Master Cybersecurity Compliance Consulting: Key Strategies for Success
Master cybersecurity compliance consulting with key strategies to enhance security and mitigate risks.

Introduction
In today’s digital landscape, the significance of cybersecurity compliance is paramount; it stands as a vital defense against an ever-evolving array of threats. Organizations, especially those working with the Department of Defense, must navigate a complex maze of regulations and standards to safeguard sensitive information and uphold their reputations. Yet, the journey to achieving and maintaining compliance is riddled with challenges. This raises an important question: what strategies can organizations adopt not only to fulfill these regulatory requirements but also to bolster their overall cybersecurity posture?
By understanding the intricacies of compliance, organizations can better prepare themselves to face the challenges ahead.
Define Cybersecurity Compliance and Its Importance
Cybersecurity compliance consulting is essential for protecting sensitive information and digital assets from cyber threats. Following established laws, regulations, and standards is not just a regulatory requirement; it’s a necessity for organizations looking to engage with the Department of Defense (DoD) and may require cybersecurity compliance consulting. The significance of adhering to digital security protocols cannot be overstated - it safeguards sensitive data, builds customer confidence, and mitigates the risk of severe legal consequences.
Organizations that neglect these regulations risk financial penalties and potential damage to their reputation and operational effectiveness. For defense contractors, understanding the complexities of these regulations is crucial, as it directly impacts their eligibility for contracts and necessitates cybersecurity compliance consulting to enhance their overall cybersecurity posture. Recent developments indicate that by the end of 2025, compliance with cybersecurity standards will be increasingly mandated in DoD contracts. This underscores the urgency for contractors to align their practices with the standards set by cybersecurity compliance consulting.
Common questions arise among defense contractors:
- What specific steps must we take to achieve compliance?
- How can we effectively interpret the requirements?
