Master NIST SP 800-171 Rev 3: 6 Steps for Defense Contractors
Master NIST SP 800-171 Rev 3 with 6 essential steps for defense contractors' compliance.

Introduction
NIST SP 800-171 Rev 3 marks a significant evolution in cybersecurity for defense contractors, introducing 97 protective requirements designed to safeguard Controlled Unclassified Information (CUI). This guide outlines a structured approach to achieving compliance, detailing six essential steps organizations can take to bolster their security posture and navigate the complexities of these new requirements.
As cyber threats continue to escalate, the question arises: how can defense contractors not only meet compliance but also stay ahead of potential vulnerabilities? By understanding and implementing these requirements, organizations can enhance their defenses and ensure they are prepared for the challenges ahead.
In this article, we will explore the critical steps necessary for compliance and provide actionable insights to help you effectively manage your cybersecurity responsibilities.
Understand NIST SP 800-171 Rev 3 Requirements
NIST SP 800-171 Rev 3 establishes 97 protective requirements that are designed to safeguard Controlled Unclassified Information (CUI) within non-federal systems. These requirements are organized into 17 families, reflecting a significant shift from the previous 14 families. New categories such as Planning, System and Services Acquisition, and Supply Chain Risk Management have been introduced. Key areas to focus on include:
- Access Control: Limit access to CUI to authorized personnel only, ensuring robust authentication measures are in place.
- Awareness and Training: Implement comprehensive training programs to equip employees with the knowledge necessary to maintain safety practices effectively.
- Audit and Accountability: Maintain detailed logs of access and modifications to CUI, facilitating accountability and traceability.
- Configuration Management: Define and enforce baseline configurations for systems that process CUI, ensuring consistency and protection.
- Incident Response: Develop and regularly update a response plan to address potential security incidents swiftly and effectively.
