Master DFARS Compliance: Key Strategies for DoD Contractors
Master dod dfars compliance with key strategies to enhance cybersecurity for DoD contractors.

Introduction
Navigating the complex landscape of DFARS compliance is crucial for contractors seeking to secure contracts with the Department of Defense. With the stakes rising due to stringent cybersecurity standards, grasping the nuances of these regulations can offer a significant competitive advantage. Yet, many contractors struggle with compliance complexities, often missing critical requirements that could threaten their eligibility.
What strategies can defense suppliers implement to not only tackle these challenges but also bolster their operational resilience in an ever-evolving regulatory environment? By understanding the intricacies of DFARS compliance, contractors can position themselves for success and ensure they meet the necessary standards.
Understand DFARS: Definition and Importance
The dod dfars establishes crucial regulations that govern how the U.S. Department of Defense (DoD) acquires goods and services. At the heart of the Defense Acquisition Regulation System are stringent information security requirements designed to protect Controlled Unclassified Information (CUI) from unauthorized access and breaches. For defense suppliers, understanding and adhering to dod dfars regulations is not just important; it’s essential, as compliance directly influences their eligibility for DoD contracts.
Moreover, the integration of the Cybersecurity Maturity Model Certification (CMMC) into defense regulations underscores the urgent need for robust cybersecurity practices. This commitment to compliance not only meets legal obligations but also strengthens a contractor's competitive edge in the defense contracting landscape. Have you considered how your organization measures up? Recent case studies reveal that companies actively addressing dod dfars-related challenges can significantly boost their operational efficiency and security posture, ultimately safeguarding sensitive information and ensuring continued eligibility for government contracts.
However, common pitfalls exist. Many underestimate the complexity of regulatory requirements or fail to implement adequate cybersecurity measures. As the regulatory landscape evolves, especially with anticipated changes in 2026, the importance of compliance with dod dfars will only intensify. It’s vital for service providers to stay informed and prepared.
The CMMC Info Hub is your essential resource, offering actionable strategies and practical guidance tailored for defense professionals. By leveraging the insights and experiences shared within the CMMC Info Hub, contractors can streamline regulatory processes and approach evaluations with newfound confidence.
Identify Key DFARS Cybersecurity Requirements
Key cybersecurity requirements demand strict adherence to NIST SP 800-171, which outlines 110 essential security controls for protecting Controlled Unclassified Information (CUI). Contractors must implement these controls across various domains, including access control, incident response, and risk assessment. Notably, regulation 252.204-7012 mandates the development of a System Security Plan (SSP) and a Plan of Action and Milestones (POA&M) to address any adherence gaps identified during evaluations. This organized approach is crucial for contractors to ensure the safeguarding of sensitive information and demonstrate compliance effectively.
Regular self-assessments, along with third-party evaluations, are vital for maintaining dod dfars standards. Consider this:
- 54% of organizations have established formal plans for SP 800-171 adherence, highlighting the growing recognition of these requirements within the defense sector.
- Furthermore, implementing all 110 NIST controls is not just a regulatory obligation; it’s a foundational step in building trust with the Department of Defense and enhancing overall cybersecurity posture.
For a comprehensive understanding and practical strategies, refer to the 'Ultimate Guide to Achieving CMMC Adherence' available at CMMC Info Hub. This resource also addresses common challenges that service providers may face in achieving compliance.
