Master the Cyber Risk Management Process: A Step-by-Step Guide
Learn the essential steps of the cyber risk management process to safeguard your organization's data.

Introduction
The rising frequency and sophistication of cyber threats have made effective risk management a crucial part of any organizational strategy. By mastering the cyber risk management process, companies can not only protect their digital assets but also ensure compliance with essential regulations like CMMC. But this complex landscape raises important questions:
- How can organizations systematically identify and mitigate risks?
- What strategies will genuinely enhance their cybersecurity posture in an ever-evolving threat environment?
This guide provides a step-by-step approach to mastering cyber risk management, equipping organizations with the necessary tools to thrive amidst uncertainty. With the right strategies in place, you can navigate these challenges confidently and secure your organization’s future.
Understand Cybersecurity Risk Management
The cyber risk management process is a structured approach that focuses on identifying, evaluating, and mitigating risks to a company's information systems. This cyber risk management process is crucial for protecting the confidentiality, integrity, and availability of data against emerging threats. Let's break down the key components:
-
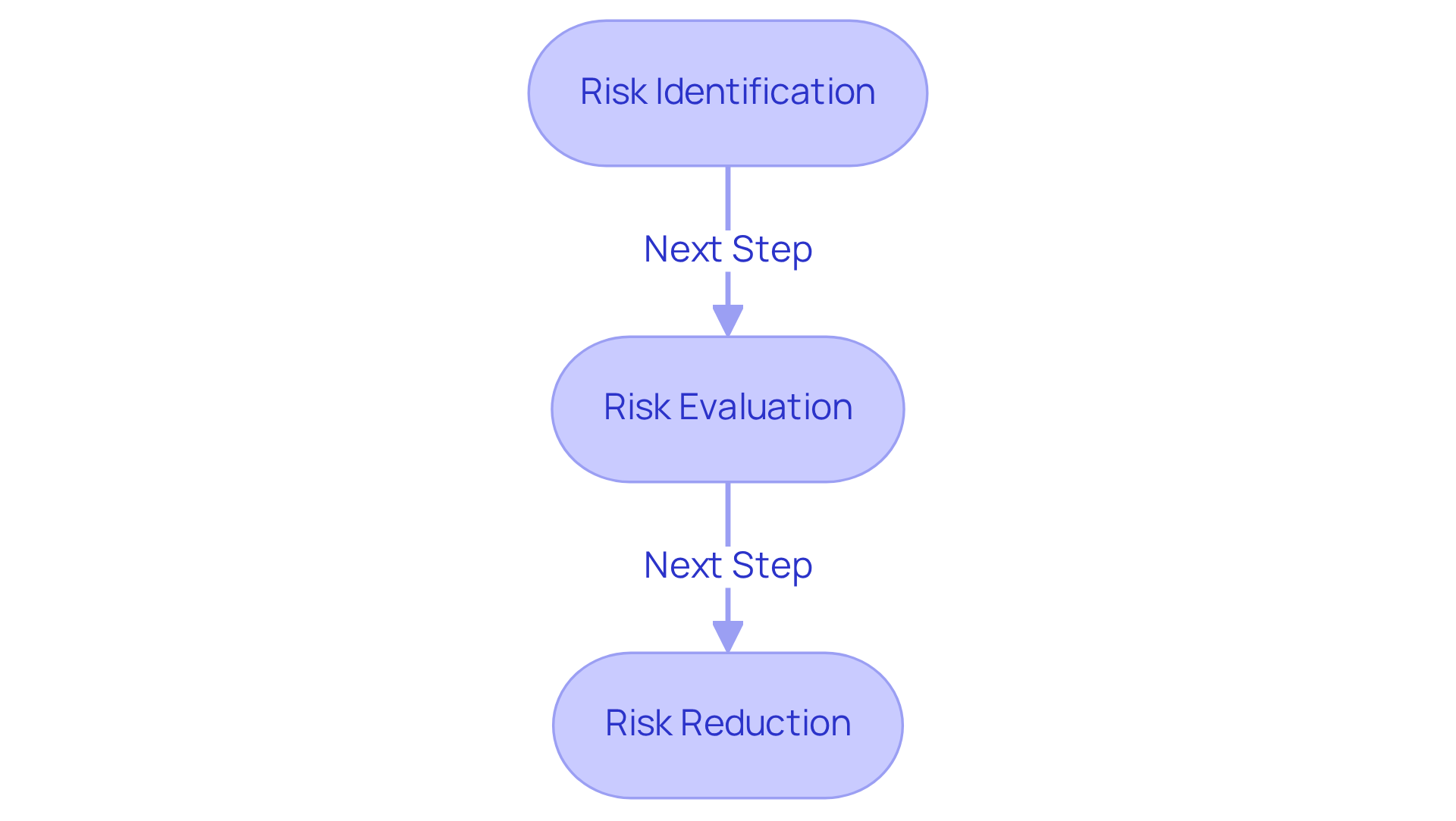
Risk Identification: Recognizing potential risks that could impact your organization is the first step. This includes cyberattacks, data breaches, and insider threats. Did you know that 88% of all cyber incidents are linked to human errors? This statistic underscores the importance of thorough threat identification. The CMMC Info Hub provides valuable resources to help you effectively recognize these hazards.
