Why We Destroy CUI
Understand what is the goal of destroying CUI to enhance cybersecurity and protect sensitive information.

Overview
The imperative of destroying Controlled Unclassified Information (CUI) lies in rendering sensitive data unreadable, indecipherable, and irrecoverable. This process is essential to prevent unauthorized access and safeguard national interests. Effective destruction methods are not merely best practices; they are crucial for compliance with federal regulations and for mitigating the risks associated with data breaches.
Consider the severe legal and reputational consequences that organizations face if they fail to properly dispose of CUI. Such outcomes underscore the necessity for organizations to adopt robust destruction strategies. By prioritizing the effective disposal of CUI, organizations can protect their integrity and uphold national security.
Introduction
The protection of sensitive data is more critical than ever, particularly as cyber threats escalate. Controlled Unclassified Information (CUI) constitutes a significant category of data that, while not classified, demands rigorous safeguarding measures to prevent unauthorized access and potential breaches.
Understanding the imperative of destroying CUI is essential for organizations aiming to bolster their cybersecurity posture and comply with federal regulations.
What are the consequences when this sensitive information is not adequately destroyed?
How can organizations ensure they are not only compliant but also effectively shielding themselves against the ever-evolving landscape of cyber threats?
Addressing these questions is vital for fostering a proactive approach to data security.
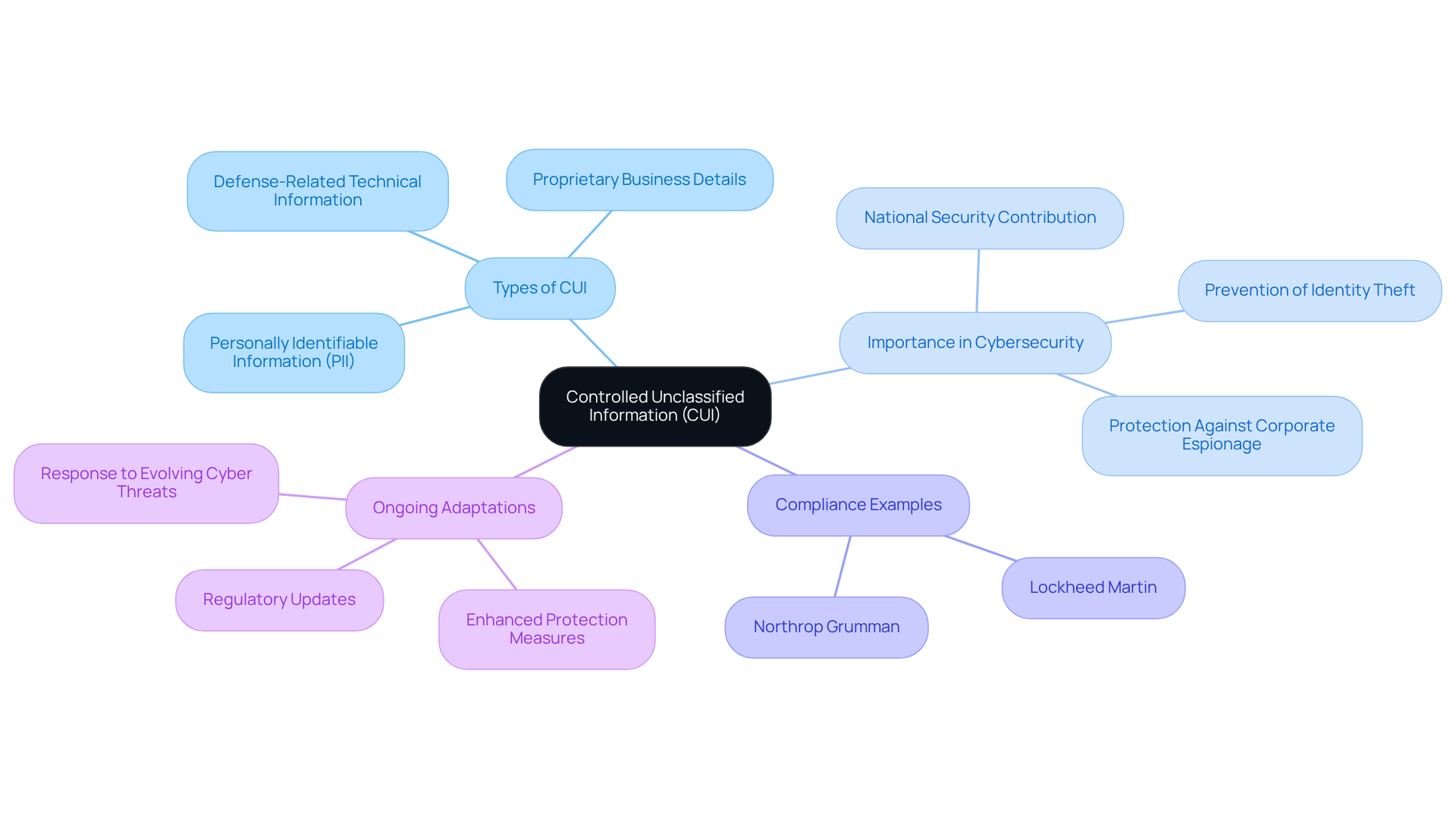
Define Controlled Unclassified Information (CUI)
