What Is the Goal of the NIST Cybersecurity Framework Protect Function?
Discover the objectives and significance of the NIST Cybersecurity Framework Protect function.

Overview
The NIST Cybersecurity Framework Protect (PR) function aims to establish robust safeguards that significantly enhance the protection of critical infrastructure. By implementing essential cybersecurity measures—such as access control, data security, and protective technology—organizations can effectively mitigate risks and safeguard their assets. But why is this important? These safeguards not only protect against cyber threats but also ensure compliance with regulatory obligations, particularly for defense contractors. This compliance fosters trust and operational resilience, which are crucial in today’s digital landscape.
Consider the implications: without these measures, organizations expose themselves to increased vulnerabilities and potential regulatory penalties. The integration of these cybersecurity practices is not just a recommendation; it’s a necessity for maintaining operational integrity and trustworthiness in the eyes of stakeholders.
In conclusion, embracing the NIST Cybersecurity Framework’s Protect function is essential for any organization looking to bolster its defenses against cyber threats. By prioritizing these safeguards, you not only protect your assets but also position your organization as a compliant and trustworthy entity in the industry.
Introduction
The landscape of cybersecurity presents numerous challenges, making the implementation of effective protective measures more critical than ever. The NIST Cybersecurity Framework (CSF) provides a structured approach to safeguarding vital infrastructure. However, the specific goals of its Protect (PR) function often remain unclear. By exploring the core objectives of this framework, organizations can discover how robust safeguards not only strengthen their defenses but also enhance compliance and build trust with stakeholders.
What are the essential components that constitute the Protect function? How can organizations leverage these elements to navigate the complexities of cybersecurity threats and regulatory demands? Understanding these components is crucial for organizations aiming to bolster their cybersecurity posture and ensure they meet compliance requirements effectively.
Define the NIST Cybersecurity Framework and Protect Function
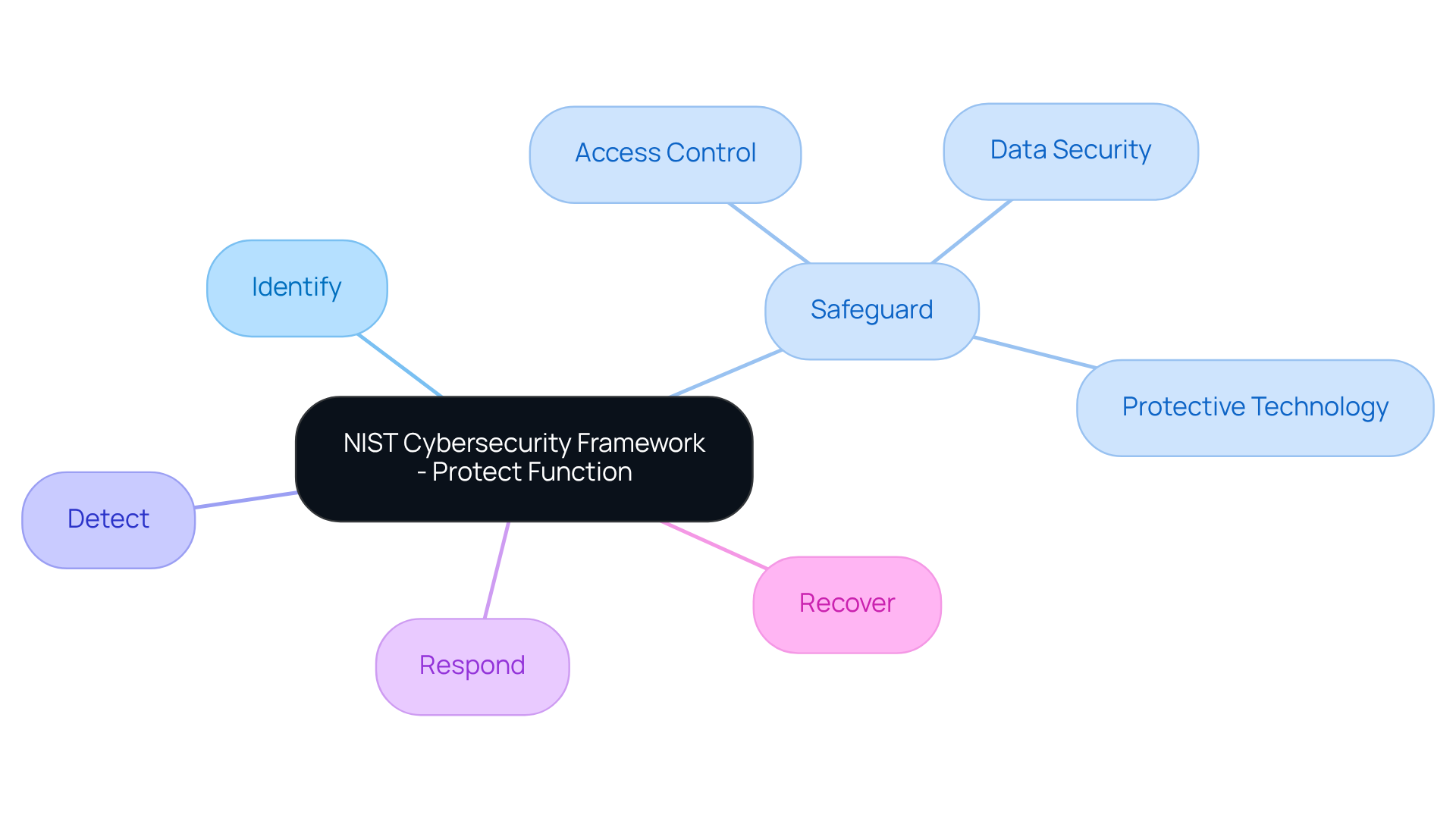
