What a Security Plan Is: Overview of System Security Requirements
Learn how a security plan is to provide an overview of the security requirements of the system and mitigate risks effectively.

Introduction
A security plan stands as the backbone of an organization's defense strategy, outlining the essential measures needed to safeguard vital assets against an ever-growing array of threats. These plans provide a comprehensive overview of the system's security requirements, enabling organizations not only to meet compliance standards but also to enhance their overall security posture.
However, with the rapid evolution of cyber threats and regulatory demands, how can organizations ensure their security plans remain effective and relevant? This article explores the critical components and historical evolution of security plans, offering valuable insights into their indispensable role in today's cybersecurity landscape.
By understanding these elements, organizations can better prepare themselves to face the challenges ahead.
Define Security Plan: Purpose and Importance
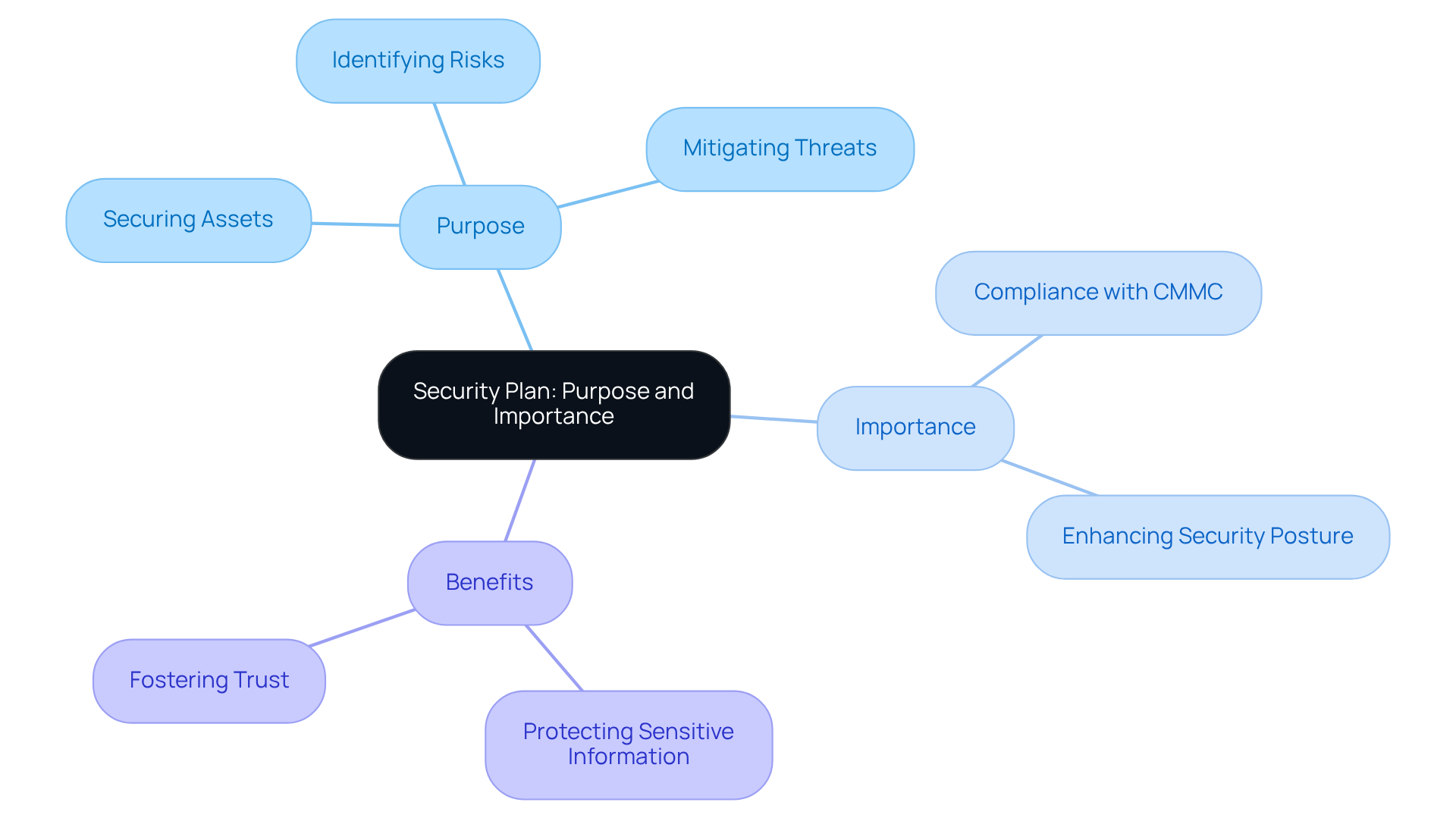
A protection strategy is a formal document that outlines a company's approach to securing its assets - individuals, property, information, and systems - from various threats. What’s the main goal? To establish a comprehensive plan, a security plan is to provide an overview of the security requirements of the system by identifying potential risks and detailing the necessary steps to mitigate those threats. This is particularly vital for organizations aiming for compliance with standards like the Cybersecurity Maturity Model Certification (CMMC). By doing so, they ensure adherence to essential protective measures and protocols.
