Master Personal Data Compliance: Key Strategies for Defense Contractors
Master personal data compliance with essential strategies for defense contractors to enhance security.

Introduction
Navigating the complex landscape of personal data compliance is crucial for defense contractors. As regulations evolve, mastering the requirements set by the Department of Defense and other regulatory authorities becomes essential. This not only safeguards sensitive information but also enhances credibility in a competitive market.
However, with frameworks like the Cybersecurity Maturity Model Certification (CMMC) and global regulations such as GDPR and CCPA, how can defense suppliers ensure compliance while effectively protecting personal data? Understanding these complexities is vital for maintaining operational integrity and trust.
By prioritizing compliance, organizations can position themselves as leaders in the industry, ready to tackle the challenges of today’s regulatory environment.
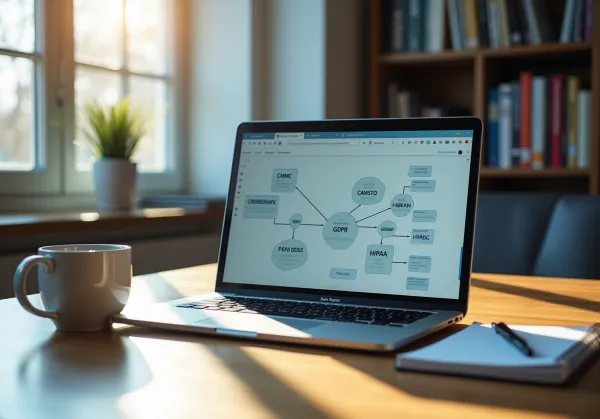
Understand Personal Data Compliance Requirements
To effectively oversee personal data compliance, defense suppliers must grasp the specific requirements set by the Department of Defense (DoD) and relevant regulatory authorities. At the heart of these requirements is the Cybersecurity Maturity Model Certification (CMMC), which outlines essential security controls for protecting Controlled Unclassified Information (CUI). Recent updates to the guidelines underscore the critical need for personal data compliance to protect personal information from unauthorized access and breaches. This makes it imperative for vendors to stay informed about these evolving standards.
Beyond CMMC, contractors should also consider personal data compliance implications of the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). These regulations provide a broader framework for compliance, particularly for those engaging with international clients or managing sensitive consumer data. Regularly assessing these requirements and remaining vigilant to updates is crucial for maintaining standards and minimizing the risk of penalties.
