Master Risk Management in Computer Security for Defense Contractors
Master risk management in computer security to strengthen defenses for defense contractors.

Introduction
In an era where cyber threats are more pronounced than ever, defense contractors encounter distinct challenges in protecting sensitive information. Cybersecurity risk management is not merely a regulatory obligation; it is crucial for sustaining operational integrity and fostering trust. This article explores essential practices that empower defense contractors to navigate the intricate cybersecurity landscape, addressing pivotal questions such as:
- How can organizations effectively identify and mitigate risks while ensuring compliance with stringent standards like CMMC 2.0?
- As the stakes escalate, mastering this process becomes vital for safeguarding both assets and reputation.
Understand the Cybersecurity Risk Management Process
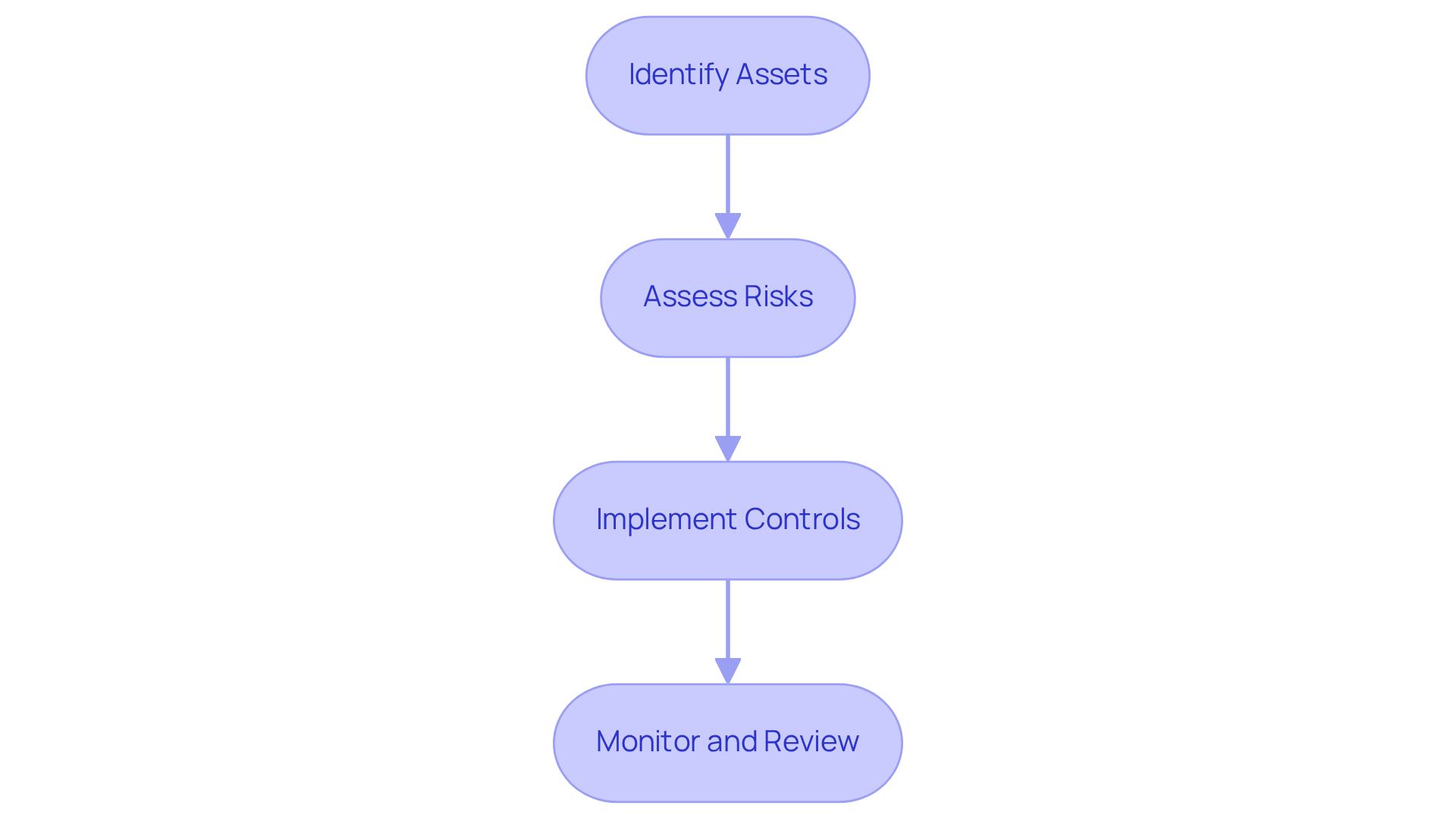
The information security threat management process is crucial for defense contractors. It involves a systematic approach to risk management in computer security, focusing on identifying, evaluating, and mitigating risks associated with information security challenges. Here’s how it unfolds:
-
Identify Assets: Recognizing all critical assets - hardware, software, and data that require protection - is the first step in building a resilient cybersecurity posture. What exactly needs safeguarding? Understanding this is essential.