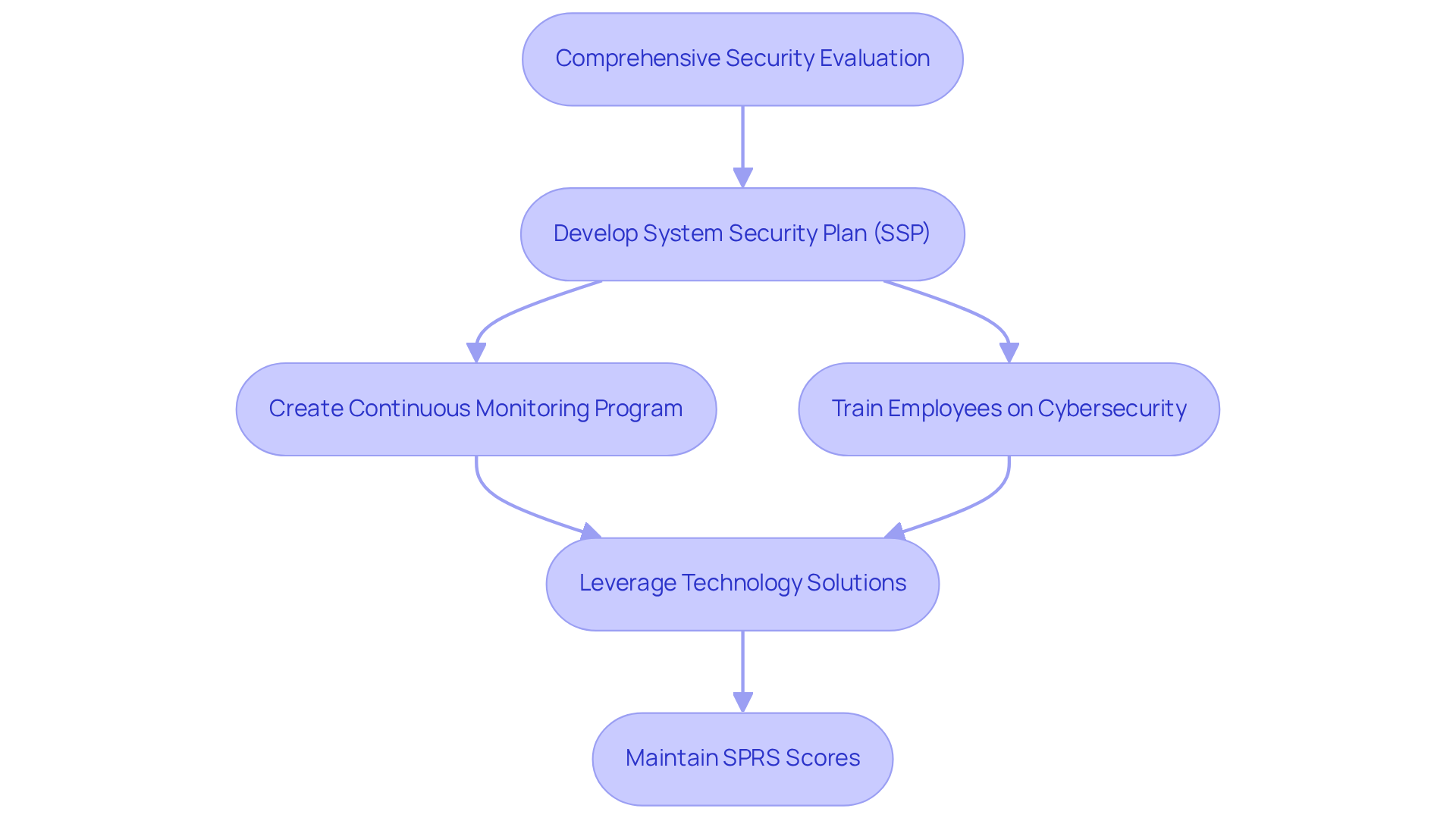
Implement Effective Strategies for DFARS Compliance
To effectively implement adherence strategies, builders must begin with a comprehensive security evaluation to pinpoint weaknesses within their systems. This foundational step is crucial, as it lays the groundwork for developing a robust System Security Plan (SSP) that outlines the security controls in place. Have you considered how a thorough evaluation can reveal substantial deficiencies in your cybersecurity strategies? Addressing these gaps can significantly enhance compliance with regulations and reduce the risk of breaches. Importantly, adherence to dod dfars is essential for eligibility in thousands of current and future defense contracts, highlighting its critical nature for contractors.
Creating a continuous monitoring program is vital for regularly assessing the effectiveness of security measures and ensuring ongoing compliance. This proactive approach not only helps identify potential vulnerabilities but also aligns with the dod dfars requirement for maintaining a mature, documented, and auditable security program. As Shawn Cheadle emphasizes, 'Assess your security protocols to guarantee adherence to the new CMMC clause.'
Training employees on cybersecurity best practices and the importance of safeguarding Controlled Unclassified Information (CUI) is another essential strategy. Engaging staff in regular training sessions fosters a culture of security awareness, which is crucial in mitigating risks associated with human error.