Organizations navigating these complex regulations have found that proactive engagement with regulatory frameworks not only strengthens their security posture but also fosters trust with clients. For instance, organizations that have successfully implemented security measures report a significant reduction in breach occurrences, showcasing the effectiveness of these guidelines in protecting confidential information. As the landscape of information privacy continues to evolve, defense firms must prioritize compliance to secure their operations and fulfill their contractual obligations.
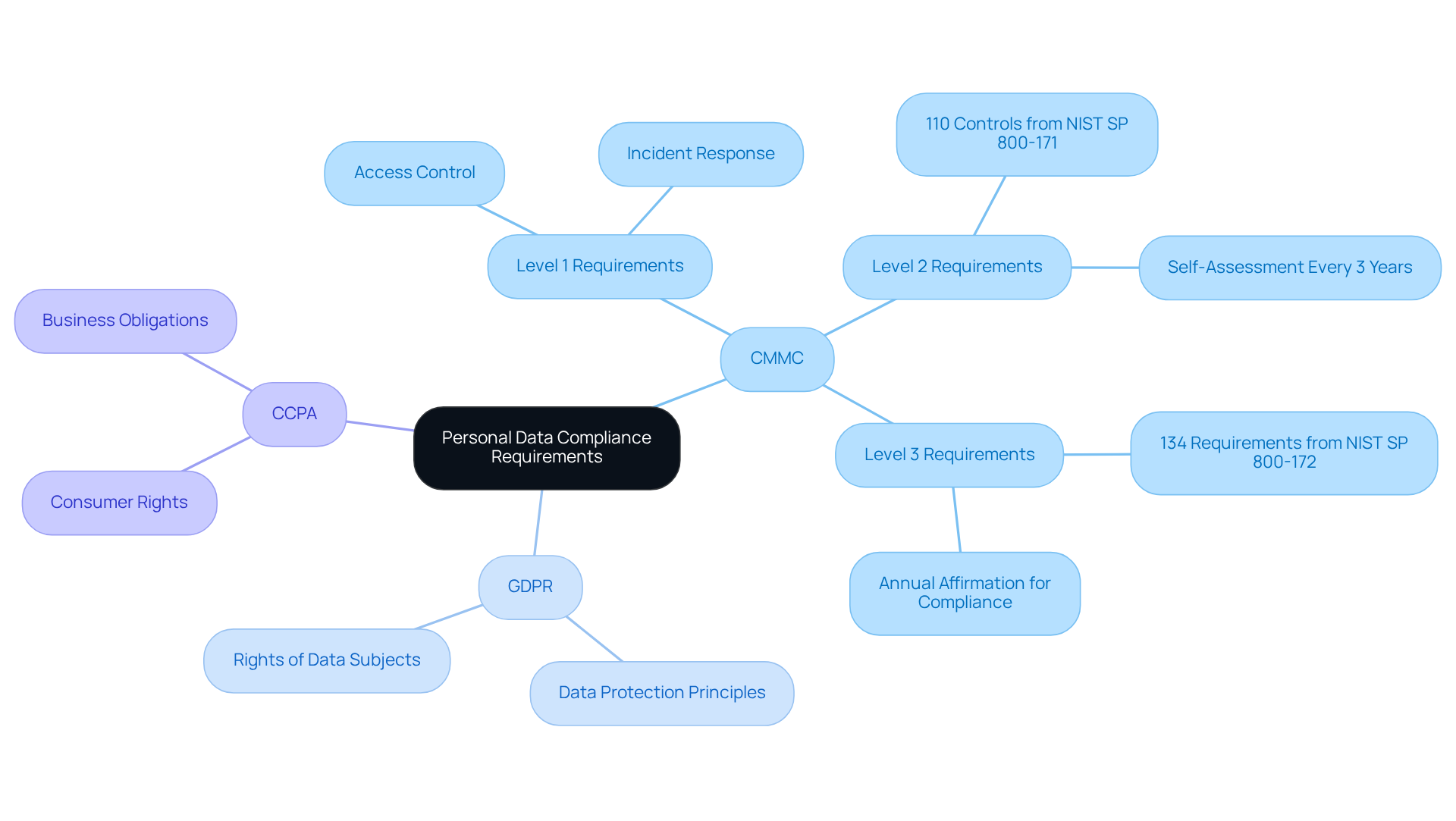
Implement Effective Data Protection Strategies
To effectively safeguard personal information and ensure personal data compliance with the cybersecurity maturity model (CMMC), defense contractors must adopt a multi-layered security approach. Why is this crucial? Because it emphasizes the importance of encryption for confidential information, both in storage and during transmission, preventing unauthorized access in line with established security standards.
Establishing strict access controls is essential. This ensures that only authorized personnel can access sensitive information, significantly reducing the risk of breaches. Additionally, regular software and system updates are critical for patching vulnerabilities. Intrusion detection systems play a vital role in monitoring for suspicious activities, providing an extra layer of security.
Conducting regular risk evaluations is another key component. These evaluations help identify potential vulnerabilities in the information protection strategy, which is crucial for personal data compliance with CMMC standards. Furthermore, developing a comprehensive incident response strategy is essential. This allows organizations to react swiftly to breaches, minimizing damage and fulfilling reporting obligations.
By implementing these best practices, defense suppliers can enhance their information security posture, effectively protect sensitive details, and navigate the complexities of CMMC regulations. Are you ready to take action and strengthen your cybersecurity measures?