-
Risk Evaluation: Once risks are identified, assessing their likelihood and potential impact is essential for prioritization. Organizations that implement structured threat management frameworks, like ISO/IEC 27005 or NIST SP 800-30, can effectively evaluate and address cybersecurity challenges as part of their cyber risk management process. Notably, 71% of entities reported an increase in cyberattack frequency over the past year, highlighting the need for proactive assessment strategies. The CMMC Info Hub offers insights and tools to assist in this evaluation process.
-
Risk Reduction: Developing strategies to mitigate or eliminate threats is vital. This may involve implementing security controls, policies, and procedures tailored to the specific vulnerabilities identified. For example, entities that conduct regular risk assessments not only enhance their security posture but also ensure compliance with regulatory frameworks such as GDPR and HIPAA, which mandate such evaluations. The CMMC Info Hub can support organizations in crafting effective mitigation strategies within their cyber risk management process.
Understanding these components is essential for organizations aiming to build a robust cybersecurity framework that meets compliance standards, particularly within the CMMC framework. As Dr. Rey Leclerc Sveinsson emphasizes, 'A thorough threat evaluation enhances a firm's capacity to respond effectively to cyber incidents.' This highlights the critical need to integrate threat management into the core of cybersecurity strategies.
Follow the Cybersecurity Risk Management Process
To effectively manage cybersecurity risks, organizations must adopt a structured process that aligns with CMMC compliance requirements. This approach not only safeguards your assets but also ensures adherence to the cyber risk management process and regulatory standards.
