Master Enclave Cyber Security: Essential Steps for Defense Contractors
Master enclave cyber security with essential strategies for defense contractors' protection.

Overview
The article highlights crucial steps for defense contractors to excel in enclave cyber security. Why is this important? Creating secure zones is vital for protecting sensitive data and ensuring compliance with regulations such as the Cybersecurity Maturity Model Certification (CMMC).
To achieve this, the article outlines practical strategies for establishing secure environments. These include:
- Conducting thorough risk assessments
- Selecting the appropriate types of enclaves
- Implementing continuous monitoring to adapt to the ever-evolving landscape of cybersecurity threats
By mastering these strategies, defense contractors can not only safeguard their data but also enhance their compliance posture. Are you ready to take action? Embrace these essential steps to fortify your cyber security framework and protect your organization from potential threats.
Introduction
In an age where cyber threats are increasingly sophisticated, the need for robust cybersecurity measures has never been more pressing—especially for defense contractors handling sensitive information. Enclave cybersecurity emerges as a critical strategy, offering a structured approach to creating secure zones that protect vital data and ensure compliance with stringent regulations. However, the path to effectively implementing these secure environments is fraught with challenges and complexities.
How can organizations navigate these obstacles to not only safeguard their assets but also enhance their operational integrity? This question is pivotal as it underscores the necessity for a proactive stance in cybersecurity. By understanding the intricacies of enclave cybersecurity, organizations can better position themselves to meet compliance requirements while fortifying their defenses against evolving threats.
Define Enclaves in Cybersecurity
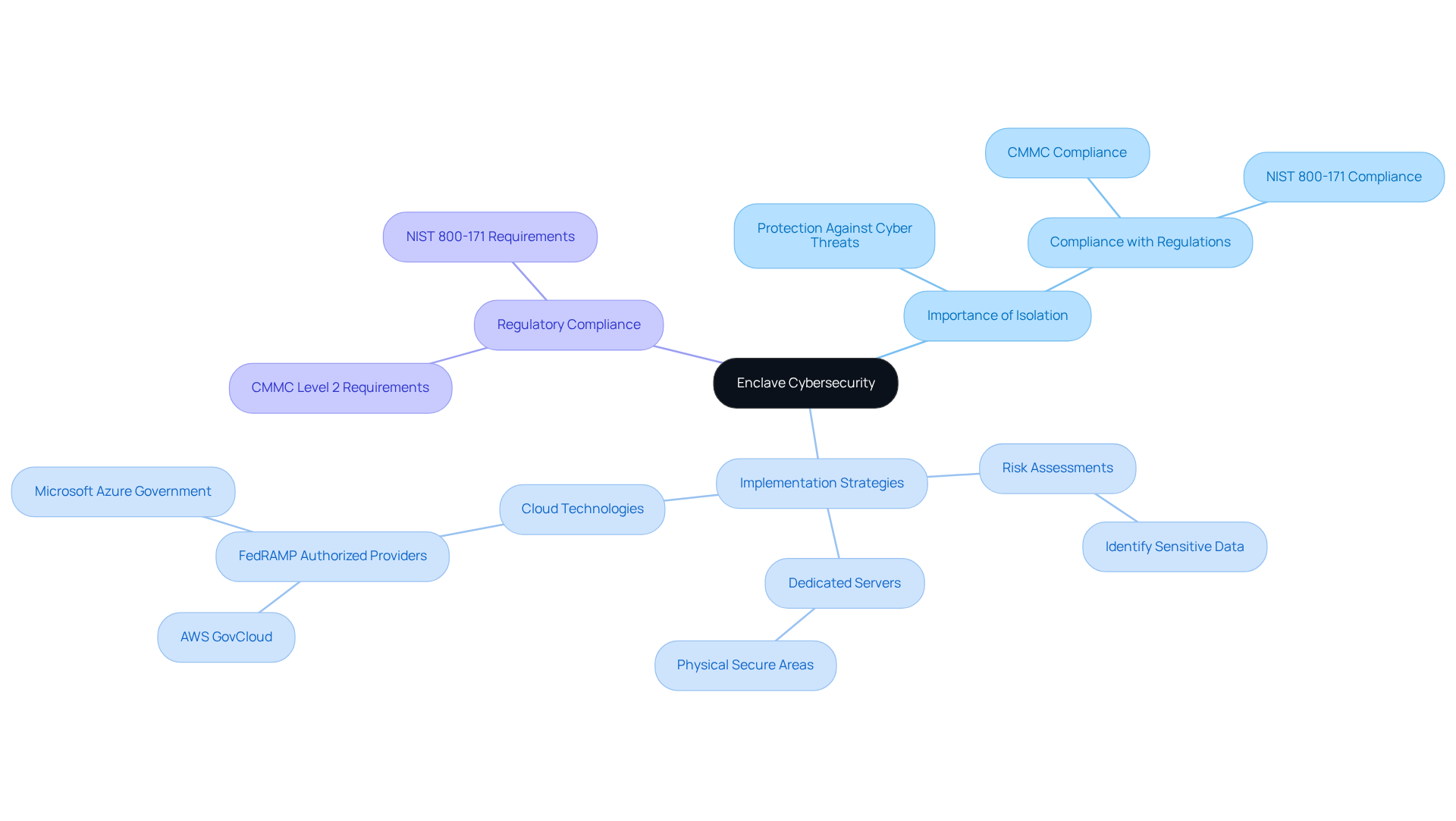
In enclave cyber security, a secure zone serves as a vital shield—a protected and isolated environment designed specifically for managing sensitive data and applications. This isolation is crucial for defending against external threats. By restricting access to approved users only, secure areas are crucial in enclave cyber security to safeguard critical assets, particularly for defense firms that must adhere to stringent Department of Defense (DoD) regulations.