-
Assess Risks: Next, evaluate potential threats and vulnerabilities that could impact these assets. This evaluation involves examining the likelihood of various threats and their potential effects on the organization. Research indicates that 95% of all data breaches involve some form of human error, underscoring the need for a thorough threat assessment.
-
Implement Controls: Develop and apply security measures to mitigate identified threats. This may include technical solutions like firewalls and encryption, alongside administrative policies and procedures. Organizations that adopt a structured approach to risk management in computer security are more likely to enhance their overall security posture. Notably, 70% of organizations faced a ransomware attack in the past year.
-
Monitor and Review: Finally, continuously observe the effectiveness of management strategies and make necessary adjustments. Regular evaluations ensure that the organization adapts to new challenges and changes in the operational environment, which is critical as the threat landscape evolves rapidly.
By mastering this process, defense contractors can lay a solid foundation for their information security initiatives. This aligns with the stringent requirements set by the Department of Defense, including the need for demonstrable, auditable security controls as mandated by CMMC 2.0 enforcement. Such a proactive approach not only aids in compliance but also strengthens resilience against the growing frequency and sophistication of cyber threats.
Identify and Assess Cybersecurity Risks
To effectively identify and assess cybersecurity risks, organizations must adopt key practices that ensure robust security measures:
-
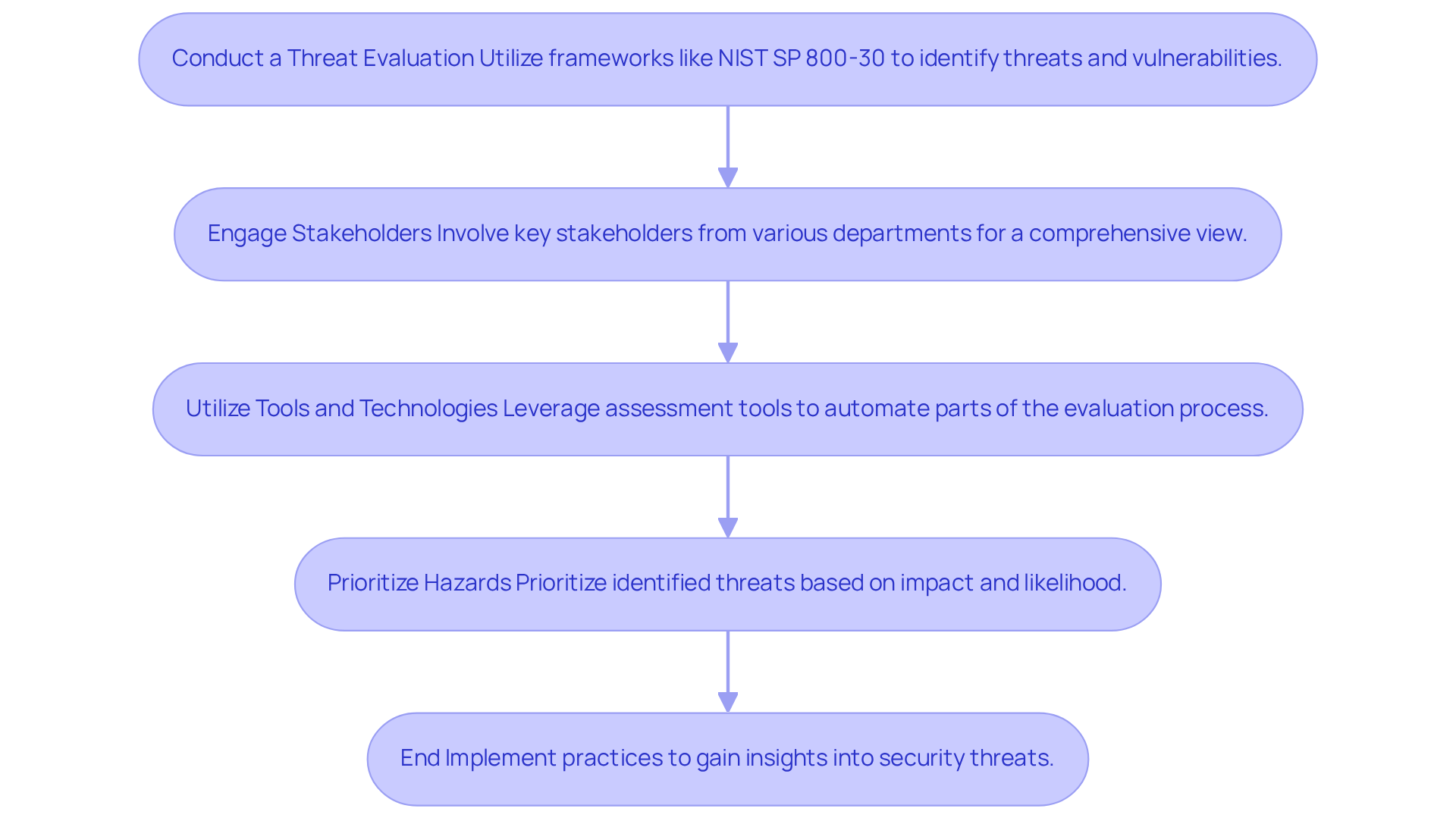
Conduct a Threat Evaluation: Start by utilizing frameworks like NIST SP 800-30, updated for 2026, to guide your threat evaluation process. This involves pinpointing potential threats, vulnerabilities, and understanding the impact of incidents on operations. Are you aware of the specific threats your organization faces?
-
Engage Stakeholders: Involve key stakeholders from various departments to gain a comprehensive view of your organization's threat landscape. By including diverse perspectives, you ensure that all possible threats are considered, fostering a culture of collective accountability in managing uncertainties.
-
Utilize Tools and Technologies: Leverage evaluation assessment tools and software to automate parts of the assessment process. This not only enhances efficiency but also improves thoroughness. Automation can significantly reduce manual workload and increase the precision of evaluations. Have you explored the latest tools available?
-
Prioritize Hazards: Once threats are identified, prioritize them based on their potential impact and likelihood. This prioritization is crucial for allocating resources effectively, allowing your organization to address the most significant threats first.
By implementing these practices, defense contractors can gain clear insights into their security threats, enabling informed decisions regarding threat control strategies. As cyber threats remain a top priority for businesses, proactive engagement in these practices is essential for ensuring compliance and safeguarding sensitive information.