-
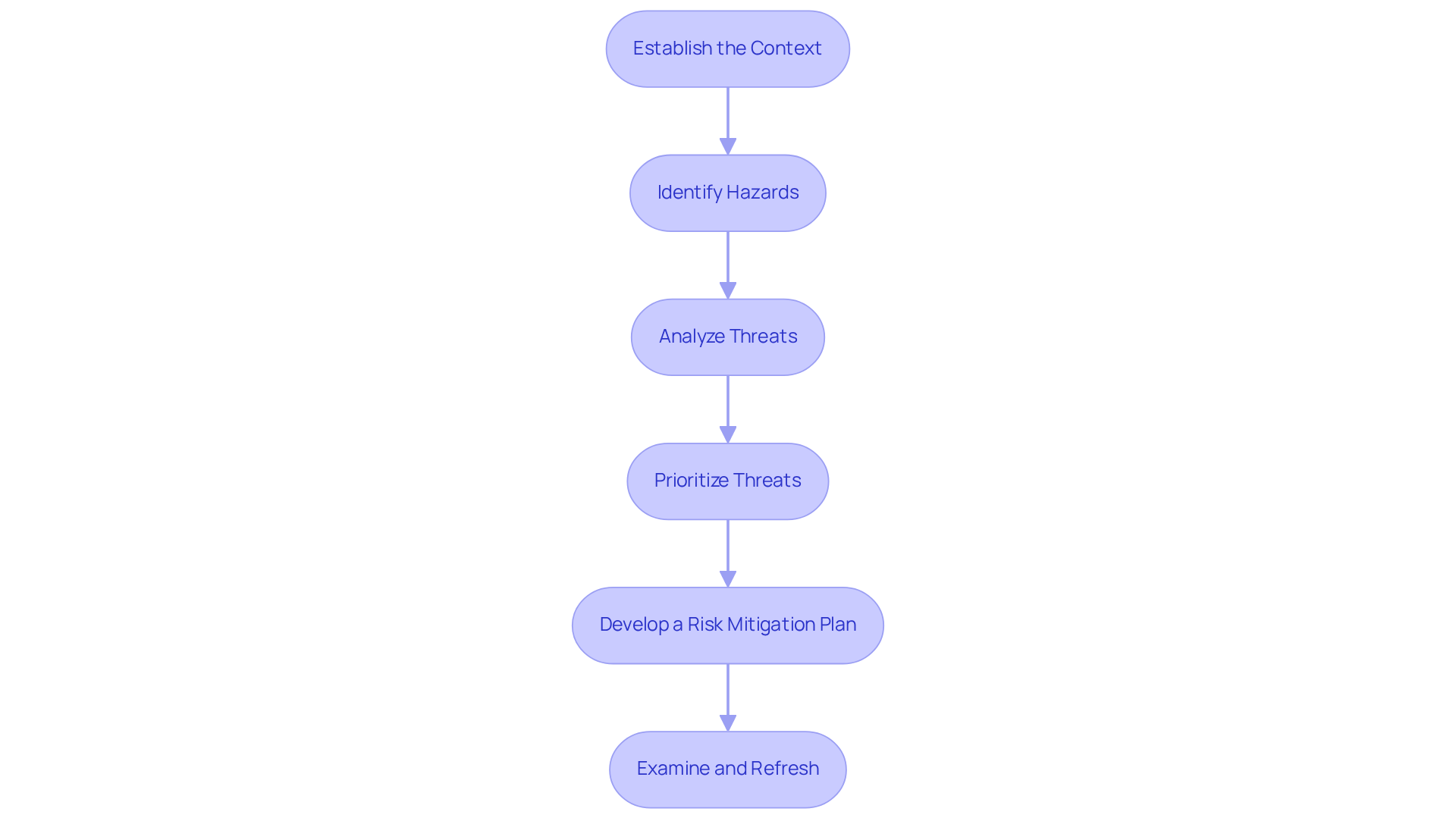
Establish the Context: Begin by defining the scope of your hazard management efforts. What assets need protection? What regulatory requirements must you meet, particularly those outlined in the CMMC framework?
-
Identify Hazards: Conduct thorough evaluations to recognize potential dangers. This includes both internal and external challenges, with a keen eye on CMMC-specific vulnerabilities. Are you aware of all possible threats?
-
Analyze Threats: Assess the identified threats based on their likelihood and potential impact on your organization. Reference CMMC requirements to guide your assessment. How do these threats affect your compliance journey?
-
Prioritize Threats: Rank the potential issues to focus on those that pose the greatest danger to your organization. Which threats could hinder your ability to achieve CMMC compliance?
-
Develop a Risk Mitigation Plan: Create a comprehensive plan that outlines how to address each identified threat. Include mitigation strategies and designate responsible parties, ensuring alignment with CMMC controls. What steps will you take to mitigate these risks?
The organization is implementing a cyber risk management process to enhance its security measures. Implement the Plan: Execute the management strategies and ensure that all stakeholders are informed of their responsibilities in maintaining compliance with CMMC standards. Are your team members clear on their roles?
- Examine and Refresh: Consistently assess the management process to adapt to new challenges and changes in the organizational environment. Integrate feedback and insights from CMMC compliance evaluations. How will you ensure continuous improvement in your risk management efforts?
