Understanding the Most Common Digital Attacks and Their Impact
Explore the most common digital attack types and their significant impacts on organizations.

Introduction
Digital threats are an ever-present danger in our interconnected world, posing significant risks to the integrity and confidentiality of information systems. As organizations face the financial and reputational fallout from these attacks, understanding the most common digital assaults becomes crucial for developing effective defense strategies. How can businesses protect themselves in an environment where cyber threats are evolving rapidly and becoming increasingly sophisticated?
This article explores the nature of digital attacks, their implications, and the proactive measures organizations must adopt to safeguard their assets and maintain stakeholder trust. By recognizing the landscape of digital threats, businesses can take informed steps to fortify their defenses and ensure resilience against potential breaches.
Define Digital Attacks and Their Significance
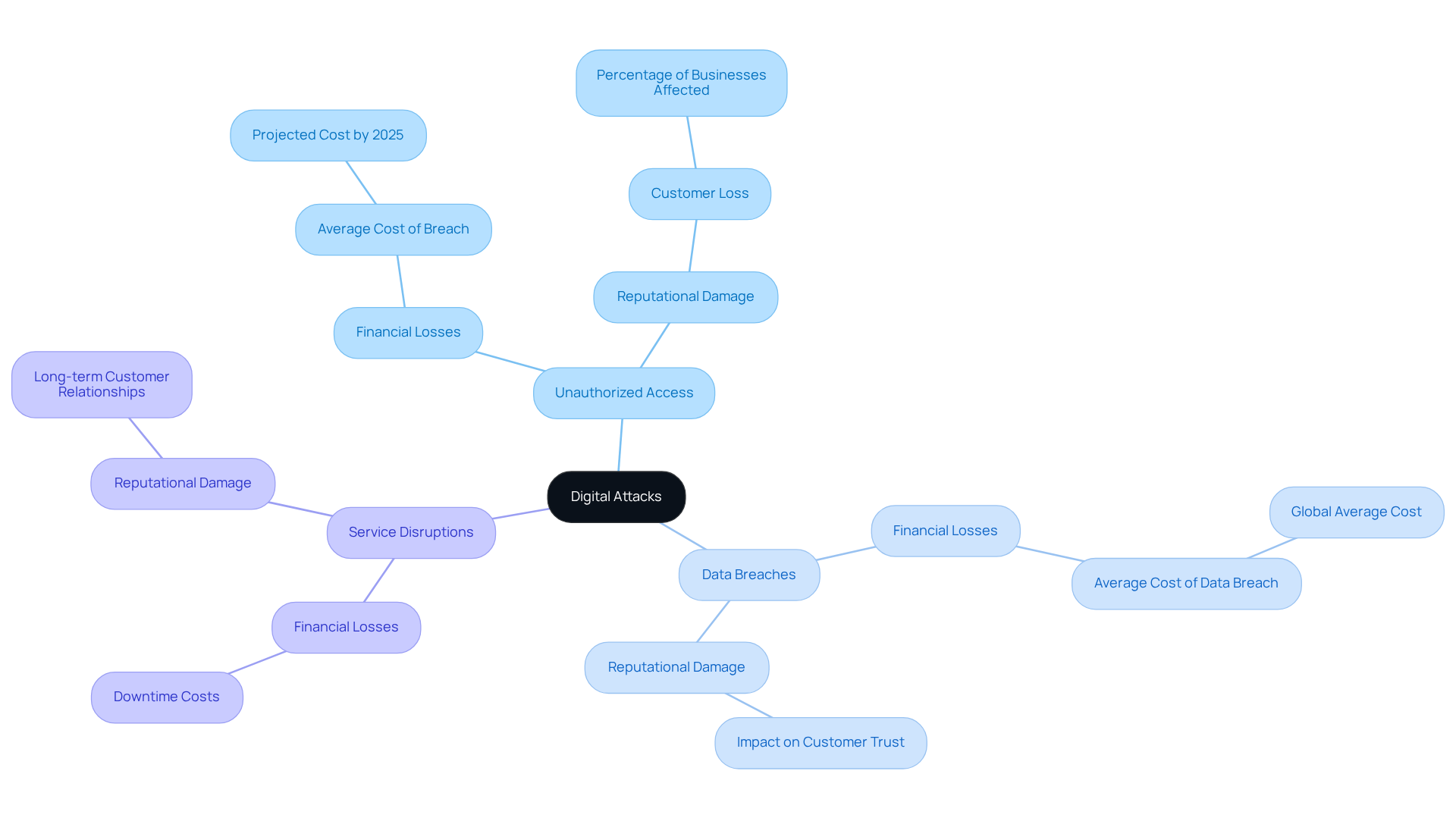
Digital threats pose serious risks to the integrity, confidentiality, and availability of information systems, networks, and devices. The most common digital attack can manifest in various ways, such as:
- Unauthorized access
- Data breaches
- Service disruptions
The consequences of these digital assaults are significant, often resulting in substantial financial losses and damage to a company's reputation. For example, the average cost of a data breach is projected to soar to $10.22 million by 2025, underscoring the financial strain companies endure when their systems are compromised. Moreover, 43% of businesses report losing existing customers due to cyberattacks, highlighting the direct link between security incidents and reputational damage.