Why is this separation so important? Enclave cyber security protects sensitive information from cyber threats and ensures compliance with regulations like the Cybersecurity Maturity Model Certification (CMMC). To effectively implement secure zones, defense contractors can adopt practical strategies:
- Conducting thorough risk assessments helps identify sensitive data.
- Utilizing dedicated servers for physical secure areas or leveraging cloud technologies for virtual environments enhances security measures.
Insights from industry peers suggest that collaborating with cybersecurity specialists can significantly improve the design and execution of these secure areas, ensuring they meet regulatory standards. As the cybersecurity landscape evolves, understanding the role and application of enclave cyber security becomes essential for organizations aiming to bolster their protection stance and efficiently fulfill compliance requirements.
In conclusion, establishing secure zones is not just a regulatory necessity; it’s a proactive step towards safeguarding your organization’s most valuable assets. Are you ready to take action and enhance your cybersecurity posture?
Explore Types of Enclaves for Defense Contractors
Defense contractors have several types of enclaves at their disposal, each offering distinct features and advantages:
-
Physical Enclaves: These dedicated hardware environments deliver a high level of security, making them ideal for processing classified information. They are physically secured to prevent unauthorized access, which makes them a robust choice for sensitive operations. However, organizations must consider the expense of establishing physical barriers, which can range from $25,000 to $90,000 each year, when designing their cybersecurity framework.
-
Virtual Compartments: Utilizing virtualization technology, these units allow multiple isolated environments to function on a single physical server. Their cost-effectiveness and scalability make them suitable for organizations with diverse operational needs, allowing for efficient resource utilization. As Famous Jefferson observes, "If you want to be on DoD contracts, it’s advantageous" to use communities effectively.
-
Cloud Environments: By leveraging the security features of cloud service providers, cloud-based environments create secure settings for data storage and processing. They offer flexibility and can be customized to meet specific compliance requirements, making them an attractive option for many defense contractors. These zones assist organizations in fulfilling the Department of Defense's Cybersecurity Maturity Model Certification (CMMC) requirements by utilizing enclave cyber security to protect controlled unclassified information (CUI).
-
Hybrid Spaces: By merging components of both physical and virtual settings, hybrid spaces offer a flexible solution that adjusts to changing protection requirements. They are particularly beneficial for organizations transitioning to cloud solutions while still maintaining on-premises security measures. Secure zones also reduce risks linked to insider threats, which present a considerable danger to enterprise IT. Notably, 43% of all breaches are carried out by insiders, underscoring the importance of these protective measures.
By grasping these categories of areas, defense contractors can make informed choices about the most appropriate solutions for their operational needs and regulatory responsibilities. Integrating these insights into their strategies will not only enhance their cybersecurity posture but also prepare them for defense contracts.