Moreover, leveraging technology solutions, such as automated regulation management tools, can streamline documentation and reporting processes. These tools facilitate easier maintenance of regulations and readiness for audits, ultimately enhancing the service provider's ability to effectively meet dod dfars requirements. By viewing security evaluations as a strategic advantage, providers can position themselves to secure more contracts and build stronger partnerships in the defense marketplace. Additionally, keeping SPRS scores updated is essential for maintaining compliance and demonstrating a commitment to information security.
Establish Continuous Monitoring and Assessment Practices
Ongoing oversight is essential for regulatory adherence, enabling service providers to identify and address security risks proactively. Have you considered how automated monitoring tools can provide real-time insights into your organization’s security posture? These tools significantly enhance threat detection capabilities.
For example, AI-driven solutions have been proven to reduce threat detection and response times, cutting breaches from days to mere minutes. In fact, organizations with fully deployed AI threat detection systems have managed to contain breaches within an average of 214 days. Regular assessments, including vulnerability scans and penetration testing, are vital for evaluating the effectiveness of security controls.
With assessment objectives projected to increase from 320 to 445 in Rev. 3-a roughly 30% rise in complexity - it's clear that organizations leveraging automated monitoring systems can pinpoint vulnerabilities more accurately than traditional methods, ensuring a robust defense against evolving threats.
Moreover, maintaining an up-to-date incident response plan is crucial for swift action during security incidents. Is your plan regularly tested to ensure readiness? By fostering a culture of continuous improvement and vigilance, organizations can enhance their cybersecurity resilience while ensuring ongoing compliance with dod dfars requirements.
As the landscape of cyber threats evolves, integrating automated monitoring tools will become increasingly critical for defense contractors aiming to secure sensitive information in compliance with dod dfars and maintain contract eligibility. It's also important to note that 65% of companies report challenges in integrating AI security solutions with legacy systems, highlighting the need for careful planning and execution when adopting these technologies.
Conclusion
Mastering DFARS compliance is crucial for contractors engaged with the Department of Defense. Understanding the intricacies of the Defense Federal Acquisition Regulation Supplement allows organizations to meet regulatory requirements while enhancing their cybersecurity posture and competitiveness in the defense contracting landscape.
Contractors must adhere to DFARS regulations, especially the cybersecurity mandates outlined in NIST SP 800-171. Key strategies for compliance include:
- Conducting thorough security evaluations
- Developing robust System Security Plans
- Implementing continuous monitoring practices
Moreover, integrating training programs and technology solutions is vital for fostering a culture of security awareness and ensuring ongoing adherence to evolving regulations.
Given the increasing complexity of DFARS requirements and anticipated changes, it’s imperative for defense contractors to proactively tackle compliance challenges. By embracing these best practices and leveraging available resources, organizations can safeguard sensitive information and position themselves for success in securing future contracts. Remember, commitment to DFARS compliance is not just a regulatory obligation; it’s a strategic advantage that can significantly enhance a contractor's operational efficiency and overall success in the defense sector.
Frequently Asked Questions
What is DFARS and why is it important?
DFARS, or the Defense Federal Acquisition Regulation Supplement, establishes regulations that govern how the U.S. Department of Defense (DoD) acquires goods and services. It is important because it includes stringent information security requirements to protect Controlled Unclassified Information (CUI) from unauthorized access and breaches.
How does DFARS compliance affect defense suppliers?
Compliance with DFARS regulations is essential for defense suppliers as it directly influences their eligibility for DoD contracts. Non-compliance can jeopardize their ability to secure government contracts.
What role does the Cybersecurity Maturity Model Certification (CMMC) play in DFARS?
The integration of CMMC into defense regulations emphasizes the need for robust cybersecurity practices. It ensures that contractors not only meet legal obligations but also enhance their competitive edge in the defense contracting landscape.
What are some common pitfalls related to DFARS compliance?
Common pitfalls include underestimating the complexity of regulatory requirements and failing to implement adequate cybersecurity measures. These oversights can lead to non-compliance and loss of contract eligibility.
Why is it important for service providers to stay informed about DFARS regulations?
As the regulatory landscape evolves, especially with anticipated changes in 2026, staying informed about DFARS regulations is vital for service providers to ensure compliance and maintain eligibility for government contracts.
What resources are available for defense professionals regarding DFARS and CMMC?
The CMMC Info Hub is a key resource that offers actionable strategies and practical guidance tailored for defense professionals, helping them streamline regulatory processes and approach evaluations with confidence.