Cybersecurity experts emphasize that the evolving nature of these threats necessitates a proactive approach to safeguarding sensitive information and ensuring compliance with regulations like the Cybersecurity Maturity Model Certification (CMMC). As cyber threats continue to escalate, understanding the nature and implications of the most common digital attack is vital for organizations striving to protect their assets and maintain trust with stakeholders.
The Info Hub stands as your comprehensive resource, offering actionable strategies and practical guidance tailored for defense contractors like you. By leveraging the insights and experiences shared in the Info Hub, you can better equip your organization to mitigate the risks associated with digital threats and confidently meet the required standards.
Explore Types of Digital Attacks
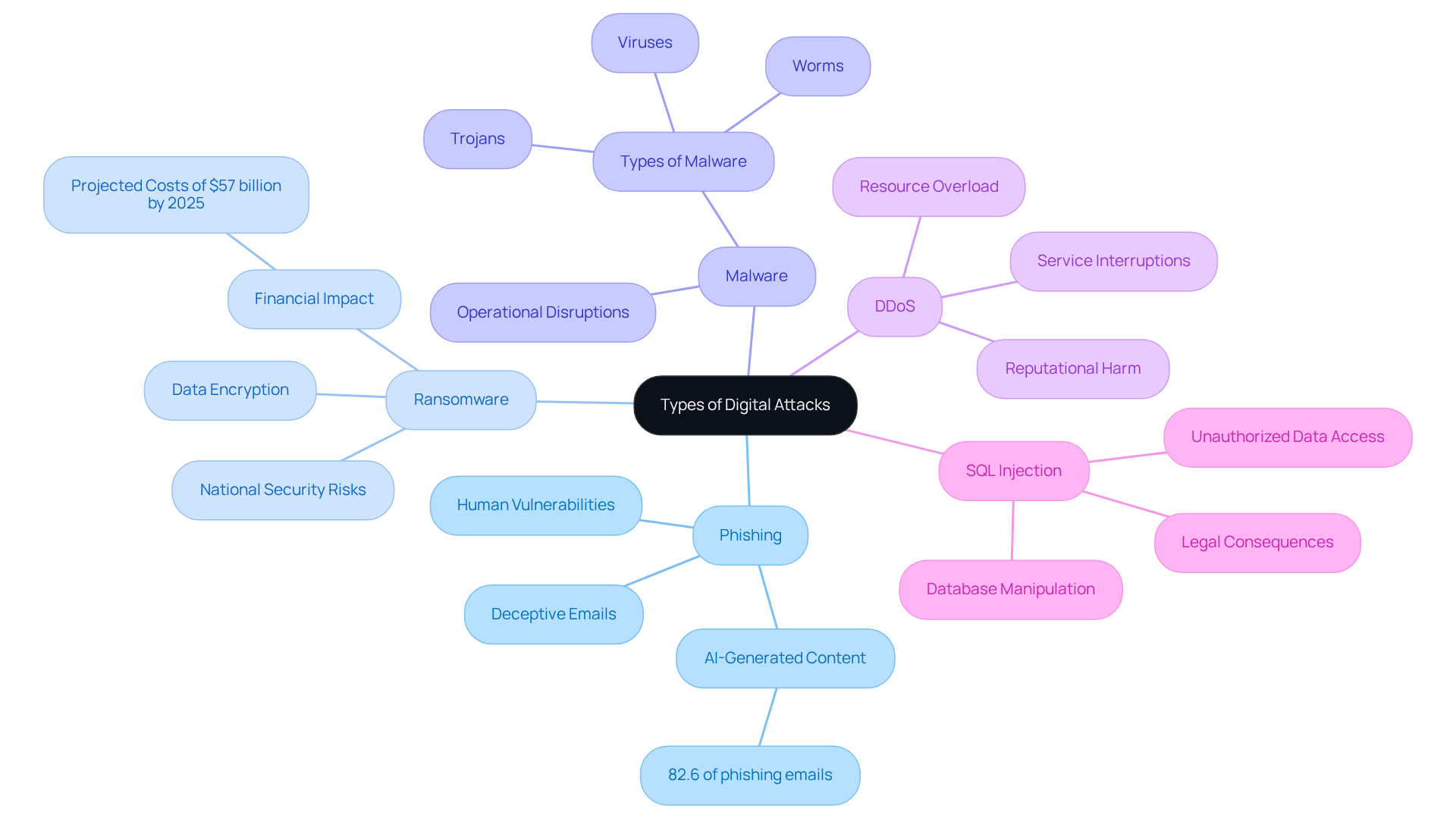
Among the various forms of digital assaults, the most common digital attack presents distinct traits and objectives that pose significant threats to organizations, especially defense contractors. Understanding these threats is essential for implementing effective security measures and ensuring compliance with CMMC requirements.
-
Phishing: Deceptive emails or messages designed to trick individuals into revealing sensitive information, such as passwords or credit card numbers, are on the rise. With 82.6% of phishing emails now utilizing AI-generated content, the complexity of these threats is increasing, making them harder to detect.
-
Ransomware: This malicious software encrypts a victim's data and demands payment for decryption. The financial impact is staggering, with global damage costs projected to reach $57 billion annually by 2025. For defense contractors, ransomware incidents can severely compromise national security and operational efficiency, potentially exposing sensitive military and defense-related information.
-
Malware: This broad category includes various malicious software, such as viruses, worms, and Trojans, aimed at damaging or disrupting systems. Malware exploits vulnerabilities in software and hardware, leading to significant operational disruptions.
-
DDoS (Distributed Denial of Service): This method overwhelms a target's resources, rendering it unavailable to users. Such assaults can interrupt services and cause reputational harm, particularly for entities that rely heavily on online operations.
-
SQL Injection: This technique exploits vulnerabilities in web applications to manipulate databases and gain unauthorized access to data. It can lead to data breaches, exposing sensitive information and resulting in legal consequences for organizations that fail to protect their data.
The evolving cyber threat landscape emphasizes that organizations must adopt a security-first approach to combat the most common digital attack. By consistently monitoring their systems and establishing robust protections against these frequent digital intrusions, defense contractors can enhance their security posture. Gaining clarity on these threats enables them to implement practical strategies that not only bolster security but also ensure compliance with CMMC requirements.
