Who Can Control CUI? 4 Steps to Identify Key Roles and Policies
Learn who can control CUI by identifying key roles and policies for effective information management.

Introduction
Understanding Controlled Unclassified Information (CUI) is crucial for any organization that engages with sensitive government data. As compliance with regulations like the Cybersecurity Maturity Model Certification (CMMC) becomes increasingly vital, identifying the key roles responsible for CUI oversight and establishing effective management policies is essential. But who exactly is in charge of controlling this sensitive information?
Exploring the intricacies of CUI management not only reveals the roles involved but also highlights the significant implications of mishandling this data. Organizations must consider:
- Are they truly equipped to protect what matters most?
This question underscores the urgency of implementing robust CUI management practices.
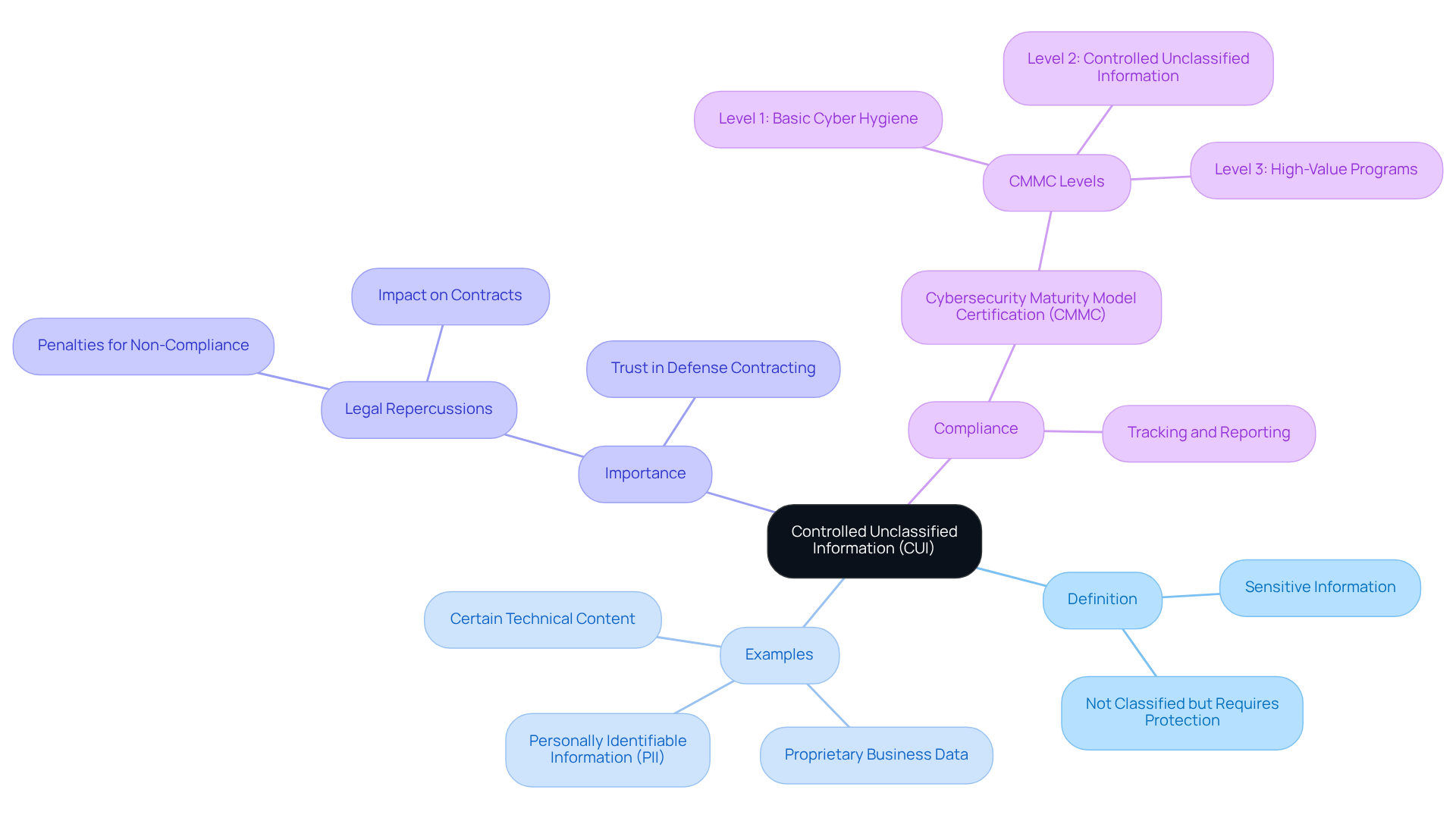
Define Controlled Unclassified Information (CUI)
Controlled Unclassified Data (CUI) encompasses sensitive information created or held by the U.S. government, or by non-federal entities acting on its behalf, that necessitates specific safeguarding or dissemination controls. While CUI is not classified, it remains sensitive and must be protected under various laws and regulations. Key examples of CUI include:
- Personally identifiable information (PII)