Identify and Assess Cybersecurity Risks
Identifying and assessing cybersecurity risks is crucial for any organization within the cyber risk management process. Here are the key steps to effectively navigate this process:
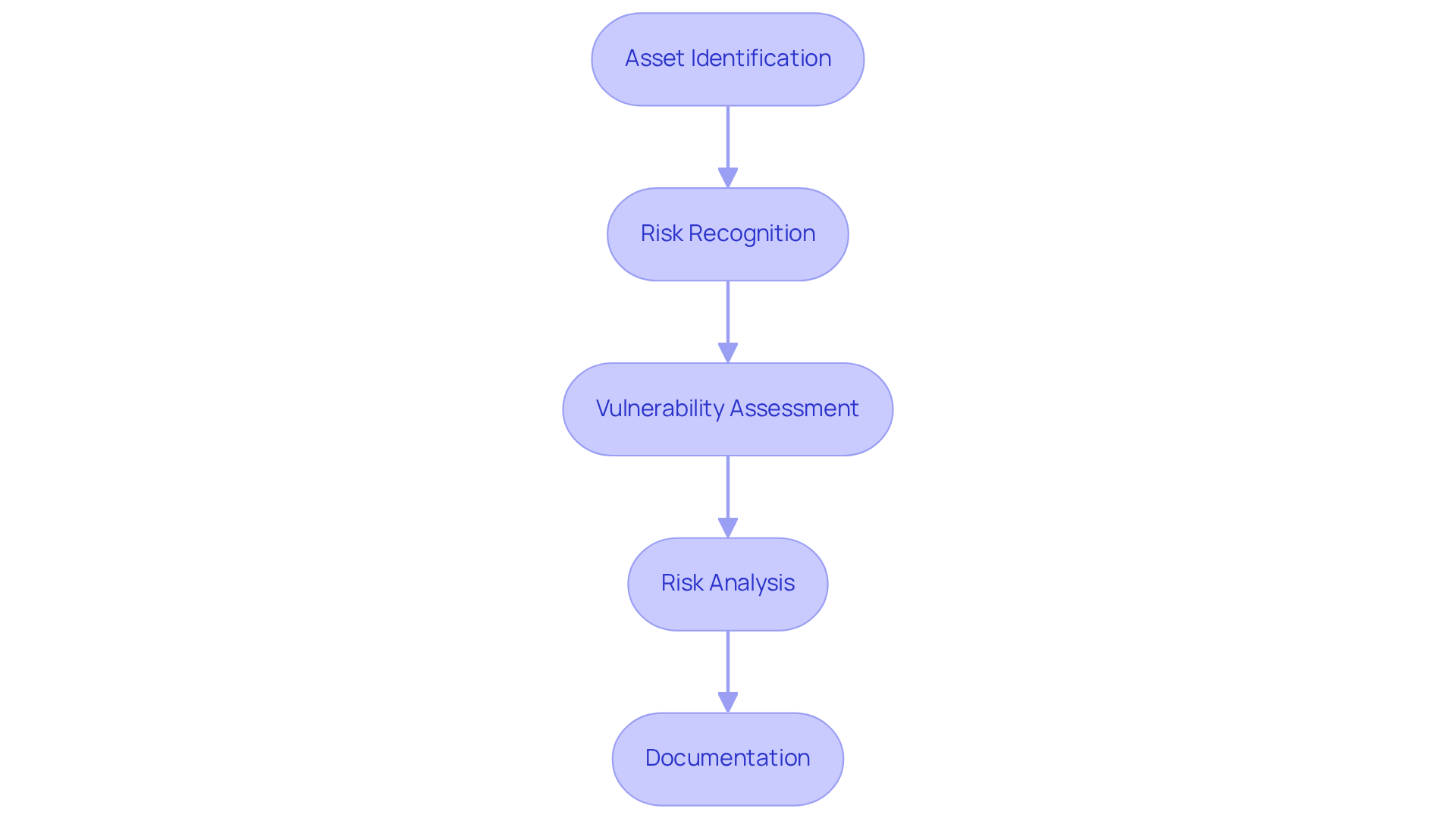
- Asset Identification: Begin by cataloging all critical assets, including hardware, software, data, and intellectual property. What do you rely on most?