Trace the Evolution of Digital Attacks
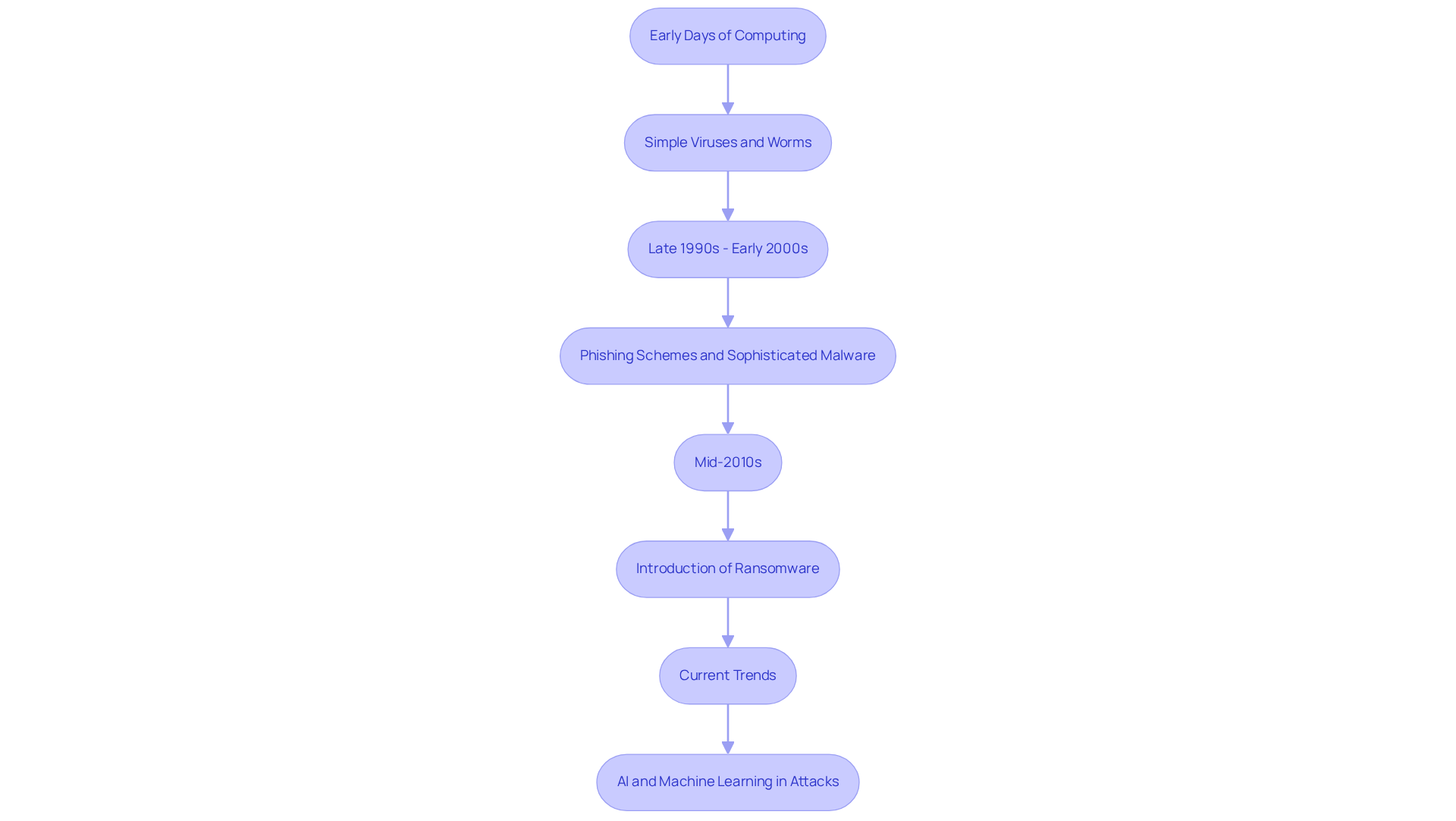
The evolution of the most common digital attack is a critical topic that requires our attention. It traces back to the early days of computing, where simple viruses and worms posed the primary threats. As technology advanced, the most common digital attack became increasingly complex. In the late 1990s and early 2000s, the rise of the internet led to a surge in phishing schemes and the emergence of more sophisticated malware. Notably, the introduction of ransomware in the mid-2010s marked a significant turning point as it became the most common digital attack, with attackers leveraging encryption to extort money from victims.