Implement Enclave Solutions: A Step-by-Step Guide
Implementing enclave solutions involves several key steps that can significantly enhance your organization's cybersecurity posture:
-
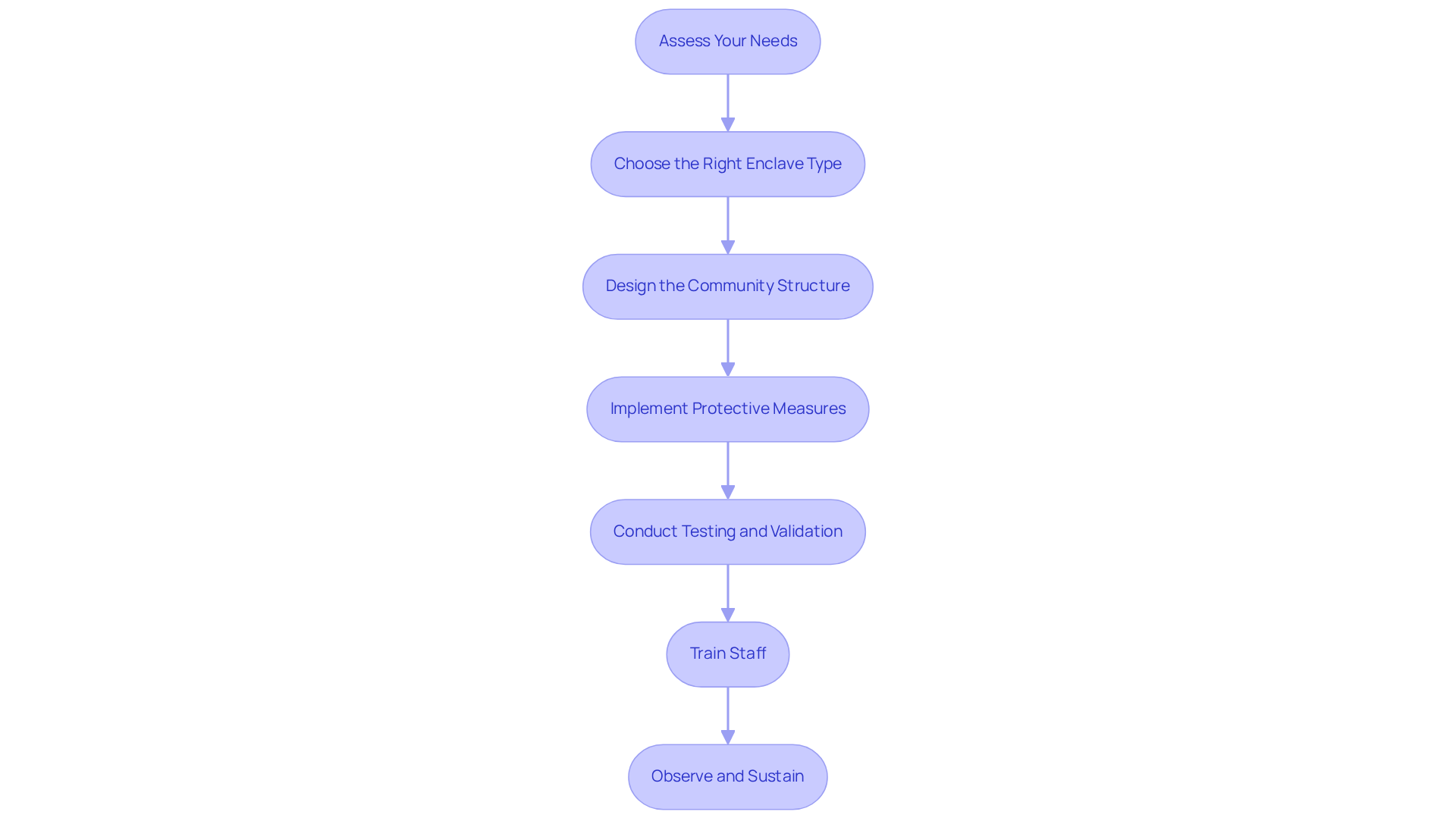
Assess Your Needs: Begin by evaluating your organization's specific cybersecurity requirements and regulatory obligations. What types of data need protection? What potential threats do you face? Cybersecurity experts emphasize that understanding your unique environment is crucial for successful implementation.
-
Choose the Right Enclave Type: After your assessment, select the most appropriate type of enclave—whether physical, virtual, cloud, or hybrid—that aligns with your operational needs and budget. Many defense contractors find that a Managed Controlled Unclassified Information (CUI) Enclave is the fastest route to compliance, often achievable within two months.
-
Design the Community Structure: Plan the architecture of your enclave, including network configurations, access controls, and protection protocols. Ensure that your design complies with CMMC requirements. Real-world examples show that a well-structured area can significantly reduce the complexity of regulatory evaluations.
-
Implement Protective Measures: Deploy essential protective measures, such as firewalls, intrusion detection systems, and encryption, to shield the enclave from unauthorized access and data breaches. Effective protective measures are vital for safeguarding sensitive information and demonstrating compliance.