The NIST Cybersecurity Framework (CSF) is a voluntary framework that includes standards, guidelines, and practices designed to address what is the goal of the NIST Cybersecurity Framework Protect (PR) function in enhancing the protection of critical infrastructure. The framework, which is designed to assist organizations in managing and reducing cybersecurity risks, raises the question: what is the goal of the NIST Cybersecurity Framework Protect (PR) function, as it delineates five essential roles: Identify, Safeguard, Detect, Respond, and Recover?
Among these, the Safeguard role is particularly crucial for understanding what is the goal of the NIST Cybersecurity Framework Protect (PR) function. The establishment of robust defenses is crucial for understanding what is the goal of the NIST Cybersecurity Framework Protect (PR) function in ensuring the provision of essential services. This includes vital measures such as access control, data security, and protective technology. These elements are not just recommendations; they are essential for mitigating risks and enhancing a company's cybersecurity posture.
Why is this important? Organizations that adopt these practices not only protect their assets but also build trust with stakeholders and customers. By implementing the CSF, companies can significantly reduce their vulnerability to cyber threats.
In conclusion, embracing the NIST Cybersecurity Framework is not merely a compliance exercise; it is a strategic move towards a more secure operational environment. Organizations are encouraged to leverage these resources to fortify their defenses and ensure resilience against cyber threats.
Contextualize the Importance of the Protect Function in Cybersecurity
The safeguarding mechanism stands as a critical barrier in the cybersecurity landscape, defending against potential threats. By establishing robust safeguards, organizations can effectively limit or contain the impact of cybersecurity incidents. For example, implementing strong access controls and data encryption significantly reduces the risk of unauthorized access and data breaches.
Moreover, these safeguarding capabilities align with regulatory obligations, making them essential for compliance, especially for defense contractors who must adhere to stringent criteria set by the Department of Defense (DoD). This proactive approach not only protects sensitive information but also fosters trust among stakeholders and clients.
Are you ready to enhance your cybersecurity posture? By prioritizing these safeguards, you not only comply with regulations but also secure your organization’s future.