Organizations must actively oversee their adherence to these requirements. This shift from a document-centric approach to one centered on ongoing supervision and control enforcement is crucial. Adherence to NIST SP 800-171 Rev 3 is not merely a checklist; it’s a dynamic process that requires ongoing vigilance and adaptation to emerging threats. As highlighted by cybersecurity specialists, the focus on active monitoring and proof of adherence marks a significant evolution in how organizations must approach their cybersecurity stance. For a complete list of requirements, refer to the official NIST documentation.
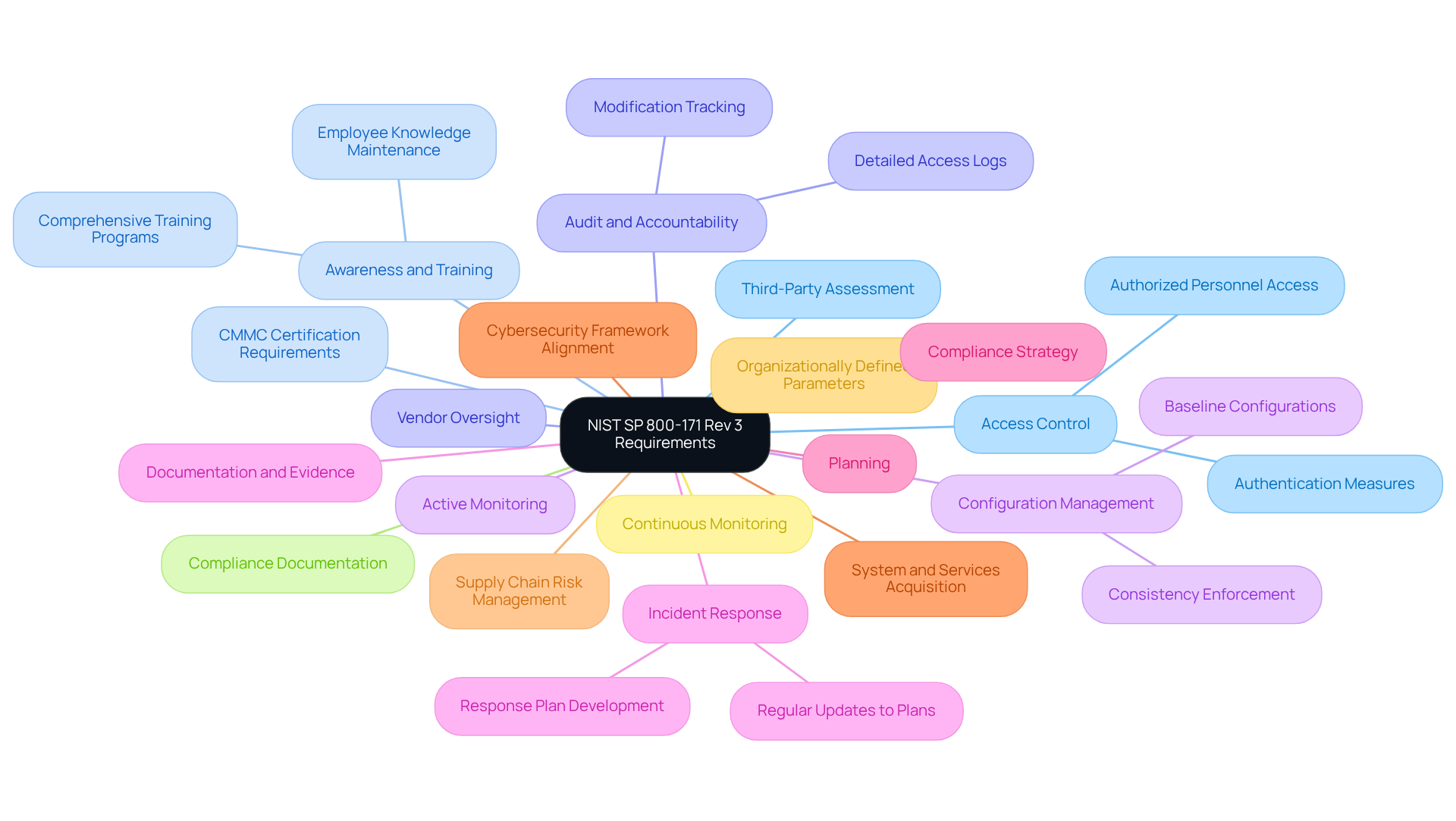
Assess Your Current Security Posture
To effectively assess your current security posture, follow these essential steps:
-
Conduct a Self-Assessment: Start by utilizing the NIST SP 800-171 Rev 3 guidelines to evaluate your compliance status against the 97 requirements. This process involves a thorough examination of your current policies, procedures, and technical measures. By identifying areas of strength and weakness, you can gain a clearer picture of your security landscape.
-
Identify Gaps: Next, document specific areas where your current practices fall short of the requirements outlined in NIST SP 800-171 Rev 3. Common gaps often include inadequate access controls, insufficient incident response plans, and the failure to implement multifactor authentication. In fact, 91% of companies have not adopted this crucial measure for local and network access.
-
Utilize Evaluation Tools: Leverage tools such as the NIST Cybersecurity Framework or third-party evaluation services to gain a comprehensive understanding of your security posture. Collaborating with knowledgeable partners can provide valuable insights into effective regulatory strategies, enhancing your compliance efforts.
-
Engage Stakeholders: It's vital to involve key personnel from IT, compliance, and management to ensure a thorough evaluation. Cooperation among departments is essential for recognizing vulnerabilities and aligning protective measures with your organizational objectives.
-
Document Findings: Create a detailed report summarizing your assessment results, highlighting both strengths and weaknesses in your current security measures. This documentation will serve as a foundation for remediation efforts and future regulatory audits, ensuring you stay on track.
-
Review and Update Regularly: Remember, compliance is not a one-time event; it requires ongoing evaluation and adjustment. Consistently review your self-evaluation to ensure your organization adapts to changing threats and regulatory requirements.
By following these steps, you can enhance your security posture and ensure compliance with industry standards.