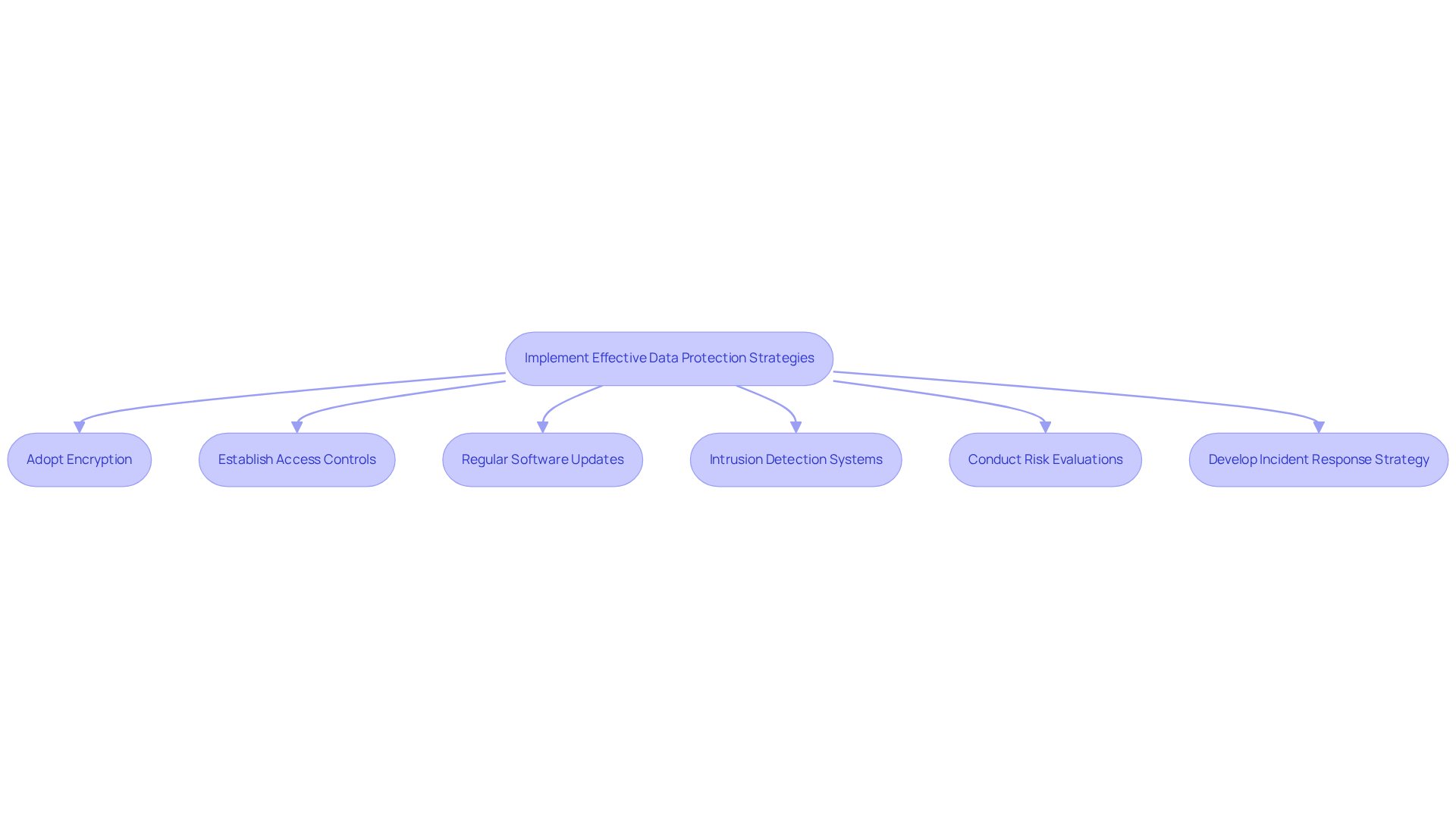
Foster a Culture of Compliance Through Training
Creating a culture of adherence starts with robust training initiatives that equip employees with essential knowledge about personal data compliance and the protection of personal information. Defense contractors must prioritize regular training sessions that cover critical topics, including:
- Best practices for information handling
- Recognizing phishing attempts
- Understanding the consequences of non-compliance
But how can organizations ensure their employees are truly prepared? Implementing role-based training is key. This approach guarantees that individuals in sensitive positions receive content tailored to their specific responsibilities, enhancing both relevance and effectiveness.
Moreover, fostering an environment where employees feel safe to report potential compliance issues without fear of repercussions is vital for accountability. Engaging training methods - like simulations and quizzes - can significantly boost information retention and engagement levels. It’s also crucial to routinely refresh training materials to align with the latest regulations and emerging threats, ensuring that the workforce remains informed and vigilant against evolving privacy challenges.