Controlled Unclassified Information (CUI) is a critical category of information created or possessed by the U.S. government that requires safeguarding or dissemination controls but does not meet classification criteria. CUI encompasses a wide range of sensitive data, including personally identifiable information (PII), proprietary business details, and defense-related technical information. The establishment of the CUI program aims to standardize the handling of sensitive information across federal agencies and their contractors, addressing what is the goal of destroying CUI by ensuring robust protection against unauthorized access and disclosure.
Recent regulations underscore the vital role of CUI in cybersecurity, compelling organizations to implement rigorous safeguarding measures. For example, the Department of Defense (DoD) has delineated specific requirements for contractors to protect CUI, reflecting an increasing acknowledgment of its essential contribution to national security. Notable organizations like Lockheed Martin and Northrop Grumman have successfully integrated CUI protection protocols into their cybersecurity frameworks, illustrating effective compliance and risk management strategies.
In cybersecurity, what is the goal of destroying CUI cannot be overstated. It serves as a foundation for safeguarding sensitive information that, if compromised, could result in severe consequences such as identity theft, corporate espionage, and threats to national security. As cyber threats evolve, the CUI program continuously adapts, with ongoing updates aimed at enhancing its effectiveness in protecting sensitive information. This proactive approach is essential for organizations striving to comply with regulations and secure their operations against emerging cyber threats. To delve deeper into CUI and related cybersecurity practices, consider exploring the external resources linked within this platform.