-
Conduct Testing and Validation: Before launching, rigorously test the environment to ensure all protective measures are functioning as intended. Does the area meet compliance standards? Can it withstand potential cyber threats? This step is critical, as organizations often struggle to expand their protective measures without thorough validation.
-
Train Staff: Provide comprehensive training for employees on securely operating within the enclave. Do they understand the importance of adhering to safety procedures and regulatory obligations? Training is essential for minimizing disruptions during the transition to a compliant environment.
-
Observe and Sustain: Continuously monitor the enclave for security incidents and compliance adherence. Regularly update security measures and conduct audits to ensure ongoing protection and compliance with CMMC standards. A proactive monitoring approach enables organizations to swiftly adapt to evolving cybersecurity threats.
Address Challenges in Adopting Enclave Technology
Adopting enclave technology presents several challenges for defense contractors that must be addressed to ensure successful implementation and compliance with cybersecurity standards:
-
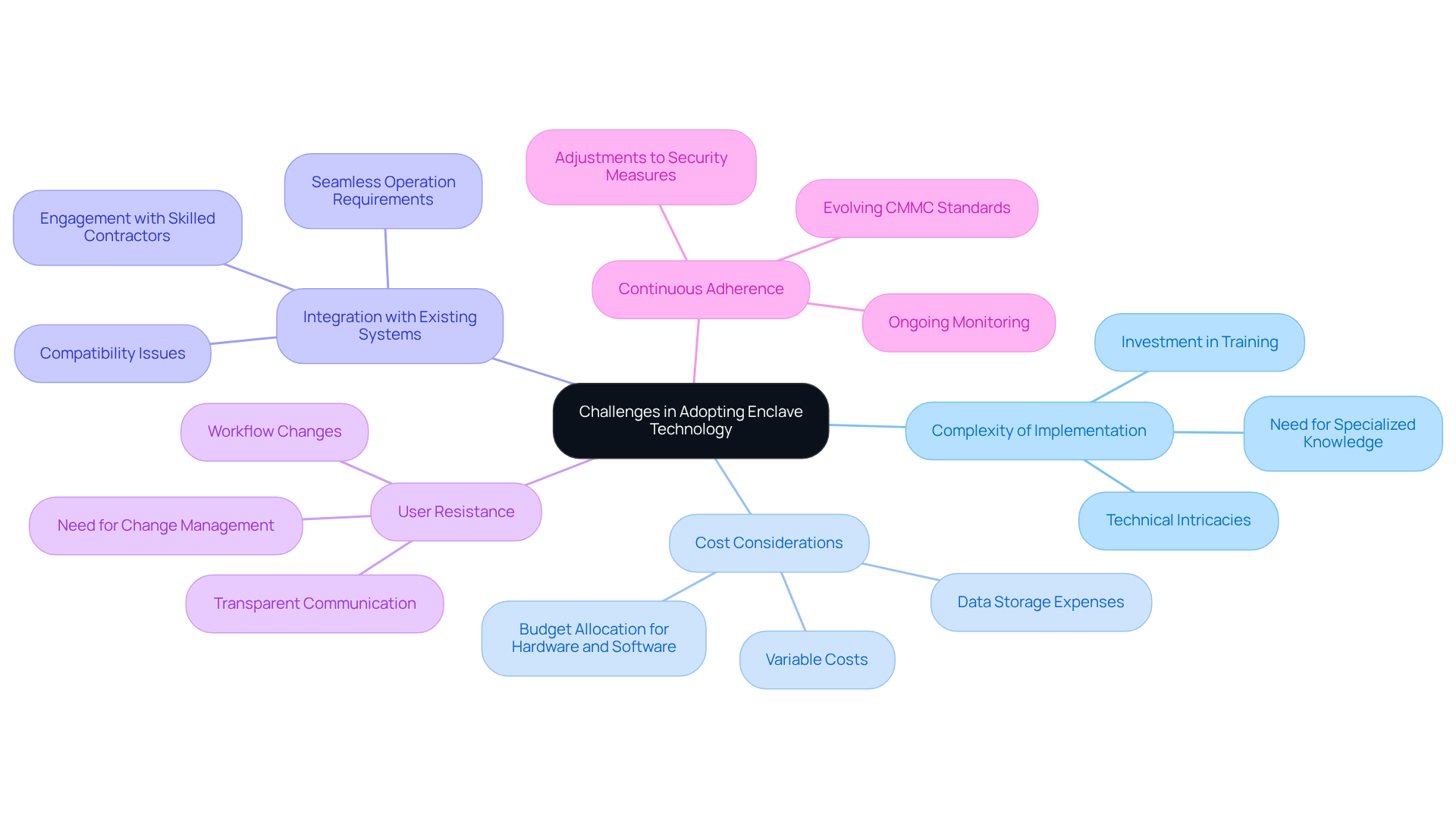
Complexity of Implementation: Establishing a secure environment can be technically intricate, requiring specialized knowledge and resources. Organizations may need to invest in training or hire experts to assist with the implementation process. As cybersecurity analyst Famous Jefferson emphasizes, "It’s all about safeguarding information," highlighting the critical nature of secure setups.