With a well-defined security strategy, organizations can significantly enhance their overall security posture, protect sensitive information, and foster trust with stakeholders and clients. Consider this: how confident are you in your current security measures? The CMMC Info Hub is an invaluable resource in this journey, offering practical solutions and insights that simplify the path to achieving and maintaining CMMC compliance.
In summary, a robust protection strategy, which is part of a security plan to provide an overview of the security requirements of the system, not only safeguards your assets but also positions your organization as a trusted entity in the eyes of clients and partners. Don’t leave your security to chance - explore the resources available to bolster your compliance efforts today.
Contextualize Security Plans within Cybersecurity Frameworks
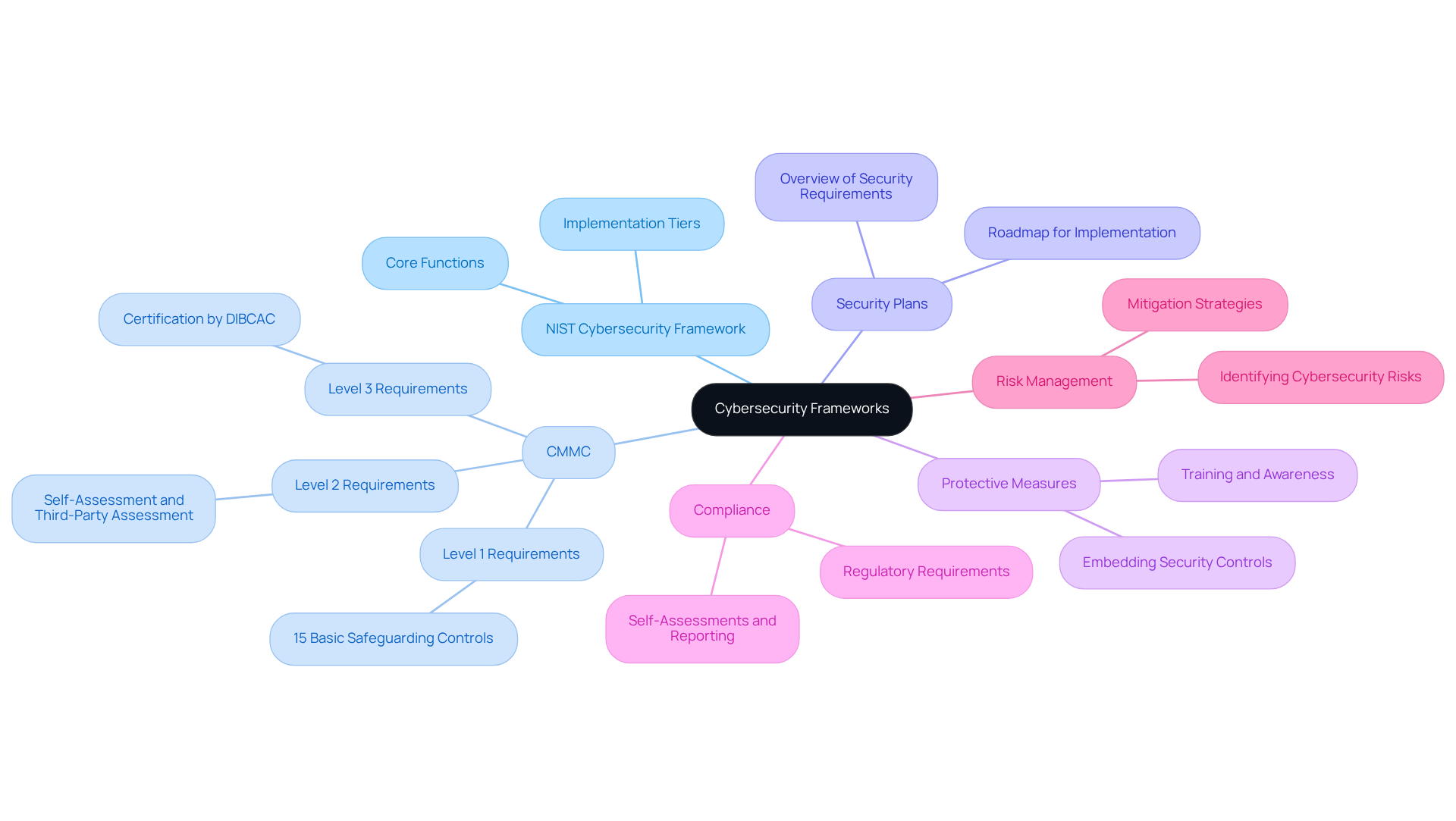
In various cybersecurity frameworks, including the NIST Cybersecurity Framework and the CMMC, a security plan is to provide an overview of the security requirements of the system and is considered an essential element. These frameworks provide structured guidelines that organizations can follow to bolster their cybersecurity measures. For instance, the CMMC framework outlines specific protective measures and procedures that defense contractors must implement to protect Controlled Unclassified Information (CUI).
