The Real Cybersecurity Challenges for Defense Contractors
Explore the critical problems of cyber security facing defense contractors and effective solutions.

Overview
The article highlights the pressing issues surrounding cybersecurity for defense contractors, underscoring the urgent need for robust security measures to safeguard sensitive information and adhere to regulations like the Cybersecurity Maturity Model Certification (CMMC). Why is this critical? Breaches can lead to severe financial losses and pose significant national security risks.
To effectively combat these challenges, the article outlines several strategies for enhancing cybersecurity:
- Regular risk assessments are essential, as they help identify vulnerabilities before they can be exploited.
- Employee training plays a crucial role in fostering a security-conscious culture within organizations.
- Advanced security technologies also provide vital layers of protection against potential threats.
In conclusion, defense contractors must prioritize cybersecurity not just for compliance, but to protect their operations and national interests. By implementing these strategies, organizations can significantly mitigate risks and ensure they are prepared to face the evolving landscape of cyber threats.
Introduction
The digital landscape presents significant challenges, particularly for defense contractors responsible for protecting sensitive information vital to national security. As cyber threats become more sophisticated, grasping the intricacies of cybersecurity is essential—not merely for regulatory compliance, but for the integrity of defense operations. What proactive measures can organizations implement to navigate this complex web of vulnerabilities and ensure strong defenses against the ever-present threat of cyber attacks?
Understanding the stakes is crucial. Cybersecurity isn't just a technical issue; it's a matter of national security. Defense contractors must recognize that the consequences of a breach can be catastrophic, affecting not only their operations but also the safety of the nation. By prioritizing cybersecurity, organizations can safeguard their assets and maintain trust with stakeholders.
To effectively combat these threats, organizations should adopt a multi-layered approach to cybersecurity. This includes:
- Regular risk assessments
- Employee training
- Implementation of advanced security technologies
Additionally, staying informed about the latest cyber threats and trends is vital. How can your organization ensure it remains one step ahead?
In conclusion, the path to robust cybersecurity is clear: organizations must take decisive action to protect themselves against cyber threats. By investing in comprehensive security measures and fostering a culture of awareness, defense contractors can navigate the complexities of the digital landscape and secure their operations against potential attacks.
Define Cybersecurity and Its Importance
Cybersecurity is essential for safeguarding systems, networks, and data from digital threats. It employs a variety of technologies, processes, and practices to protect sensitive information from unauthorized access, theft, or damage. For military contractors, the significance of digital security cannot be overstated. As online threats become increasingly sophisticated, robust protective measures are vital—not only for compliance with regulations like the Cybersecurity Maturity Model Certification (CMMC) but also for preserving the integrity of national protection operations.
The repercussions of a security breach can be dire, leading to significant financial losses, reputational damage, and potential risks to national security. For instance, the contractor MORSECORP faced a staggering $4.6 million settlement due to noncompliance with digital security standards, underscoring the financial stakes involved. Similarly, Hill ASC, Inc. was hit with a $14.75 million settlement for submitting invoices for unapproved digital security services, illustrating the legal and financial ramifications of failing to meet security standards.
Moreover, breaches can compromise sensitive information critical to national security. A notable example is a U.S. health care insurance provider that agreed to pay $11 million for inaccurately certifying adherence to security standards. Such incidents highlight the urgent need for contractors to implement effective security measures and continuously monitor and adapt their strategies in response to evolving threats. When seeking information on security compliance, it’s crucial to verify the reliability of external resources; links to outside sites do not imply endorsement and may lead to misinformation.
In this complex landscape, understanding and implementing robust cybersecurity measures is not merely a regulatory obligation; it is crucial for addressing the problems of cyber security, which are fundamental to national security and operational integrity for organizations involved in contracting for national safety. Are you prepared to take the necessary steps to ensure compliance and protect your organization?
Explore Common Cyber Threats and Vulnerabilities
Defense firms encounter a multitude of problems of cyber security, including ransomware, phishing attacks, and advanced persistent threats (APTs). Ransomware attacks, considered among the serious problems of cyber security, involve malicious actors encrypting data and demanding payment for its release, and have surged in frequency, significantly disrupting operational continuity. Phishing attacks, often involving deceptive emails that trick employees into revealing sensitive information, illustrate the problems of cyber security as a persistent threat. APTs are sophisticated, targeted attacks that can linger over time, reflecting the problems of cyber security as they aim to steal sensitive data or intellectual property.
Outdated software, insufficient employee training, and inadequate security protocols contribute to the problems of cyber security. For instance, a recent study revealed that 44% of security suppliers had not implemented end-to-end encryption, a fundamental requirement for CMMC compliance. This statistic underscores the critical need for robust security measures to combat the problems of cyber security.