Outline Key Objectives and Components of the Protect Function
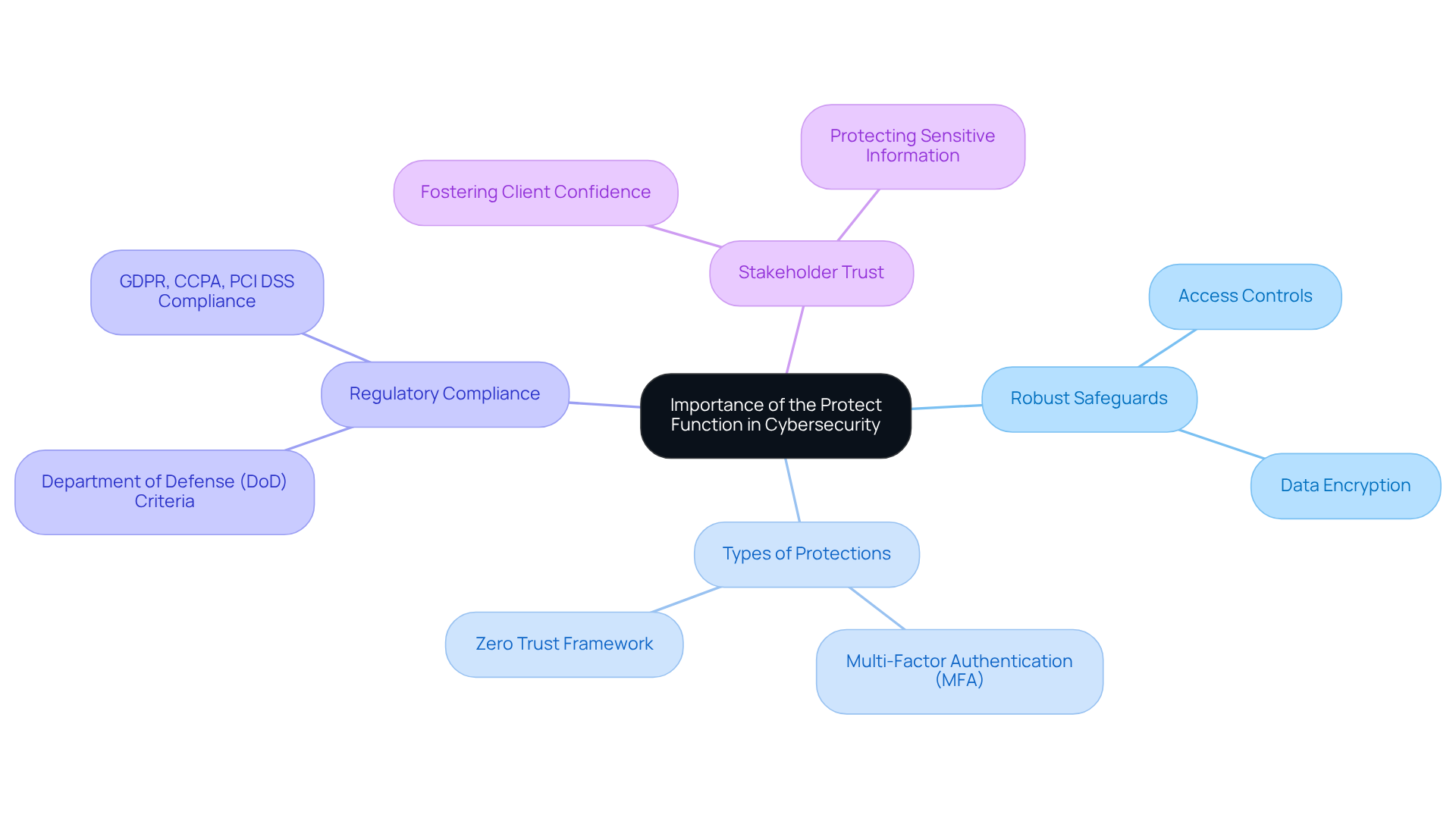
What is the goal of the NIST Cybersecurity Framework Protect (PR) function, which encompasses several key objectives and components vital for achieving CMMC adherence and ensuring robust cybersecurity within defense contracting? These components include:
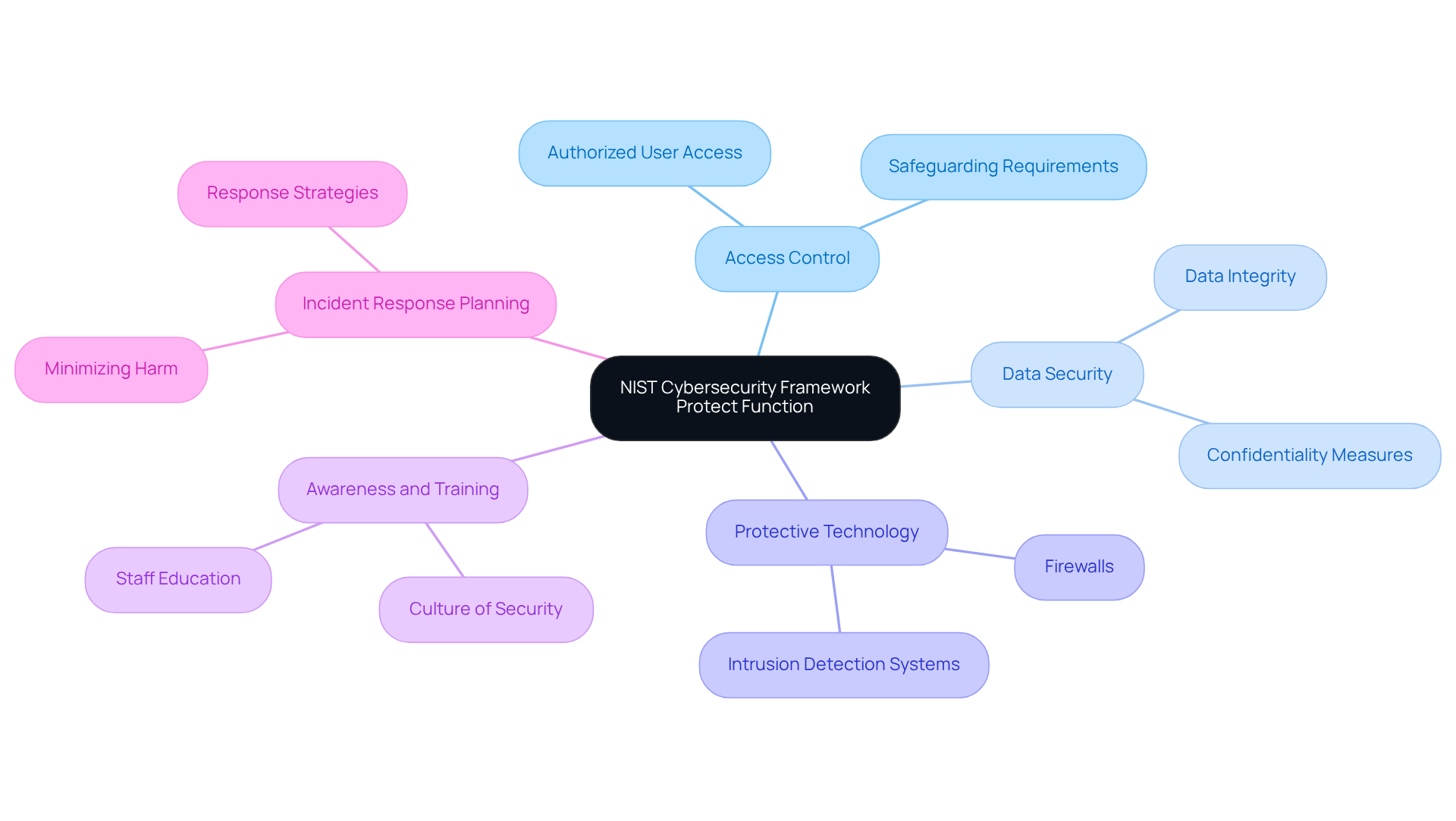
- Access Control: It’s critical to ensure that only authorized users have access to sensitive information and systems. This is essential for meeting the safeguarding requirements outlined in FAR 52.204-21, which forms the foundation for CMMC Level 1 standards.
- Data Security: Implementing measures to protect data integrity and confidentiality—such as encryption and data masking—is crucial for ensuring adherence and securing sensitive defense information.