But why are these frameworks so crucial? A protection strategy aligns with the idea that a security plan is to provide an overview of the security requirements of the system, serving as a roadmap for organizations to implement their safeguarding practices. This alignment not only ensures compliance with regulatory requirements but also enhances the management of cybersecurity risks.
By embedding protective measures within these frameworks, organizations can better understand the importance of comprehensive safety strategies in achieving compliance and safeguarding their assets. Are you ready to take the necessary steps to enhance your cybersecurity posture? Embrace these frameworks and fortify your defenses today.
Identify Key Components of a Security Plan
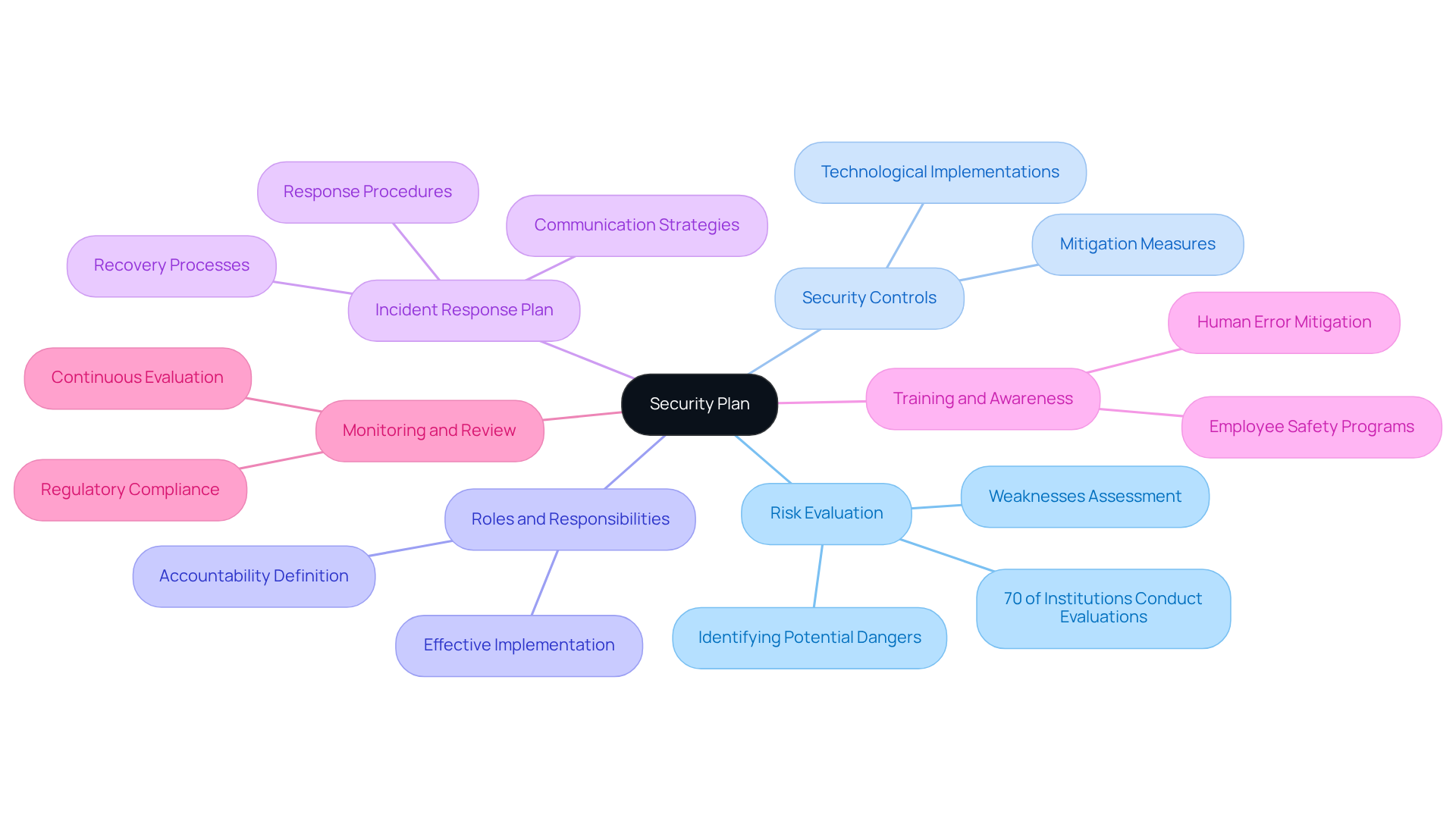
For any organization aiming to protect its assets effectively, a security plan is to provide an overview of the security requirements of the system. It typically encompasses several critical components:
-
Risk Evaluation: This foundational element involves identifying potential dangers and weaknesses within the entity’s assets. Recent studies indicate that approximately 70% of institutions conduct risk evaluations as part of their safety planning, underscoring its significance in safeguarding sensitive information.
-
Security Controls: This section outlines the specific measures and technologies that will be implemented to mitigate identified risks. By doing so, organizations can prepare to defend against potential threats.
-
Roles and Responsibilities: Clearly defining accountability for various aspects of the protection plan is crucial. This clarity ensures effective implementation and accountability throughout the organization.
-
Incident Response Plan: Outlining procedures for responding to incidents, including communication strategies and recovery processes, is vital. This preparation minimizes damage and facilitates swift restoration of operations.
-
Training and Awareness: Developing a program to inform employees about safety policies and practices is essential. Human error remains a significant factor in breaches, making this training vital.
-
Monitoring and Review: Establishing procedures for continuous evaluation and revisions to the protection strategy allows entities to adapt to evolving threats and maintain compliance with regulatory obligations.