- Risk Recognition: Next, identify possible risks to these assets. Consider threats like malware, phishing attacks, and insider risks. Are you aware of the vulnerabilities that could be exploited?
- Vulnerability Assessment: Assess the weaknesses in your systems that could be targeted. This may involve utilizing tools and frameworks designed to identify vulnerabilities. How robust are your defenses?
- Risk Analysis: Analyze the likelihood of each threat exploiting a vulnerability and the potential impact on your organization. Use both qualitative and quantitative techniques to evaluate uncertainties. What would be the consequences of a breach?
- Documentation: Finally, maintain a register that records identified threats, their assessments, and any relevant details. This facilitates ongoing monitoring and review. Are you keeping track of your cybersecurity landscape?
By following these steps, you can build a solid foundation for your cybersecurity strategy that includes a robust cyber risk management process, ensuring that you are prepared to face potential threats head-on.
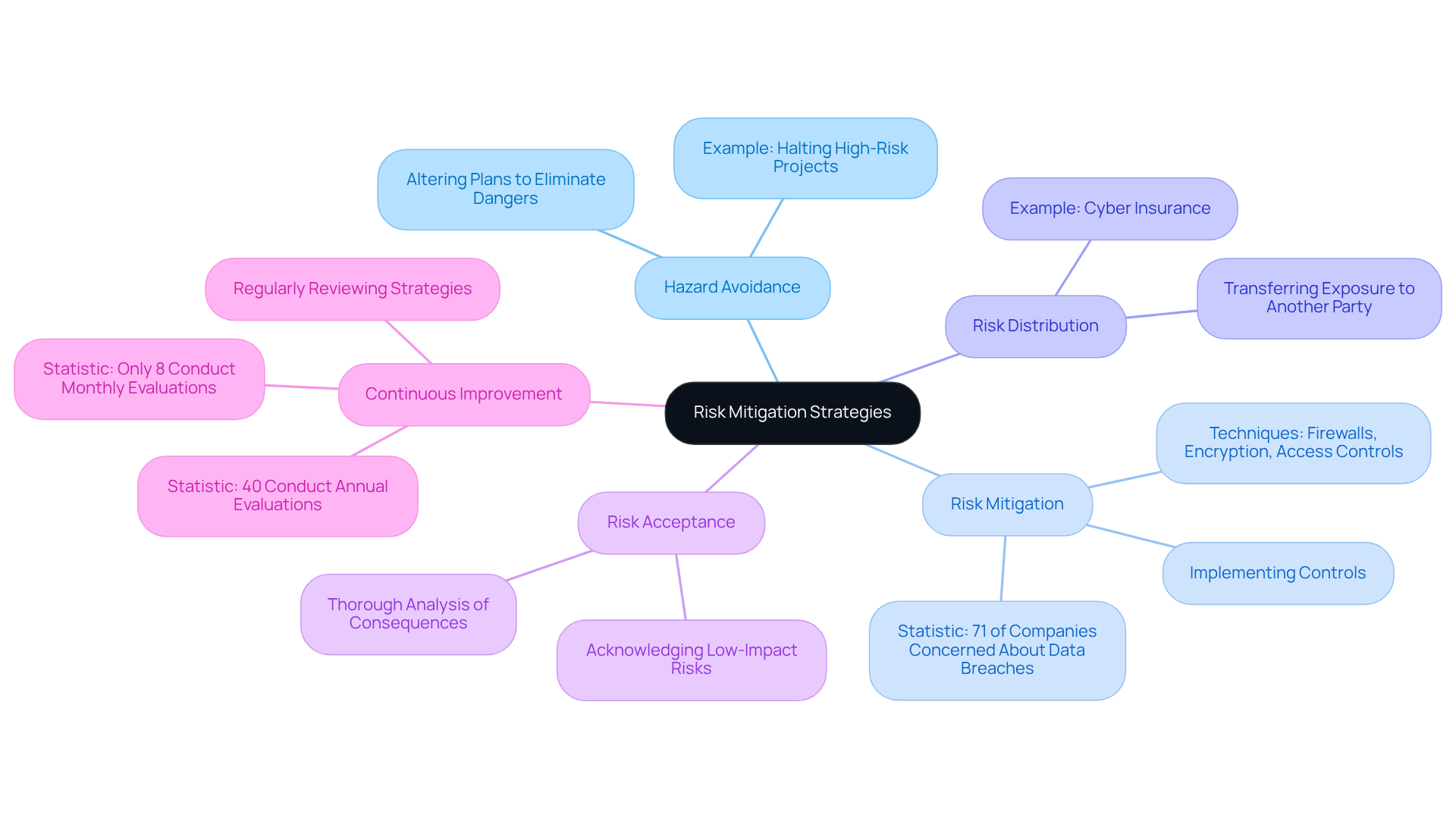
Develop Risk Mitigation Strategies
To effectively tackle cyber challenges, organizations must develop robust mitigation strategies within the cyber risk management process after identifying and assessing potential threats. Here are key techniques to consider:
-
Hazard Avoidance: This strategy involves altering plans to eliminate potential dangers. For example, a defense contractor might decide to halt a project that presents significant cybersecurity risks, thereby avoiding associated vulnerabilities.
-