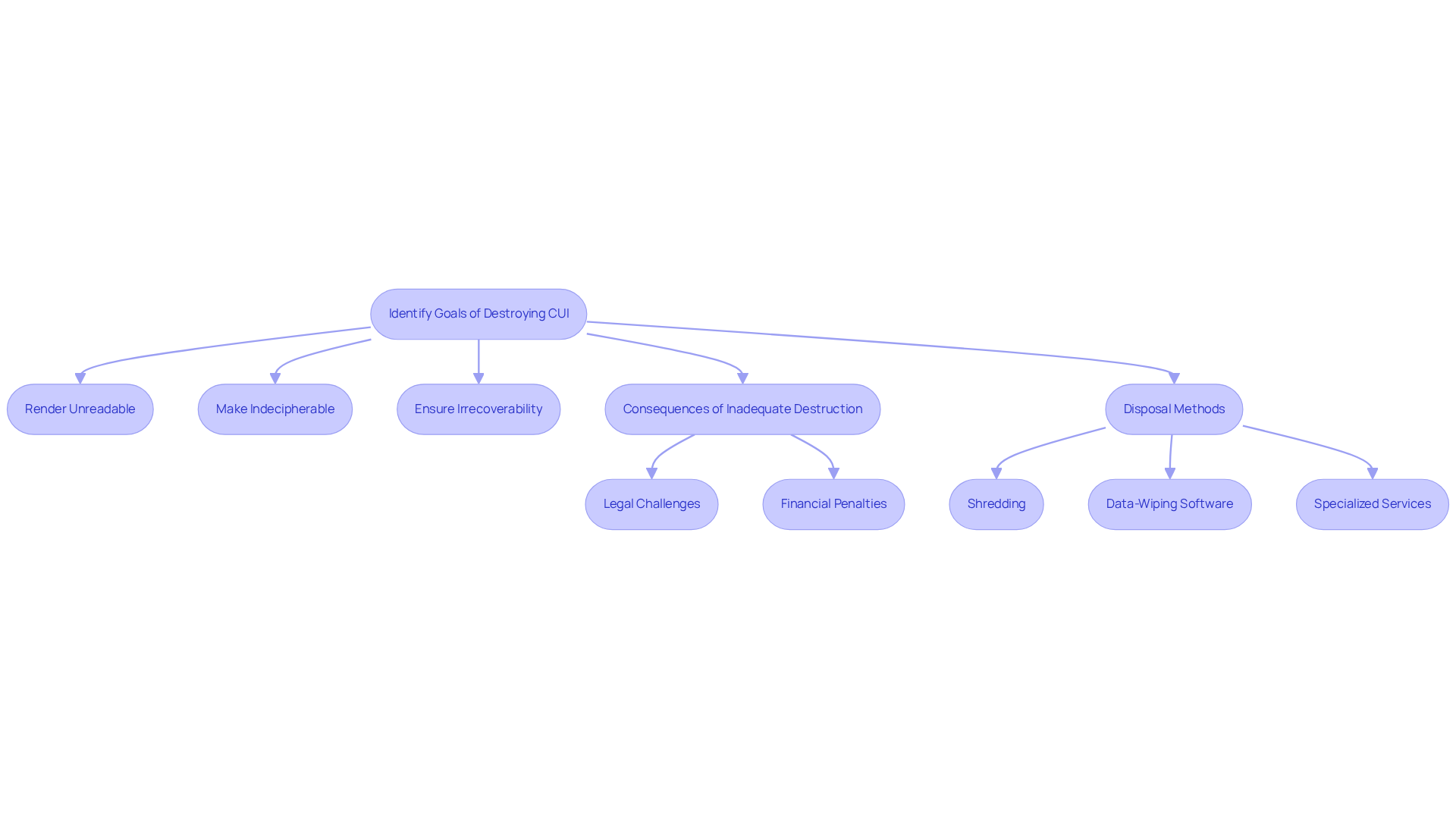
Identify Goals of Destroying CUI
The primary objectives of destroying Controlled Unclassified Information (CUI) are to render the information unreadable, indecipherable, and irrecoverable, which leads to the question: what is the goal of destroying CUI? This process is essential for preventing unauthorized access and safeguarding national interests, particularly in compliance with FAR 52.204-21, which outlines the basic safeguarding requirements for covered contractor information systems. When CUI is no longer required, it must be destroyed in a way that guarantees it cannot be reconstructed or retrieved.
Why is this so crucial? In the field of cybersecurity, information breaches can result in serious consequences, such as financial penalties and the potential loss of government contracts. Organizations that fail to adequately destroy sensitive information may face legal challenges and reputational damage. The rising costs associated with data breaches, which averaged $4.88 million globally in 2022, underscore the importance of effective information disposal.
Effective disposal methods include:
- Shredding physical documents
- Utilizing data-wiping software for electronic files
- Engaging specialized services that adhere to federal guidelines
By prioritizing the secure elimination of CUI, organizations can address what is the goal of destroying CUI, mitigate risks, and enhance their overall cybersecurity posture. It is imperative that organizations take action now to ensure compliance and protect their interests.