By integrating these elements, organizations can create a robust defense strategy, as a security plan is to provide an overview of the security requirements of the system, which not only meets compliance requirements but also significantly enhances their overall protective posture. Experts emphasize that a well-organized risk evaluation is crucial for effective protection planning, enabling entities to proactively address vulnerabilities and strengthen their defenses.
Trace the Evolution of Security Plans
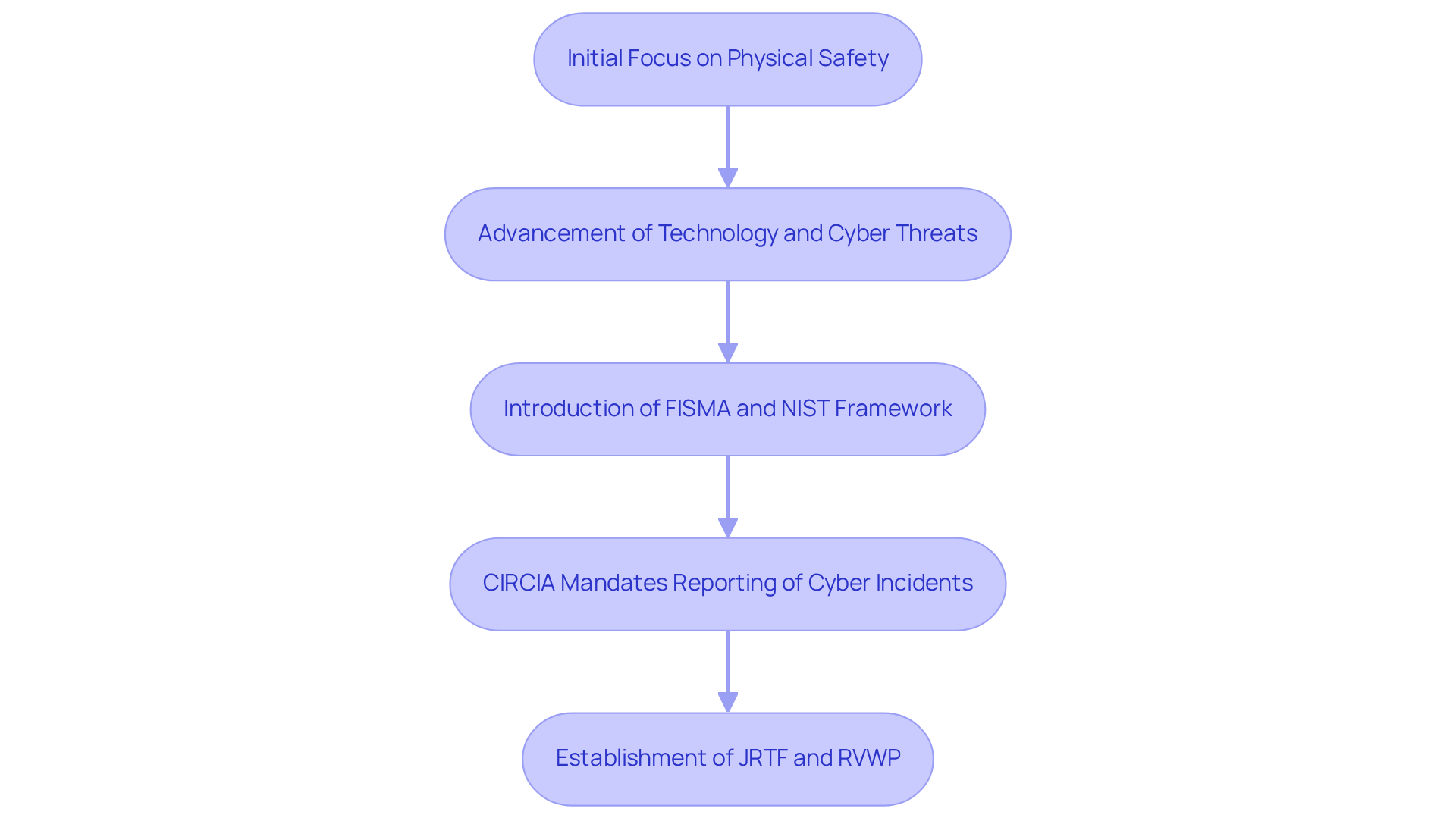
The evolution of protection strategies marks a pivotal shift from merely safeguarding physical assets to embracing a comprehensive approach that includes digital security measures. Initially, organizations concentrated on physical safety, but as technology advanced and cyber threats proliferated, the need for robust protection strategies became undeniable. Regulatory frameworks like the Federal Information Security Management Act (FISMA) and the NIST Cybersecurity Framework have been instrumental in this transformation, mandating rigorous risk management practices.