The CMMC Info Hub provides practical strategies and peer insights to help military suppliers effectively address these vulnerabilities. By leveraging resources focused on updating software and enhancing employee training, firms can develop a strong security strategy to combat the problems of cyber security. This not only mitigates risks but also positions them to achieve CMMC compliance with confidence.
Are you ready to take action? Embrace these resources and fortify your defenses against cyber threats.
Navigate Compliance Challenges in Cybersecurity for Defense Contractors
Adhering to cybersecurity regulations, particularly the CMMC, reveals the problems of cyber security that defense providers face. One of the most pressing hurdles is the complexity of the requirements, which can overwhelm organizations lacking dedicated compliance resources. Many builders struggle with executing essential controls, often due to a misunderstanding of specific requirements or insufficient budget allocations. In fact, a staggering 99% of service providers are not fully prepared for CMMC audits, which highlights critical problems of cyber security in their posture.
To effectively navigate these challenges, builders should:
- Conduct thorough gap analyses to pinpoint areas of non-compliance.
- Develop a structured roadmap for implementation.
- Engage with external regulatory specialists to provide invaluable insights and assistance throughout the compliance process.
For further support, builders are encouraged to explore FAQs related to CMMC compliance and utilize external resources designed to guide them in achieving compliance effectively. By taking these steps, organizations can enhance their cybersecurity posture and ensure they meet the necessary regulatory standards.
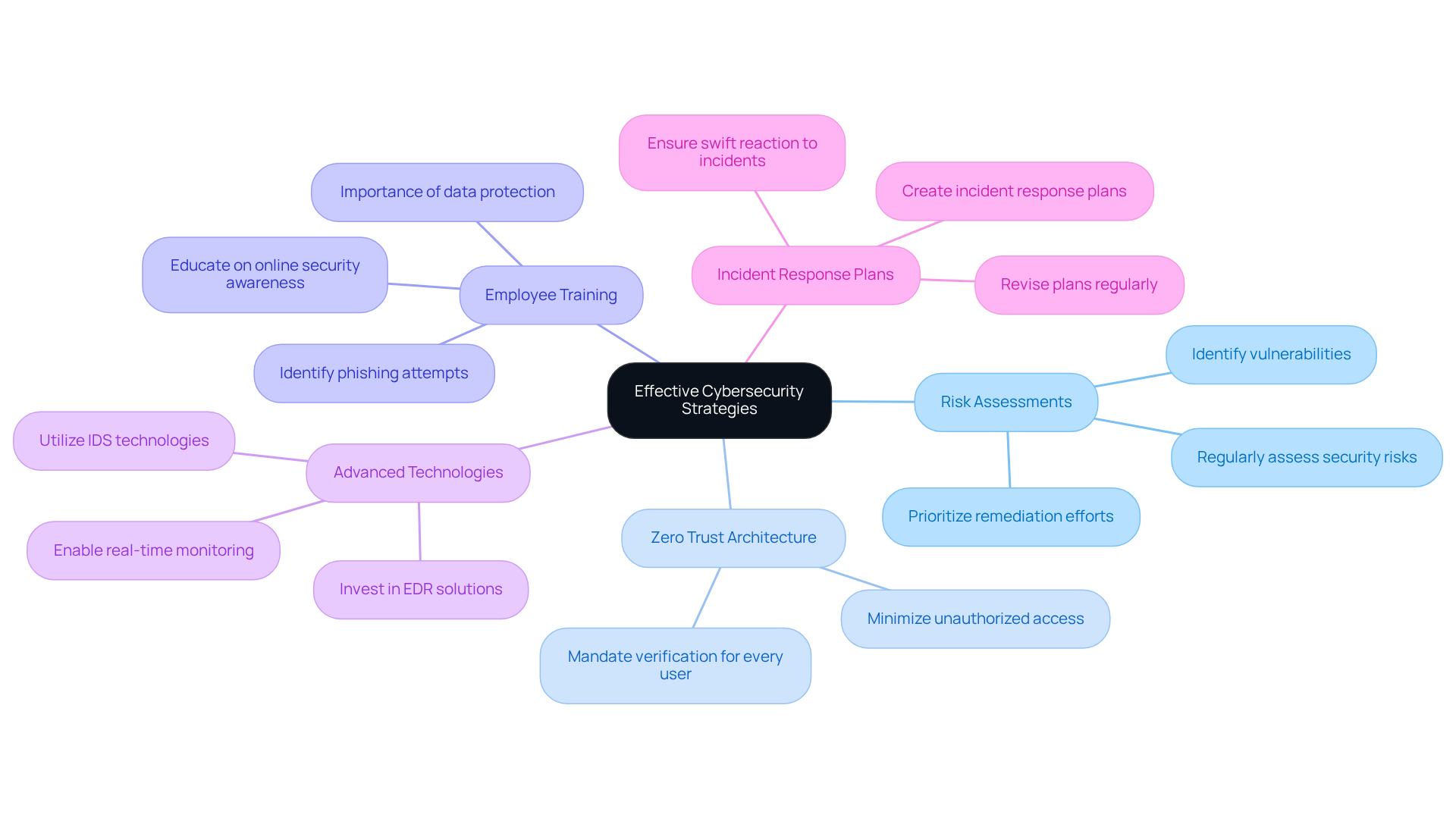
Implement Effective Cybersecurity Strategies and Best Practices
To effectively enhance online security, defense contractors must adopt a multi-layered approach that encompasses several best practices:
-
Conduct Regular Risk Assessments: Frequently assess your organization's security risks to identify vulnerabilities and prioritize remediation efforts. This proactive measure is crucial in staying ahead of potential threats.