Develop a Comprehensive Cybersecurity Risk Management Plan
A comprehensive cybersecurity risk management plan must encompass several essential components:
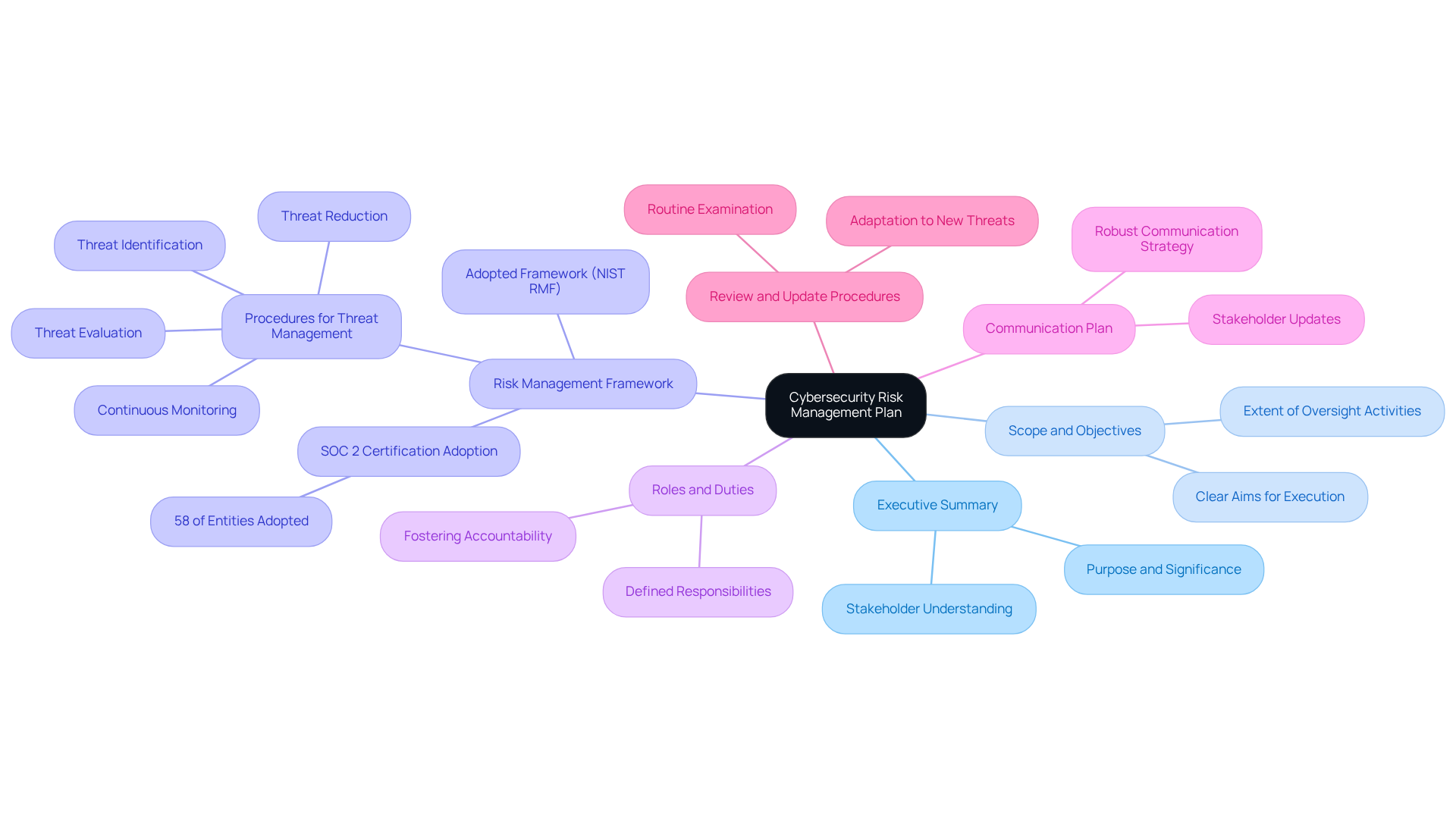
- Executive Summary: This section outlines the plan's purpose and its significance to the entity’s overarching cybersecurity strategy. It ensures that all stakeholders understand its importance.
- Scope and Objectives: Clearly define the extent of oversight activities, specifying which assets and operations are involved. Establish clear aims for the plan to guide its execution.
- Risk Management Framework: Adopt a recognized framework, such as the NIST Risk Management Framework (RMF), to steer the development and execution of the plan focused on risk management in computer security. This framework should detail procedures for threat identification, evaluation, reduction, and continuous monitoring. Notably, 58% of entities have adopted SOC 2 certification, reflecting a growing commitment to structured oversight.
- Roles and Duties: Clearly define the roles and responsibilities of team members involved in the uncertainty handling process. This clarity fosters accountability and ensures effective execution of the plan.
- Communication Plan: Establish a robust communication strategy to keep stakeholders informed about identified challenges and the status of mitigation efforts. This is crucial for maintaining transparency and trust within the organization.
- Review and Update Procedures: Integrate processes for the routine examination and modification of the plan to adapt to new threats and organizational shifts. This ensures that the strategy for handling uncertainties remains relevant and effective.
By creating a thorough threat handling strategy, defense contractors can efficiently prepare to tackle cybersecurity challenges and uphold compliance with CMMC standards. This proactive approach is vital, especially considering that the average cost of a data breach reached $4.88 million in 2025, underscoring the financial implications of inadequate management.