Risk Mitigation: Implementing controls is crucial for reducing the likelihood or impact of threats. Techniques such as deploying firewalls, encryption, and access controls are essential. According to Secureframe, 71% of companies report that data breaches are their top concern regarding third-party usage, underscoring the importance of these protective measures.
-
Risk Distribution: Organizations can transfer exposure to another party, such as through insurance or outsourcing specific functions. This approach helps mitigate financial impacts from potential breaches, allowing companies to concentrate on core operations while effectively managing uncertainties.
-
Risk Acceptance: In some cases, organizations may choose to acknowledge specific uncertainties and accept them, particularly when they are low-impact and do not warrant extensive mitigation efforts. This decision should stem from a thorough analysis of potential consequences.
-
Continuous Improvement: Regularly reviewing and updating threat mitigation strategies is vital in response to evolving dangers and vulnerabilities. Organizations should conduct regular cyber threat evaluations. Alarmingly, only 8% of organizations performed these evaluations monthly in 2025, while 40% did so annually. This ongoing assessment is crucial to the cyber risk management process, ensuring that defenses remain effective against new challenges. With an estimated 800,000 cyberattacks occurring annually in 2025, the necessity of implementing these mitigation strategies cannot be overstated.
By applying these strategies, defense contractors can enhance their cybersecurity posture, minimize vulnerabilities, and more effectively protect sensitive information amid rising cyber risks.
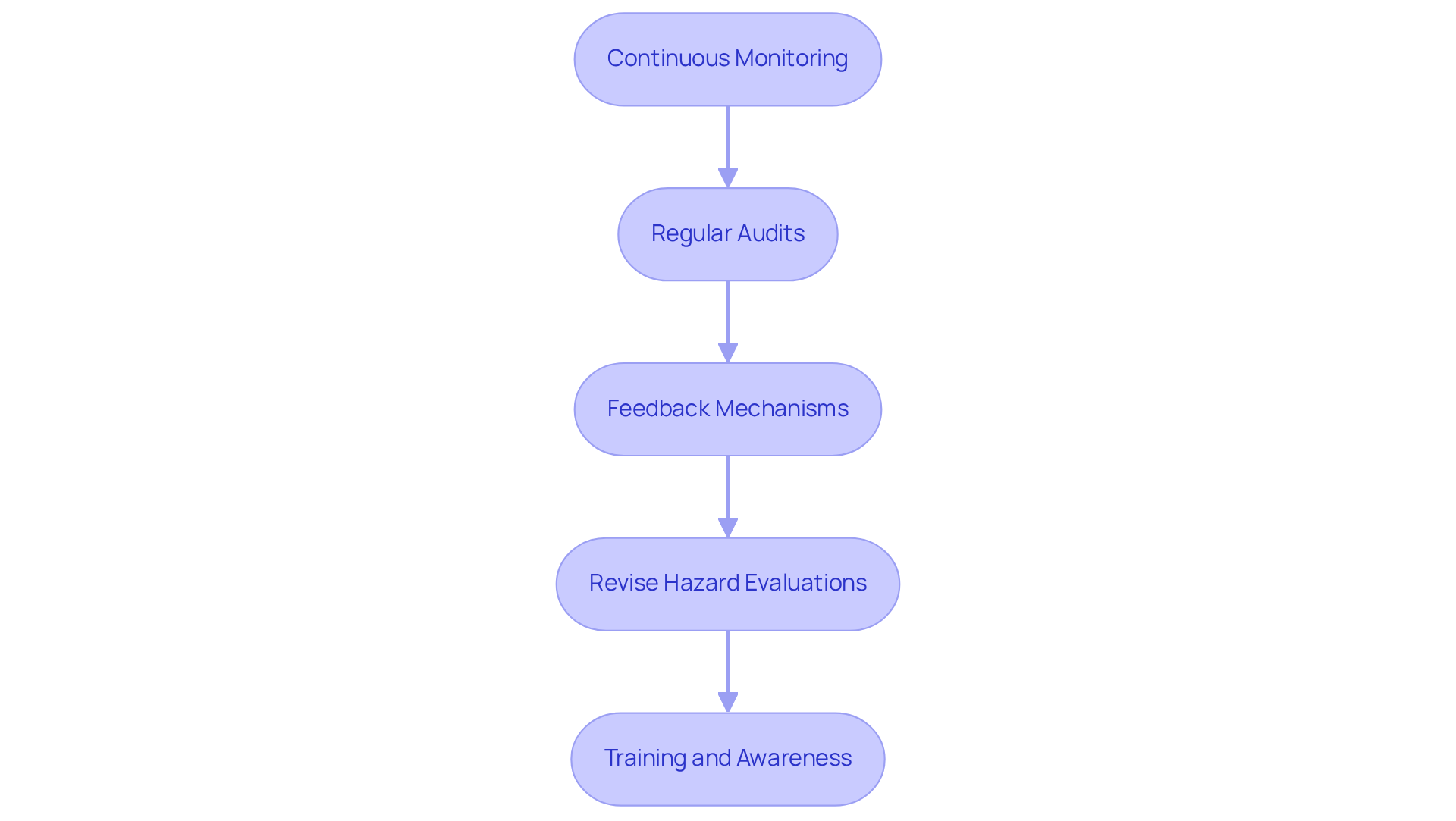
Implement Ongoing Monitoring and Review