Today, the most common digital attack is characterized by the use of advanced techniques, including artificial intelligence and machine learning. These innovations enable perpetrators to automate and expand their operations, making them more formidable than ever. This evolution underscores the pressing need for continuous adaptation in cybersecurity strategies. Organizations must remain vigilant and proactive in combating emerging threats. Are your cybersecurity measures keeping pace with these developments? It's essential to evaluate and enhance your defenses regularly to safeguard against potential intrusions.
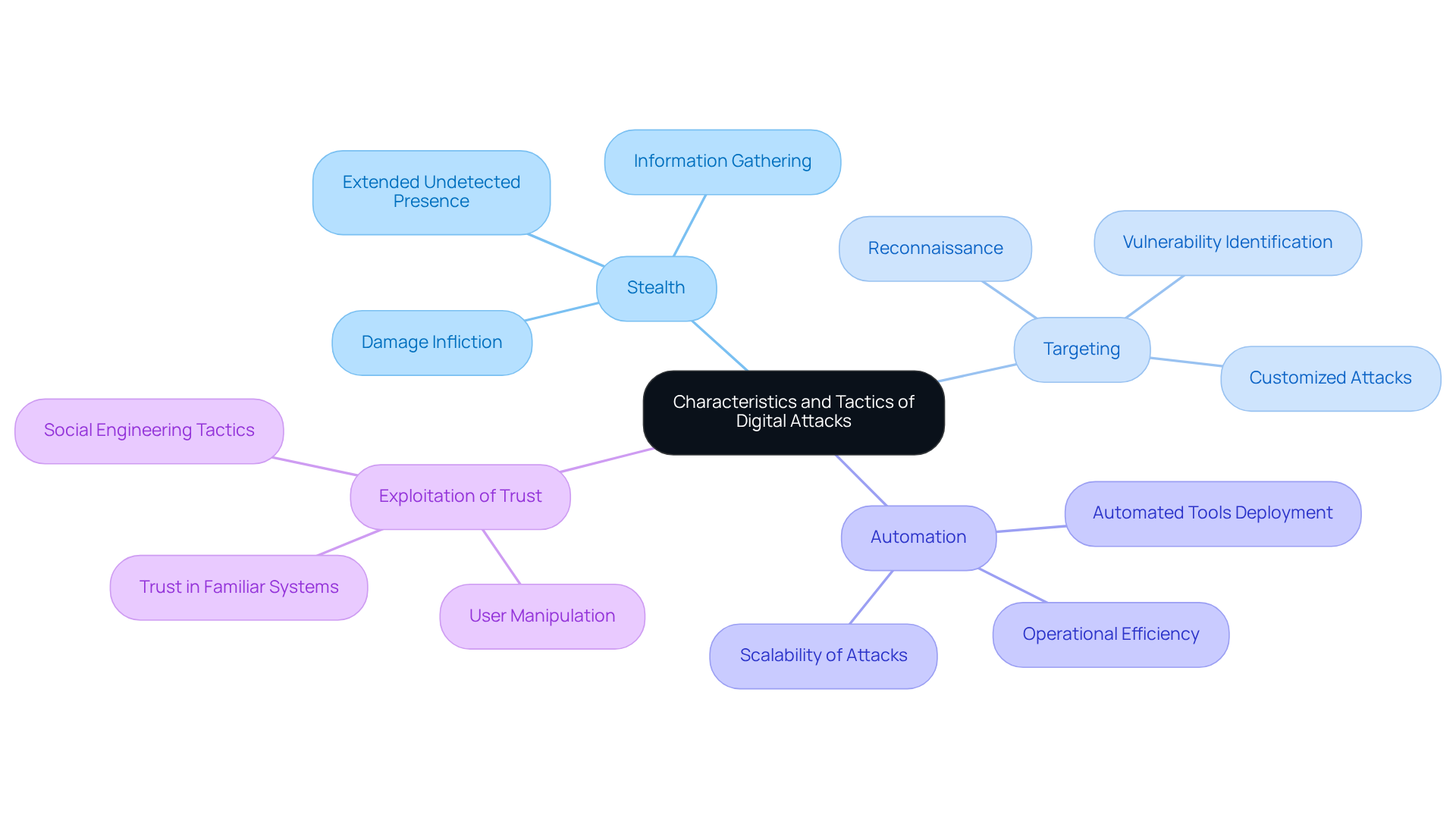
Identify Characteristics and Tactics of Digital Attacks
Digital intrusions often share common traits and strategies that can help organizations recognize and mitigate risks, particularly in achieving compliance with relevant standards. Understanding these key characteristics is essential:
- Stealth: Many attacks are crafted to remain undetected for extended periods, enabling attackers to gather sensitive information or inflict damage without triggering alarms. Recognizing this can empower organizations to implement measures that align with compliance standards.