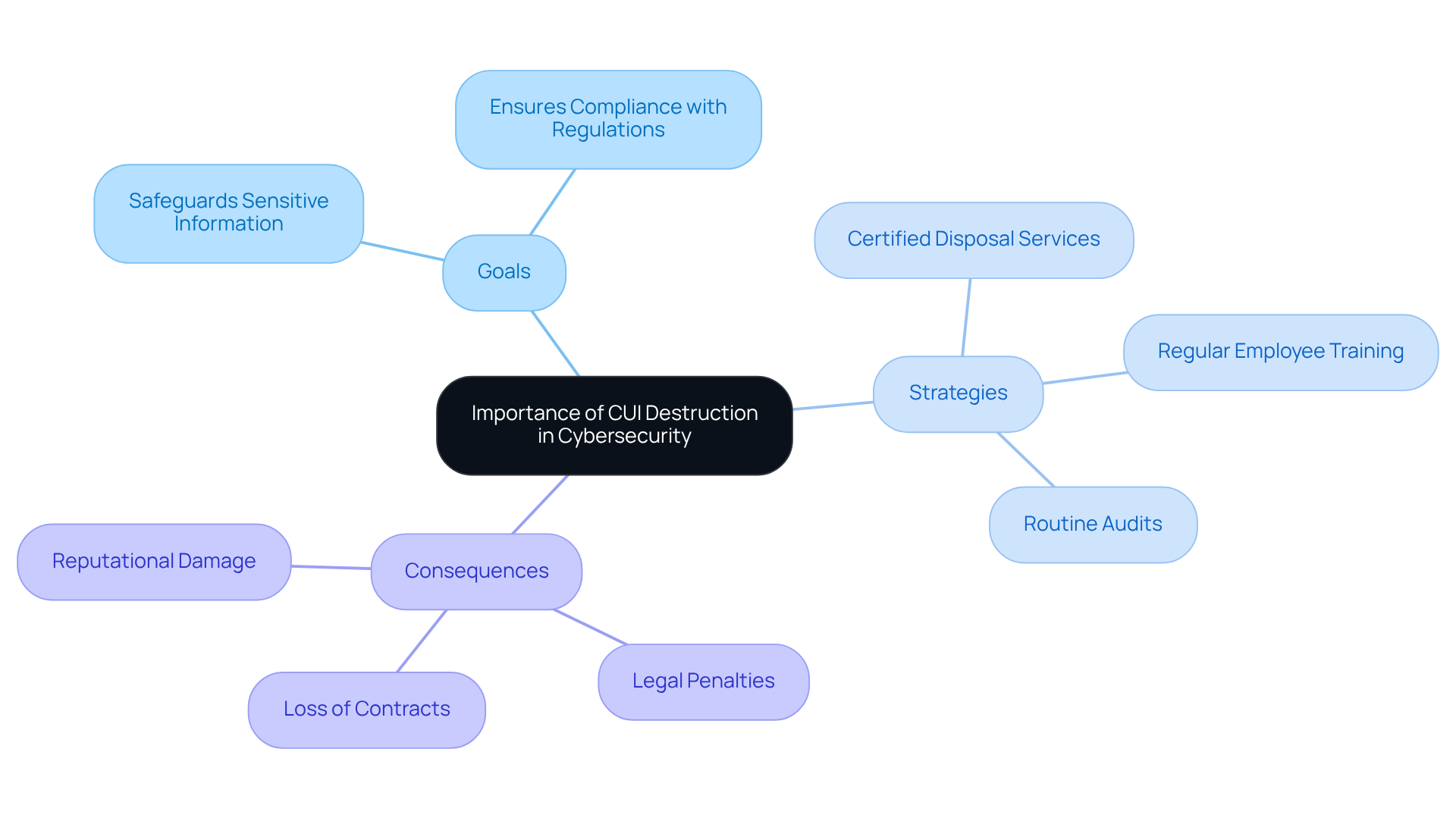
Discuss Importance of CUI Destruction in Cybersecurity
Understanding what is the goal of destroying CUI is crucial for enhancing cybersecurity and mitigating risks associated with breaches and unauthorized access. Efficient CUI elimination not only safeguards sensitive information but also ensures compliance with federal regulations, including the Cybersecurity Maturity Model Certification (CMMC). Organizations can adopt practical strategies, such as:
- Regular employee training on information sanitization techniques
- Utilizing certified information disposal services
- Conducting routine audits to verify adherence to disposal protocols
Failing to properly destroy CUI can lead to severe repercussions, including legal penalties, loss of contracts, and significant reputational damage. For instance, a study revealed that 40% of devices sold online contained Personally Identifiable Information (PII), underscoring the dangers of inadequate information sanitization practices. Furthermore, the Department of Defense mandates that documents must be disposed of in a manner that renders them 'unreadable, indecipherable, and irrecoverable.'
As cyber threats continue to evolve, organizations must prioritize understanding what is the goal of destroying CUI to effectively protect their operations and maintain trust with stakeholders. The consequences of neglecting this responsibility can be dire, highlighting the importance of establishing robust data disposal protocols. Following NIST SP 800-88 guidelines provides a framework for effective data sanitization and elimination, ensuring compliance and protecting sensitive information.