Consider the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA), which compels critical infrastructure entities to report cyber incidents within 24 hours. This requirement underscores the urgency of adopting proactive security measures. Val Cofield emphasizes that CIRCIA significantly impacts cybersecurity practices, urging organizations to enhance their incident response capabilities. In 2023, CISA completed 1,754 notifications to entities operating internet-accessible vulnerable devices, showcasing the proactive steps businesses are taking to address vulnerabilities.
Furthermore, the establishment of the Joint Ransomware Task Force (JRTF) and the Ransomware Vulnerability Warning Pilot (RVWP) program reflects an ongoing commitment to confronting emerging challenges. This historical perspective emphasizes that a security plan is to provide an overview of the security requirements of the system, which is essential for organizations to continuously adapt their security strategies and effectively navigate the ever-evolving landscape of cybersecurity threats and compliance requirements. Are your security plans up to date? It's crucial to stay ahead in this dynamic environment.
Conclusion
A well-structured security plan is essential for any organization aiming to protect its assets from a myriad of threats. It not only outlines the necessary security requirements and strategies but also enhances compliance with critical frameworks like the Cybersecurity Maturity Model Certification (CMMC). More importantly, it builds a foundation of trust with clients and stakeholders. The significance of a comprehensive security plan cannot be overstated; it plays a pivotal role in safeguarding sensitive information and strengthening the overall security posture of an organization.
Key components of an effective security plan include:
- Risk evaluation
- Security controls
- Roles and responsibilities
- Incident response planning
- Training and awareness
- Ongoing monitoring and review
Each of these elements contributes to a robust defense strategy, ensuring organizations are well-equipped to address vulnerabilities and adapt to the ever-evolving landscape of cybersecurity threats. The historical evolution of security plans also highlights a shift from a focus on physical security to a more holistic approach that encompasses digital security measures, reflecting the growing complexity of today's threats.
Ultimately, the importance of a security plan extends beyond mere compliance; it is a vital tool for organizations striving to protect their assets and maintain operational integrity. By embracing a proactive approach to security planning, organizations can mitigate risks and effectively navigate the complexities of regulatory requirements. It is imperative for businesses to continually assess and update their security strategies to stay ahead of emerging threats and ensure a resilient future.
Frequently Asked Questions
What is a security plan?
A security plan is a formal document that outlines a company's approach to securing its assets, including individuals, property, information, and systems, from various threats.
What is the main goal of a security plan?
The main goal of a security plan is to establish a comprehensive strategy that provides an overview of the security requirements of a system by identifying potential risks and detailing the necessary steps to mitigate those threats.
Why is a security plan particularly important for organizations seeking compliance?
A security plan is vital for organizations aiming for compliance with standards like the Cybersecurity Maturity Model Certification (CMMC) as it ensures adherence to essential protective measures and protocols.
How does a well-defined security strategy benefit organizations?
A well-defined security strategy enhances an organization's overall security posture, protects sensitive information, and fosters trust with stakeholders and clients.
What resources are available to help organizations achieve and maintain CMMC compliance?
The CMMC Info Hub is an invaluable resource that offers practical solutions and insights to simplify the path to achieving and maintaining CMMC compliance.
What are the key components of a robust protection strategy?
A robust protection strategy includes an overview of the security requirements of the system, identification of potential risks, and detailed steps to mitigate those threats.