The Info Hub provides practical advice and community insights to help navigate these challenges. By effectively managing regulations, organizations not only enhance their security protocols but also bolster customer confidence, positioning themselves favorably in a competitive landscape where reputational integrity is paramount.
Implement Key Strategies for Achieving Compliance
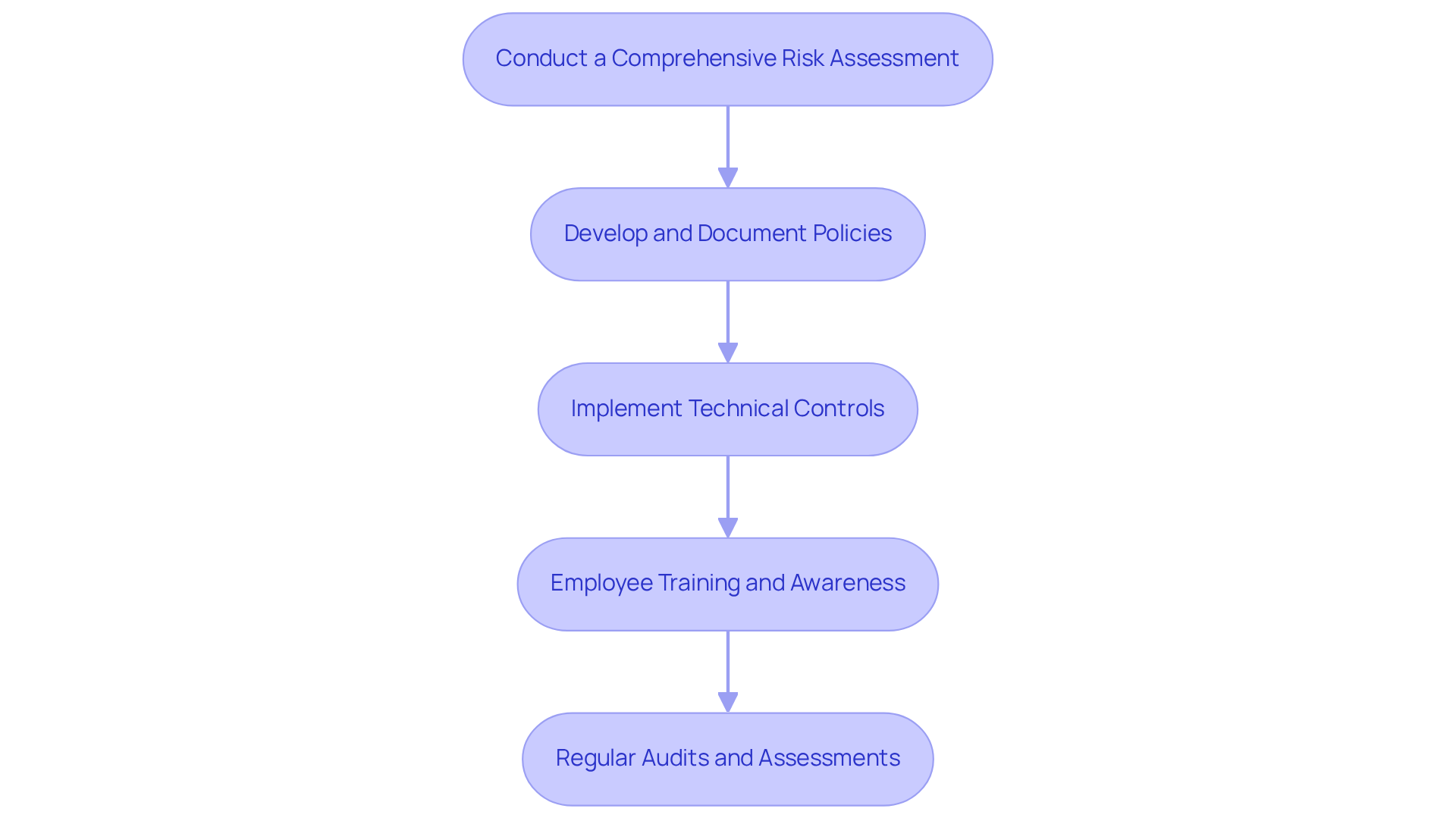
To achieve compliance with the CMMC framework, organizations must implement several key strategies:
-
Conduct a Comprehensive Risk Assessment: Have you identified your vulnerabilities? Assessing the potential impact of cyber threats is essential. This foundational step enables entities to prioritize security measures effectively. In 2025, a significant percentage of organizations reported having documented security policies, underscoring the importance of this practice.
-
Develop and Document Policies: Are your security policies clear? Outlining roles, responsibilities, and procedures for ensuring adherence is crucial. Thorough documentation not only aids in audits and assessments but also ensures that all employees understand their roles in safeguarding sensitive information.
-
Implement Technical Controls: What technical measures are you using? Deploying necessary technical controls, such as firewalls, intrusion detection systems, and encryption, is vital for protecting sensitive data. These measures constitute the foundation of a strong security posture.
-
Employee Training and Awareness: How often do you train your employees? Regular training on cybersecurity best practices and regulatory requirements fosters a culture of security within the organization. Engaged employees serve as the first line of defense against cyber threats, making their awareness and training critical.
-
Regular Audits and Assessments: When was your last audit? Arranging regular audits to assess adherence levels and pinpoint areas for enhancement is a proactive strategy that guarantees continuous conformity to standards. Organizations should consider utilizing outside expertise in cybersecurity compliance consulting for these evaluations, as it can offer valuable insights and improve regulatory efforts.
By concentrating on these strategies, organizations can not only attain regulatory adherence but also foster a culture of ongoing cybersecurity enhancement. This is vital for managing the complexities of the compliance landscape.
