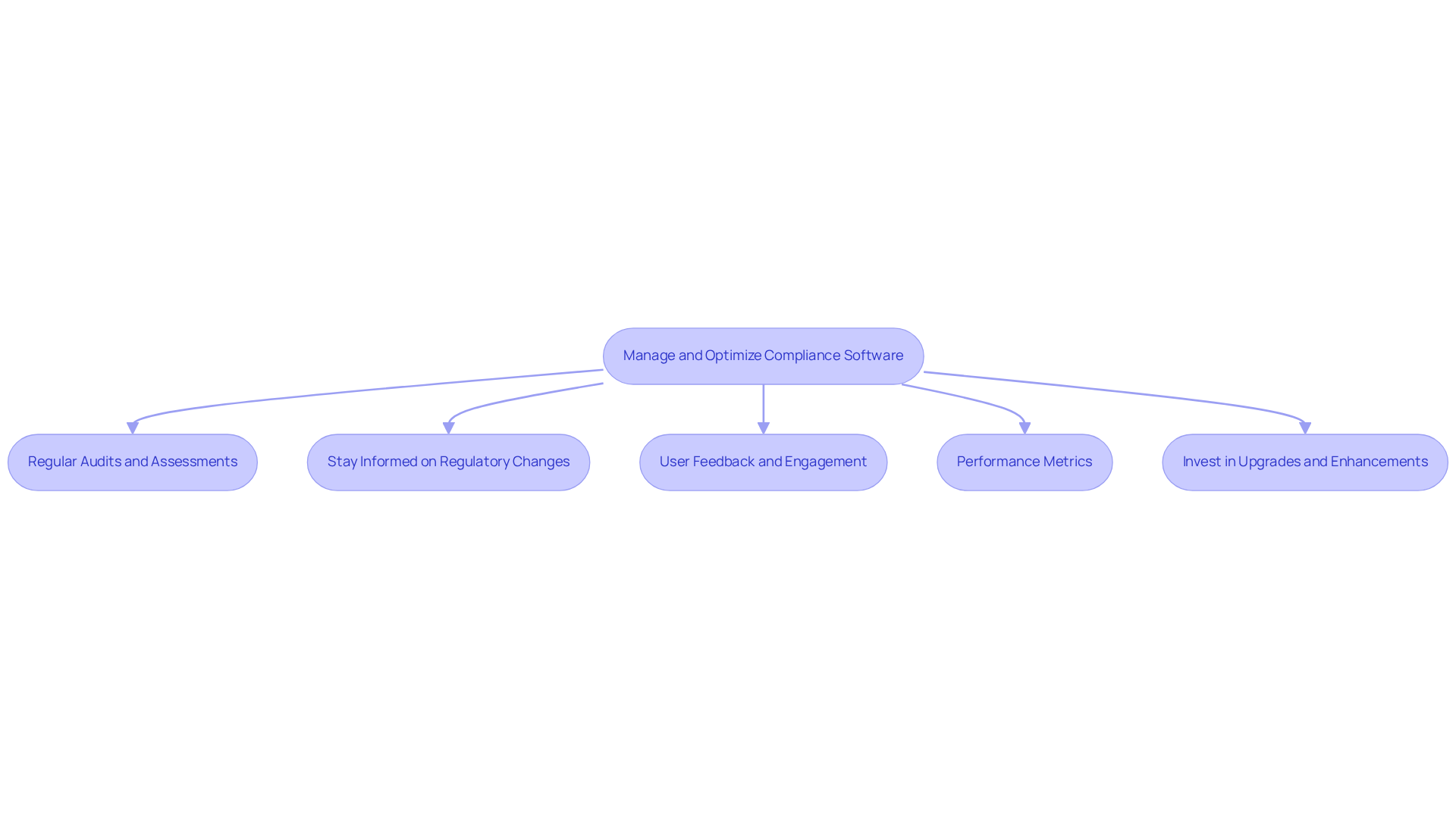
To uphold regulations and enhance your cybersecurity stance, it is essential to manage and optimize your cyber security compliance software continuously. Here are key strategies to achieve this:
-
Regular Audits and Assessments: Periodic audits of your compliance software are crucial to ensure it functions as intended and meets all regulatory requirements. This practice helps recognize gaps and areas for enhancement. Consider this: 80,000 defense contractors require Level 2 certification, yet only 270 currently possess final certification. As John Minnix, Co-Founder of Bright Defense, emphasizes, "The Defense Industrial Base is running out of time. Contractors that aren’t prepared will be locked out of billions in DOD contracts."