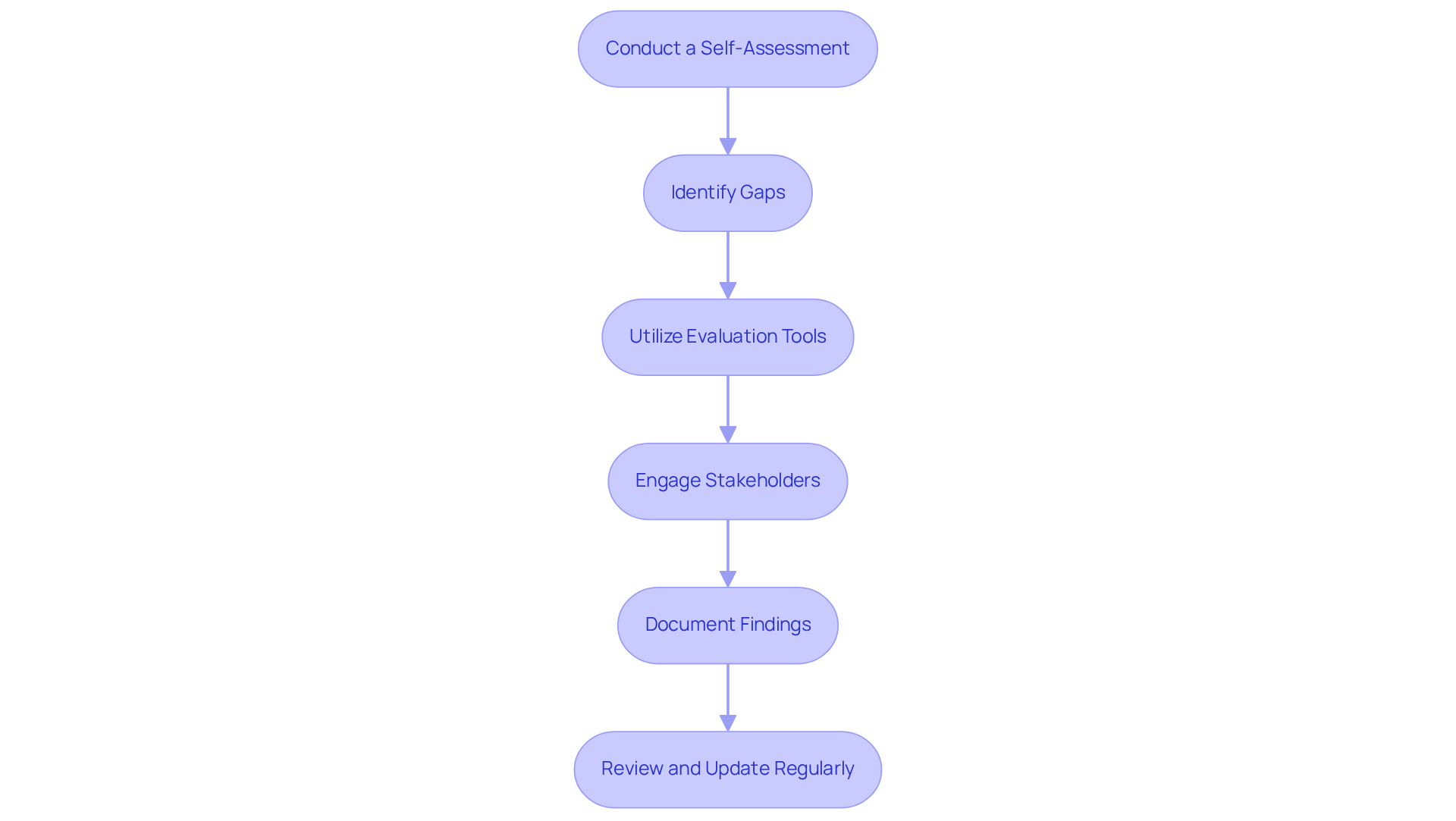
Develop a System Security Plan (SSP)
Creating a System Security Plan (SSP) involves several essential steps:
-
Define System Boundaries: Start by clearly delineating the systems that process, store, or transmit Controlled Unclassified Information (CUI). This definition should encompass all relevant hardware, software, and network components. Establishing precise boundaries is crucial; it helps assessors understand the scope of your security measures. A well-defined boundary is foundational for effective adherence, as emphasized in the Ultimate Guide to Achieving CMMC Adherence.
-
Identify Security Controls: For each of the 97 requirements outlined in NIST SP 800-171 Rev 3, specify how your organization will implement and monitor compliance with NIST SP 800-171 Rev 3. This includes outlining technical measures, policies, and procedures that align with best practices. A strong SSP embodies a proactive culture of protection, integrating these measures into daily operations, as highlighted in the guide.
-
Document Roles and Responsibilities: Assign specific roles to team members accountable for implementing and maintaining protective measures. Clear accountability ensures that everyone understands their duties, which is essential for efficient management.
-
Include Risk Evaluation Results: Integrate findings from your protection stance evaluation into your SSP. This step is vital, as it enables you to address potential vulnerabilities and align your protective measures with identified risks, underscoring the importance of defining the scope of your CMMC evaluation.