- Protective Technology: Utilizing technology solutions like firewalls and intrusion detection systems helps entities meet CMMC requirements and defend against cyber threats effectively.
- Awareness and Training: Educating staff about cybersecurity threats and best practices fosters a culture of security within the organization, which is vital for compliance and effective incident response.
- Incident Response Planning: Developing and maintaining strategies to respond efficiently to cybersecurity incidents minimizes potential harm and is a key element of the CMMC adherence roadmap.
These components work together to create a strong defense against cyber threats, which relates to what is the goal of the NIST Cybersecurity Framework Protect (PR) function, ensuring that entities can maintain operational continuity even in the face of potential attacks. They also align with the ultimate goal of achieving CMMC compliance. By incorporating practical strategies and insights from peers, organizations can further enhance their understanding and implementation of these essential components.
Discuss Compliance Implications for Defense Contractors
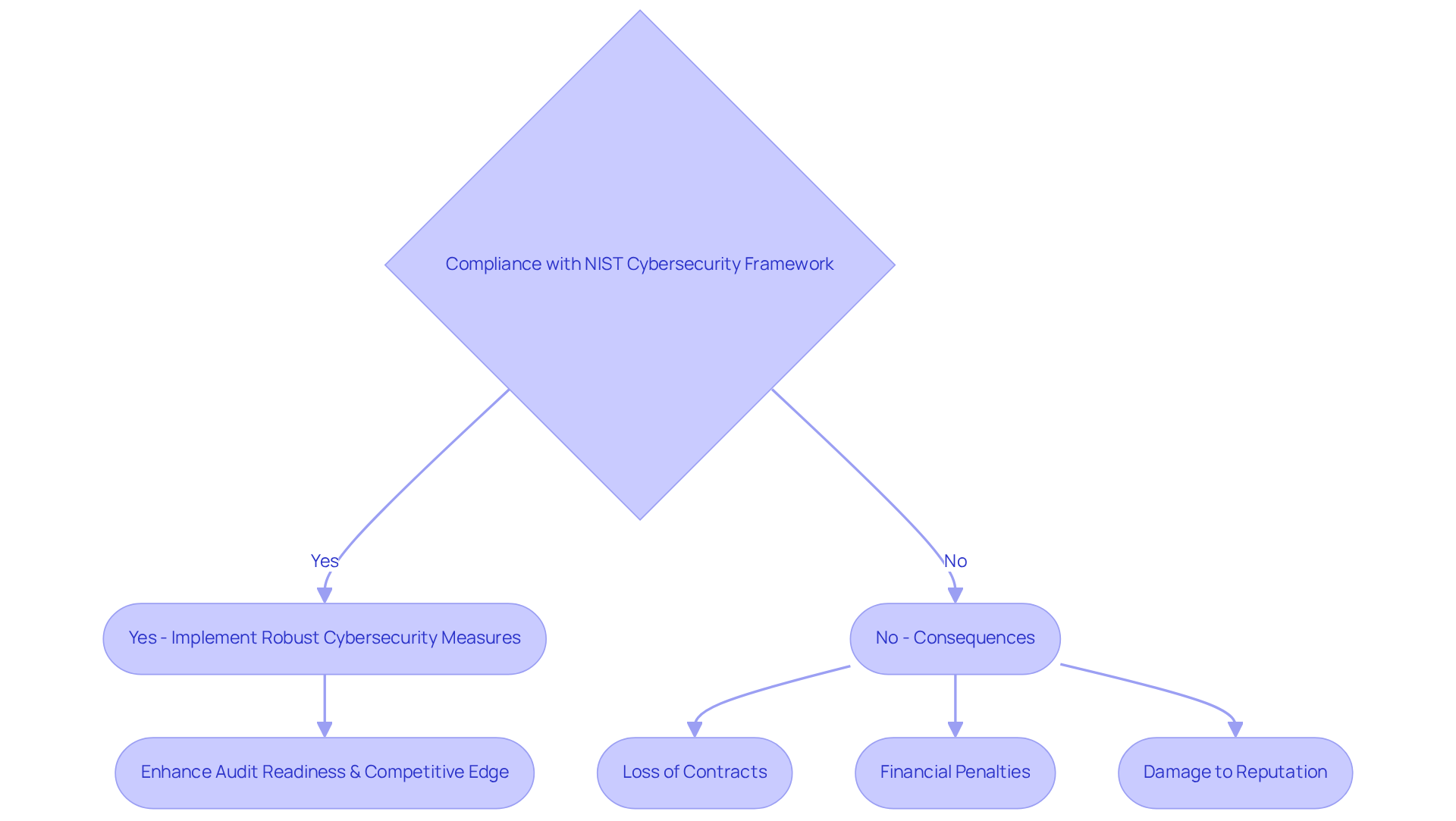
For defense contractors, compliance with the NIST Cybersecurity Framework is not just a best practice; it’s a contractual requirement imposed by the Department of Defense (DoD). This necessity compels organizations to implement robust cybersecurity measures to protect Controlled Unclassified Information (CUI). What happens if they don’t comply? The consequences can be severe: loss of contracts, financial penalties, and damage to a company’s reputation that may never fully heal.