- Proprietary business data
- Certain technical content
Understanding CUI is crucial for compliance with the Cybersecurity Maturity Model Certification (CMMC) and other federal regulations. Improper management of this data can lead to serious legal and security repercussions. Protecting CUI is not just a regulatory obligation; it is vital for maintaining trust and integrity within the defense contracting landscape.
So, who can control CUI to ensure that organizations are compliant? For further information and resources, please refer to the external links provided on the CMMC Info Hub. By taking proactive steps to safeguard CUI, organizations can not only meet regulatory requirements but also enhance their reputation and reliability in the industry.
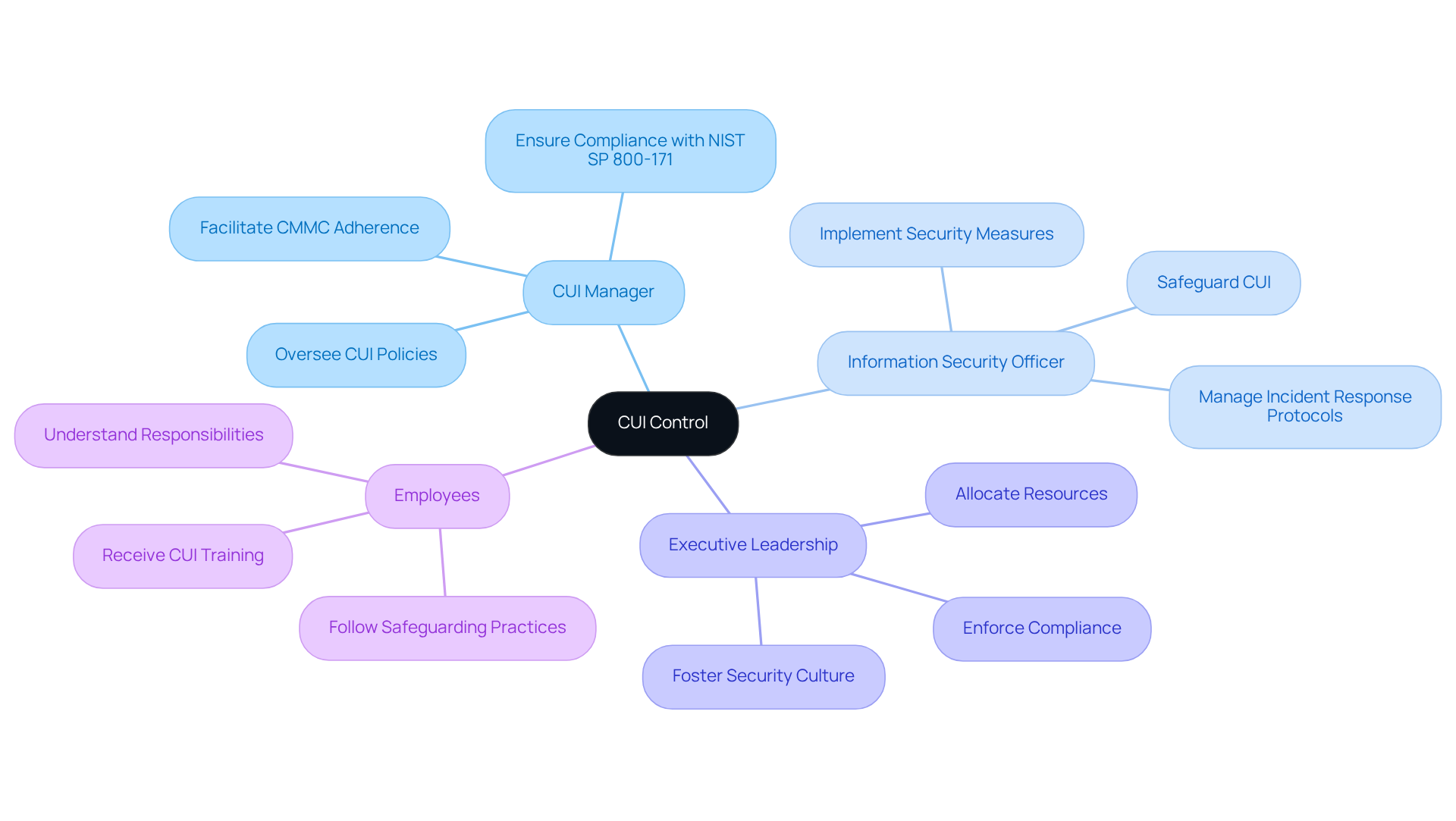
Identify Key Roles Responsible for CUI Control
To effectively manage Controlled Unclassified Information (CUI), organizations must clearly identify who can control CUI and the key roles responsible for its oversight and protection. These roles typically include:
- CUI Manager: This individual oversees the implementation of CUI policies and procedures, ensuring compliance with federal regulations such as NIST SP 800-171 and DFARS requirements. They play a vital role in preserving the integrity of CUI procedures, which is necessary for attaining CMMC adherence as detailed in The Ultimate Guide to Achieving CMMC Adherence.
- Information Security Officer: Tasked with safeguarding CUI, the Information Security Officer ensures that appropriate security measures are in place, including access controls and incident response protocols. Their expertise is essential for protecting sensitive information from unauthorized access or breaches, aligning with the practical strategies detailed in the ultimate guide to CMMC adherence.
- Executive Leadership: Senior leadership offers crucial oversight and responsibility for CUI administration. They are responsible for allocating necessary resources, enforcing compliance, and fostering a culture of security within the organization, which is critical for navigating the CMMC ecosystem.
- Employees: All staff members who handle CUI must receive training on proper oversight and safeguarding practices. This training is essential for ensuring that everyone comprehends their responsibilities and the significance of safeguarding sensitive data. Mishandling CUI can lead to severe consequences, including regulatory penalties and loss of contracts.
By clearly defining these roles and emphasizing the significance of training and adherence to regulations, organizations can establish a structured approach to determine who can control CUI. This guarantees that all staff are informed of their duties and the importance of protecting sensitive data, ultimately aiding their path towards CMMC adherence.