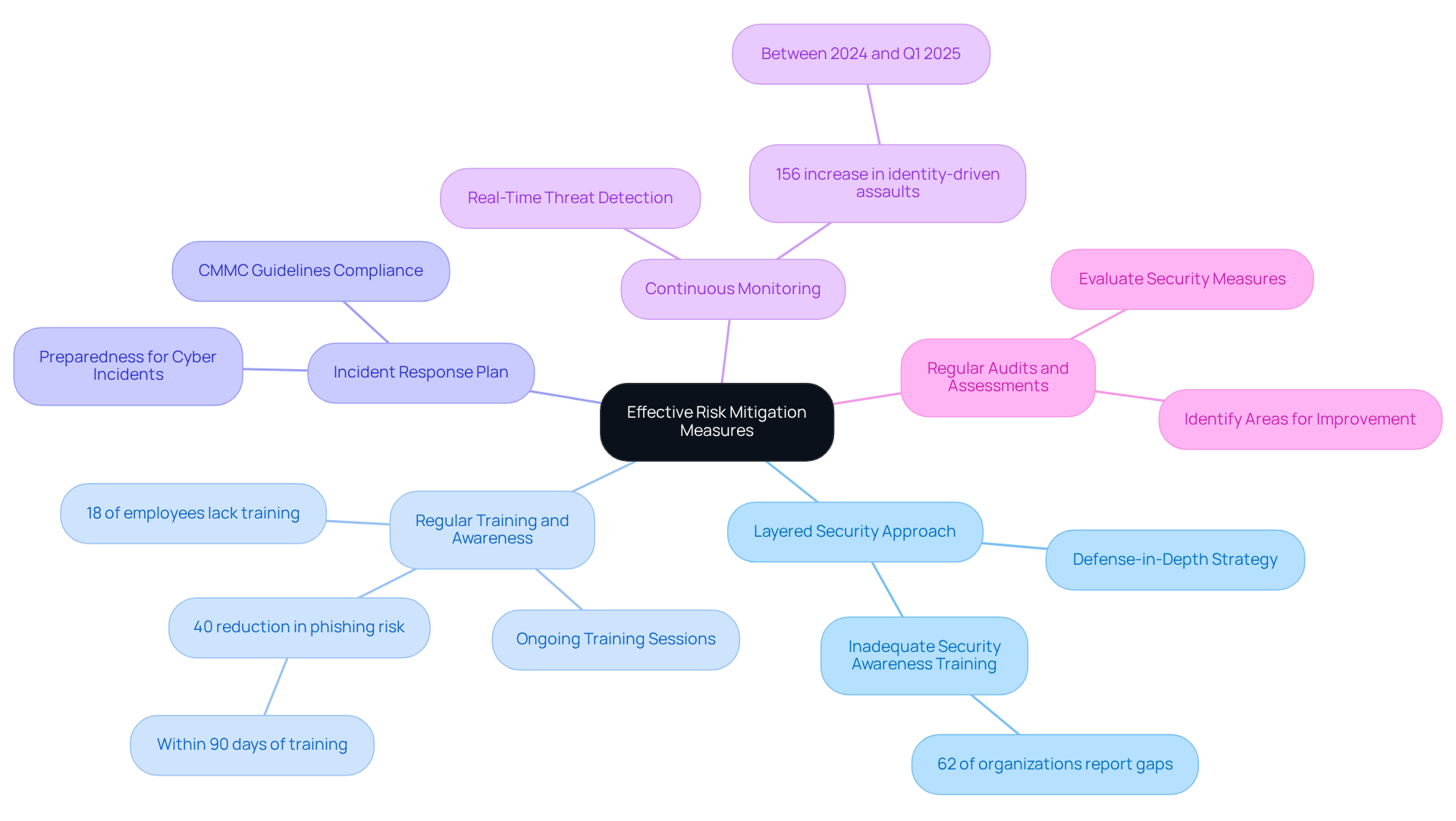
Implement Effective Risk Mitigation Measures
To implement effective risk mitigation measures and achieve CMMC compliance with confidence, organizations should consider the following strategies:
-
Layered Security Approach: Employ a defense-in-depth strategy that includes multiple layers of security controls, such as firewalls, intrusion detection systems, and endpoint protection. This approach not only enhances security but also aligns with CMMC requirements. Did you know that 62% of organizations report inadequate security awareness training? Addressing this gap is crucial.