To enhance the effectiveness of your cybersecurity risk management process, implementing ongoing monitoring and review strategies is crucial:
-
Continuous Monitoring: Are you leveraging automated tools like external attack surface management (EASM) and compliance monitoring solutions? These tools continuously assess your systems for vulnerabilities and threats, providing real-time notifications for suspicious activities. This ensures prompt responses to potential breaches. Research indicates that organizations employing continuous monitoring experience a significant reduction in incident response times, with timely alerts preventing breaches before they escalate. For instance, automated compliance tools can quickly alert you when a danger threshold is exceeded, thereby improving your company's responsiveness.
-
Regular Audits: Have you conducted regular audits of your management processes? These audits are essential for ensuring compliance with internal policies as part of the cyber risk management process and regulatory requirements. They should evaluate the effectiveness of your monitoring tools and identify any gaps in your cyber risk management process. Studies show that organizations with regular assessments are better equipped to adapt to evolving challenges, maintaining a clearer understanding of their vulnerability landscape. In fact, 61% of companies have simulated worst-case scenarios, significantly enhancing their preparedness.
-
Feedback Mechanisms: Are you creating strong channels for feedback from stakeholders, including employees and management? Engaging with team members can reveal insights that enhance your overall cybersecurity framework and foster a culture of vigilance. This collaborative approach can lead to continuous improvement in your management strategies.