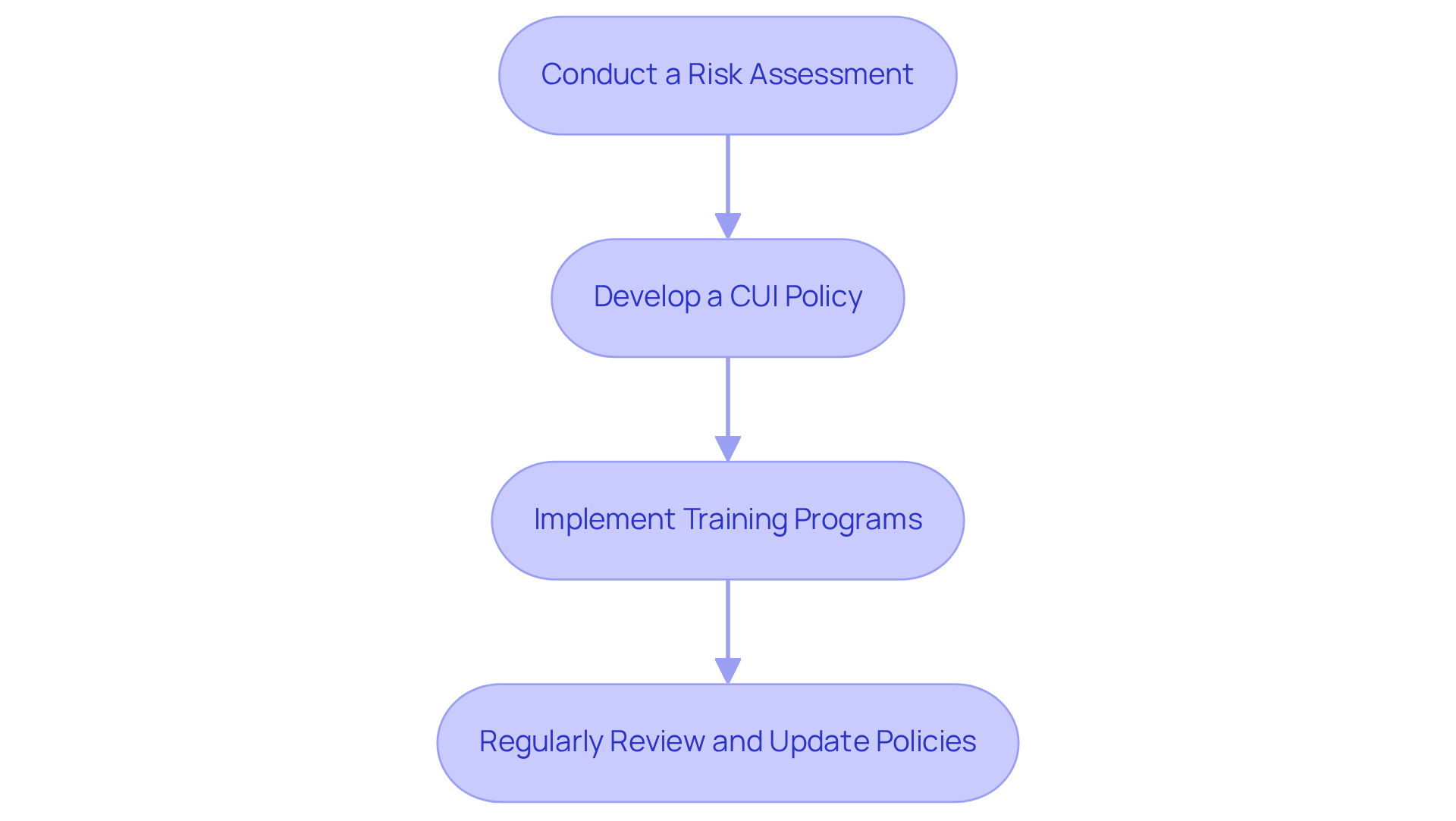
Establish Policies and Procedures for CUI Management
Organizations must establish robust policies and procedures to determine who can control CUI effectively. Here’s how:
- Conduct a Risk Assessment: What risks are associated with handling CUI? Identifying these risks is crucial. Determine the necessary controls to mitigate them effectively.
- Develop a CUI Policy: A formal document is essential. This policy should clearly outline how CUI will be identified, handled, stored, and shared. Include definitions, roles, and responsibilities to ensure clarity.
- Implement Training Programs: Are your employees equipped to handle CUI? Ensure that all staff receive comprehensive training on CUI policies and procedures, emphasizing the importance of safeguarding sensitive information.