Statistics reveal that organizations investing in comprehensive training see a marked improvement in employee awareness of protection regulations. In fact, 92% of Americans express concern over online privacy. By prioritizing these training initiatives, defense suppliers can cultivate a skilled workforce that not only adheres to regulatory standards but also actively promotes a culture of information protection.
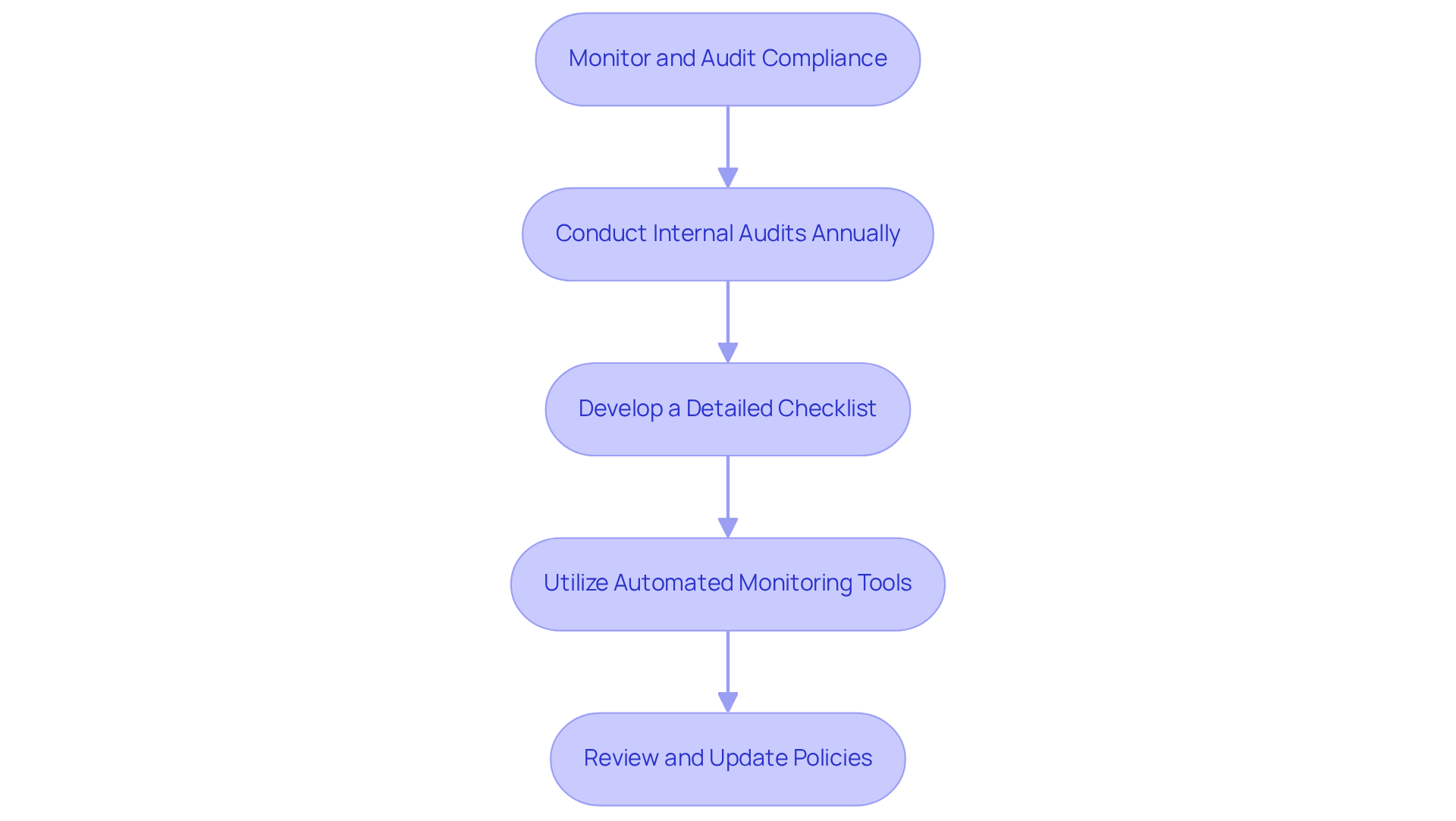
Monitor and Audit Compliance Regularly
To ensure personal data compliance with protection requirements, defense contractors must establish a systematic monitoring and auditing process. Why is this crucial? Conducting internal audits at least annually is essential for assessing adherence to CMMC and ensuring personal data compliance with other relevant regulations. Organizations should develop a detailed checklist to ensure personal data compliance with these regulatory requirements for thorough coverage during audits.