The safeguarding role is pivotal in fulfilling these regulatory requirements, as it emphasizes what is the goal of the NIST Cybersecurity Framework Protect (PR) function in ensuring that entities adopt the necessary measures to effectively mitigate risks. By aligning their cybersecurity strategies with what is the goal of the NIST Cybersecurity Framework Protect (PR) function?, defense contractors not only bolster their readiness for audits and assessments but also enhance their competitive edge in the defense contracting landscape. Consider this: organizations that have failed to meet these requirements have faced significant penalties, highlighting the critical importance of compliance in maintaining operational integrity and securing future contracts.
In summary, the stakes are high. Defense contractors must prioritize compliance with the NIST Cybersecurity Framework to safeguard their interests and ensure their place in the industry. Are you ready to take action and align your cybersecurity strategies with these essential requirements?
Conclusion
The NIST Cybersecurity Framework's Protect function is crucial for enhancing organizational cybersecurity by establishing robust safeguards that protect critical infrastructure. By focusing on essential components like access control, data security, and protective technology, organizations can effectively mitigate risks and cultivate a culture of security vital for operational resilience.
Why is implementing the Protect function so important? It not only helps organizations comply with regulatory requirements but also builds trust with stakeholders. By prioritizing effective cybersecurity measures, organizations can significantly reduce their vulnerability to cyber threats while ensuring compliance with standards such as CMMC. This discussion highlights how the Protect function serves as a cornerstone for defense contractors, emphasizing the necessity of a proactive approach to safeguard sensitive information and maintain a competitive edge.
Ultimately, embracing the NIST Cybersecurity Framework transcends mere compliance; it is a strategic imperative that secures an organization's future in a landscape rife with cyber risks. Organizations are urged to take decisive action by integrating these practices into their cybersecurity strategies. This fosters a secure environment that not only protects assets but also enhances overall trust and integrity in their operations.
Frequently Asked Questions
What is the NIST Cybersecurity Framework (CSF)?
The NIST Cybersecurity Framework (CSF) is a voluntary framework that includes standards, guidelines, and practices to help organizations manage and reduce cybersecurity risks.
What are the main functions of the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework delineates five essential roles: Identify, Safeguard, Detect, Respond, and Recover.
What is the goal of the Protect (PR) function in the NIST Cybersecurity Framework?
The goal of the Protect (PR) function is to enhance the protection of critical infrastructure by establishing robust defenses and ensuring the provision of essential services.
What are some key measures included in the Protect (PR) function?
Key measures in the Protect (PR) function include access control, data security, and protective technology.
Why is adopting the NIST Cybersecurity Framework important for organizations?
Adopting the NIST Cybersecurity Framework is important because it helps organizations protect their assets, build trust with stakeholders and customers, and significantly reduce vulnerability to cyber threats.
Is implementing the NIST Cybersecurity Framework just about compliance?
No, implementing the NIST Cybersecurity Framework is not merely a compliance exercise; it is a strategic move towards creating a more secure operational environment.