Explore Best Practices for CUI Destruction
To effectively destroy Controlled Unclassified Information (CUI), organizations must implement several best practices:
-
Develop a Destruction Policy: Establish comprehensive guidelines that clearly outline procedures for destroying CUI, detailing roles and responsibilities within the organization. This policy should incorporate specific methods for disposal, frequency of disposal, and criteria for determining when information should be eliminated. This policy is crucial as it forms the foundation of a robust cybersecurity program, ensuring that security controls are implemented consistently and effectively in line with the CMMC framework, which relates to what is the goal of destroying CUI.
-
Use Approved Methods: Ensure that disposal techniques align with federal standards, such as shredding for paper documents and employing certified data-wiping software in accordance with NIST 800-88 and DoD Instruction 5200.48 for electronic files. In 2025, these methods remain essential for adherence and security.
-
Document Disposal Activities: Keep detailed records of all disposal activities, including what was eliminated, when, and by whom, to demonstrate adherence during audits and inspections. Certificates of elimination should also be acquired to provide evidence of compliance, emphasizing the significance of comprehensive documentation in achieving CMMC adherence.
-
Train Employees: Provide thorough training for employees on the importance of CUI disposal and the specific procedures they must follow to ensure compliance and security. This training is essential for fostering a culture of security awareness and accountability within the organization.
-
Regularly Review and Update Policies: Continuously assess and refine destruction policies to adapt to evolving regulations and emerging cybersecurity threats. This proactive strategy is essential for upholding regulations and improving the overall cybersecurity stance.
By adhering to these best practices, organizations can significantly enhance their cybersecurity posture and clarify what is the goal of destroying CUI regulations. Notably, a recent survey revealed that only 30% of organizations have implemented comprehensive CUI disposal policies, underscoring the necessity for proactive measures in this area. Furthermore, improper data destruction can have significant environmental implications, making secure practices even more essential.
Conclusion
Understanding the goal of destroying Controlled Unclassified Information (CUI) is essential for maintaining robust cybersecurity measures. The destruction of CUI is not merely a regulatory requirement; it serves as a critical safeguard against unauthorized access and potential threats to national security. By ensuring that sensitive information is rendered unreadable, indecipherable, and irrecoverable, organizations can protect themselves from the dire consequences associated with data breaches.
This article has highlighted the importance of implementing effective CUI destruction practices, including:
- Developing comprehensive policies
- Utilizing approved disposal methods
- Ensuring continuous employee training
The financial implications of improper CUI management, alongside the potential for reputational damage and legal repercussions, underscore the necessity for organizations to prioritize the secure elimination of sensitive information. As cyber threats evolve, so too must the strategies employed to safeguard against them.
Ultimately, the significance of CUI destruction extends beyond mere compliance; it is a fundamental aspect of an organization’s cybersecurity posture. By adopting best practices and fostering a culture of security awareness, organizations can not only mitigate risks but also enhance trust with stakeholders. Taking proactive steps to understand and implement effective CUI destruction protocols is crucial in today's digital landscape, where the stakes are higher than ever.
Frequently Asked Questions
What is Controlled Unclassified Information (CUI)?
Controlled Unclassified Information (CUI) is a category of information created or possessed by the U.S. government that requires safeguarding or dissemination controls but does not meet classification criteria. It includes sensitive data such as personally identifiable information (PII), proprietary business details, and defense-related technical information.
What is the purpose of the CUI program?
The CUI program aims to standardize the handling of sensitive information across federal agencies and their contractors, ensuring robust protection against unauthorized access and disclosure.
Why is CUI important for cybersecurity?
CUI is vital for cybersecurity as it requires organizations to implement rigorous safeguarding measures to protect sensitive information that, if compromised, could lead to severe consequences like identity theft, corporate espionage, and threats to national security.
What specific requirements has the Department of Defense (DoD) established for CUI protection?
The Department of Defense has delineated specific requirements for contractors to protect CUI, reflecting the increasing acknowledgment of its essential contribution to national security.
How have organizations like Lockheed Martin and Northrop Grumman addressed CUI protection?
Organizations like Lockheed Martin and Northrop Grumman have successfully integrated CUI protection protocols into their cybersecurity frameworks, demonstrating effective compliance and risk management strategies.
How does the CUI program adapt to evolving cyber threats?
The CUI program continuously adapts with ongoing updates aimed at enhancing its effectiveness in protecting sensitive information, which is essential for organizations striving to comply with regulations and secure their operations against emerging cyber threats.