Utilizing automated adherence monitoring tools can significantly streamline this process. These tools offer real-time insights into adherence status and help identify potential vulnerabilities. Additionally, monitoring key performance indicators (KPIs) related to information protection - such as the frequency of breaches, employee training completion rates, and incident response times - provides valuable metrics for evaluating effectiveness.
Consistently reviewing and updating regulatory policies based on audit findings is vital for adapting to evolving regulations and enhancing personal data compliance. This includes:
- Establishing a formal change process for proposing and approving updates
- Maintaining version control of policies
- Archiving previous policy versions
- Effectively communicating changes to all affected personnel
In light of the fact that 72% of Q3 ransomware cases are attributed to the manufacturing sector, these structured practices are essential. They transform confusion into clarity and empower organizations to achieve CMMC compliance with confidence.
Conclusion
Ensuring personal data compliance is not just a responsibility; it’s a critical imperative for defense contractors. With evolving regulations like the Cybersecurity Maturity Model Certification (CMMC), GDPR, and CCPA, organizations must recognize that these frameworks dictate how sensitive information is handled and stress the necessity of a proactive approach to data protection. By understanding and implementing these requirements, defense contractors can effectively safeguard personal information against unauthorized access and breaches. This not only fulfills contractual obligations but also enhances overall security posture.
To achieve compliance, several key strategies stand out:
- Adopting effective data protection measures is essential.
- Fostering a culture of compliance through robust training ensures that all employees are aware of their responsibilities.
- Establishing systematic monitoring and auditing processes is crucial for identifying vulnerabilities and ensuring adherence to regulations.
Regular training sessions tailored to specific roles, combined with continuous monitoring of compliance metrics, empower defense contractors to navigate the complexities of personal data protection effectively.
But why does personal data compliance matter? The significance extends beyond mere regulatory adherence; it’s vital for building trust with clients and maintaining a competitive edge in the defense industry. Organizations that prioritize compliance and invest in comprehensive training and monitoring strategies not only protect sensitive information but also position themselves as reliable partners in an increasingly scrutinized landscape.
Taking action now to enhance cybersecurity measures and compliance protocols will yield long-term benefits. By doing so, defense contractors can ensure both operational integrity and client confidence in the years to come. Are you ready to take the necessary steps towards compliance and secure your organization’s future?
Frequently Asked Questions
What is the primary focus of personal data compliance for defense suppliers?
The primary focus is to understand and comply with the specific requirements set by the Department of Defense (DoD) and relevant regulatory authorities, particularly the Cybersecurity Maturity Model Certification (CMMC) for protecting Controlled Unclassified Information (CUI).
What is the Cybersecurity Maturity Model Certification (CMMC)?
The CMMC is a framework that outlines essential security controls necessary for protecting Controlled Unclassified Information (CUI) and is a key requirement for personal data compliance in defense contracting.
Why is personal data compliance important for defense suppliers?
Personal data compliance is important to protect personal information from unauthorized access and breaches, thereby minimizing the risk of penalties and ensuring the security of operations.
What other regulations should contractors consider for personal data compliance?
Contractors should also consider the implications of the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), especially when engaging with international clients or managing sensitive consumer data.
How can organizations benefit from proactive engagement with regulatory frameworks?
Proactive engagement with regulatory frameworks can strengthen an organization's security posture and foster trust with clients, leading to a significant reduction in breach occurrences.
What should defense firms do to maintain compliance with evolving standards?
Defense firms should regularly assess compliance requirements, stay informed about updates, and prioritize compliance to secure their operations and fulfill contractual obligations.