Maintain Compliance Through Continuous Assessment and Improvement
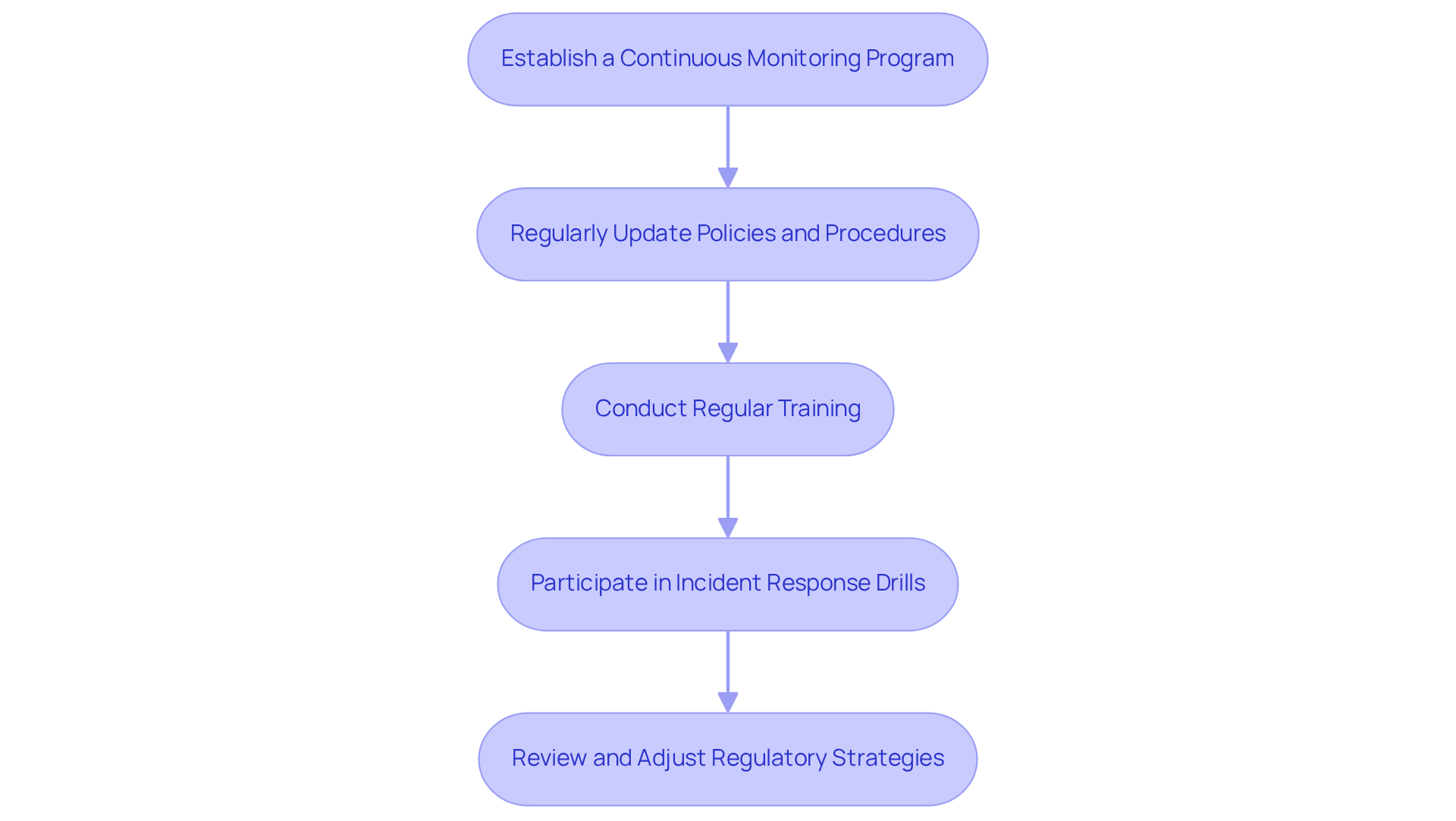
Maintaining adherence is an ongoing endeavor that requires continuous assessment and enhancement. Organizations must adopt the following practices to ensure compliance:
-
Establish a Continuous Monitoring Program: Implement tools and processes to continuously monitor systems for adherence to CMMC requirements. This includes real-time tracking of security controls and identifying vulnerabilities.
-
Regularly Update Policies and Procedures: As regulations and threats evolve, entities must revise their security policies and procedures to align with current best practices and legal requirements. In fact, nearly 80% of organizations revise their security policies annually to stay ahead of emerging threats.
-
Conduct Regular Training: Ongoing training programs for employees are crucial to ensure they stay updated on the latest regulatory requirements and cybersecurity threats. This education is vital for maintaining a strong regulatory stance.
-
Participate in Incident Response Drills: Regularly evaluating incident response strategies is essential for ensuring that the entity can efficiently react to security breaches while upholding regulations. These drills strengthen readiness and flexibility in confronting changing dangers, especially in light of significant online security incidents that occurred in 2025.