-
Stay Informed on Regulatory Changes: Keeping abreast of changes to CMMC requirements and other relevant regulations is imperative. By 2026, regulatory experts will face significant challenges due to overlapping regulatory changes, making it vital to modify systems and processes accordingly.
-
User Feedback and Engagement: Regularly soliciting feedback from users can help identify pain points and areas for enhancement. Involving users in the optimization process fosters a culture of ongoing improvement. Did you know that 67% of regulatory leaders are focusing on enhancing data quality for risk detection this year?
-
Performance Metrics: Setting key performance indicators (KPIs) to assess the efficiency of your regulatory tools is essential. Consistently evaluating these metrics allows organizations to gauge performance and discover optimization opportunities, especially since regulatory complexity adversely affects 77% of companies.
-
Invest in Upgrades and Enhancements: As technology advances, investing in upgrades or additional features can significantly improve your system's capabilities. This proactive strategy ensures that your organization remains compliant and secure, particularly given the anticipated $12.2 trillion cost of cybercrime by 2031, underscoring the importance of robust regulatory technology.
By implementing these strategies, organizations can effectively manage and optimize their cyber security compliance software, ensuring ongoing adherence to CMMC requirements and enhancing their overall cybersecurity posture.
Conclusion
Understanding and implementing effective cybersecurity compliance software is crucial for defense contractors navigating the complex regulatory landscape. Are you aware of the intricacies of frameworks like CMMC? By adhering to standards such as NIST SP 800-171 and DFARS, organizations can not only ensure compliance but also significantly enhance their overall cybersecurity posture.
To select the right compliance software, it’s essential to assess your organizational needs, ensure system integration, and prioritize user-friendliness. What are the critical phases of implementation? Developing a clear plan, engaging stakeholders, and providing ongoing support are vital steps. Continuous management and optimization of compliance software through regular audits, user feedback, and performance metrics are key to maintaining compliance and adapting to evolving regulations.
In an era where cybersecurity threats are ever-present, defense contractors must prioritize robust compliance strategies to safeguard sensitive information and maintain eligibility for government contracts. By adopting these best practices and investing in tailored cybersecurity compliance solutions, organizations can not only meet regulatory requirements but also position themselves as leaders in the defense industry. Are you ready to tackle the challenges of the future?
Frequently Asked Questions
What is the importance of understanding cybersecurity compliance requirements for defense contracts?
Understanding cybersecurity compliance requirements is crucial for organizations to navigate defense contracting effectively and to safeguard Controlled Unclassified Information (CUI) as mandated by the Department of Defense (DoD).
What is the Cybersecurity Maturity Model Certification (CMMC)?
The CMMC is a framework established by the DoD that outlines necessary practices and processes for organizations to implement cybersecurity compliance software to protect CUI.
What are the different levels of CMMC?
CMMC has tiered levels ranging from Level 1, which focuses on basic cyber hygiene, to Level 5, which encompasses advanced and progressive cybersecurity practices.
What does NIST SP 800-171 entail?
NIST SP 800-171 is a standard that specifies the criteria for safeguarding CUI and is a vital component of CMMC adherence, detailing 14 families of security requirements.
What is DFARS and why is it important?
The Defense Federal Acquisition Regulation Supplement (DFARS) mandates specific cybersecurity standards for defense contractors, making it essential for maintaining eligibility for government contracts.
What is the current state of awareness regarding CMMC among defense contractors?
As of 2026, a significant percentage of defense contractors are still unfamiliar with the CMMC framework, indicating a need for increased awareness and education.
How can organizations benefit from engaging with cybersecurity standards?
Organizations that actively engage with security standards can improve their readiness for regulations and strengthen their overall cybersecurity posture, positioning themselves better in the competitive defense contracting environment.