-
Cost Considerations: The costs associated with enclave technology can vary significantly based on the type of area selected. Organizations must allocate funds for hardware, software, and ongoing maintenance to keep the environment secure and compliant. A major challenge lies in accurately calculating the expenses related to data storage, which can greatly influence financial planning for defense suppliers.
-
Integration with Existing Systems: Incorporating secure technology with current IT infrastructure can be challenging. Organizations must ensure compatibility and seamless operation between new and legacy systems. Engaging with contractors skilled in community setups can provide valuable insights into effective integration strategies.
-
User Resistance: Employees may resist changes to their workflows or the introduction of new protective protocols. To mitigate this resistance, effective change management strategies, including training and communication, are essential. Transparent communication about the advantages of the new area can foster acceptance among staff.
-
Continuous Adherence: Maintaining alignment with evolving CMMC standards requires ongoing observation and revisions to protective measures. Organizations must stay informed about regulatory changes and adjust their solutions accordingly. Vigilance in adherence efforts is crucial to ensure that security measures remain aligned with the latest standards.
By proactively addressing these challenges, defense contractors can significantly enhance their chances of successfully implementing enclave cyber security technology and achieving compliance with cybersecurity standards. Are you ready to take the necessary steps to secure your operations?
Conclusion
Establishing a robust enclave cybersecurity framework is essential for defense contractors aiming to protect sensitive data and comply with stringent regulations. Secure zones that isolate critical information not only safeguard assets from cyber threats but also demonstrate a commitment to regulatory compliance, such as the Cybersecurity Maturity Model Certification (CMMC). In today’s ever-evolving digital landscape, this proactive approach to cybersecurity is crucial.
Throughout this article, we explored various types of enclaves—physical, virtual, cloud, and hybrid environments—each offering unique advantages tailored to different operational needs. Key steps for successful implementation were outlined, emphasizing thorough assessments, careful design, and continuous monitoring. Challenges such as cost, complexity, and user resistance were also addressed, highlighting the need for strategic planning and expert guidance to navigate potential obstacles.
Ultimately, the significance of enclave cybersecurity cannot be overstated. As defense contractors face increasing cyber threats and regulatory demands, taking decisive action to implement effective enclave solutions is not just an option; it is a necessity. By prioritizing cybersecurity measures, organizations can better protect their vital assets, ensure compliance, and maintain a competitive edge in the defense industry. Embracing these practices today will pave the way for a more secure and resilient future.
Frequently Asked Questions
What are enclaves in cybersecurity?
Enclaves in cybersecurity refer to secure zones that serve as protected and isolated environments specifically designed for managing sensitive data and applications.
Why is isolation important in enclave cybersecurity?
Isolation is crucial in enclave cybersecurity as it helps defend against external threats by restricting access to approved users only, thereby safeguarding critical assets.
Who primarily benefits from enclave cybersecurity?
Defense firms, particularly those that must adhere to stringent Department of Defense (DoD) regulations, primarily benefit from enclave cybersecurity.
How does enclave cybersecurity support compliance?
Enclave cybersecurity protects sensitive information from cyber threats and ensures compliance with regulations like the Cybersecurity Maturity Model Certification (CMMC).
What strategies can defense contractors adopt to implement secure zones?
Defense contractors can conduct thorough risk assessments to identify sensitive data and utilize dedicated servers for physical secure areas or leverage cloud technologies for virtual environments to enhance security measures.
How can collaboration with cybersecurity specialists improve secure zones?
Collaborating with cybersecurity specialists can significantly improve the design and execution of secure areas, ensuring they meet regulatory standards.
Why is understanding enclave cybersecurity important for organizations?
Understanding enclave cybersecurity is essential for organizations aiming to bolster their protection stance and efficiently fulfill compliance requirements as the cybersecurity landscape evolves.
Is establishing secure zones only a regulatory necessity?
No, establishing secure zones is not just a regulatory necessity; it is also a proactive step towards safeguarding an organization’s most valuable assets.