- Targeting: Attackers frequently conduct reconnaissance to pinpoint specific vulnerabilities within an organization, customizing their approach to maximize impact. This highlights the importance of thorough self-evaluation as part of the compliance process.
- Automation: The deployment of automated tools and scripts allows perpetrators to execute operations at scale, significantly enhancing their efficiency and reach. Organizations must remain vigilant against these tactics to bolster their cybersecurity posture and fulfill compliance requirements.
- Exploitation of Trust: Many attacks take advantage of the inherent trust users place in familiar systems or contacts, making social engineering a prevalent tactic. By recognizing these strategies, organizations can fortify their defenses and ensure compliance with cybersecurity standards, such as those outlined by relevant frameworks. This understanding is a crucial element in the comprehensive guide to achieving CMMC compliance, serving as a valuable resource for defense contractors striving for cybersecurity maturity. Furthermore, integrating practical strategies and insights from peers can significantly enhance the effectiveness of these defenses.
Conclusion
Digital attacks pose a significant threat to organizations, impacting both operational integrity and reputation. Understanding these threats is essential for businesses, especially as cybercrime continues to evolve. By recognizing various forms of digital attacks - like phishing, ransomware, and malware - organizations can better prepare to mitigate risks and protect sensitive information.
This article highlights key insights into the characteristics and tactics employed by cybercriminals, underscoring the necessity of a proactive cybersecurity strategy. With projections indicating that the average cost of a data breach could exceed $10 million by 2025, and a notable percentage of businesses losing customers due to these incidents, the urgency for robust security measures is clear. Furthermore, the historical evolution of digital attacks reveals an increasing complexity of threats, emphasizing the importance of continuous adaptation and vigilance in cybersecurity practices.
The significance of understanding and addressing digital attacks cannot be overstated. Organizations must prioritize implementing effective security protocols and complying with standards like the Cybersecurity Maturity Model Certification (CMMC). By doing so, they not only safeguard their assets but also build trust with stakeholders, ensuring long-term success in an increasingly digital landscape. Taking action now to enhance cybersecurity measures is vital for navigating the challenges posed by evolving cyber threats.
Frequently Asked Questions
What are digital attacks?
Digital attacks are threats that pose serious risks to the integrity, confidentiality, and availability of information systems, networks, and devices. They can manifest in various forms, including unauthorized access, data breaches, and service disruptions.
What are the consequences of digital attacks?
The consequences of digital attacks can be significant, often resulting in substantial financial losses and damage to a company's reputation. For example, the average cost of a data breach is projected to reach $10.22 million by 2025, and 43% of businesses report losing existing customers due to cyberattacks.
Why is it important for organizations to understand digital attacks?
Understanding digital attacks is vital for organizations as it helps them protect their assets, ensure compliance with regulations like the Cybersecurity Maturity Model Certification (CMMC), and maintain trust with stakeholders.
What proactive measures should organizations take against digital threats?
Organizations should adopt a proactive approach to safeguarding sensitive information, which includes implementing cybersecurity strategies and practices to mitigate risks associated with digital threats.
What resources are available for defense contractors to address digital threats?
The Info Hub serves as a comprehensive resource, offering actionable strategies and practical guidance specifically tailored for defense contractors to help them mitigate risks associated with digital threats.