-
Regular Training and Awareness: Conduct ongoing training sessions for employees to raise awareness about digital security threats and best practices. A knowledgeable workforce is a vital line of defense against cyber attacks. In fact, 18% of employees have never undergone training in security measures. Organizations that implement continuous security awareness training can reduce phishing risk by over 40% within 90 days, which is essential for maintaining compliance with CMMC standards.
-
Incident Response Plan: Develop and maintain an incident response plan that outlines procedures for responding to cybersecurity incidents. This plan should encompass roles, responsibilities, and communication protocols. Is your organization prepared to manage incidents effectively while meeting CMMC guidelines?
-
Continuous Monitoring: Implement continuous monitoring solutions to detect and respond to threats in real-time. This proactive strategy assists entities in staying ahead of potential attacks. Consider this: identity-driven assaults rose by 156% between 2024 and Q1 2025. Staying vigilant is a vital aspect of CMMC compliance.
-
Regular Audits and Assessments: Schedule regular audits and assessments to evaluate the effectiveness of security measures and identify areas for improvement. These evaluations are crucial for ensuring ongoing compliance with CMMC requirements and strengthening the overall security posture of the organization.
By adopting these risk mitigation measures, defense contractors can significantly enhance their risk management in computer security and ensure compliance with CMMC requirements.
Conclusion
Mastering risk management in computer security is not just essential; it’s the backbone of a resilient cybersecurity framework for defense contractors. By systematically identifying, assessing, and mitigating risks, organizations can comply with stringent regulations while bolstering their defenses against an ever-evolving threat landscape. These proactive measures are vital components in establishing a robust security posture that protects critical assets and sensitive information.
Key insights from the article underscore the importance of thorough asset identification, risk assessment, and the implementation of effective controls. How can organizations empower themselves? By engaging stakeholders, utilizing advanced tools, and prioritizing risks, they can make informed decisions that enhance their security. Moreover, developing a comprehensive cybersecurity risk management plan that includes clear roles, communication strategies, and regular reviews is paramount for ongoing success. Continuous monitoring and employee training are not just recommendations; they are necessities for a well-rounded approach to cybersecurity.
In an age where cyber threats are increasingly sophisticated and prevalent, defense contractors must prioritize their cybersecurity risk management strategies. By adopting these best practices, organizations enhance their compliance with CMMC standards and significantly reduce the likelihood of costly data breaches. The time to act is now. Investing in a proactive cybersecurity strategy is not merely a compliance requirement; it’s a critical necessity for safeguarding the future of defense contracting.
Frequently Asked Questions
What is the cybersecurity risk management process?
The cybersecurity risk management process is a systematic approach used by defense contractors to identify, evaluate, and mitigate risks associated with information security challenges.
What is the first step in the cybersecurity risk management process?
The first step is to identify critical assets, including hardware, software, and data that require protection.
How are risks assessed in the cybersecurity risk management process?
Risks are assessed by evaluating potential threats and vulnerabilities that could impact identified assets, including examining the likelihood of various threats and their potential effects on the organization.
What is a significant statistic regarding data breaches mentioned in the article?
Research indicates that 95% of all data breaches involve some form of human error.
What does implementing controls involve?
Implementing controls involves developing and applying security measures, such as technical solutions like firewalls and encryption, as well as administrative policies and procedures to mitigate identified threats.
Why is monitoring and reviewing important in the cybersecurity risk management process?
Monitoring and reviewing are important to continuously observe the effectiveness of management strategies and make necessary adjustments, ensuring the organization adapts to new challenges and changes in the operational environment.
How does the cybersecurity risk management process help defense contractors?
By mastering this process, defense contractors can establish a solid foundation for their information security initiatives, comply with Department of Defense requirements, and strengthen resilience against cyber threats.
What are the implications of CMMC 2.0 enforcement for organizations?
CMMC 2.0 enforcement requires organizations to demonstrate auditable security controls, which emphasizes the need for a proactive approach to cybersecurity.