-
Review and Update Regularly: Treat the SSP as a living document that evolves with your organization. Regular updates are necessary, especially when significant changes occur in your systems or the regulatory landscape. Evaluate the SSP at least once a year, and ensure that any updates are recorded to maintain adherence and preparedness for evaluations. For ongoing monitoring and maintenance practices, refer to resources available on the NIST website, which can help ensure your SSP remains effective.
By following these steps, defense contractors can develop a comprehensive SSP that not only meets regulatory requirements but also complies with NIST SP 800-171 Rev 3, thereby enhancing their overall cybersecurity posture. Organizations should anticipate that the average time taken to develop a robust SSP can vary, but thorough preparation and adherence to best practices can significantly streamline the process.
Create a Plan of Action and Milestones (POA&M)
To create an effective Plan of Action and Milestones (POA&M), follow these essential steps:
-
Identify Tasks: Start by listing all tasks necessary to address the regulatory gaps identified during your security posture assessment and System Security Plan (SSP). This foundational step ensures that all vulnerabilities are accounted for, setting the stage for effective remediation.
-
Set Milestones: Establish clear milestones for each task, specifying deadlines and assigning responsible parties. This structured approach not only facilitates accountability but also aids in tracking progress effectively. How can you ensure that your team stays on target? By defining these milestones, you create a roadmap for success.
-
Allocate Resources: Assess and determine the resources required for each task, including personnel, budget, and tools. Proper resource allocation is crucial for timely completion and successful remediation of identified weaknesses. Are you equipped with the right tools and personnel to tackle these tasks?
-
Monitor Progress: Regularly review the POA&M to track progress against established milestones. This continuous oversight enables prompt modifications, ensuring that your organization remains aligned with regulatory deadlines. What adjustments might be necessary to stay on track?
-
Document Changes: Maintain a comprehensive record of any modifications made to the POA&M, including the rationale for adjustments and updated timelines. This documentation is essential for transparency and accountability in the regulatory process. How can you ensure that your changes are well-documented and justified?
By applying these measures, organizations can efficiently handle their regulatory tasks, streamline their cybersecurity initiatives, and improve their overall protection stance. For defense contractors, the average number of tasks identified in a POA&M typically ranges from 10 to 20, depending on the complexity of the compliance requirements and the organization's existing security measures.
Implement Necessary Controls and Practices
To effectively implement the necessary controls and practices for safeguarding Controlled Unclassified Information (CUI), defense contractors should follow these strategic steps:
-
Prioritize Controls: Start by performing a comprehensive risk evaluation to identify vulnerabilities. Based on this evaluation and your Plans of Actions & Milestones (POA&M), prioritize measures that reduce the highest risks. Did you know that only 14% of organizations feel fully prepared for emerging threats? This statistic underscores the importance of a focused approach.
-
Deploy Technical Solutions: Implement robust technical controls, including firewalls, encryption, and access controls. These measures are essential for protecting CUI from unauthorized access and cyber threats. Organizations are encouraged to adopt secure platforms for CUI transmission, such as encrypted email and secure file-sharing solutions.
-
Establish Policies and Procedures: Develop comprehensive policies that govern the use of systems handling CUI. This encompasses incident response protocols and data handling procedures, ensuring that all employees understand their duties in upholding safety.
-
Train Employees: Conduct regular training sessions to ensure that all personnel understand their roles in cybersecurity and compliance. Awareness and training are critical, as human error remains a significant contributor to security incidents.
-
Monitor and Review: Continuously observe the effectiveness of implemented measures. Regular evaluations and modifications are essential to tackle emerging threats and guarantee alignment with evolving standards, such as the recent updates in NIST SP 800-171 Rev 3, which consolidates requirements to enhance clarity.
By following these steps, organizations can effectively prioritize their cybersecurity controls based on risk evaluations, thereby enhancing their overall security stance and readiness for regulations.
Conduct Regular Assessments and Updates
To maintain compliance, it’s essential to implement a routine for assessments and updates:
-
Schedule Regular Evaluations: Conduct evaluations at least once a year or whenever significant changes occur in your systems or processes. For Level 1, an annual self-evaluation is mandatory, while Level 2 reviews can be self-conducted every three years or certified by a C3PAO. This proactive approach helps identify vulnerabilities and ensures your organization remains aligned with evolving regulatory standards.