-
Implement a Zero Trust Architecture: Embrace a zero trust model that mandates verification for every user and device attempting to access resources. This strategy significantly minimizes the risk of unauthorized access, reinforcing your security framework.
-
Improve Employee Training: Regularly educate employees on online security awareness. Focus on identifying phishing attempts and understanding the importance of data protection. A well-informed team is your first line of defense against cyber threats.
-
Utilize Advanced Security Technologies: Invest in cutting-edge security solutions such as endpoint detection and response (EDR) and intrusion detection systems (IDS). These technologies enable real-time monitoring and response to threats, enhancing your overall security posture.
-
Establish Incident Response Plans: Create and routinely revise incident response plans to ensure a swift and effective reaction to any security incidents. Preparedness is key to minimizing damage and restoring operations quickly.
By implementing these strategies, defense contractors can significantly bolster their cybersecurity posture to mitigate the problems of cyber security and align more effectively with CMMC compliance requirements. Are you ready to take action and secure your organization?
Conclusion
The landscape of cybersecurity for defense contractors presents significant challenges that require immediate and effective action. As digital threats continue to evolve, the need for robust security measures goes beyond mere compliance; it is essential for protecting sensitive information and ensuring national security. Understanding the complex nature of these threats and vulnerabilities is crucial for contractors who aim to safeguard their operations and maintain their integrity in an increasingly hostile digital environment.
Defense contractors face a myriad of cyber threats, including:
- Ransomware
- Phishing
- Advanced persistent threats
The financial and reputational repercussions of breaches can be substantial, with compliance failures leading to staggering settlements. Additionally, navigating the complexities of cybersecurity regulations, such as the Cybersecurity Maturity Model Certification (CMMC), presents further hurdles. By conducting thorough risk assessments, adopting a zero trust architecture, and enhancing employee training, organizations can significantly strengthen their defenses against these persistent threats.
The importance of cybersecurity for defense contractors cannot be overstated. It’s not just about meeting regulatory requirements; it’s about ensuring the very foundation of national security remains intact. By taking decisive action and implementing effective strategies, defense contractors can protect their assets, uphold their commitments, and contribute to a safer operational environment. The time to act is now; every step taken towards enhanced cybersecurity is a step towards securing the future.
Frequently Asked Questions
What is cybersecurity?
Cybersecurity is the practice of protecting systems, networks, and data from digital threats using various technologies, processes, and practices to safeguard sensitive information from unauthorized access, theft, or damage.
Why is cybersecurity important for military contractors?
Cybersecurity is crucial for military contractors to comply with regulations like the Cybersecurity Maturity Model Certification (CMMC) and to preserve the integrity of national protection operations, especially as online threats become more sophisticated.
What are the potential consequences of a cybersecurity breach?
The repercussions of a cybersecurity breach can include significant financial losses, reputational damage, and risks to national security.
Can you provide examples of financial repercussions faced by contractors due to cybersecurity issues?
Yes, for instance, MORSECORP faced a $4.6 million settlement for noncompliance with digital security standards, and Hill ASC, Inc. was hit with a $14.75 million settlement for submitting invoices for unapproved digital security services.
How can breaches affect sensitive information related to national security?
Breaches can compromise sensitive information that is critical to national security, as illustrated by a U.S. health care insurance provider that paid $11 million for inaccurately certifying adherence to security standards.
What should organizations do to ensure effective cybersecurity?
Organizations must implement effective security measures and continuously monitor and adapt their strategies in response to evolving threats to ensure compliance and protection.
How should organizations verify information on security compliance?
It is crucial for organizations to verify the reliability of external resources, as links to outside sites do not imply endorsement and may lead to misinformation.