- Regularly Review and Update Policies: How often do you revisit your policies? Establish a schedule for reviewing and updating CUI policies to reflect changes in regulations or organizational practices.
By adopting these steps, organizations can create a thorough framework for CUI oversight, which raises the important question of who can control CUI, enhancing adherence and security. This proactive approach not only protects sensitive information but also fosters a culture of compliance within the organization.
Assess Current CUI Control Practices
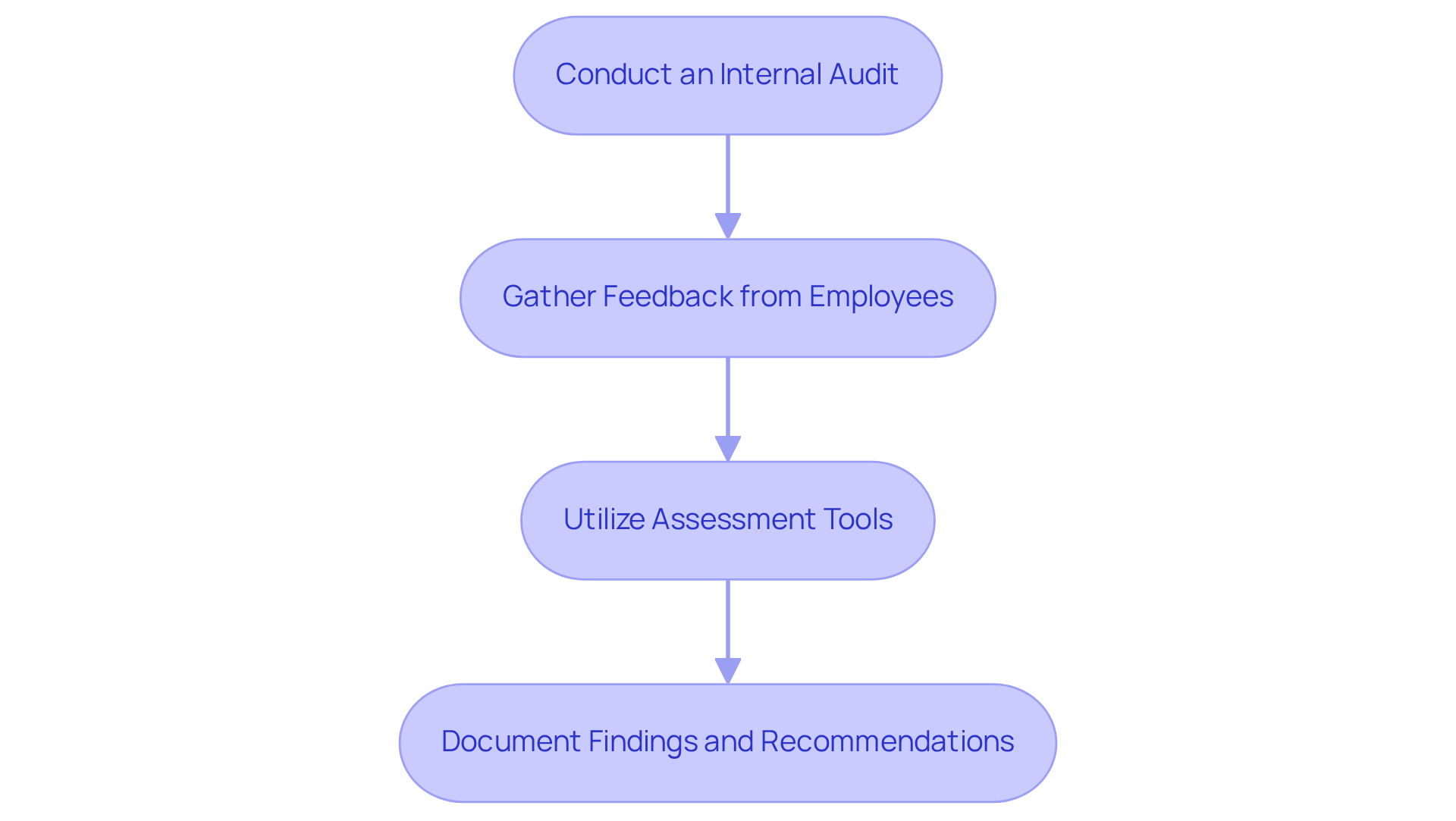
To effectively evaluate current practices for managing Controlled Unclassified Information (CUI), organizations must consider who can control CUI. Here are the essential steps:
-
Conduct an Internal Audit: Begin by systematically reviewing existing CUI management practices against established policies and regulatory requirements. This audit is crucial for identifying adherence gaps and areas that need enhancement.