-
Employ NIST SP 800-171 rev 3: Utilize the evaluation procedures outlined in NIST SP 800-171 rev 3 to assess the effectiveness of your protective measures. Currently, about 50% of organizations leverage these procedures, underscoring their importance in evaluating compliance with NIST SP 800-171 rev 3 amidst the challenges many face in implementing necessary controls.
-
Revise the SSP and POA&M: After each evaluation, promptly update your System Security Plan (SSP) and Plan of Action and Milestones (POA&M) to reflect any changes in your protective stance or compliance status. This practice is vital for maintaining an accurate representation of your cybersecurity measures.
-
Engage External Auditors: Consider hiring independent auditors for an unbiased assessment of your compliance efforts. This external perspective can provide valuable insights and help pinpoint areas for improvement that may be overlooked internally.
-
Document Findings and Actions: Maintain detailed records of assessment results, actions taken, and any modifications made to your security practices. This documentation not only supports compliance but also facilitates the continuous enhancement of your cybersecurity framework.
By following these best practices, organizations can strengthen their cybersecurity posture and ensure they are well-prepared for the forthcoming CMMC compliance requirements.
Conclusion
Mastering NIST SP 800-171 Rev 3 is crucial for defense contractors who aim to protect Controlled Unclassified Information (CUI) effectively. This guide presents a systematic approach to compliance, emphasizing that adherence is not merely a one-time task but a continuous process that requires vigilance and adaptability. By grasping the requirements, assessing current security measures, developing a System Security Plan, and implementing necessary controls, organizations can significantly bolster their cybersecurity posture.
The article outlines six critical steps:
- Understanding the requirements
- Assessing security posture
- Creating a System Security Plan
- Developing a Plan of Action and Milestones
- Implementing controls
- Conducting regular assessments
Each step builds upon the previous one, ensuring a comprehensive framework for compliance and security. Collaboration among departments and ongoing training for employees is vital, as these elements are essential for fostering a robust security culture.
The significance of NIST SP 800-171 Rev 3 compliance cannot be overstated, particularly in an era where cyber threats are increasingly sophisticated. Organizations must take proactive measures to safeguard sensitive information and prepare for evolving regulatory landscapes. By committing to these practices, defense contractors not only fulfill compliance requirements but also strengthen their defenses against potential cyber threats, securing their operations and reputation in the industry.
Frequently Asked Questions
What is NIST SP 800-171 Rev 3?
NIST SP 800-171 Rev 3 establishes 97 protective requirements designed to safeguard Controlled Unclassified Information (CUI) within non-federal systems, organized into 17 families.
What are the new categories introduced in NIST SP 800-171 Rev 3?
The new categories introduced include Planning, System and Services Acquisition, and Supply Chain Risk Management.
What are some key areas of focus in NIST SP 800-171 Rev 3?
Key areas include Access Control, Awareness and Training, Audit and Accountability, Configuration Management, and Incident Response.
How should organizations approach adherence to NIST SP 800-171 Rev 3?
Organizations must actively oversee their adherence to the requirements, focusing on ongoing supervision and control enforcement rather than treating it as a mere checklist.
What is the first step to assess your current security posture?
The first step is to conduct a self-assessment using the NIST SP 800-171 Rev 3 guidelines to evaluate compliance against the 97 requirements.
How can organizations identify gaps in their security practices?
Organizations can identify gaps by documenting specific areas where their practices fall short of the NIST SP 800-171 Rev 3 requirements, such as inadequate access controls and insufficient incident response plans.
What tools can be utilized to evaluate security posture?
Tools such as the NIST Cybersecurity Framework or third-party evaluation services can be leveraged to gain a comprehensive understanding of security posture.
Why is stakeholder engagement important in assessing security posture?
Engaging key personnel from IT, compliance, and management ensures a thorough evaluation and helps recognize vulnerabilities while aligning protective measures with organizational objectives.
What should organizations do with the findings from their security assessment?
Organizations should document their findings in a detailed report, highlighting strengths and weaknesses, which will serve as a foundation for remediation efforts and future audits.
How often should organizations review and update their compliance efforts?
Organizations should review and update their compliance efforts regularly, as compliance requires ongoing evaluation and adjustment to adapt to changing threats and regulatory requirements.