-
Revise Hazard Evaluations: How often do you review and modify your hazard evaluations? Consistently updating these evaluations to reflect changes in the threat landscape and organizational structure is vital. This proactive approach ensures that your strategies within the cyber risk management process remain relevant and effective against emerging threats. Ongoing threat monitoring provides real-time insights into third-party vulnerabilities, enabling timely adjustments to your evaluations.
-
Training and Awareness: Are you providing ongoing training for employees? Keeping them informed about cybersecurity threats and best practices for mitigation is essential. Cybersecurity professionals emphasize that a well-informed workforce serves as a critical line of defense against cyber threats. Regular training sessions can significantly enhance employees' ability to identify and respond to potential threats, ultimately strengthening your organization's security posture. As Jason Venner noted, effective tools should simplify the lives of CIOs and CISOs, facilitating better governance, risk, and compliance.
Conclusion
Mastering the cyber risk management process is not just essential; it’s a critical necessity for organizations aiming to protect their information systems from an ever-evolving landscape of cyber threats. Are you aware of the intricacies involved in risk identification, evaluation, and reduction? By understanding these elements, businesses can establish a structured approach that safeguards their assets and ensures compliance with regulatory standards like CMMC.
This guide outlines key components of the cyber risk management process, including:
- Establishing context
- Identifying hazards
- Analyzing threats
- Developing robust mitigation strategies
The importance of ongoing monitoring and regular audits cannot be overstated. These practices help organizations adapt to new challenges and maintain a proactive stance against potential vulnerabilities. Moreover, engaging employees in training and fostering a culture of vigilance significantly strengthens an organization’s cybersecurity posture.
In a landscape where cyber incidents are increasingly prevalent, implementing a comprehensive cyber risk management process is not merely a best practice; it’s a necessity. Organizations must take decisive action to protect their data and ensure resilience against cyber threats. By prioritizing these strategies, companies can enhance their security measures and build trust with stakeholders, paving the way for sustainable success in the digital age.
Frequently Asked Questions
What is the cyber risk management process?
The cyber risk management process is a structured approach that focuses on identifying, evaluating, and mitigating risks to a company's information systems to protect the confidentiality, integrity, and availability of data against emerging threats.
What are the key components of cyber risk management?
The key components include Risk Identification, Risk Evaluation, and Risk Reduction. These steps involve recognizing potential risks, assessing their likelihood and impact, and developing strategies to mitigate or eliminate those risks.
How important is risk identification in the cyber risk management process?
Risk identification is crucial as it involves recognizing potential risks such as cyberattacks, data breaches, and insider threats. Statistics show that 88% of cyber incidents are linked to human errors, emphasizing the need for thorough threat identification.
What frameworks can organizations use for risk evaluation?
Organizations can use structured threat management frameworks like ISO/IEC 27005 or NIST SP 800-30 to effectively evaluate and address cybersecurity challenges as part of their cyber risk management process.
What strategies can be employed for risk reduction?
Strategies for risk reduction may include implementing security controls, policies, and procedures tailored to specific vulnerabilities, as well as conducting regular risk assessments to enhance security and ensure compliance with regulations like GDPR and HIPAA.
How does the CMMC framework relate to cyber risk management?
The CMMC framework provides compliance standards that organizations must meet, making it essential to integrate threat management into their cybersecurity strategies to safeguard assets and adhere to regulatory requirements.
What steps should organizations take to follow the cyber risk management process?
Organizations should establish the context, identify hazards, analyze threats, prioritize threats, develop a risk mitigation plan, implement the plan, and consistently examine and refresh the management process to adapt to new challenges.
Why is it important to prioritize threats?
Prioritizing threats allows organizations to focus on those that pose the greatest danger, ensuring that they address issues that could hinder their ability to achieve CMMC compliance effectively.
What role does continuous improvement play in cyber risk management?
Continuous improvement is essential for adapting to new challenges and changes in the organizational environment, integrating feedback from CMMC compliance evaluations to enhance the overall risk management efforts.