-
Review and Adjust Regulatory Strategies: Periodically reviewing regulatory strategies allows organizations to assess their effectiveness and make necessary adjustments based on audit findings and emerging threats. This proactive approach is crucial for maintaining adherence in a rapidly evolving cybersecurity environment.
As Emil Sayegh noted, "Cyber adherence is now table stakes for doing business with the federal government." By applying these strategies, businesses can enhance their preparedness for compliance with cybersecurity standards through cybersecurity compliance consulting and better safeguard sensitive data against advancing cyber threats.
Leverage Expert Consulting for Enhanced Compliance Success
Collaborating with cybersecurity compliance consulting can significantly enhance a company's ability to meet and maintain the standards set by the framework. Here are some key benefits of leveraging expert consulting:
- Tailored Adherence Pathways: Consultants can develop personalized adherence pathways that align with the unique needs and challenges of your organization. This ensures a focused approach to achieving certification.
- Expertise in Regulatory Requirements: With a deep understanding of the CMMC framework and other relevant regulations, consultants help organizations navigate complex regulatory environments with ease.
- Resource Optimization: By outsourcing compliance efforts to experts, businesses can allocate internal resources more effectively. This allows teams to concentrate on core operations while ensuring compliance.
- Ongoing Support and Guidance: Consultants provide continuous assistance, helping organizations adapt to changes in regulations and emerging cybersecurity threats.
- Enhanced Audit Preparedness: With expert guidance, organizations can bolster their audit readiness, ensuring they are well-prepared for assessments and minimizing the risk of non-compliance.
Are you ready to take your compliance efforts to the next level? Engaging with cybersecurity compliance consulting advisors could be the strategic move your organization needs.
Conclusion
Mastering cybersecurity compliance consulting is essential for organizations that want to protect sensitive information and meet regulatory standards. This journey isn’t just about following rules; it’s about creating a strong security framework that builds trust and operational integrity. With the ever-evolving landscape of cybersecurity threats, engaging in proactive compliance measures is more important than ever.
In this article, we’ve outlined key strategies for achieving and maintaining compliance. From conducting thorough risk assessments and developing clear policies to implementing technical controls and fostering employee training, each step is crucial in establishing a resilient cybersecurity posture. Continuous assessment and improvement of compliance practices ensure that organizations stay agile and ready to tackle emerging threats and regulatory changes.
So, what’s the takeaway? Organizations must prioritize cybersecurity compliance consulting to protect their assets and reputation. By leveraging expert guidance and adopting best practices, businesses can effectively navigate the complexities of compliance. The stakes are high, and the time to act is now. Embracing these strategies will not only meet regulatory requirements but also position organizations for success in a competitive marketplace.
Frequently Asked Questions
What is cybersecurity compliance?
Cybersecurity compliance refers to the adherence to established laws, regulations, and standards designed to protect sensitive information and digital assets from cyber threats.
Why is cybersecurity compliance important?
It is essential for safeguarding sensitive data, building customer confidence, and mitigating the risk of severe legal consequences. Additionally, it is crucial for organizations looking to engage with the Department of Defense (DoD).
What risks do organizations face if they neglect cybersecurity compliance?
Organizations that neglect these regulations risk financial penalties, potential damage to their reputation, and a decrease in operational effectiveness.
How does cybersecurity compliance affect defense contractors?
For defense contractors, understanding cybersecurity regulations is vital as it impacts their eligibility for contracts and necessitates compliance consulting to enhance their overall cybersecurity posture.
What are the upcoming changes regarding cybersecurity compliance in DoD contracts?
By the end of 2025, compliance with cybersecurity standards will be increasingly mandated in DoD contracts, highlighting the urgency for contractors to align their practices accordingly.
What common questions do defense contractors have about achieving compliance?
Common questions include what specific steps must be taken to achieve compliance and how to effectively interpret the requirements.
Where can organizations find support for navigating cybersecurity compliance challenges?
The Info Hub provides practical advice and community insights to help organizations manage regulations and enhance their cybersecurity protocols.