-
Gather Feedback from Employees: Actively solicit input from staff members who handle CUI. Understanding their experiences and challenges is vital, especially when considering who can control CUI, as employee feedback can reveal significant insights into the effectiveness of current practices.
-
Utilize Assessment Tools: Employ frameworks such as NIST SP 800-171 to assess the effectiveness of existing CUI controls. Conducting a gap assessment against these controls is essential for pinpointing weaknesses and ensuring compliance.
-
Document Findings and Recommendations: Compile the assessment results, emphasizing areas for improvement. Create a comprehensive action plan to address recognized shortcomings, ensuring that the organization can enhance its CUI handling practices.
Why is this important? Failing to manage CUI effectively can lead to serious consequences, including liability for government response and mitigation costs. It is essential to evaluate who can control CUI regularly to uphold regulations and protect sensitive information. With 64% of compliance leaders prioritizing stronger privacy controls this year, organizations must remain proactive in their approach to CUI management.
Conclusion
Understanding who can control Controlled Unclassified Information (CUI) is essential for organizations that handle sensitive data. Why is this important? The effective management of CUI not only involves identifying key roles responsible for its oversight but also establishing robust policies and procedures that ensure compliance with federal regulations. By recognizing the significance of CUI and the necessity for strict governance, organizations can protect sensitive information and maintain trust in their operations.
The critical roles involved in CUI management include:
- CUI Manager
- Information Security Officer
- Executive Leadership
- All employees handling CUI
Each role serves a unique purpose in safeguarding this sensitive information, from policy implementation to ensuring compliance with training programs. Establishing clear policies and conducting regular assessments are vital steps for organizations to enhance their CUI control practices and align with regulatory requirements.
In light of the increasing emphasis on data protection and compliance, organizations must take proactive measures to strengthen their CUI management frameworks. This includes:
- Conducting audits
- Gathering employee feedback
- Continuously updating policies to reflect best practices
By prioritizing the protection of Controlled Unclassified Information, organizations not only fulfill their regulatory obligations but also foster a culture of security that ultimately enhances their reputation and reliability in the industry. Are you ready to take the necessary steps to ensure your organization is compliant and secure?
Frequently Asked Questions
What is Controlled Unclassified Information (CUI)?
Controlled Unclassified Information (CUI) includes sensitive information created or held by the U.S. government or non-federal entities acting on its behalf that requires specific safeguarding or dissemination controls.
Is CUI classified information?
No, CUI is not classified, but it is still sensitive and must be protected under various laws and regulations.
What are some examples of CUI?
Key examples of CUI include personally identifiable information (PII), proprietary business data, and certain technical content.
Why is understanding CUI important?
Understanding CUI is crucial for compliance with the Cybersecurity Maturity Model Certification (CMMC) and other federal regulations. Improper management of CUI can lead to serious legal and security repercussions.
What are the implications of improperly managing CUI?
Improper management of CUI can result in legal issues and security breaches, undermining trust and integrity within the defense contracting landscape.
How can organizations ensure compliance with CUI regulations?
Organizations can ensure compliance by taking proactive steps to safeguard CUI, which also enhances their reputation and reliability in the industry.
Where can I find more information about controlling CUI?
For further information and resources, refer to the external links provided on the CMMC Info Hub.